- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Internet not working (NAT)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Internet not working (NAT)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 09:17 PM
I have 2 ISP connected to my router
Presently my primary internet can make tunnel and my computer can connect to internet
as soon as my primary internet shuts, my secondary internet can make tunnel but my computer can not access internet
I have done the following command
ip nat inside source list NAT interface GigabitEthernet0 overload
I tried adding a second command
ip nat inside source list NAT interface fast ethernet 8 overload 10 (But this does not work)
- Labels:
-
LAN Switching
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 10:08 PM
When you have multiple interfaces where you want nat the usual solution is to implement nat using a route map.Something like ip nat inside source route-map ISP1 interface x. Where route map ISP1 will have two match statements. The first match would reference the acl that you use to identify the traffic and the second match statement would specify the interface. Use a second similar approach for the other interface and ISP2.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 11:34 PM
can you provide an example
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 12:28 AM
Hello,
post the full running configuration of your router...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 01:17 AM
Hello
You would require some conditional routing so when the primary default gateway is down the backup default via the secondary ISP is entered into the route table:
Example:
ip sla 1
icmp-echo x.x.x.x source-interface GigabitEthernet0
ip sla schedule 1 life forever start-time now
track 1 rtr 1 reachability
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0 x.x.x.x 1 name Primary-ISP track 1
ip route 0.0.0.0 0.0.0.0 ethernet 8 y.y.y.y.200 name secindary-ISP
As for the nat, using route-maps for both ISP links would be applicable
route-map LAN permit 10
match ip address NAT
match interface GigabitEthernet0
route-map LAN2 permit 10
match ip address NAT
match interface ethernet 8
ip nat inside source route-map LAN interface GigabitEthernet0 overload
ip nat inside source route-map LAN2 interface ethernet 8 overload
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 03:03 AM
sir
I have implemented this but internet on primary is not working. all other things are ok
On secondary internet My tunnel is working, also i can access internet
on Primary internet my tunnel is working but my computer can not access internet.
what is the problem with my current configuration.
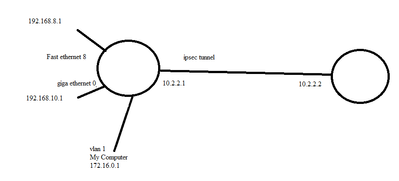
Interface1 : fastethernet 192.168.8.1 (For secondary Internet)
Interface1: Dialer1 (For Primary Internet, IP automatically assign)
Configuration:
ip source-route
!
track 200 interface Dialer1 ip routing
ip nat inside source route-map isp1 interface Dialer1 overload
ip nat inside source route-map isp2 interface FastEthernet8 overload
ip route 0.0.0.0 0.0.0.0 Dialer1 5 track 200
ip route 0.0.0.0 0.0.0.0 192.168.8.1 10
ip route 8.8.4.4 255.255.255.255 192.168.8.1
ip sla 8844
icmp-echo 8.8.4.4 source-interface FastEthernet8
timeout 1000
threshold 1000
frequency 5
ip sla schedule 8844 life forever start-time now
dialer-list 2 protocol ip permit
no cdp run
!
!
!
!
route-map isp2 permit 10
match ip address NAT
match interface FastEthernet8
!
route-map isp1 permit 10
match ip address NAT
match interface Dialer1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 03:26 AM - edited 02-04-2023 03:27 AM
ip route 8.8.4.4 255.255.255.255 192.168.8.1 <<- this wrong
you need
ip route 8.8.4.4 255.255.255.255 dialer1 permanent <<- and this
also
icmp-echo 8.8.4.4 source-interface FastEthernet8 <<- change the source interface to be dialer1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 12:46 AM
after changes, still unable to use internet through dialer connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:31 AM
can I see the last config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 02:06 AM - edited 02-06-2023 02:07 AM
yes
This is my full configuration
Please note that i can access my tunnel and internet from fastethernet8 , but from dialer1 can only access tunnel but no internet. i have reverse the settings you told me to change. this is my original confiuration
ip cef
ip domain name re.local
ip name-server 8.8.4.4
no ipv6 cef
track 200 interface Dialer1 ip routing
!
class-map type inspect match-any inside-to-vpn
match access-group name ACL-INSIDE-TO-VPN
class-map type inspect match-any vpn-to-inside
match access-group name ACL-VPN-TO-INSIDE
class-map type inspect match-any inside-to-outside
match access-group name ACL-INSIDE-TO-OUTSIDE
class-map type inspect match-any outside-to-self
match access-group name ACL-outside-TO-self
class-map type inspect match-any self-to-outside
match access-group name ACL-self-TO-outside
!
!
policy-map type inspect Policy-inside-to-vpn
class type inspect inside-to-vpn
inspect
class class-default
drop log
policy-map type inspect Policy-vpn-to-inside
class type inspect vpn-to-inside
inspect
class class-default
drop log
policy-map type inspect Policy-outside-to-self
class type inspect outside-to-self
inspect
class class-default
drop log
policy-map type inspect Policy-inside-to-outside
class type inspect inside-to-outside
inspect
class class-default
drop
policy-map type inspect Policy-self-to-outside
class type inspect self-to-outside
inspect
class class-default
drop log
!
zone security inside
zone security outside
zone security vpn
zone-pair security inside-to-outside source inside destination outside
service-policy type inspect Policy-inside-to-outside
zone-pair security inside-to-vpn source inside destination vpn
service-policy type inspect Policy-inside-to-vpn
zone-pair security vpn-to-inside source vpn destination inside
service-policy type inspect Policy-vpn-to-inside
zone-pair security outside-to-inside source outside destination inside
!
!
crypto isakmp policy 100
encr aes
authentication pre-share
group 2
crypto isakmp key ****** address 0.0.0.0 0.0.0.0
crypto isakmp keepalive 60
!
!
crypto ipsec transform-set CR-TS-***** esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile CR-PR-******
set transform-set CR-TS-******
!
!
!
!
!
!
interface Tunnel1
ip address 10.2.1.205 255.255.255.0
no ip redirects
ip mtu 1370
ip hold-time eigrp 10 60
ip nhrp authentication ****
ip nhrp map multicast dynamic
ip nhrp map multicast *.*.*.*
ip nhrp map 10.2.1.254 *.*.*.*
ip nhrp network-id 2
ip nhrp holdtime 120
ip nhrp nhs 10.2.1.254
ip nhrp registration no-unique
zone-member security vpn
tunnel source Dialer1
tunnel mode gre multipoint
tunnel key 121
tunnel protection ipsec profile CR-PR-*****
!
!
interface Tunnel2
ip address 10.2.2.205 255.255.255.0
no ip redirects
ip mtu 1390
ip nhrp authentication *****
ip nhrp map multicast dynamic
ip nhrp map multicast *.*.*.*
ip nhrp map 10.2.2.254 *.*.*.*
ip nhrp network-id 222
ip nhrp holdtime 60
ip nhrp nhs 10.2.2.254
ip nhrp registration no-unique
zone-member security vpn
tunnel source FastEthernet8
tunnel mode gre multipoint
tunnel key 222
tunnel protection ipsec profile CR-PR-*****
!
interface FastEthernet8
ip address 192.168.8.2 255.255.255.0
ip nat outside
ip virtual-reassembly
zone-member security outside
duplex auto
speed auto
!
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 2
!
!
interface Vlan1
ip address 172.20.5.1 255.255.255.0
ip nat inside
ip virtual-reassembly
zone-member security inside
ip tcp adjust-mss 1452
!
!
interface Dialer1
mtu 1480
bandwidth 6000
ip address negotiated
ip nat outside
ip virtual-reassembly
zone-member security outside
encapsulation ppp
ip tcp adjust-mss 1400
dialer pool 2
dialer-group 2
ppp authentication chap pap callin
ppp chap hostname 0258545240de
ppp chap password 0 test
ppp pap sent-username 0258545240 password 0 test
no cdp enable
!
!
!
router eigrp 10
network 10.2.1.0 0.0.0.255
network 172.20.5.0 0.0.0.255
passive-interface Vlan1
eigrp stub connected
!
!
router eigrp 2
network 10.2.2.0 0.0.0.255
network 172.20.5.0 0.0.0.255
passive-interface Vlan1
eigrp stub connected
!
ip forward-protocol nd
no ip http server
ip http authentication local
no ip http secure-server
!
!
ip dns server
ip nat inside source route-map isp1 interface Dialer1 overload
ip nat inside source route-map isp2 interface FastEthernet8 overload
ip route 0.0.0.0 0.0.0.0 Dialer1 5 track 200
ip route 0.0.0.0 0.0.0.0 192.168.8.1 10
ip route 8.8.4.4 255.255.255.255 192.168.8.1
!
ip access-list extended ACL-INSIDE-TO-OUTSIDE
permit ip any any
permit udp any any
ip access-list extended ACL-INSIDE-TO-VPN
permit ip any any
permit udp any any
ip access-list extended ACL-VPN-TO-INSIDE
permit ip any any
permit udp any any
ip access-list extended ACL-outside-TO-self
permit ip any any
permit udp any any
ip access-list extended ACL-self-TO-outside
permit ip any any
permit udp any any
ip access-list extended NAT
permit ip 172.20.5.0 0.0.0.255 any
!
ip sla 8844
icmp-echo 8.8.4.4 source-interface FastEthernet8
timeout 1000
threshold 1000
frequency 5
ip sla schedule 8844 life forever start-time now
dialer-list 2 protocol ip permit
no cdp run
!
!
!
!
route-map isp2 permit 10
match ip address NAT
match interface FastEthernet8
!
route-map isp1 permit 10
match ip address NAT
match interface Dialer1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 03:21 AM
but you dont add static route with permanent and you dont change the source of IP SLA ? or this is old config ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2023 10:00 PM
I have changed the configuration. see if its ok
interface Dialer1
mtu 1480
bandwidth 6000
ip address negotiated
ip nat outside
ip virtual-reassembly
zone-member security outside
encapsulation ppp
ip tcp adjust-mss 1400
dialer pool 2
dialer-group 2
ppp authentication chap pap callin
ppp chap hostname *****
ppp chap password 0 ptcl
ppp pap sent-username ****** password 0 *****
no cdp enable
exit
interface FastEthernet8
ip address 192.168.8.2 255.255.255.0
ip nat outside
no shut
exit
ip sla 8844
icmp-echo 8.8.4.4 source-interface dialer1
frequency 10
exit
ip sla schedule 8844 start-time now life forever
track 1 ip sla 8844
track 1 ip sla 8844 reachability
delay 10 up 10 down 10
exit
route-map for_isp1 permit 10
match interface dialer1
exit
route-map for_isp2 permit 10
match interface FastEthernet8
exit
ip route 0.0.0.0 0.0.0.0 192.168.8.1 2
ip route 0.0.0.0 0.0.0.0 dialer1 track 1
ip nat inside source route-map for_isp1 interface dialer1 overload
ip nat inside source route-map for_isp2 interface FastEthernet8 overload
also should i add these lines ???????
ip access-list extended for_isp1
permit icmp any hotst 8.8.4.4
permit icmp any 8.8.4.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2023 11:07 PM
Hello,
it looks like you also have a ZBF implemented. FastEthernet8 is not a member of the outside zone ? Is that intentional ? Post the full running configuration (sh run), as the ZBF requires a lot of other configuration details that need to be checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 01:07 AM
The route maps for NAT have a match statement for the interface but do not have a match statement for an acl to identify traffic.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 09:55 AM
It OK from my view,
do you check connectivity ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide