- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ISP/s -> L2 Switch -> Firewall -> LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISP/s -> L2 Switch -> Firewall -> LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2018 08:34 PM - edited 03-05-2019 10:58 AM
Hi,
I would like to seek help with my proposed network.
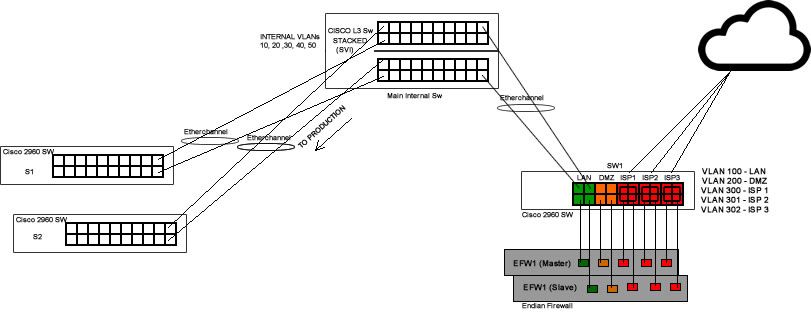
It consist of Cisco Switches (L2/L3) and Endian Firewalls. I know, I have the wrong equipment and wrong forum but I want to ask if this topology is valid or ask if someone already experience this type of network.
Here's my topology.
In order for my Endian Firewall to have fail-over, it needs a managed switch.
In my SW1, I've created a VLANs for the LAN, DMZ and separate VLANs for each ISP.
These VLANs were isolated on each other.
I've already tried this with the actual testing equipment and it works but with 1 ISP only.
Routing and Switching also works within the internal also works also with fail-overs.
My questions is, with my managed switch (SW1) that connects with the ISPs, does it have any issues if I will add 2 or more ISPs on it? Different ISP, different VLAN.
Will it have any issues on the Switch? VLANs? Broadcast Domain?
Does normal VLAN works or Private VLAN?
Please let me know your know thoughts and questions.
Thank you in advance.
- Labels:
-
LAN Switching
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2018 11:08 PM
As long as it is segmented with different VLAN - you are ok.
On top of that you need to take care of routing, how you want to route the outgoing traffic to ISP1 /2/3 so on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2018 11:26 PM
Thanks for the advise.
Anyway, the Endian Firewall will take care all the routing of internal VLANs per ISP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 09:38 AM
I am sure you have FW facing internet side which protects. you only need to VLAN Extended.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 10:58 AM
Hello
as the main internal switch is performing inter-vlan routing why not just have your sw1 as a host switch thus having no L3 whatsoever and only providing the physical and transparent connectivity for your isps and Fw ?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 06:04 PM
Hi Paul,
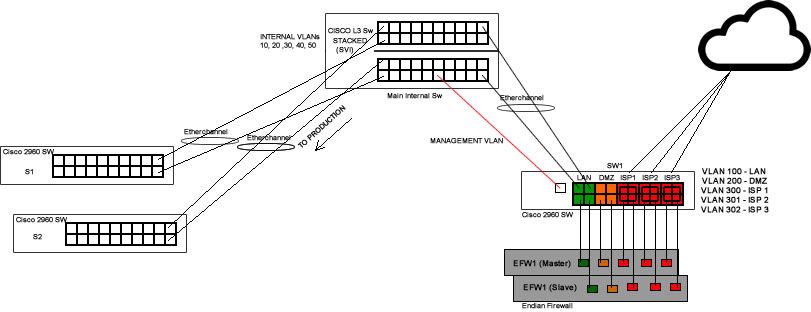
Actually, I did it but on the Sw1 and Main Internal Sw. I connect it with a trunk line and only allow the management VLAN to pass.
But not on the transparent mode. I configured the Main internal Sw as VTP Server for the internal switches and the Sw1 as a VTP Server on its own.
If I were to ask, what would be the best? is it on the Transparent Mode or a Server on its own?
Thanks again in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 12:06 AM
Helloi
have your firewalll connect directly into the internal switch and then have the isps and firewall connect via sw1
Then you can totally wipe sw1 and just use it as a transparent host for physical connectivity?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 01:34 AM
Hi Paul,
There is a problem connecting the firewall into the internal switch.
The Endian Firewall doesn't support etherchannel and its fail-over wouldn't work.
Already tried it but only one cable will work. As per its documentations, it will need a managed switch and own VLAN.
Please check it on my diagram.
It my L3 Sw, I configured the etherchannel with IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 07:46 AM - edited 10-12-2018 07:52 AM
Hello
@daniel wrote:There is a problem connecting the firewall into the internal switch.
The Endian Firewall doesn't support etherchannel and its fail-over wouldn't work.
Why does it need ether-channel ,Surely two ports in the same vlan is all that is required for the HA FO links, Now even if you dont want to use the internal switch for HA your dmz can use it instead Either way I cannot see anything negating you defaulting that sw1 and just using it transparently
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2018 08:43 PM
Hi Paul,
I think it is better to use the Sw1 for the HA / FO links.
Directing the 2 LAN at the internal switch may be good but HA/FO will not work that way unless they're on a separate or segmented VLAN.
For now I will not make any changes on the diagram.
I will keep on testing and will find any other issues.
Thanks in Advanced :)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide