- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: IPsec tunnel issue (between Cisco & Fortigate)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPsec tunnel issue (between Cisco & Fortigate)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 02:35 AM
Hey all,
Right now im trying to establish a site to site IPsec between a Cisco 2900 Router and a FortiGate 40F Firewall. The FortiGate GUI shows that the Tunnel is UP, but on the Cisco it's still not working.
Debug on Cisco:
000087: *Aug 17 17:04:36.311 MET: IKEv2-ERROR:Couldn't find matching SA: Detected an invalid IKE SPI
000088: *Aug 17 17:04:36.311 MET: IKEv2-PAK:(SESSION ID = 0,SA ID = 0):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER Message id: 0, length: 88
000089: *Aug 17 17:04:36.311 MET: IKEv2-ERROR:: A supplied parameter is incorrect
000090: *Aug 17 17:04:36.311 MET: IKEv2-ERROR:Couldn't find matching SA: Detected an invalid IKE SPI
000091: *Aug 17 17:04:36.311 MET: IKEv2-PAK:(SESSION ID = 0,SA ID = 0):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER Message id: 0, length: 88
000092: *Aug 17 17:04:36.311 MET: IKEv2-ERROR:: A supplied parameter is incorrect
000093: *Aug 17 17:04:36.315 MET: IKEv2-PAK:(SESSION ID = 1415,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: IKE_AUTH, flags: RESPONDER MSG-RESPONSE Message id: 1, length: 248
Payload contents:
IDr Next payload: AUTH, reserved: 0x0, length: 13
Id type: FQDN, Reserved: 0x0 0x0
AUTH Next payload: SA, reserved: 0x0, length: 56
Auth method PSK, reserved: 0x0, reserved 0x0
SA Next payload: TSi, reserved: 0x0, length: 44
last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA384
last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
TSi Next payload: TSr, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 172.19.58.2, end addr: 172.19.58.2
TSr Next payload: NONE, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 172.20.32.2, end addr: 172.20.32.2
Debug on FortiGate:
ike 0:IPSEC:7729: enc 2700000D02000000466F7274692100003802000000A1A3E9C1FB05665A8AB9748404008262F793B2510A84C615558286D7FFF1569F7889FA0CB2F1EAE0A2DA2009911FF2B92C00002C00000028010304036D41372C0300000C0100000C800E0100030000080300000D00000008050000002D00001801000000070000100000FFFFAC133A02AC133A020000001801000000070000100000FFFFAC142002AC1420020E0D0C0B0A0908070605040302010E
ike 0:IPSEC:7729: out 4D03AA75B993DBA72D3755CF2BF798B02E20232000000001000000F8240000DC174306D41DC510A0F9A9EDC94D411DEE2E0AA47BA8F857C666AA0CCCC28A1B058A94311E85A9A4477409C8F0C364D22E27F1B1D5634AEF36F061C2DCB72207E5D1DF7B73620D806CCD4E3ADBE604553E10BEC0F76A6B29735607BF2C82678C5222F8BE4BEC53A0758B3327942E3D7A6E0B823D28CB8A3C5C91677B0A02C59473A58552631BEF6B2AEB9CB8E1EC30C72CF0D627C4427580FC1B770C85105D57BAD4636613CA094ABB5378AE960D7BE00C3DE5E23EC354C0789C0BC111D2BAE6C67328CE6E06B08A4B38F8B0CF2F4FBEC32F5BADD2E0F21768
ike 0:IPSEC:7729: sent IKE msg (AUTH_RESPONSE): 20.113.40.21:500->20.113.40.20:500, len=248, id=4d03aa75b993dba7/2d3755cf2bf798b0:00000001
ike 0:IPSEC:7728: out F27D1FE3C91885D98A05085C5F95F1912E20250000000000000000582A00003CDEBE755BEE14AA3E05D75C1BACE79CCEB60CD47A75238020AFFF57DFBFFF3563A63F973935DED013AEE8B71516FCEF3A2A0010CFABE38B40
ike 0:IPSEC:7728: sent IKE msg (RETRANSMIT_INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=f27d1fe3c91885d9/8a05085c5f95f191
ike 0:IPSEC:7728: out F27D1FE3C91885D98A05085C5F95F1912E20250000000000000000582A00003CDEBE755BEE14AA3E05D75C1BACE79CCEB60CD47A75238020AFFF57DFBFFF3563A63F973935DED013AEE8B71516FCEF3A2A0010CFABE38B40
ike 0:IPSEC:7728: sent IKE msg (RETRANSMIT_INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=f27d1fe3c91885d9/8a05085c5f95f191
ike shrank heap by 159744 bytes
ike 0:IPSEC:7728: out F27D1FE3C91885D98A05085C5F95F1912E20250000000000000000582A00003CDEBE755BEE14AA3E05D75C1BACE79CCEB60CD47A75238020AFFF57DFBFFF3563A63F973935DED013AEE8B71516FCEF3A2A0010CFABE38B40
ike 0:IPSEC:7728: sent IKE msg (RETRANSMIT_INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=f27d1fe3c91885d9/8a05085c5f95f191
ike 0: comes 20.113.40.20:500->20.113.40.21:500,ifindex=8....
ike 0: IKEv2 exchange=SA_INIT id=4b41e0a2391b4cb9/0000000000000000 len=398
ike 0: in 4B41E0A2391B4CB9000000000000000021202208000000000000018E220000300000002C010100040300000C0100000C800E01000300000802000006030000080300000D0000000804000005280000C8000500005B995A3FC39FE90554467E070D76F519777E59850ADA483F372E5A13C5F11BF2427EC6FCB979A32EAA34B65273FE5C6D8929DFFA79A287A71E8E1C6C68F5ED0D3B0DA9B901A60B8286A033EF26DF77BBB1FB35B7AEC7279486F12FA4C6098EE2D62C89B975246517EA58CA35CDB27397DF853664C29DD4C9173E2CA9DC342D8F57A28D0760FB271AF463717934C986DA7133AAF83AEF5255565BB32C6F335CDA5765DC16DDBFF34281B67B3AD9BCB78F2C1E00DA894AD18CC6D436E4BE045C5B2B000024A1B9045E66A8E191BDBDCA719BDBF8958F749C115D5E4972F2C77987E7BCA2422B000017434953434F2D44454C4554452D524541534F4E2B000013434953434F56504E2D5245562D30322B000017434953434F2D44594E414D49432D524F55544500000015464C455856504E2D535550504F52544544
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: responder received SA_INIT msg
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: VID unknown (19): CISCO-DELETE-REASON
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: VID unknown (15): CISCOVPN-REV-02
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: VID unknown (19): CISCO-DYNAMIC-ROUTE
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: VID unknown (17): FLEXVPN-SUPPORTED
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: incoming proposal:
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: proposal id = 1:
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: protocol = IKEv2:
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: encapsulation = IKEv2/none
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=ENCR, val=AES_CBC (key_len = 256)
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=INTEGR, val=AUTH_HMAC_SHA2_384_192
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=PRF, val=PRF_HMAC_SHA2_384
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=DH_GROUP, val=MODP1536.
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: matched proposal id 1
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: proposal id = 1:
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: protocol = IKEv2:
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: encapsulation = IKEv2/none
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=ENCR, val=AES_CBC (key_len = 256)
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=INTEGR, val=AUTH_HMAC_SHA2_384_192
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=PRF, val=PRF_HMAC_SHA2_384
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: type=DH_GROUP, val=MODP1536.
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: lifetime=3600
ike 0:4b41e0a2391b4cb9/0000000000000000:7730: SA proposal chosen, matched gateway IPSEC
ike 0: found IPSEC 20.113.40.21 8 -> 20.113.40.20:500
ike 0:IPSEC:7730: responder preparing SA_INIT msg
ike 0:IPSEC:7730: out 4B41E0A2391B4CB987099916DC3EAD42212022200000000000000138220000300000002C010100040300000C0100000C800E01000300000802000006030000080300000D0000000804000005280000C8000500002722BAE54C8F9A4194852A1D08FF1A74277CD0B13F0BDD8395732F0081900133B0C3440387C88ECB62D37D31431F7AD08C27B0A76E260A7A745EAB734A12076F9A34778DD9F2FB8ED0392ABB9C50B7A32D413B7BEA627A80B9D26833EF81FF4BAFC9D07798989A856879D2A56AE35C0143C21FBD2C5C0A924605D36D61B76F1F94D234BC79A71A2EB10E1741CE38EE65D3BB7FB4CF9D5AE11172527E6ADE7E1BC614AA66DE29B22CEF40B60591037E85BFD21B0057766D6483F4591FBFE6E32F00000024CD2966F34F553E5A2FC4012771E6825CA05E31A187995F532EABDFF9DBF2C6AC
ike 0:IPSEC:7730: sent IKE msg (SA_INIT_RESPONSE): 20.113.40.21:500->20.113.40.20:500, len=312, id=4b41e0a2391b4cb9/87099916dc3ead42
ike 0:IPSEC:7730: IKE SA 4b41e0a2391b4cb9/87099916dc3ead42 SK_ei 32:46596C02B2EF32A2018CB458A971C77EA1FC656B58023EA4795D85BD37B5681E
ike 0:IPSEC:7730: IKE SA 4b41e0a2391b4cb9/87099916dc3ead42 SK_er 32:F3915C9CE92F8D6A9816CAAE3BC70C09AA619E7B40614E4B0E2247EF1C5C1E75
ike 0:IPSEC:7730: IKE SA 4b41e0a2391b4cb9/87099916dc3ead42 SK_ai 48:3018E934FD70B307ADF82D83D28FE2C45DB13C1A6AA7B3AE20028EE8B3141CF6EC80007BD7055117B82D140175A348B0
ike 0:IPSEC:7730: IKE SA 4b41e0a2391b4cb9/87099916dc3ead42 SK_ar 48:D63CE52C9CCD093485BE16DFFE8855C35C17C890EE1B2EFC4403A637D8806E9C3DD8E248FEFC625E9D4FB4FDC68C5B8C
ike 0: comes 20.113.40.20:500->20.113.40.21:500,ifindex=8....
ike 0: IKEv2 exchange=AUTH id=4b41e0a2391b4cb9/87099916dc3ead42:00000001 len=296
ike 0: in 4B41E0A2391B4CB987099916DC3EAD422E20230800000001000001282B00010C3A7E227DBA7B26C10990244CAF1C201116D33FA18DD3578372DFC888EF58B3BE5CFC040723044D5784496F56176517651680A234282E7D6D7B86D34D9940AACD060CA077CC89643705064D4818416C84E9AF8FE82DF73BBBCE3478704AC1C58B583070893394FA5B4E6429D867AD1C730F9E47938AC16029E5C2E1BF544BABAEED9EEBFA7EAF30F770FA0565B0B4193B0E0C7B7324BACDCEEEABA5AA3BBC7A3AE9DFFF026C67B2F085809C9E496FD763D30A9E11A68CCD41BBC26384CB083E624D2C0E3C824B692D8D8E895E616E99CFA4D3E88F703C49D872859C83BE4D436518EC4BD93DA190E463FC8CC5D413A6630B9CA858D478E0BFCC33F2516A7383E7D7DCE9416C2F231B
ike 0:IPSEC:7730: dec 4B41E0A2391B4CB987099916DC3EAD422E20230800000001000000F82B000004230000144A41E1A22A2CBFFE3B262D535015BC622700000C01000000147128142100003802000000B983ACAAC629AD5EE7A0F8BDE8A19774E0492AB18C48649C47D51515F6A7C05AB8C151944545728477AC237E444F4EE02C00002C00000028010304032648F4F10300000C0100000C800E0100030000080300000D00000008050000002D00001801000000070000100000FFFFAC133A00AC133AFF2900001801000000070000100000FFFFAC142000AC1420FF29000008000040002900000C0000400100000005290000080000400A000000080000400B
ike 0:IPSEC:7730: responder received AUTH msg
ike 0:IPSEC:7730: processing notify type INITIAL_CONTACT
ike 0:IPSEC:7730: processing notify type SET_WINDOW_SIZE
ike 0:IPSEC:7730: processing notify type ESP_TFC_PADDING_NOT_SUPPORTED
ike 0:IPSEC:7730: processing notify type NON_FIRST_FRAGMENTS_ALSO
ike 0:IPSEC:7730: peer identifier IPV4_ADDR 20.113.40.20
ike 0:IPSEC:7730: auth verify done
ike 0:IPSEC:7730: responder AUTH continuation
ike 0:IPSEC:7730: authentication succeeded
ike 0:IPSEC:7730: responder creating new child
ike 0:IPSEC:7730:7761: peer proposal:
ike 0:IPSEC:7730:7761: TSi_0 0:172.19.58.0-172.19.58.255:0
ike 0:IPSEC:7730:7761: TSr_0 0:172.20.32.0-172.20.32.255:0
ike 0:IPSEC:7730:PHASE2:7761: comparing selectors
ike 0:IPSEC:7730:PHASE2:7761: matched by rfc-rule-4
ike 0:IPSEC:7730:PHASE2:7761: phase2 matched by intersection
ike 0:IPSEC:7730:PHASE2:7761: accepted proposal:
ike 0:IPSEC:7730:PHASE2:7761: TSi_0 0:172.19.58.2-172.19.58.2:0
ike 0:IPSEC:7730:PHASE2:7761: TSr_0 0:172.20.32.2-172.20.32.2:0
ike 0:IPSEC:7730:PHASE2:7761: autokey
ike 0:IPSEC:7730:PHASE2:7761: incoming child SA proposal:
ike 0:IPSEC:7730:PHASE2:7761: proposal id = 1:
ike 0:IPSEC:7730:PHASE2:7761: protocol = ESP:
ike 0:IPSEC:7730:PHASE2:7761: encapsulation = TUNNEL
ike 0:IPSEC:7730:PHASE2:7761: type=ENCR, val=AES_CBC (key_len = 256)
ike 0:IPSEC:7730:PHASE2:7761: type=INTEGR, val=SHA384
ike 0:IPSEC:7730:PHASE2:7761: type=ESN, val=NO
ike 0:IPSEC:7730:PHASE2:7761: PFS is disabled
ike 0:IPSEC:7730:PHASE2:7761: matched proposal id 1
ike 0:IPSEC:7730:PHASE2:7761: proposal id = 1:
ike 0:IPSEC:7730:PHASE2:7761: protocol = ESP:
ike 0:IPSEC:7730:PHASE2:7761: encapsulation = TUNNEL
ike 0:IPSEC:7730:PHASE2:7761: type=ENCR, val=AES_CBC (key_len = 256)
ike 0:IPSEC:7730:PHASE2:7761: type=INTEGR, val=SHA384
ike 0:IPSEC:7730:PHASE2:7761: type=ESN, val=NO
ike 0:IPSEC:7730:PHASE2:7761: PFS is disabled
ike 0:IPSEC:7730:PHASE2:7761: lifetime=3600
ike 0:IPSEC:7730: responder preparing AUTH msg
ike 0:IPSEC:7730: established IKE SA 4b41e0a2391b4cb9/87099916dc3ead42
ike 0:IPSEC:7730: processing INITIAL-CONTACT
ike 0:IPSEC: flushing
ike 0:IPSEC: deleting IPsec SA with SPI f256164b
ike 0:IPSEC:PHASE2: deleted IPsec SA with SPI f256164b, SA count: 0
ike 0:IPSEC: sending SNMP tunnel DOWN trap for PHASE2
ike 0:IPSEC:7729:PHASE2:7759: sending delete for IPsec SA SPI 6d41372c
ike 0:IPSEC:7729:7762: send informational
ike 0:IPSEC:7729: enc 0000000C030400016D41372C03020103
ike 0:IPSEC:7729: out 4D03AA75B993DBA72D3755CF2BF798B02E20250000000000000000582A00003C8431BC904EE0B39CB86B33B361B073372A1F48DE48C9F5CC64E457F2D31BE09E1A82C203447FECFEEFA6998EEE4B25655D6452CAC7EF946B
ike 0:IPSEC:7729: sent IKE msg (INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=4d03aa75b993dba7/2d3755cf2bf798b0
ike 0:IPSEC:PHASE2: sending SNMP tunnel DOWN trap
ike 0:IPSEC: deleting IPsec SA with SPI f256164b
ike 0:IPSEC: deleting IPsec SA with SPI 133511a1
ike 0:IPSEC: deleting IPsec SA with SPI f256164b
ike 0:IPSEC:7729:7763: send informational
ike 0:IPSEC:7729: enc 00000008010000000706050403020107
ike 0:IPSEC:7729: out 4D03AA75B993DBA72D3755CF2BF798B02E20250000000000000000582A00003CEF40F7B603616AD2E1573F35D59CD1E7262777831816763A37C4F8BAC9D2FC98547BA92C16C0AB9AAD460162A7A8F81A215A1675FB567B00
ike 0:IPSEC:7729: sent IKE msg (INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=4d03aa75b993dba7/2d3755cf2bf798b0
ike 0:IPSEC: schedule auto-negotiate
ike 0:IPSEC: deleting IPsec SA with SPI 133511a1
ike 0:IPSEC:7728:7764: send informational
ike 0:IPSEC:7728: enc 00000008010000000706050403020107
ike 0:IPSEC:7728: out F27D1FE3C91885D98A05085C5F95F1912E20250000000000000000582A00003CF42448826441A894C9C2770C75C25B046A898AD75F9835C16B5FF21E528FE7D7BE57E35E400F28FE1A83EA12AA6E48ABB6F838B5342AA374
ike 0:IPSEC:7728: sent IKE msg (INFORMATIONAL): 20.113.40.21:500->20.113.40.20:500, len=88, id=f27d1fe3c91885d9/8a05085c5f95f191
ike 0:IPSEC: flushed
ike 0:IPSEC:7730: processed INITIAL-CONTACT
ike 0:IPSEC:7730:PHASE2:7761: replay protection enabled
ike 0:IPSEC:7730:PHASE2:7761: set sa life soft seconds=3331.
ike 0:IPSEC:7730:PHASE2:7761: set sa life hard seconds=3600.
ike 0:IPSEC:7730:PHASE2:7761: IPsec SA selectors #src=1 #dst=1
ike 0:IPSEC:7730:PHASE2:7761: src 0 7 0:172.20.32.2-172.20.32.2:0
ike 0:IPSEC:7730:PHASE2:7761: dst 0 7 0:172.19.58.2-172.19.58.2:0
ike 0:IPSEC:7730:PHASE2:7761: add IPsec SA: SPIs=6d41372d/2648f4f1
ike 0:IPSEC:7730:PHASE2:7761: IPsec SA dec spi 6d41372d key 32:736CCBF9D6876A594EF14BC44E5946595ADF77F0655B879D5C8C3FBAE058BC94 auth 48:2D7AB0D922D6B18EA76FCB4A308B3EDF4AF871854AD7F6EBDD9842F5679A76723C738DFCDA31017847FD1CA0C858E01E
ike 0:IPSEC:7730:PHASE2:7761: IPsec SA enc spi 2648f4f1 key 32:3CABDB3478713846F4DADCB1197732547791E244C87A1ED129FF30045DA412F9 auth 48:F9AEE42BA3CDD0393ABCEC5E1D880A3E1B0A1E233DF43BC7EA1D83ED9750DCC360FF0E75E74681F88B8415D9E62371C6
ike 0:IPSEC:7730:PHASE2:7761: added IPsec SA: SPIs=6d41372d/2648f4f1
ike 0:IPSEC:7730:PHASE2:7761: sending SNMP tunnel UP trap
ike 0:IPSEC:7730: enc 2700000D02000000466F7274692100003802000000B8D1BB750C3279675975B8782E9A42CAA051D144FF7F9E585BD17294A9BFAC788B8F39545535627302FA06894488DF302C00002C00000028010304036D41372D0300000C0100000C800E0100030000080300000D00000008050000002D00001801000000070000100000FFFFAC133A02AC133A020000001801000000070000100000FFFFAC142002AC1420020E0D0C0B0A0908070605040302010E
ike 0:IPSEC:7730: out 4B41E0A2391B4CB987099916DC3EAD422E20232000000001000000F8240000DC087B8FA70D0B95FCDA07DCFC580AD0B95A988347E965A284169328278C8AAAF3178B2800CC62BC4E38034EDFA06A377A7BD84D9150BD77A6312CCDC5BADC025958C88D7109EDA008ECCD45BD30258DF59D3C5A099AF40177C721209EA29E5486339F35DB4702AEB9793684176019006E5CABCA62B9179AFC349DD19A0DE2A44DA90F322BE0E28B4B7D9E00CCEBE862BA9E672BF08966FA9FB5DC524E37D82D0A6052E9371678BC2EB10213A36B986FAA9A8A8797999559A02B80B8DE79989F63F21C3B11DF049076A0052C67249B17A30556BBC613A93808
ike 0:IPSEC:7730: sent IKE msg (AUTH_RESPONSE): 20.113.40.21:500->20.113.40.20:500, len=248, id=4b41e0a2391b4cb9/87099916dc3ead42:00000001
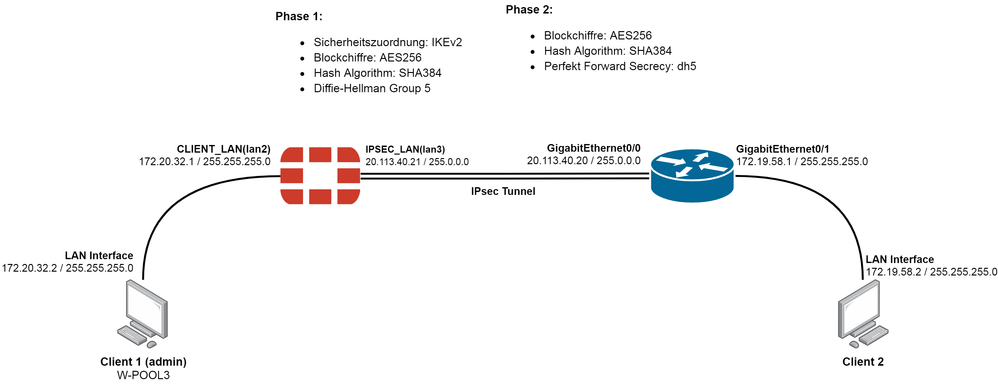
Cisco Config:
Current configuration : 5883 bytes
!
redundancy
!
crypto ikev2 proposal FortiProposal
encryption aes-cbc-256
integrity sha384
group 5
!
crypto ikev2 policy FortiPolicy
match address local 20.113.40.20
proposal FortiProposal
!
crypto ikev2 keyring FortiKeyring
peer Forti
address 20.113.40.21 255.0.0.0
pre-shared-key pskey
!
!
!
crypto ikev2 profile FortiProfile
match identity remote address 20.113.40.21 255.255.255.255
identity local address 20.113.40.20
authentication remote pre-share
authentication local pre-share
keyring local FortiKeyring
!
no crypto ikev2 http-url cert
!
!
!
crypto logging session
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 periodic
!
crypto ipsec security-association idle-time 60
!
crypto ipsec transform-set FortiTransform esp-aes 256 esp-sha384-hmac
mode tunnel
no crypto ipsec nat-transparency udp-encapsulation
!
!
!
crypto map FortiMap 10 ipsec-isakmp
set peer 20.113.40.21
set transform-set FortiTransform
set pfs group5
set ikev2-profile FortiProfile
match address FortiAccess
!
!
!
!
!
interface Loopback0
no ip address
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
ip address 20.113.40.20 255.0.0.0
duplex auto
speed auto
no cdp enable
crypto map FortiMap
!
interface GigabitEthernet0/1
ip address 172.19.58.1 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 172.20.32.0 255.255.255.0 GigabitEthernet0/0 20.113.40.21
!
ip access-list extended FortiAccess
permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
permit ip 20.0.0.0 0.255.255.255 172.20.32.0 0.0.0.255
!
end
FortiGate Config:
config vpn ipsec phase1-interface
edit "IPSEC"
set interface "lan3"
set ike-version 2
set local-gw 20.113.40.21
set keylife 3600
set peertype any
set net-device disable
set proposal aes256-sha384
set localid "Forti"
set dhgrp 5
set nattraversal disable
set remote-gw 20.113.40.20
set psksecret ENC goAzR4xNf31WsVq6AP0WfRzZobw8jpJh4PTTInPYicYLgQx1qWB7AAAdl+hPWT0if/kTNJBGPgnJhb13fj2PSzhqS56m7d5DaqT2sZyiXlH1nVprjpDQ/NX3AsRSShh2V7CvKnENvVl3CvPo2z2NYg0GOiU/CjcLZIFD9MMM06hGRPd7f9c6aEBi5h5YrCrRYv4/vA==
next
end
config vpn ipsec phase2-interface
edit "PHASE2"
set phase1name "IPSEC"
set proposal aes256-sha384
set dhgrp 5
set keepalive enable
set keylifeseconds 3600
set src-subnet 172.20.32.2 255.255.255.255
set dst-subnet 172.19.58.2 255.255.255.255
next
end
I would be very thankful if you informed about any possible mistakes and its solution
Martin
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 03:34 AM
Hello,
most likely, the ciphers are not supported on either platform. Try sha256 instead of 384 (see the lines marked in bold
Cisco Config:
Current configuration : 5883 bytes
!
redundancy
!
crypto ikev2 proposal FortiProposal
encryption aes-cbc-256
--> integrity sha256
group 5
!
crypto ikev2 policy FortiPolicy
match address local 20.113.40.20
proposal FortiProposal
!
crypto ikev2 keyring FortiKeyring
peer Forti
address 20.113.40.21 255.0.0.0
pre-shared-key pskey
!
crypto ikev2 profile FortiProfile
match identity remote address 20.113.40.21 255.255.255.255
identity local address 20.113.40.20
authentication remote pre-share
authentication local pre-share
keyring local FortiKeyring
!
no crypto ikev2 http-url cert
!
crypto logging session
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 periodic
!
crypto ipsec security-association idle-time 60
!
--> crypto ipsec transform-set FortiTransform esp-aes 256 esp-sha256-hmac
mode tunnel
no crypto ipsec nat-transparency udp-encapsulation
!
crypto map FortiMap 10 ipsec-isakmp
set peer 20.113.40.21
set transform-set FortiTransform
set pfs group5
set ikev2-profile FortiProfile
match address FortiAccess
!
interface Loopback0
no ip address
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
ip address 20.113.40.20 255.0.0.0
duplex auto
speed auto
no cdp enable
crypto map FortiMap
!
interface GigabitEthernet0/1
ip address 172.19.58.1 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 172.20.32.0 255.255.255.0 GigabitEthernet0/0 20.113.40.21
!
ip access-list extended FortiAccess
permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
permit ip 20.0.0.0 0.255.255.255 172.20.32.0 0.0.0.255
!
end
FortiGate Config:
config vpn ipsec phase1-interface
edit "IPSEC"
set interface "lan3"
set ike-version 2
set local-gw 20.113.40.21
set keylife 3600
set peertype any
set net-device disable
--> set proposal aes256-sha256
set localid "Forti"
set dhgrp 5
set nattraversal disable
set remote-gw 20.113.40.20
set psksecret ENC goAzR4xNf31WsVq6AP0WfRzZobw8jpJh4PTTInPYicYLgQx1qWB7AAAdl+hPWT0if/kTNJBGPgnJhb13fj2PSzhqS56m7d5DaqT2sZyiXlH1nVprjpDQ/NX3AsRSShh2V7CvKnENvVl3CvPo2z2NYg0GOiU/CjcLZIFD9MMM06hGRPd7f9c6aEBi5h5YrCrRYv4/vA==
next
end
!
config vpn ipsec phase2-interface
edit "PHASE2"
set phase1name "IPSEC"
--> set proposal aes256-sha256
set dhgrp 5
set keepalive enable
set keylifeseconds 3600
set src-subnet 172.20.32.2 255.255.255.255
set dst-subnet 172.19.58.2 255.255.255.255
next
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 04:30 AM
Changed it now and ping still doenst work.
When i do: debug crypto ipsec, debug crypto isakmp, debug crypto ikv2.
i get this output:
000047: *Aug 17 21:37:29.059 MET: IPSEC:(SESSION ID = 1) (key_engine) request timer fired: count = 4,
(identity) local= 20.113.40.20:0, remote= 20.113.40.21:0,
local_proxy= 172.19.58.0/255.255.255.0/256/0,
remote_proxy= 172.20.32.0/255.255.255.0/256/0
000048: *Aug 17 21:37:29.059 MET: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 20.113.40.20:500, remote= 20.113.40.21:500,
local_proxy= 172.19.58.0/255.255.255.0/256/0,
remote_proxy= 172.20.32.0/255.255.255.0/256/0,
protocol= ESP, transform= esp-aes 256 esp-sha256-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
000049: *Aug 17 21:37:29.059 MET: IKEv2:% Getting preshared key from profile keyring FortiKeyring
000050: *Aug 17 21:37:29.059 MET: IKEv2:% Matched peer block 'Forti'
000051: *Aug 17 21:37:29.059 MET: IKEv2:Searching Policy with fvrf 0, local address 20.113.40.20
000052: *Aug 17 21:37:29.059 MET: IKEv2:Found Policy 'FortiPolicy'
000053: *Aug 17 21:37:29.059 MET: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 5
000054: *Aug 17 21:37:29.059 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Request queued for computation of DH key
000055: *Aug 17 21:37:29.059 MET: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000056: *Aug 17 21:37:29.059 MET: IKEv2:IKEv2 initiator - no config data to send in IKE_SA_INIT exch
000057: *Aug 17 21:37:29.059 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Generating IKE_SA_INIT message
000058: *Aug 17 21:37:29.059 MET: IKEv2:(SESSION ID = 1,SA ID = 1):IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
AES-CBC SHA256 SHA256 DH_GROUP_1536_MODP/Group 5
000059: *Aug 17 21:37:29.063 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Sending Packet [To 20.113.40.21:500/From 20.113.40.20:500/VRF i0:f0]
Initiator SPI : CCDFD43F86C5045C - Responder SPI : 0000000000000000 Message id: 0
IKEv2 IKE_SA_INIT Exchange REQUEST
Payload contents:
SA KE N VID VID VID VID
000060: *Aug 17 21:37:29.063 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Insert SA
000061: *Aug 17 21:37:29.063 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Received Packet [From 20.113.40.21:500/To 20.113.40.20:500/VRF i0:f0]
Initiator SPI : CCDFD43F86C5045C - Responder SPI : 528DE8907CF30F1C Message id: 0
IKEv2 IKE_SA_INIT Exchange RESPONSE
Payload contents:
SA KE N
000062: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Processing IKE_SA_INIT message
000063: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Verify SA init message
000064: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Processing IKE_SA_INIT message
000065: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Checking NAT discovery
000066: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):NAT not found
000067: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 5
000068: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Request queued for computation of DH secret
000069: *Aug 17 21:37:29.067 MET: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000070: *Aug 17 21:37:29.067 MET: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Calculate SKEYSEED and create rekeyed IKEv2 SA
000071: *Aug 17 21:37:29.067 MET: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] SKEYSEED calculation and creation of rekeyed IKEv2 SA PASSED
000072: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Completed SA init exchange
000073: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Check for EAP exchange
000074: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Generate my authentication data
000075: *Aug 17 21:37:29.067 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Use preshared key for id 20.113.40.20, key len 6
000076: *Aug 17 21:37:29.067 MET: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
000077: *Aug 17 21:37:29.071 MET: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
000078: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Get my authentication method
000079: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):My authentication method is 'PSK'
000080: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Check for EAP exchange
000081: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Generating IKE_AUTH message
000082: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Constructing IDi payload: '20.113.40.20' of type 'IPv4 address'
000083: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
AES-CBC SHA256 Don't use ESN
000084: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Building packet for encryption.
Payload contents:
VID IDi AUTH SA TSi TSr NOTIFY(INITIAL_CONTACT) NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
000085: *Aug 17 21:37:29.071 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Sending Packet [To 20.113.40.21:500/From 20.113.40.20:500/VRF i0:f0]
Initiator SPI : CCDFD43F86C5045C - Responder SPI : 528DE8907CF30F1C Message id: 1
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
ENCR
000086: *Aug 17 21:37:29.075 MET: IKEv2-ERROR:Couldn't find matching SA: Detected an invalid IKE SPI
000087: *Aug 17 21:37:29.075 MET: IKEv2:(SESSION ID = 0,SA ID = 0):Received Packet [From 20.113.40.21:500/To 20.113.40.20:500/VRF i0:f0]
Initiator SPI : 06E42793251935C0 - Responder SPI : C0D5D5833194B5BB Message id: 0
IKEv2 INFORMATIONAL Exchange REQUEST
000088: *Aug 17 21:37:29.075 MET: IKEv2-ERROR:: A supplied parameter is incorrect
000089: *Aug 17 21:37:29.079 MET: IKEv2-ERROR:Couldn't find matching SA: Detected an invalid IKE SPI
000090: *Aug 17 21:37:29.079 MET: IKEv2:(SESSION ID = 0,SA ID = 0):Received Packet [From 20.113.40.21:500/To 20.113.40.20:500/VRF i0:f0]
Initiator SPI : 06E42793251935C0 - Responder SPI : C0D5D5833194B5BB Message id: 0
IKEv2 INFORMATIONAL Exchange REQUEST
000091: *Aug 17 21:37:29.079 MET: IKEv2-ERROR:: A supplied parameter is incorrect
000092: *Aug 17 21:37:29.079 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Received Packet [From 20.113.40.21:500/To 20.113.40.20:500/VRF i0:f0]
Initiator SPI : CCDFD43F86C5045C - Responder SPI : 528DE8907CF30F1C Message id: 1
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
IDr AUTH SA TSi TSr
000093: *Aug 17 21:37:29.079 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Process auth response notify
000094: *Aug 17 21:37:29.079 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Searching policy based on peer's identity 'Forti' of type 'FQDN'
000095: *Aug 17 21:37:29.083 MET: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):: Failed to locate an item in the database
000096: *Aug 17 21:37:29.083 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Verification of peer's authentication data FAILED
000097: *Aug 17 21:37:29.083 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Auth exchange failed
000098: *Aug 17 21:37:29.083 MET: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):: Auth exchange failed
000099: *Aug 17 21:37:29.083 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Abort exchange
000100: *Aug 17 21:37:29.083 MET: IKEv2:(SESSION ID = 1,SA ID = 1):Deleting SA
000101: *Aug 17 21:37:59.059 MET: IPSEC:(SESSION ID = 1) (key_engine) request timer fired: count = 5,
(identity) local= 20.113.40.20:0, remote= 20.113.40.21:0,
local_proxy= 172.19.58.0/255.255.255.0/256/0,
remote_proxy= 172.20.32.0/255.255.255.0/256/0
Still, thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 04:38 AM
Hello,
to be honest, I have seen this quite often: the 'legacy' crypto maps configured on a Cisco IOS router often don't work. As soon as you use a VTI, it all works. A configuration guide is linked below, it is not really difficult to implement...
https://kb.fortinet.com/kb/documentLink.do?externalID=FD34846
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 04:39 AM
Hello @Kronberger_Industries ,
on the Cisco side your ACL for interesting traffic is wrong:
ip access-list extended FortiAccess
permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
>>> permit ip 20.0.0.0 0.255.255.255 172.20.32.0 0.0.0.255
I would remove the second line as the external IP addresses fall in that address block.
Remember the ACLs for interesting traffic should describe traffic between internal LAN subnets and they should be a mirror of each other just changing source and destination addresses.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 01:07 PM
You are defining the interesting traffic differently on the Cisco router than you are on the Fortigate.
// Current Cisco router
ip access-list extended FortiAccess
permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
permit ip 20.0.0.0 0.255.255.255 172.20.32.0 0.0.0.255
// Current Fortigate
set src-subnet 172.20.32.2 255.255.255.255
set dst-subnet 172.19.58.2 255.255.255.255
These need to be a mirror of each other, other wise you'll fail to establish IPSec SA.
Change the Fortigate to use the /24 network rather the /32 host.
set src-subnet 172.20.32.0 255.255.255.0
set dst-subnet 172.19.58.0 255.255.255.0
As already mentioned you can also remove the second line from the ACL on the cisco router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 12:43 AM
Changed what you've recommended, when i try to Ping throught the Tunnel it still shows as UP on the FortiGate and on the cisco i get those errors with the "show crypto ikev2 diagnose errors" :
Error(5): A supplied parameter is incorrect
-Traceback= 36905E1Cz 3690F0D4z 3690F3B0z 36912F44z 36913410z 3695A96Cz 3695AA50z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(4533): Failed to locate an item in the database
-Traceback= 3690D5C8z 36912F44z 36913410z 3695A96Cz 3695AA50z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(4533): Failed to match profile sent by IPSEC
-Traceback= 369C5DCCz 369482A0z 3690D5C8z 36912F44z 36913410z 3695A96Cz 3695AA50z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(8): Detected an invalid IKE SPI
-Traceback= 3695A110z 3695AA50z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(4528): Failed to retrieve issuer public key hash list
-Traceback= 36930328z 3690B924z 36912F44z 36913410z 3692A448z 3692ACCCz 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(4528): Failed to retrieve issuer public key hash list
-Traceback= 3690B628z 36912F44z 36913410z 3695A96Cz 3695AA50z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Error(27): A supplied parameter is incorrect
-Traceback= 36905E1Cz 3690F0D4z 3690F3B0z 36912F44z 36913410z 369276C0z 369236A0z 36989DF0z 30032B5Cz 30032B40z
Thanks for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 01:09 AM - edited 08-18-2021 01:29 AM
Hello,
I was going through some Forigate forum posts, and somebody suggested to add the line marked in bold to the Cisco profile:
crypto ikev2 profile FortiProfile
match identity remote address 20.113.40.21 255.255.255.255
identity local address 20.113.40.20
authentication remote pre-share
authentication local pre-share
keyring local FortiKeyring
--> no config-exchange request
If that doesn't help, I still think the VTI will work. I have seen the same issue with AWS, Palo Alto, SonicWall and I think even pfSense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 04:24 AM
Hello,
thanks for the help btw. I have tried that now and it doesn't work either. Now i configured the VTI but its still not working. I think i forgot something. Maybe you got an Idea.
My new cisco config:
! crypto ikev2 proposal FortiProposal encryption aes-cbc-256 integrity sha256 group 5 ! crypto ikev2 policy FortiPolicy proposal FortiProposal ! crypto ikev2 keyring FortiKeyring peer Forti address 20.113.40.21 255.0.0.0 pre-shared-key martin ! ! ! crypto ikev2 profile FortiProfile match identity remote address 20.113.40.21 255.0.0.0 identity local address 20.113.40.20 authentication remote pre-share authentication local pre-share keyring local FortiKeyring dpd 10 2 on-demand no config-exchange request ! no crypto ikev2 http-url cert ! ! ! crypto logging session crypto isakmp invalid-spi-recovery crypto isakmp keepalive 30 periodic ! crypto ipsec security-association idle-time 60 ! crypto ipsec transform-set FortiTransform esp-aes 256 esp-sha256-hmac mode tunnel ! crypto ipsec profile FortiIPsecProfile set transform-set FortiTransform set pfs group5 set ikev2-profile FortiProfile ! ! ! crypto map FortiMap 10 ipsec-isakmp set peer 20.113.40.21 set transform-set FortiTransform set pfs group5 set ikev2-profile FortiProfile match address FortiAccess ! ! ! ! ! interface Loopback0 no ip address ! interface Tunnel0 ip address 30.113.40.20 255.255.255.0 ip ospf mtu-ignore load-interval 30 tunnel source 20.113.40.20 tunnel mode ipsec ipv4 tunnel destination 20.113.40.21 tunnel protection ipsec profile FortiIPsecProfile ! interface Embedded-Service-Engine0/0 no ip address shutdown ! interface GigabitEthernet0/0 ip address 20.113.40.20 255.0.0.0 duplex auto speed auto ! interface GigabitEthernet0/1 ip address 172.19.58.1 255.255.255.0 duplex auto speed auto ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto ! ! router eigrp 2704 network 172.19.59.192 0.0.0.63 redistribute connected redistribute static route-map Aussenstationen ! router ospf 10 network 30.113.40.0 0.0.0.255 area 0 ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ip route 172.20.32.0 255.255.255.0 Tunnel0 ip route 172.20.32.0 255.255.255.0 GigabitEthernet0/0 20.113.40.21 ! ip access-list extended FortiAccess permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
My new FortiGate config:
config vpn ipsec phase1-interface
edit "IPSEC"
set interface "lan3"
set ike-version 2
set keylife 3600
set peertype any
set net-device disable
set proposal aes256-sha256
set localid "Forti"
set dhgrp 5
set nattraversal disable
set remote-gw 20.113.40.20
set psksecret ENC 71U8GsFvtt+760+ENWoiXK/JgdycyJuKtD8GhJHeE2MG4yIlIGaFKJM/klrF9Zs9NkAs45JE1kLRgW65D3I3kVLoH1Vaj+nkb9K9rxVFQQ1NoEvbqGXhyQedeolOS+0xh8OEMb4SScIXXg8yAplLh6cfrvQOqDiY0qzDOXC68nQi1Eo5wO5Q6PAmhVxnbimVQy9SiA==
next
end
config vpn ipsec phase2-interface
edit "PHASE2"
set phase1name "IPSEC"
set proposal aes256-sha256
set dhgrp 5
set keepalive enable
set keylifeseconds 3600
set src-subnet 172.20.32.0 255.255.255.0
set dst-subnet 172.19.58.0 255.255.255.0
next
end
config system interface
edit "IPSEC"
set vdom "root"
set ip 30.113.40.20 255.255.255.255
set allowaccess ping https ssh
set type tunnel
set remote-ip 30.113.40.21 255.0.0.0
set alias "IPsec_Tunnel"
set snmp-index 8
set interface "lan3"
next
end
config firewall policy
edit 1
set name "FORTI_TO_CISCO"
set uuid e4251f92-ff66-51eb-1903-16e6ada83278
set srcintf "lan"
set dstintf "IPSEC"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set name "CISCO_TO_FORTI"
set uuid f9aef270-ff66-51eb-80c4-9472f80b5da1
set srcintf "IPSEC"
set dstintf "lan"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
config router ospf
config area
edit 0.0.0.0
next
end
config ospf-interface
edit "IPSEC"
set interface "IPSEC"
set mtu-ignore enable
set network-type point-to-point
next
end
config network
edit 1
set prefix 30.113.40.0 255.255.255.0
next
end I feel like i forgot something, but I can't figure out what it is.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 05:25 AM
Hello,
at first glance, the static routing doesn't look right. Make the changes marked in bold. I check for other stuff as well, but this is the first thing I noticed:
crypto ikev2 proposal FortiProposal
encryption aes-cbc-256
integrity sha256
group 5
!
crypto ikev2 policy FortiPolicy
proposal FortiProposal
!
crypto ikev2 keyring FortiKeyring
peer Forti
address 20.113.40.21 255.0.0.0
pre-shared-key martin
!
crypto ikev2 profile FortiProfile
match identity remote address 20.113.40.21 255.0.0.0
identity local address 20.113.40.20
authentication remote pre-share
authentication local pre-share
keyring local FortiKeyring
dpd 10 2 on-demand
no config-exchange request
!
no crypto ikev2 http-url cert
!
crypto logging session
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 periodic
!
crypto ipsec security-association idle-time 60
!
crypto ipsec transform-set FortiTransform esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile FortiIPsecProfile
set transform-set FortiTransform
set pfs group5
set ikev2-profile FortiProfile
!
--> no crypto map FortiMap 10 ipsec-isakmp
set peer 20.113.40.21
set transform-set FortiTransform
set pfs group5
set ikev2-profile FortiProfile
match address FortiAccess
!
interface Loopback0
no ip address
!
interface Tunnel0
ip address 30.113.40.20 255.255.255.0
ip ospf mtu-ignore
load-interval 30
tunnel source 20.113.40.20
tunnel mode ipsec ipv4
tunnel destination 20.113.40.21
tunnel protection ipsec profile FortiIPsecProfile
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
ip address 20.113.40.20 255.0.0.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
ip address 172.19.58.1 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
!
router eigrp 2704
network 172.19.59.192 0.0.0.63
redistribute connected
redistribute static route-map Aussenstationen
!
router ospf 10
network 30.113.40.0 0.0.0.255 area 0
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
--> ip route 172.20.32.0 255.255.255.0 Tunnel0
--> ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 20.113.40.21
!
ip access-list extended FortiAccess
permit ip 172.19.58.0 0.0.0.255 172.20.32.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 05:52 AM
Also, and maybe I have been looking at this for too long, on the Fortigate side you have the tunnel IP addresses switched around:
config system interface
edit "IPSEC"
set vdom "root"
set ip 30.113.40.20 255.255.255.255 <-- this needs to be 30.113.40.21
set allowaccess ping https ssh
set type tunnel
set remote-ip 30.113.40.21 255.0.0.0 <-- this needs to be 30.113.30.20
set alias "IPsec_Tunnel"
set snmp-index 8
set interface "lan3"
next
end
Cisco
interface Tunnel0
ip address 30.113.40.20 255.255.255.0
ip ospf mtu-ignore
load-interval 30
tunnel source 20.113.40.20
tunnel mode ipsec ipv4
tunnel destination 20.113.40.21
tunnel protection ipsec profile FortiIPsecProfile
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 07:49 AM - edited 08-18-2021 07:50 AM
Hey,
now its finaly working! I changed what you've suggested, plus:
Forti:
config firewall policy
edit 1
set name "FORTI_TO_CISCO"
set uuid e4251f92-ff66-51eb-1903-16e6ada83278
set srcintf "lan2"
set dstintf "IPSEC"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set name "CISCO_TO_FORTI"
set uuid f9aef270-ff66-51eb-80c4-9472f80b5da1
set srcintf "IPSEC"
set dstintf "lan2"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
Cisco:
crypto ikev2 profile FortiProfile
match identity remote any
identity local fqdn zentrale
authentication remote pre-share
authentication local pre-share
keyring local FortiKeyring
dpd 10 2 on-demand
no config-exchange request
Thanks for the help, I really appreciate it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 08:32 AM
Great ! Good stuff, and we also have a reference for future users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 11:10 AM
Actually, can you post the full working configs of both the Cisco and the Fortigate, for reference ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2021 01:02 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide