- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Inside - Inside NATting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Inside - Inside NATting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 12:10 PM - edited 12-28-2020 01:21 PM
Hello everyone.
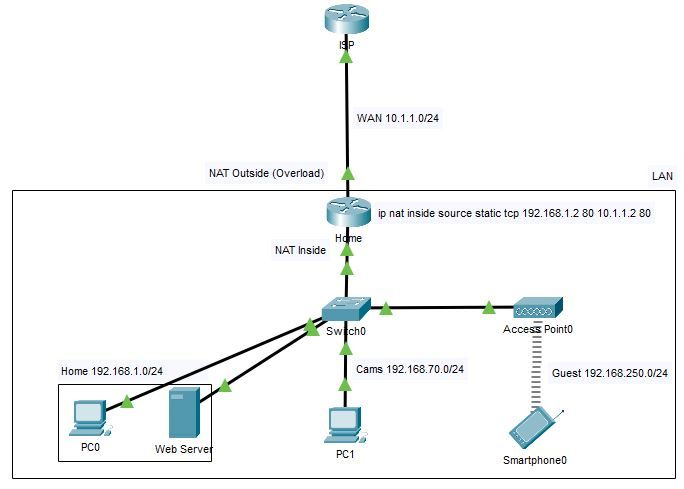
The image below is a simplified layout of my home network where I have a web server with port forwarding. From the WAN the server is accessible, and from the LAN it is through its LAN IP, as expected. The question is, how to make the server accessible from all 3 networks on the LAN through the public IP? Note that I'm using ZBF with each network on a separate zone and the required policies to allow specific interzone traffic.
This has proven surprisingly convoluted to pull off. I tried domainless NAT changing all 3 subtinterfaces and the WAN interface to ip nat enable with different combinations of no ip redirects, changing static NAT entries to ip nat source and clearing the NAT translation table, but all results in losing access to the internet; despite the router (ISR 1941 on IOS 15.8) showing NVI translations being made.
Running config attached.
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 12:15 PM
Hello
Can you copy the running config of the home rtr into a file and attach it to this OP please.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 01:14 PM
Hello Paul. Attached. Thanks for you help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 01:24 PM
Hello
Apologies but I don't see any attachment?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 03:58 AM - edited 12-29-2020 04:07 AM
Hello
You may have to hairpin using domian nat an as suggested by @Georg Pauwen however can you test something if possible and temporary remove the URPF from the interfaces and test again using the nat you already have applied.
in x/x
no ip verify unicast source reachable-via any
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 03:07 PM
Paul, removing URPF with NVR didn't do it. I lost Internet. More detail in my reply below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 02:59 AM - edited 12-29-2020 02:59 AM
Hello,
below is one way to make NAT hairpinning work. If you add the lines marked in bold, all three networks can access the local server (192.168.1.2) through its public IP address (10.1.1.2).
I took all the other static NAT entries out, to make clearer what I have configured:
Router1941#sh run
Building configuration...
Current configuration : 8715 bytes
!
! No configuration change since last restart
!
version 15.8
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec
service timestamps log datetime msec localtime show-timezone
service password-encryption
!
hostname Router1941
!
boot-start-marker
boot-end-marker
!
enable secret 5 <elided>
!
no aaa new-model
clock timezone EST -5 0
clock summer-time DST recurring
!
no ip source-route
ip options drop
!
ip dhcp bootp ignore
!
no ip bootp server
no ip domain lookup
ip domain name <elided>
ip name-server 192.168.1.14
ip name-server 8.8.8.8
ip name-server 8.8.4.4
ip cef
login block-for 120 attempts 3 within 60
no ipv6 cef
!
multilink bundle-name authenticated
!
license udi pid CISCO1941/K9 sn <elided>
license boot module c1900 technology-package securityk9
!
memory reserve critical 5
memory reserve console 4096
memory free low-watermark processor 10
memory free low-watermark IO 10
username <elided> secret 9 <elided>
!
redundancy
!
class-map type inspect match-any ALL_TRAFFIC_CMAP
match access-group name PERMIT_ANY
class-map type inspect match-any WAN-HOME_CMAP
match access-group name WAN-HOME
class-map type inspect match-any DHCP_REQUEST_CMAP
match access-group name DHCP_REQUEST
class-map type inspect match-any DCHP_REPLY_CMAP
match access-group name DHCP_REPLY
class-map type inspect match-any UNTRUSTED_VLAN-SELF_CMAP
match access-group name PERMIT_PING_GATEWAY
class-map type inspect match-any GUEST_WIFI-HOME_CMAP
match access-group name GUEST_WIFI-HOME
class-map type inspect match-any CAMERAS-WAN_CMAP
match access-group name PERMIT_CAMS_INTERNET
!
policy-map type inspect UNTRUSTED_VLAN-SELF_PMAP
description Passes DHCP requests, inspects ICMP and drops everything else.
class type inspect DHCP_REQUEST_CMAP
pass log
class type inspect UNTRUSTED_VLAN-SELF_CMAP
inspect
class class-default
drop log
policy-map type inspect SELF-WAN_PMAP
description Passes DHCP requests and inspects everything else.
class type inspect DHCP_REQUEST_CMAP
pass
class type inspect ALL_TRAFFIC_CMAP
inspect
class class-default
drop log
policy-map type inspect WAN-HOME_PMAP
class type inspect WAN-HOME_CMAP
inspect
class class-default
drop log
policy-map type inspect DHCP_REPLY_PMAP
description Passes DHCP replies.
class type inspect DCHP_REPLY_CMAP
pass log
class class-default
drop log
policy-map type inspect GUEST_WIFI-HOME_PMAP
class type inspect GUEST_WIFI-HOME_CMAP
inspect
class class-default
drop log
policy-map type inspect INSPECT_ALL_PMAP
class type inspect ALL_TRAFFIC_CMAP
inspect
class class-default
drop log
policy-map type inspect CAMERAS-WAN_PMAP
class type inspect CAMERAS-WAN_CMAP
inspect
class class-default
drop log
!
zone security WAN
zone security HOME
zone security GUEST_WIFI
zone security CAMERAS
zone-pair security SELF-WAN_ZP source self destination WAN
service-policy type inspect SELF-WAN_PMAP
zone-pair security WAN-SELF_ZP source WAN destination self
service-policy type inspect DHCP_REPLY_PMAP
zone-pair security HOME-WAN_ZP source HOME destination WAN
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security WAN-HOME_ZP source WAN destination HOME
service-policy type inspect WAN-HOME_PMAP
zone-pair security HOME-SELF_ZP source HOME destination self
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security SELF-HOME_ZP source self destination HOME
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security GUEST_WIFI-SELF_ZP source GUEST_WIFI destination self
service-policy type inspect UNTRUSTED_VLAN-SELF_PMAP
zone-pair security SELF-GUEST_WIFI_ZP source self destination GUEST_WIFI
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security GUEST_WIFI-WAN_ZP source GUEST_WIFI destination WAN
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security SELF-CAMERAS_ZP source self destination CAMERAS
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security CAMERAS-SELF_ZP source CAMERAS destination self
service-policy type inspect UNTRUSTED_VLAN-SELF_PMAP
zone-pair security HOME-CAMERAS_ZP source HOME destination CAMERAS
service-policy type inspect INSPECT_ALL_PMAP
zone-pair security CAMERAS-WAN_ZP source CAMERAS destination WAN
service-policy type inspect CAMERAS-WAN_PMAP
zone-pair security GUEST_WIFI-HOME_ZP source GUEST_WIFI destination HOME
service-policy type inspect GUEST_WIFI-HOME_PMAP
zone-pair security HOME-GUEST_WIFI_ZP source HOME destination GUEST_WIFI
service-policy type inspect INSPECT_ALL_PMAP
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
--> interface Loopback0
--> ip address 169.254.1.1 255.255.255.255
--> ip nat inside
!
interface GigabitEthernet0/0
description LAN
no ip address
ip virtual-reassembly in
duplex auto
speed auto
no mop enabled
!
interface GigabitEthernet0/0.1
description Home
encapsulation dot1Q 1
ip address 192.168.1.1 255.255.255.0
ip flow ingress
ip flow egress
no ip redirects
--> ip nat outside
--> ip policy route-map PBR_NAT_RM
ip virtual-reassembly in
ip verify unicast source reachable-via any
zone-member security HOME
!
interface GigabitEthernet0/0.70
description Cameras
encapsulation dot1Q 70
ip address 192.168.70.1 255.255.255.0
ip helper-address 192.168.1.14
ip flow ingress
ip flow egress
no ip redirects
--> ip nat outside
--> ip policy route-map PBR_NAT_RM
ip virtual-reassembly in
ip verify unicast source reachable-via any
zone-member security CAMERAS
!
interface GigabitEthernet0/0.111
description Native
encapsulation dot1Q 111 native
ip verify unicast source reachable-via any
!
interface GigabitEthernet0/0.250
description Guest WiFi
encapsulation dot1Q 250
ip address 192.168.250.1 255.255.255.0
ip helper-address 192.168.1.14
ip flow ingress
ip flow egress
no ip redirects
--> ip nat outside
--> ip policy route-map PBR_NAT_RM
ip virtual-reassembly in
ip verify unicast source reachable-via any
zone-member security GUEST_WIFI
!
interface GigabitEthernet0/1
description WAN
ip address dhcp client-id GigabitEthernet0/1
no ip redirects
--> ip nat outside
ip virtual-reassembly in
zone-member security WAN
duplex auto
speed auto
no cdp enable
no mop enabled
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
ip flow-export version 9
ip flow-export destination 192.168.1.116 11839
!
--> ip nat inside source static tcp 192.168.1.2 80 10.1.1.2 80
--> ip nat inside source list NAT_ACL interface GigabitEthernet0/1 overload
--> ip nat inside source list NAT__HAIRPIN_ACL interface Loopback0 overload
!
--> ip access-list extended NAT_ACL
--> deny ip 192.168.1.0 0.0.0.255 192.168.1.0 0.0.0.255
--> deny ip 192.168.70.0 0.0.0.255 192.168.70.0 0.0.0.255
--> deny ip 192.168.250.0 0.0.0.255 192.168.250.0 0.0.0.255
--> permit ip 192.168.1.0 0.0.0.255 any
--> permit ip 192.168.70.0 0.0.0.255 any
--> permit ip 192.168.250.0 0.0.0.255 any
!
--> ip access-list extended NAT_HAIRPIN_ACL
--> permit ip 192.168.1.0 0.0.0.255 host 192.168.1.2
--> permit ip 192.168.70.0 0.0.0.255 host 192.168.1.2
--> permit ip 192.168.250.0 0.0.0.255 host 192.168.1.2
!
--> route-map PBR_NAT_RM permit 10
--> set interface Loopback0
!
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 dhcp
ip ssh authentication-retries 5
ip ssh version 2
!
ip access-list standard NAT
remark
remark Permit Home VLAN
permit 192.168.1.0 0.0.0.255
remark Permit Guest WiFi VLAN
permit 192.168.250.0 0.0.0.255
remark Permit Cameras VLAN
permit 192.168.70.0 0.0.0.255
ip access-list standard PERMIT_ANY
permit any
!
ip access-list extended DHCP_REPLY
permit udp any any eq bootpc
ip access-list extended DHCP_REQUEST
permit udp any any eq bootps
ip access-list extended GUEST_WIFI-HOME
remark Plex
permit tcp 192.168.250.0 0.0.0.255 host 192.168.1.99 eq 32400
ip access-list extended PERMIT_CAMS_INTERNET
remark KT Cam
permit udp host 192.168.70.51 any
permit tcp host 192.168.70.51 any
remark LV Cam
permit udp host 192.168.70.52 any
permit tcp host 192.168.70.52 any
ip access-list extended PERMIT_PING_GATEWAY
remark Allow ping gateway from Guest Wifi VLAN
permit icmp 192.168.250.0 0.0.0.255 host 192.168.250.1
remark Allow ping gateway from Cameras VLAN
permit icmp 192.168.70.0 0.0.0.255 host 192.168.70.1
ip access-list extended WAN-HOME
remark Plex
permit tcp any host 192.168.1.99 eq 32400
remark piVPN
permit udp any host 192.168.1.118 eq 13808
remark Syncthing R01KDESKTOP
permit udp any host 192.168.1.24 eq 56363
remark Syncthing R01K-LAPTOP
permit udp any host 192.168.1.25 eq 57477
!
logging host 192.168.1.22
!
control-plane host
management-interface GigabitEthernet0/0.1 allow ftp https ssh tftp snmp
!
control-plane
!
banner motd ^CUnauthorized Access is Prohibited!^C
!
line con 0
exec-timeout 0 0
password 7 <elided>
logging synchronous
login
line aux 0
exec-timeout 0 1
no exec
transport output none
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
exec-timeout 60 0
login local
transport input ssh
line vty 5 15
login local
transport input none
!
exception crashinfo maximum files 5
scheduler allocate 20000 1000
ntp server 129.6.15.26
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 03:53 AM - edited 12-29-2020 04:02 PM
Hello @tresdodi
Did you try removing URPF from the existing NVI nat ?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 03:16 PM - edited 12-29-2020 03:19 PM
Thank you both for your input.
With Georg's configuration I'm still unable to connect internally and also face the original problem of losing Internet. Introducing Paul's adjustments brings Internet back, but no connection internally. I suspect that the ZBF is the obstacle but need to understand this hairpinning technique better in order to troubleshoot. If my interpretation of Georg's config is right, this is how it would work:
A. Connecting to the server from the inside through the public IP:
- Packet arrives at Gi0/0.1 (Home interface, nat outside) directed to 10.1.1.2 80 (public server socket). Because of the policy route to Lo0 (nat inside), the static translation occurs changing the destination to 192.168.1.2 80.
- As the packet turns around from Lo0 (nat inside) back to Gi0/0.1 (Home interface, nat outside) and matches NAT_HAIRPIN_ACL the origin address is translated to the Lo0 address.
B. Browsing the Internet:
- Packet directed to a WAN address arrives at Gi0/0.1 (Home interface, nat outside), it's routed to Lo0 (nat inside) and no NAT entry matches so no destination translation occurs.
- As the packet goes from Lo0 (nat inside) to the ISP gateway out of Gi0/1 (WAN interface, nat outside) and matches NAT_ACL the origin address is translated to the Gi0/1 address.
With Paul's variation having Lo0 as nat inside, translation on step A1 would not take place as the packet would be going inside -> inside.
Is this correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 03:46 PM - edited 12-29-2020 03:55 PM
Hello,
does it actually work with the ZBF disabled ?
Post the running configuration with the changes you have implemented. I have tested this without the ZBF, and Internet access worked fine..
EDIT: make the loopback interface member of an inside zone as well....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 05:09 PM
Tomorrow I'll change the ZBF and see. By the way, my comment that you replied to has disappeared. Strange )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 05:07 PM
I did. But I still had no Internet. On next tests tomorrow I'll play with the ZBF and report results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2020 12:59 AM
Hello,
I just lab tested this, adding the loopback to an inside zone seems to solve this (both NAT hairpinning and 'normal' NAT to the outside work).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 10:03 AM
Switching to NVI and taking the interfaces out of the Zone-Based Firewall (leaving URPF on) does the trick. I have Internet and NAT hairpinning works. I prefer this solution over the Loopback interface because it's much simpler. But I need ZBF and there's a bug in the interoperability of NVI and ZBF. When a policy is applied to the outside -> self zone pair, ZBF drops traffic returning to the self zone (the public IP). I confirmed that the bug occurs for me as described by many others. There are conflicting reports of this working fine on some IOS releases. The workarounds are stop using ZBF or pass traffic between outside and self zones, which are a no-go.
The loopback technique for some reason didn't work for me even without the ZBF. It must be something that I'm missing but I didn't dig deeper.
Regardless, I decided to use split DNS and put an ASA between the ISP modem and the router later if needed.
Thank you you both for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 11:58 AM
Hello,
I tested the 'loopback solution' with the ZBF and just with the configuration you initially posted (as far as I recall there was no self zone in there?). But good to know about the bug. That said, do you really need the self zone ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide