- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Issue with Routing over Dynamic VTI
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2020 11:23 AM
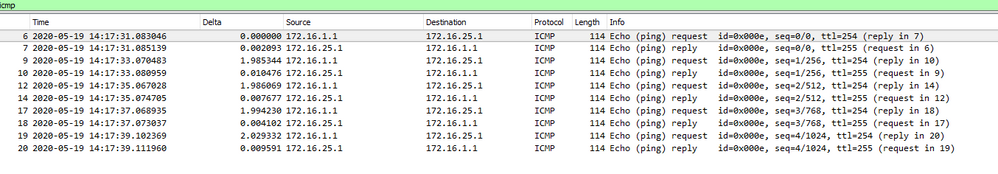
In my lab, I have a Dynamic VTI established between two routers. I'm exchanging routes via bgp between the two routers. Off my Branch VPN router (VPN1), I have a router(Node8) with a loopback and a point-to-point interface to the VPN1. My DVTI is up, and I can ping networks that are directly connected to the routers. I'm unable to ping anything off the routers even though I'm exchanging routes successfully. After looking at pcaps, it appears the return traffic is not getting re-encrypted on the branch router.
Ping from MVPN1 to VPN1:
mvpn1#ping 172.16.25.2 source loopback 500
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.25.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/43/52 ms
Ping from MVPN1 to Node8:
mvpn1#ping 172.16.25.1 source loopback 500
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.25.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.2
.....
Success rate is 0 percent (0/5)
Capture on VPN1 ETH1/0 interface:
My topology:
VPN1 is the branch vpn router and MVPN1 is the remote router. Router Hotspot is supposed to emulate a mobile hotspot performing NAT and DHCP. I'm translating the eth1/1 interface of MVPN1 to 8.8.8.8.
Configs:
VPN1:
crypto ikev2 proposal PROP
encryption aes-cbc-128
integrity sha256
group 19
crypto ikev2 policy POLICY
proposal PROP
crypto ikev2 profile PROFILE
match certificate mycertmap
identity local dn
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
dpd 30 10 periodic
aaa authorization group cert list default default
virtual-template 1
crypto ipsec transform-set TS esp-aes esp-sha256-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set TS
set ikev2-profile PROFILE
responder-only
interface Virtual-Template1 type tunnel
ip unnumbered Loopback500
tunnel source Ethernet1/1
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile IPSEC_PROFILE shared
end
router eigrp 100
network 172.16.1.0 0.0.0.255
network 172.16.25.0 0.0.0.255
redistribute bgp 6128 metric 100000 10 255 1 1500
router bgp 6128
bgp log-neighbor-changes
redistribute eigrp 100
neighbor 5.5.5.5 remote-as 3128
neighbor 5.5.5.5 ebgp-multihop 2
neighbor 5.5.5.5 distribute-list deny_1918 out
neighbor 192.168.1.2 remote-as 65535
neighbor 192.168.1.2 ebgp-multihop 255
neighbor 192.168.1.2 soft-reconfiguration inbound
MVPN1:
crypto ikev2 proposal PROP
encryption aes-cbc-128
integrity sha256
group 19
crypto ikev2 policy POLICY
proposal PROP
crypto ikev2 profile PROFILE
match certificate mycertmap
identity local dn
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint CA
dpd 30 10 periodic
aaa authorization group cert list default default
crypto ipsec transform-set TS esp-aes esp-sha256-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set TS
set ikev2-profile PROFILE
interface Tunnel1
ip unnumbered Loopback500
tunnel source Ethernet1/1
tunnel mode ipsec ipv4
tunnel destination 1.1.1.1
tunnel protection ipsec profile IPSEC_PROFILE
end
router bgp 65535
bgp log-neighbor-changes
network 25.25.25.25 mask 255.255.255.255
network 172.16.1.0 mask 255.255.255.0
neighbor 192.168.1.1 remote-as 6128
neighbor 192.168.1.1 ebgp-multihop 255
neighbor 192.168.1.1 next-hop-self
Node8
router eigrp 100
network 172.16.25.0 0.0.0.255
network 172.16.26.0 0.0.0.255
Show Commands:
VPN1:
VPN1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 5.5.5.5 to network 0.0.0.0
B* 0.0.0.0/0 [20/0] via 5.5.5.5, 01:31:05
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.1.0/30 is directly connected, Ethernet1/1
L 1.1.1.1/32 is directly connected, Ethernet1/1
5.0.0.0/32 is subnetted, 1 subnets
S 5.5.5.5 [1/0] via 1.1.1.2
7.0.0.0/24 is subnetted, 1 subnets
B 7.7.7.0 [20/0] via 5.5.5.5, 01:30:48
8.0.0.0/24 is subnetted, 1 subnets
B 8.8.8.0 [20/0] via 5.5.5.5, 01:30:48
172.16.0.0/16 is variably subnetted, 4 subnets, 2 masks
B 172.16.1.0/24 [20/0] via 192.168.1.2, 00:11:24
C 172.16.25.0/24 is directly connected, Ethernet1/0
L 172.16.25.2/32 is directly connected, Ethernet1/0
D 172.16.26.1/32 [90/409600] via 172.16.25.1, 00:03:01, Ethernet1/0
192.168.1.0/24 is variably subnetted, 3 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Loopback500
L 192.168.1.1/32 is directly connected, Loopback500
S 192.168.1.2/32 is directly connected, Virtual-Access1
192.168.10.0/32 is subnetted, 1 subnets
C 192.168.10.1 is directly connected, Loopback10
VPN1#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 1.1.1.1/4500 8.8.8.8/4500 none/none READY
Encr: AES-CBC, keysize: 128, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/1809 sec
VPN1#show crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 8.8.8.8 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 96, #pkts encrypt: 96, #pkts digest: 96
#pkts decaps: 105, #pkts decrypt: 105, #pkts verify: 105
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 8.8.8.8
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet1/1
current outbound spi: 0x411F081D(1092552733)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xD6C37685(3603134085)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 3, flow_id: 3, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4302810/1691)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x411F081D(1092552733)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 4, flow_id: 4, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4302825/1691)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
MVPN1:
mvpn1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 10.1.1.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.1.1.1
7.0.0.0/24 is subnetted, 1 subnets
B 7.7.7.0 [20/0] via 192.168.1.1, 00:11:34
8.0.0.0/24 is subnetted, 1 subnets
B 8.8.8.0 [20/0] via 192.168.1.1, 00:11:34
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Ethernet1/1
L 10.1.1.2/32 is directly connected, Ethernet1/1
172.16.0.0/16 is variably subnetted, 4 subnets, 2 masks
C 172.16.1.0/24 is directly connected, Loopback600
L 172.16.1.1/32 is directly connected, Loopback600
B 172.16.25.0/24 [20/0] via 192.168.1.1, 00:11:34
B 172.16.26.1/32 [20/409600] via 192.168.1.1, 00:02:41
192.168.1.0/24 is variably subnetted, 3 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Loopback500
S 192.168.1.1/32 is directly connected, Tunnel1
L 192.168.1.2/32 is directly connected, Loopback500
mvpn1#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 10.1.1.2/4500 1.1.1.1/4500 none/none READY
Encr: AES-CBC, keysize: 128, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/1842 sec
IPv6 Crypto IKEv2 SA
mvpn1#show crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 10.1.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 1.1.1.1 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 102, #pkts encrypt: 102, #pkts digest: 102
#pkts decaps: 93, #pkts decrypt: 93, #pkts verify: 93
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.1.1.2, remote crypto endpt.: 1.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet1/1
current outbound spi: 0xD6C37685(3603134085)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x411F081D(1092552733)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 4, flow_id: 4, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4367379/1748)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xD6C37685(3603134085)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 3, flow_id: 3, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4367391/1748)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Node8:
Show ip route:
D*EX 0.0.0.0/0 [170/284160] via 172.16.25.2, 00:00:16, Ethernet1/0
7.0.0.0/24 is subnetted, 1 subnets
D EX 7.7.7.0 [170/284160] via 172.16.25.2, 00:00:16, Ethernet1/0
8.0.0.0/24 is subnetted, 1 subnets
D EX 8.8.8.0 [170/284160] via 172.16.25.2, 00:00:16, Ethernet1/0
172.16.0.0/16 is variably subnetted, 4 subnets, 2 masks
D EX 172.16.1.0/24 [170/284160] via 172.16.25.2, 00:00:16, Ethernet1/0
C 172.16.25.0/24 is directly connected, Ethernet1/0
L 172.16.25.1/32 is directly connected, Ethernet1/0
C 172.16.26.1/32 is directly connected, Loopback0
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2020 06:20 AM
Thanks for your reply. I was completely out of ideas last night, and I decided to go ahead, and migrate my routers from a dynamip 7200 image to an IOL image, and after doing that everything is working as expected. I made no other changes to my configs. My guess is it was some kind of bug in the dynamips image I was running.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2020 03:37 AM
Hello
It doesseem that your routing is being propergated correctly - Can you post from
VPN and Node 8 :
sh ip protocols
sh ip access-list
MVPN1
traceroute 172.16.25.2 source loopback 500 numeric
traceroute 172.16.25.1 source loopback 500 numeric
Node8
traceroute 172.16.1.1 source loopback 0 numeric
traceroute 172.16.1.1 source eth1/0 numeric
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2020 06:20 AM
Thanks for your reply. I was completely out of ideas last night, and I decided to go ahead, and migrate my routers from a dynamip 7200 image to an IOL image, and after doing that everything is working as expected. I made no other changes to my configs. My guess is it was some kind of bug in the dynamips image I was running.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2020 07:25 AM
Hello
Glad to hear you got it working.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide