- Cisco Community
- Technology and Support
- Networking
- Routing
- IOS VPN double nat
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IOS VPN double nat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2011 09:53 AM - edited 03-04-2019 11:47 AM
Hi,
I have an issue with a 881 router doing source and destination nat with VPN.
We are hosting a service where we need access to customers infrastructure. Our machine has IP 10.145.4.76 and needs to be natted due to ip overlapping at customers sites. Furthermore we do not dictate customers ip subnets. Then we need both source and destination nat after encryption on customer site.
plz help
Thomas
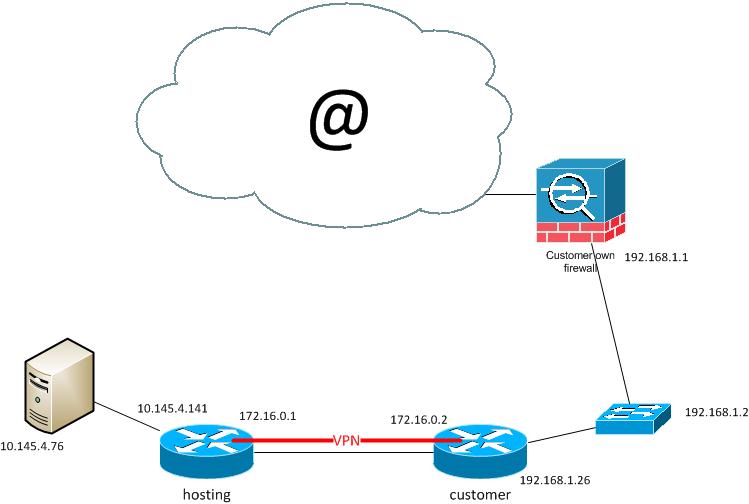
Hosting router (no changes possible, this is a test setup, we are using an ASA in production):
crypto isakmp policy 10
encr aes 256
hash md5
authentication pre-share
group 2
crypto isakmp key ********* address 172.16.0.2 no-xauth
!
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes 256 esp-md5-hmac
!
crypto map solarwinds 10 ipsec-isakmp
set peer 172.16.0.2
set transform-set ESP-AES-256-MD5
match address vpn_acl
!
interface FastEthernet4
ip address 172.16.0.1 255.255.255.252
crypto map solarwinds
!
interface Vlan1
ip address 10.145.4.141 255.255.255.0
!
ip access-list extended vpn_acl
permit ip host 10.145.4.76 10.127.45.0 0.0.0.255
!
ip route 10.127.45.0 255.255.255.0 172.16.0.2
Customer router (change need to be done here):
crypto isakmp policy 10
encr aes 256
hash md5
authentication pre-share
group 2
crypto isakmp key ********** address 172.16.0.1 no-xauth
!
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes 256 esp-md5-hmac
!
crypto map solarwinds 10 ipsec-isakmp
set peer 172.16.0.1
set transform-set ESP-AES-256-MD5
match address vpn_acl
!
interface FastEthernet4
ip address 172.16.0.2 255.255.255.252
ip nat outside
ip virtual-reassembly
crypto map solarwinds
!
interface Vlan1
ip address 192.168.1.26 255.255.255.0
ip nat inside
ip virtual-reassembly
!
ip route 0.0.0.0 0.0.0.0 172.16.0.1
!
ip nat inside source static network 192.168.1.0 10.127.45.0 /28 extendable
ip nat outside source static 10.145.4.76 192.168.1.27 extendable add-route
!
ip access-list extended vpn_acl
permit ip 10.127.45.0 0.0.0.255 host 10.145.4.76
DEBUG nat detailed and icmp:
*Mar 17 16:31:40.215: NAT*: o: icmp (10.145.4.76, 1) -> (10.127.45.1, 1) [14706]
*Mar 17 16:31:40.215: NAT*: o: icmp (10.145.4.76, 1) -> (10.127.45.1, 1) [14706]
*Mar 17 16:31:40.215: NAT*: s=10.145.4.76->192.168.1.27, d=10.127.45.1 [14706]
*Mar 17 16:31:40.215: NAT*: s=192.168.1.27, d=10.127.45.1->192.168.1.1 [14706]
*Mar 17 16:31:40.219: ICMP: echo reply rcvd, src 192.168.1.1, dst 192.168.1.27
brink#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
--- --- --- 192.168.1.27 10.145.4.76
icmp 10.127.45.1:1 192.168.1.1:1 192.168.1.27:1 10.145.4.76:1
--- 10.127.45.1 192.168.1.1 --- ---
--- 10.127.45.0 192.168.1.0 --- ---
protected vrf: (none)
local ident (addr/mask/prot/port): (10.127.45.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.145.4.76/255.255.255.255/0/0)
current_peer 172.16.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 70, #pkts decrypt: 70, #pkts verify: 70
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.0.2, remote crypto endpt.: 172.16.0.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet4
current outbound spi: 0x62CF4C51(1657752657)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xFD47C1D7(4249338327)
transform: esp-256-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 5, flow_id: Onboard VPN:5, sibling_flags 80000046, crypto map: solarwinds
sa timing: remaining key lifetime (k/sec): (4524473/1655)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x62CF4C51(1657752657)
transform: esp-256-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 6, flow_id: Onboard VPN:6, sibling_flags 80000046, crypto map: solarwinds
sa timing: remaining key lifetime (k/sec): (4524474/1655)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
- Labels:
-
Other Routing
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide