- Cisco Community
- Technology and Support
- Networking
- Routing
- Can You post configuration of
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Local host not working because of NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2015 10:14 AM - edited 03-05-2019 12:42 AM
I'm sure this is a simple one but it is beyond me at the moment. I have a host on an inside interface that is going out NAT'd behind the outside interface of an ASA trying to gain access to host on that same outside interface via an ARIN address we have.
See the following in logs:
Deny IP spoof from (97.x.x.226) to 205.x.x.108 on interface outside
The 97.x.x.226 is the outside interface IP address and the 205.x.x.108 is the ARIN address with a static NAT to host on another inside network.
Using Packet Tracer gives me this:
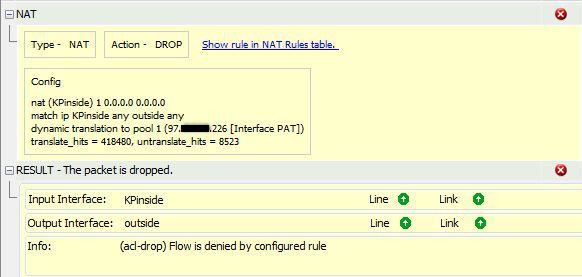
Anti-spoofing is not enabled on any interfaces at the moment.
Any assistance in the right direction would be greatly appreciated. The inside host initiating communication needs to access other sites on the Internet as well so I don't want to mess that functionality up.
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2015 03:17 AM
Can You post configuration of this ASA?
Helping seriously ill children, all together. All information about this, is posted on my blog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2015 07:20 AM
!
ASA Version 8.2(3)
!
hostname GL
names
dns-guard
!
interface Ethernet0/0
description GL-Networks
nameif outside
security-level 0
ip address 97.x.x.226 255.255.255.248 standby 97.x.x.227
!
interface Ethernet0/1
no nameif
no security-level
no ip address
!
interface Ethernet0/1.11
vlan 11
nameif KPinside
security-level 50
ip address 10.16.11.1 255.255.255.0 standby 10.16.11.4
!
interface Ethernet0/1.98
vlan 98
nameif vlan98
security-level 50
ip address 10.64.98.1 255.255.255.0 standby 10.64.98.4
!
interface Ethernet0/1.111
vlan 111
nameif KPdmz
security-level 20
ip address 172.26.11.1 255.255.255.0 standby 172.26.11.4
!
interface Ethernet0/1.192
vlan 192
nameif vlan192
security-level 50
ip address 192.168.1.1 255.255.255.0 standby 192.168.1.4
!
interface Ethernet0/2
nameif vlan205
security-level 50
ip address 10.64.96.1 255.255.255.0 standby 10.64.96.4
!
interface Ethernet0/3
description LAN/STATE Failover Interface
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
boot system disk0:/asa823-k8.bin
ftp mode passive
clock timezone PST -8
dns domain-lookup vlan98
dns domain-lookup vlan192
dns domain-lookup vlan205
dns server-group DefaultDNS
name-server 10.64.97.15
name-server 10.64.97.14
domain-name g.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object-group network GL-ACTUAL
network-object 10.64.96.0 255.255.255.0
network-object 10.64.98.0 255.255.255.0
network-object 10.64.97.0 255.255.255.0
network-object 192.168.1.0 255.255.255.0
object-group network BVT-ACTUAL
network-object 10.6.57.0 255.255.255.0
network-object 10.6.48.0 255.255.255.0
network-object 10.6.51.0 255.255.255.0
network-object 172.29.15.0 255.255.255.0
network-object 172.29.14.0 255.255.255.0
network-object 10.6.245.0 255.255.255.0
network-object 10.6.26.0 255.255.255.0
network-object 10.6.252.0 255.255.255.0
network-object 10.6.7.0 255.255.255.0
network-object 172.29.10.0 255.255.255.0
network-object 172.29.21.0 255.255.255.0
network-object 172.29.6.0 255.255.255.0
network-object 10.6.5.0 255.255.255.0
network-object 10.6.6.0 255.255.255.0
network-object 10.6.1.0 255.255.255.0
network-object 10.6.16.0 255.255.255.0
network-object 10.6.4.0 255.255.255.0
network-object 10.6.31.0 255.255.255.0
network-object 10.6.11.0 255.255.255.0
network-object 10.6.21.0 255.255.255.0
network-object 10.6.33.0 255.255.255.0
object-group network GLOFFICE-ACTUAL
network-object 10.64.99.0 255.255.255.0
network-object 192.168.199.0 255.255.255.0
object-group network DR-ACTUAL
network-object 192.168.254.0 255.255.255.0
network-object 10.6.248.0 255.255.255.0
network-object 10.6.151.0 255.255.255.0
network-object 172.29.215.0 255.255.255.0
network-object 172.29.214.0 255.255.255.0
network-object 172.29.206.0 255.255.255.0
network-object 10.6.205.0 255.255.255.0
network-object 10.6.250.0 255.255.255.0
object-group network KP-PROD
network-object 10.16.11.0 255.255.255.0
object-group network Ext-KP
network-object host 205.x.x.11
object-group service KPRDP
description 10.16.11.202
service-object tcp eq 3389
service-object tcp-udp eq 445
service-object tcp-udp range 1024 65535
service-object tcp eq 135
service-object tcp eq 5504
service-object tcp eq 5722
service-object tcp-udp eq 464
service-object udp eq netbios-dgm
service-object udp eq netbios-ns
service-object tcp eq netbios-ssn
service-object udp eq isakmp
object-group service KPAD
description 10.16.11.203
service-object tcp-udp eq 389
service-object tcp eq ldaps
service-object tcp eq 3268
service-object tcp eq 3269
service-object tcp-udp eq 88
service-object tcp-udp eq domain
service-object tcp eq 42
service-object tcp-udp eq 445
service-object tcp eq smtp
service-object tcp eq 135
service-object tcp eq 5722
service-object udp eq ntp
service-object tcp-udp eq 464
service-object tcp-udp eq 1812
service-object tcp-udp range 1024 65535
service-object udp eq netbios-dgm
service-object udp eq netbios-ns
service-object tcp eq netbios-ssn
service-object udp eq isakmp
object-group icmp-type ping
icmp-object echo
icmp-object echo-reply
object-group network PrivateIPs
network-object 10.0.0.0 255.0.0.0
network-object 172.16.0.0 255.240.0.0
network-object 192.168.0.0 255.255.0.0
object-group network KPRDPaccess
This group contains multiple "network-object host" for external sites I am permitting 10.16.11.202 access to.
object-group service KPRDPservicesAccess
service-object tcp eq www
service-object tcp eq https
object-group network obj_ns1.g.com
network-object 205.x.x.100 255.255.255.255
object-group network obj_ns2.g.com
network-object 205.x.x.101 255.255.255.255
object-group network obj_ws.g.com
network-object 205.x.x.103 255.255.255.255
object-group network obj_images.g.com
network-object 205.x.x.105 255.255.255.255
object-group network obj_allw.com
network-object 205.x.x.106 255.255.255.255
object-group network obj_g.com-haproxy
network-object 205.x.x.107 255.255.255.255
object-group network obj_int.g.com
network-object 205.x.x.108 255.255.255.255
object-group network obj_post.g.com
network-object 205.x.x.109 255.255.255.255
object-group network obj_get.g.com
network-object 205.x.x.110 255.255.255.255
object-group network obj_mail.g.com
network-object 205.x.x.111 255.255.255.255
object-group network obj_mobile.g.com
network-object 205.x.x.112 255.255.255.255
object-group network obj_api-test.g.com
network-object 205.x.x.115 255.255.255.255
object-group network obj_preview.g.com
network-object 205.x.x.117 255.255.255.255
object-group network obj_ci.g.com
network-object 205.x.x.118 255.255.255.255
object-group network obj_demo.g.com
network-object 205.x.x.125 255.255.255.255
object-group network obj_GLport20
group-object obj_get.g.com
group-object obj_int.g.com
group-object obj_post.g.com
object-group network obj_GLport21
group-object obj_get.g.com
group-object obj_int.g.com
group-object obj_post.g.com
object-group network obj_GLport22
group-object obj_preview.g.com
object-group network obj_GLport25
group-object obj_get.g.com
group-object obj_int.g.com
group-object obj_mail.g.com
group-object obj_ns1.g.com
group-object obj_post.g.com
object-group network obj_GLport53
group-object obj_ns1.g.com
group-object obj_ns2.g.com
object-group network obj_GLport80
group-object obj_allw.com
group-object obj_api-test.g.com
group-object obj_demo.g.com
group-object obj_g.com-haproxy
group-object obj_images.g.com
group-object obj_int.g.com
group-object obj_mob.g.com
group-object obj_ns1.g.com
group-object obj_ns2.g.com
group-object obj_prev.g.com
group-object obj_ws.g.com
object-group network obj_GLport443
group-object obj_allw.com
group-object obj_api-test.g.com
group-object obj_ci.g.com
group-object obj_demo.g.com
group-object obj_g.com-haproxy
group-object obj_images.g.com
group-object obj_mob.g.com
group-object obj_ns1.g.com
group-object obj_ns2.g.com
group-object obj_preview.g.com
group-object obj_ws.g.com
object-group network obj_GLport2121
group-object obj_int.g.com
group-object obj_post.g.com
object-group network obj_GLport8080
group-object obj_ci.g.com
access-list outside-access extended permit icmp any 205.x.x.0 255.255.255.0 object-group ping
access-list outside-access remark -- Begin gl
access-list outside-access extended permit tcp any object-group obj_GLport20 eq ftp-data
access-list outside-access extended permit tcp any object-group obj_GLport21 eq ftp
access-list outside-access extended permit tcp any object-group obj_GLport22 eq ssh
access-list outside-access extended permit tcp any object-group obj_GLport25 eq smtp
access-list outside-access extended permit tcp any object-group obj_GLport53 eq domain
access-list outside-access extended permit udp any object-group obj_GLport53 eq domain
access-list outside-access extended permit tcp any object-group obj_GLport80 eq www
access-list outside-access extended permit tcp any object-group obj_GLport443 eq https
access-list outside-access extended permit tcp any object-group obj_GLport2121 eq 2121
access-list outside-access extended permit tcp any object-group obj_GLport8080 eq 8080
access-list outside-access remark -- Begin KP
access-list outside-access extended permit tcp any host 205.x.x.11 eq https
access-list outside-access extended permit tcp any host 205.x.x.12 eq ftp
access-list outside-access extended permit tcp any host 205.x.x.12 eq ftp-data
access-list glprod-bvt extended permit ip object-group GL-ACTUAL object-group BVT-ACTUAL
access-list glprod-bvt extended permit ip host 97.x.x.226 host 10.6.245.6
access-list glprod-bvt extended permit ip object-group KP-PROD object-group BVT-ACTUAL
access-list glprod-bvt extended permit ip object-group KP-PROD 10.50.2.0 255.255.255.0
access-list glprod-bvt extended permit ip host 172.26.11.10 object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip 192.168.1.0 255.255.255.0 192.168.200.0 255.255.255.0
access-list nonat-intervlan extended permit ip 10.64.96.0 255.255.255.0 192.168.200.0 255.255.255.0
access-list nonat-intervlan extended permit ip 10.64.97.0 255.255.255.0 192.168.200.0 255.255.255.0
access-list nonat-intervlan extended permit ip 10.64.98.0 255.255.255.0 192.168.200.0 255.255.255.0
access-list nonat-intervlan extended permit ip object-group GL-ACTUAL object-group GL-ACTUAL
access-list nonat-intervlan extended permit ip 10.64.98.0 255.255.255.0 object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip 10.64.97.0 255.255.255.0 object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip 10.64.96.0 255.255.255.0 object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip object-group GL-ACTUAL object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip object-group GL-ACTUAL object-group GLOFFICE-ACTUAL
access-list nonat-intervlan extended permit ip object-group GL-ACTUAL object-group DR-ACTUAL
access-list nonat-intervlan extended permit ip object-group KP-PROD object-group BVT-ACTUAL
access-list nonat-intervlan extended permit ip object-group KP-PROD 10.50.2.0 255.255.255.0
access-list nonat-intervlan extended permit ip 172.26.11.0 255.255.255.0 object-group KP-PROD
access-list nonat-intervlan extended permit ip object-group KP-PROD 172.26.11.0 255.255.255.0
access-list nonat-intervlan extended permit ip host 172.26.11.10 object-group BVT-ACTUAL
access-list icmp extended permit icmp any any
access-list vlan98-outbound extended permit ip 10.64.98.0 255.255.255.0 any
access-list vlan98-outbound extended permit ip 10.64.98.0 255.255.255.0 object-group BVT-ACTUAL
access-list vlan205-outbound extended permit ip 10.64.96.0 255.255.255.0 any
access-list vlan205-outbound extended permit ip 10.64.96.0 255.255.255.0 object-group BVT-ACTUAL
access-list glprod-gloffice extended permit ip object-group GL-ACTUAL object-group GLOFFICE-ACTUAL
access-list glprodvpn_splitTunnelAcl standard permit 192.168.1.0 255.255.255.0
access-list glprodvpn_splitTunnelAcl standard permit 10.64.96.0 255.255.255.0
access-list glprodvpn_splitTunnelAcl standard permit 10.64.98.0 255.255.255.0
access-list glprodvpn_splitTunnelAcl standard permit 10.64.97.0 255.255.255.0
access-list glprodvpn_splitTunnelAcl standard permit 192.168.199.0 255.255.255.0
access-list outside_cryptomap extended permit ip object-group GL-ACTUAL object-group GLOFFICE-ACTUAL
access-list policy1 extended permit tcp host 10.64.96.5 any eq smtp
access-list policy2 extended permit tcp host 10.64.96.5 any
access-list policy2 extended permit udp host 10.64.96.5 any
access-list gl-dr extended permit ip object-group GL-ACTUAL object-group DR-ACTUAL
access-list KPdmzAccess1 extended permit object-group KPRDP host 172.26.11.10 host 10.16.11.202
access-list KPdmzAccess1 extended permit icmp host 172.26.11.10 host 10.16.11.202 object-group ping
access-list KPdmzAccess1 extended permit object-group KPAD host 172.26.11.10 host 10.16.11.203
access-list KPdmzAccess1 extended permit icmp host 172.26.11.10 host 10.16.11.203 object-group ping
access-list KPdmzAccess1 extended deny ip 172.26.11.0 255.255.255.0 object-group PrivateIPs
access-list KPdmzAccess1 extended permit ip 172.26.11.0 255.255.255.0 any
access-list KPinsideAccess1 extended permit ip host 10.16.11.202 object-group KPRDPaccess
access-list KPinsideAccess1 extended deny object-group KPRDPservicesAccess host 10.16.11.202 any
access-list KPinsideAccess1 extended permit ip 10.16.11.0 255.255.255.0 10.50.2.0 255.255.255.0
access-list KPinsideAccess1 extended deny ip 10.16.11.0 255.255.255.0 object-group PrivateIPs
access-list KPinsideAccess1 extended permit ip 10.16.11.0 255.255.255.0 any
access-list capin extended permit ip host 10.16.11.77 host 205.x.x.108
access-list capin extended permit ip host 205.x.x.108 host 10.16.11.77
access-list capout extended permit ip host 10.16.11.77 host 205.x.x.108
access-list capout extended permit ip host 205.x.x.108 host 10.16.11.77
access-list capin1 extended permit ip host 10.16.11.77 host 205.x.x.108
access-list capin1 extended permit ip host 205.x.x.108 host 10.16.11.77
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu KPinside 1500
mtu vlan98 1500
mtu KPdmz 1500
mtu vlan192 1500
mtu vlan205 1500
ip local pool glprodvpn 192.168.200.1-192.168.200.25 mask 255.255.255.0
failover
failover lan unit primary
failover lan interface FC Ethernet0/3
failover key gl123
failover link FC Ethernet0/3
failover interface ip FC 10.10.10.10 255.255.255.0 standby 10.10.10.20
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-621.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
global (outside) 5 205.x.x.111
nat (KPinside) 0 access-list nonat-intervlan
nat (KPinside) 1 0.0.0.0 0.0.0.0
nat (vlan98) 0 access-list nonat-intervlan
nat (vlan98) 1 0.0.0.0 0.0.0.0
nat (KPdmz) 0 access-list nonat-intervlan
nat (KPdmz) 1 0.0.0.0 0.0.0.0
nat (vlan192) 0 access-list nonat-intervlan
nat (vlan192) 1 0.0.0.0 0.0.0.0
nat (vlan205) 0 access-list nonat-intervlan
nat (vlan205) 5 access-list policy1
nat (vlan205) 1 access-list policy2
nat (vlan205) 1 0.0.0.0 0.0.0.0
static (KPdmz,outside) 205.x.x.11 172.26.11.10 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.118 10.64.96.118 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.100 10.64.96.100 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.101 10.64.96.101 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.103 10.64.96.103 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.105 10.64.96.105 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.106 10.64.96.106 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.107 10.64.96.107 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.108 10.64.96.108 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.109 10.64.96.109 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.110 10.64.96.110 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.112 10.64.96.112 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.115 10.64.96.115 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.117 10.64.96.117 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.125 10.64.96.125 netmask 255.255.255.255
static (vlan205,outside) 205.x.x.111 10.64.96.111 netmask 255.255.255.255
static (KPdmz,outside) 205.x.x.12 172.26.11.88 netmask 255.255.255.255
access-group outside-access in interface outside
access-group KPinsideAccess1 in interface KPinside
access-group KPdmzAccess1 in interface KPdmz
route outside 0.0.0.0 0.0.0.0 97.x.x.225 1
route vlan205 10.64.97.0 255.255.255.0 10.64.96.254 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication ssh console LOCAL
http server enable
http 0.0.0.0 0.0.0.0 vlan98
snmp-server host vlan98 10.6.4.18 community 2bon2b
snmp-server host vlan205 10.64.97.162 community glpublic version 2c
snmp-server location Beaverton, OR
snmp-server contact Ben Maynard <bmaynard@g.com>
snmp-server community glpublic
snmp-server enable traps snmp authentication linkup linkdown coldstart
snmp-server enable traps syslog
snmp-server enable traps ipsec start stop
snmp-server enable traps entity config-change fru-insert fru-remove
snmp-server enable traps remote-access session-threshold-exceeded
sysopt connection tcpmss 1300
sysopt connection preserve-vpn-flows
service resetoutside
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set esp-aes-sha esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set myset esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_dynmap 10 match address glprod-bvt
crypto map outside_dynmap 10 set peer 208.x.x.14
crypto map outside_dynmap 10 set transform-set ESP-3DES-MD5
crypto map outside_dynmap 10 set security-association lifetime seconds 28800
crypto map outside_dynmap 10 set security-association lifetime kilobytes 4608000
crypto map outside_dynmap 20 match address glprod-gloffice
crypto map outside_dynmap 20 set peer 50.x.x.141
crypto map outside_dynmap 20 set transform-set ESP-3DES-MD5
crypto map outside_dynmap 20 set security-association lifetime seconds 28800
crypto map outside_dynmap 20 set security-association lifetime kilobytes 4608000
crypto map outside_dynmap 25 match address gl-dr
crypto map outside_dynmap 25 set peer 97.x.x.210
crypto map outside_dynmap 25 set transform-set ESP-3DES-MD5
crypto map outside_dynmap 25 set security-association lifetime seconds 2147483640
crypto map outside_dynmap 25 set security-association lifetime kilobytes 2147483646
crypto map outside_dynmap 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_dynmap interface outside
crypto isakmp identity hostname
crypto isakmp enable outside
crypto isakmp policy 4
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 11
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto isakmp policy 13
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 21
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh 0.0.0.0 0.0.0.0 vlan98
ssh timeout 30
console timeout 0
management-access vlan98
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable outside
svc enable
tunnel-group-list enable
group-policy DfltGrpPolicy attributes
dns-server value 10.64.97.15 10.64.97.14
vpn-tunnel-protocol IPSec l2tp-ipsec svc webvpn
default-domain value g.com
webvpn
hidden-shares visible
group-policy glprodvpn internal
group-policy glprodvpn attributes
dns-server value 10.64.97.15 10.64.97.14
vpn-tunnel-protocol IPSec svc
split-tunnel-policy tunnelspecified
split-tunnel-network-list value glprodvpn_splitTunnelAcl
split-dns value g.com
group-policy GLPRODVPN internal
group-policy GLPRODVPN attributes
dns-server value 10.64.97.15 10.64.97.14
vpn-tunnel-protocol IPSec l2tp-ipsec svc
split-tunnel-policy tunnelspecified
split-tunnel-network-list value glprodvpn_splitTunnelAcl
default-domain value g.com
split-dns value g.com
webvpn
svc keep-installer installed
svc ask none default svc
tunnel-group 208.x.x.14 type ipsec-l2l
tunnel-group 208.x.x.14 ipsec-attributes
pre-shared-key fbs123
tunnel-group 50.x.x.141 type ipsec-l2l
tunnel-group 50.x.x.141 ipsec-attributes
pre-shared-key gl123
tunnel-group GLPRODVPN type remote-access
tunnel-group GLPRODVPN general-attributes
address-pool glprodvpn
default-group-policy GLPRODVPN
tunnel-group GLPRODVPN webvpn-attributes
group-alias GLPRODVPN enable
tunnel-group glprodvpn type remote-access
tunnel-group glprodvpn general-attributes
address-pool glprodvpn
default-group-policy glprodvpn
tunnel-group glprodvpn ipsec-attributes
pre-shared-key gl123!
tunnel-group 97.x.x.210 type ipsec-l2l
tunnel-group 97.x.x.210 ipsec-attributes
pre-shared-key fbs123
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect h323 h225
inspect h323 ras
inspect rsh
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect ip-options
inspect ftp
inspect icmp
!
service-policy global_policy global
prompt hostname context
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2015 11:49 PM
Hello!
Can You do next:
packet-tracer icmp 10.16.11.10 1 1 8.8.8.8 detailed
And post the tesult
?
Helping seriously ill children, all together. All information about this, is posted on my blog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2015 07:22 AM
That is blocked by design. Only 10.16.11.202 is permitted to access specific IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2015 12:21 PM
Called Cisco support and they resolved the issue.
Thank you for the assist Oleg.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
