- Cisco Community
- Technology and Support
- Networking
- Routing
- IPSEC in ASR 1001-X
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 03:11 AM
Hello Team,
I am planning to replace old End of Support IPSEC router with new ASR 1001-X. This router has included IOS as below:
Cisco IOS XE Software, Version 16.06.03 Cisco IOS Software [Everest], ASR1000 Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.6.3, RELEASE SOFTWARE (fc8)
I would like to paste there IPSEC configuration. Will it work? I mean, do I need some specific IOS or license to run simple IPSEC?
My old IPSEC router is Cisco 3845, with IOS Version 12.4(20)T3, (c3845-advsecurityk9-mz.124-20.T3). There are no licenses, and IPSEC is working good.
ipsec4#sh license
ipsec4#dir flash:
Directory of flash:/
1 -rw- 40031984 Apr 12 2011 06:44:06 +00:00 c3845-advsecurityk9-mz.124-20.T3
2 -rw- 2751 May 15 2008 07:58:04 +00:00 sdmconfig-38xx.cfg
3 -rw- 6389760 May 15 2008 07:58:34 +00:00 sdm.tar
4 -rw- 931840 May 15 2008 07:58:50 +00:00 es.tar
5 -rw- 1505280 May 15 2008 07:59:08 +00:00 common.tar
6 -rw- 1038 May 15 2008 07:59:24 +00:00 home.shtml
7 -rw- 112640 May 15 2008 07:59:36 +00:00 home.tar
8 -rw- 1697952 May 15 2008 07:59:58 +00:00 securedesktop-ios-3.1.1.45-k9.pkg
9 -rw- 415956 May 15 2008 08:00:14 +00:00 sslclient-win-1.1.4.176.pkg
10 -rw- 12343 Oct 12 2011 11:50:02 +00:00 backup_conf
11 -rw- 11091 Sep 12 2011 14:07:04 +00:00 ipsec4.txt
64012288 bytes total (12877824 bytes free)Please let me know.. or show me way how to check it.
Thanks a lot.
Jozef
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 03:30 AM
Hello @jbaros
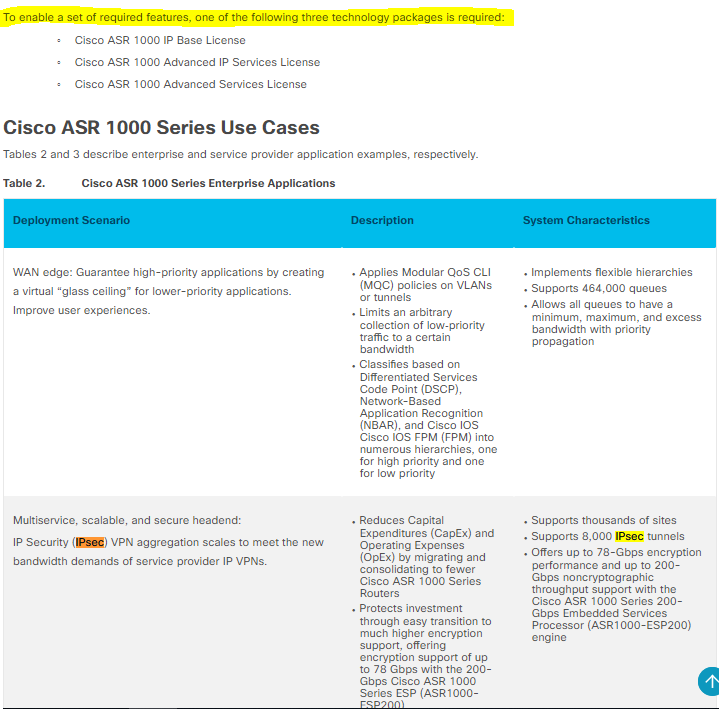
Look it:
More information here: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/datasheet-c78-731632.html
*** Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 03:30 AM
Hello @jbaros
Look it:
More information here: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/datasheet-c78-731632.html
*** Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 04:21 AM
Hello,
one thing to keep in mind is that encryption algorithms have evolved quite a bit since verison 12.4. So cutting and pasting might work, but it is better to manually change the IPSec parameters mentioned below:
--> Cisco no longer recommends using DES, 3DES, MD5 (including HMAC variant), and Diffie-Hellman (DH) groups 1, 2 and 5; instead, you should use AES, SHA and DH Groups 14 or higher.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide