- Cisco Community
- Technology and Support
- Networking
- Routing
- OSPF and GRE questions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 09:55 AM
Hi everybody,
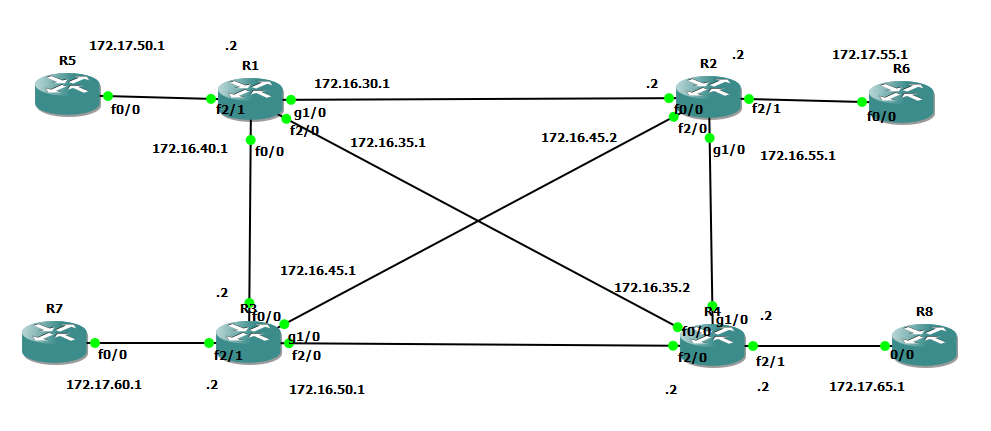
I'm experimenting with OSPF topologies and I have different questions. In my topology, I'm simulating a infraestructure of 4 router connected between them throught "internet" (I have simulated "internet" using OSPF between R1,R2,R3 and R4).
This works, I can do ping between all devices (R5,R6,R7 and R8) but, this is correct? I mean, from external devices (R5,R6,R7 and R8) should can doing ping to internet devices (R1,R2,R3 and R4) using OSPF without any access-list?
R1 OSPF configuration
R1#sh runn | s ospf
router ospf 31
router-id 10.0.10.10
//gre tunnel network
network 10.1.30.0 0.0.0.255 area 0
// all "internet" networks
network 172.16.30.0 0.0.0.255 area 0
network 172.16.35.0 0.0.0.255 area 0
network 172.16.40.0 0.0.0.255 area 0
network 172.17.50.0 0.0.0.255 area 0
network 172.17.55.0 0.0.0.255 area 0
network 172.17.60.0 0.0.0.255 area 0
network 172.17.65.0 0.0.0.255 area 0
R1#
R5 OSPF configuration
router ospf 41
router-id 10.0.50.10
//gre tunnel network
network 10.1.30.0 0.0.0.255 area 0
// all "internet" networks
network 172.17.50.0 0.0.0.255 area 0
network 172.17.55.0 0.0.0.255 area 0
network 172.17.60.0 0.0.0.255 area 0
network 172.17.65.0 0.0.0.255 area 0
With the external routers (R5,R6,R7 and R8) only are connected to next router, is this correct or I need to add all routes (currently works between all devices)
Also, I have add a GRE tunnel between external routers (R5,R6,R7 and R8) and also it's works using ping, but if I do tracer I see that use OSPF route and not GRE tunnel and I thinks that it's incorrect, I mean appears:
R5#traceroute 10.1.30.104 source Tunnel1 (between R5 and R8)
Type escape sequence to abort.
Tracing the route to 10.1.30.104
VRF info: (vrf in name/id, vrf out name/id)
1 172.17.50.2 16 msec 16 msec 20 msec
2 172.16.35.2 48 msec 24 msec 36 msec
3 172.17.65.1 72 msec 56 msec 64 msec
R5#
but I think that would have to appears GRE tunnel ip address (10.1.30.X), is it correct?
A different problem after to mount GRE tunnel between all devices (R5->R6, R5->R7, R5->R8, R6->R5, R6->R7...) with the message
*Jun 30 15:03:07.662: %OSPF-5-ADJCHG: Process 41, Nbr 10.0.80.10 on Tunnel1 from EXSTART to DOWN, Neighbor Down: Too many retransmissions
R5#
*Jun 30 15:04:07.662: %OSPF-5-ADJCHG: Process 41, Nbr 10.0.80.10 on Tunnel1 from DOWN to DOWN, Neighbor Down: Ignore timer expired
I have investigated and all messages talk about MTU problem. I have checked all tunnel interfaces to check if there is a problem with MTU, but all are correctly.
Thanks everybody!!
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 10:28 AM
Hello @sir_ulrick ,
first question there is end to end connectivity even if the external routers are not taking part in OSPF because you advertise in OSPF the links between the internal routers R1-R4 and the external routers R5-R8.
Also note that your configuration is in some aspects excessive R1 should have network commands under router ospf only for those IP subnets that are associated to connected interfaces.
However, this is a minor aspect that does not cause any issue.
routers perform routing by default so they don't need an ACL to permit traffic. (the opposite is true for firewalls usually).
b) how to use a GRE tunnel to put traffic over it ?
the simplest way to use a p2p GRE tunnel is to use a static route that specifies the tunnel as the exit interface
ip route 172.17.65.0 255.255.255.0 tunnel58
c) how to run OSPF over a GRE tunnel ?
In order to be able to run OSPF over a GRE tunnel it is wise to reduce the ip mtu of the tunnel in order to allow OSPF link state database exchange over the tunnel.
These special packets are exchanged when building an adjacency and have the don't fragment bit set.
The GRE overhead is 24 bytes so the following is needed
int tunnel 58
ip mtu 1476
Finally be aware of the risk of recursive routing: the destination and source addresses of the tunnel itself must not be advertised over the tunnel itself or the tunnel will go up/down in cycle.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 02:27 PM
This is a good explanation from @Giuseppe Larosa. I would add one thing to his explanation about how to run OSPF over the GRE tunnel - you need to have a network statement under router ospf that matches the address (or subnet) of the GRE tunnel.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 10:28 AM
Hello @sir_ulrick ,
first question there is end to end connectivity even if the external routers are not taking part in OSPF because you advertise in OSPF the links between the internal routers R1-R4 and the external routers R5-R8.
Also note that your configuration is in some aspects excessive R1 should have network commands under router ospf only for those IP subnets that are associated to connected interfaces.
However, this is a minor aspect that does not cause any issue.
routers perform routing by default so they don't need an ACL to permit traffic. (the opposite is true for firewalls usually).
b) how to use a GRE tunnel to put traffic over it ?
the simplest way to use a p2p GRE tunnel is to use a static route that specifies the tunnel as the exit interface
ip route 172.17.65.0 255.255.255.0 tunnel58
c) how to run OSPF over a GRE tunnel ?
In order to be able to run OSPF over a GRE tunnel it is wise to reduce the ip mtu of the tunnel in order to allow OSPF link state database exchange over the tunnel.
These special packets are exchanged when building an adjacency and have the don't fragment bit set.
The GRE overhead is 24 bytes so the following is needed
int tunnel 58
ip mtu 1476
Finally be aware of the risk of recursive routing: the destination and source addresses of the tunnel itself must not be advertised over the tunnel itself or the tunnel will go up/down in cycle.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2020 02:27 PM
This is a good explanation from @Giuseppe Larosa. I would add one thing to his explanation about how to run OSPF over the GRE tunnel - you need to have a network statement under router ospf that matches the address (or subnet) of the GRE tunnel.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 02:41 AM
Thanks for your reply @Richard Burts,
when you say "you need to have a network statement under router ospf that matches the address (or subnet) of the GRE tunnel" are you talking about that it's necessary to add GRE tunnel network (10.1.30.X) in OSPF process of external routers (R1,R2,R3 and R4) to allow this communication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 02:54 PM
You only need to have the OSPF network statement for the subnet of the GRE tunnel on the 2 routers that are the source and the destination of the GRE tunnel.
You seem to believe that you need OSPF network statements for networks that you want advertised in OSPF. That is not the case. The network statement does not tell OSPF what to advertise. The network statement is used by OSPF to determine which local interfaces will participate in the OSPF process. OSPF looks at each interface on the router/switch and at the network statements. If a network statement matches the interface address then that interface will participate in the OSPF process (will send OSPF hello messages, listen for OSPF hello messages, etc) and OSPF will advertise networks configured on that interface.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2020 08:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2020 10:36 AM
You are welcome. I hope that our explanations have been helpful.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 02:35 AM
Hi @Giuseppe Larosa,
thanks a lot for your complete reply :). I answer about your mail.
"first question there is end to end connectivity even if the external routers are not taking part in OSPF because you advertise in OSPF the links between the internal routers R1-R4 and the external routers R5-R8."
It's correct, but not are included all routes to reach all internal routes in the OSPF 41 process, only routes to allow first internal router (172.17.50.1-> to R1,172.17.55.1 -> to R2,172.17.60.1 -> to R3,172.17.65.1 -> to R4), the rest of the internal routes (172.16.X.X) are not included in the process but currently I can access to this path but I don't understand why. Could be that both OSPF process, internal ("internet") and external (end sites R5,R6,R7 and R8) share all routes?
"Also note that your configuration is in some aspects excessive R1 should have network commands under router ospf only for those IP subnets that are associated to connected interfaces."
Thanks for this clarification, I thought that was necessary to add all OSPF routes necessaries to reach each device in each router. I mean, from each internal router (R1,R2,R3 and R4) must to have all router where I need to go (all internal router to simulate internet, R1,R2,R3 and R4)
"routers perform routing by default so they don't need an ACL to permit traffic. (the opposite is true for firewalls usually)."
I think there was a misunderstanding, sorry. I would like to ask if it's correct that from any external devices (R5,R6,R7 or R8) I can to do ping to any internal device (R1,R2,R3 and R4) without any ACL to block the traffic. I mean if it's normal access to the complete network using OSPF.
"how to use a GRE tunnel to put traffic over it ? the simplest way to use a p2p GRE tunnel is to use a static route that specifies the tunnel as the exit interface
ip route 172.17.65.0 255.255.255.0 tunnel58"
Thanks! I suppose that for this reason tracer didn't work as it should
"In order to be able to run OSPF over a GRE tunnel it is wise to reduce the ip mtu of the tunnel in order to allow OSPF link state database exchange over the tunnel.
These special packets are exchanged when building an adjacency and have the don't fragment bit set.
The GRE overhead is 24 bytes so the following is needed
int tunnel 58
ip mtu 1476"
Really I want to run GRE over OSPF, but with the follow code I'm trying to use OSPF to communicate all GRE tunnels dinamically.
router ospf 41
router-id 10.0.50.10
//gre tunnel network
network 10.1.30.0 0.0.0.255 area 0
In the other way, to avoid problem fragmentation I used ip mtu 1400 in all tunnels, so I suppose that will not be necessary to use 1476, right?
"Finally be aware of the risk of recursive routing: the destination and source addresses of the tunnel itself must not be advertised over the tunnel itself or the tunnel will go up/down in cycle."
Thanks a lot again! I didn't know about this. I was advertising source / destination GRE tunnel ip address (10.1.30.X -> network 10.1.30.0 0.0.0.255 area 0) to allow communication between all end to end devices (R5,R6,R7 and R8). If I cant advertise this, how I can use OSPF to communicate all GRE tunnels? Maybe adding 10.1.30.X network in the external OSPF process (R1,R2,R3 and R4)?
Thanks a lof for your time! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 11:47 PM - edited 07-01-2020 11:59 PM
Hello @sir_ulrick ,
the only way to be sure to avoid recursive routing with OSPF is to use two different OSPF processes:
one process OSPF id 41 will provide the connectivity betweeen the routers
A new OSPF process like OSPF id 51 can be used to be run over the GRE tunnels to advertise for example same LAN interfaces that are not advertised in OSPF process 41.
The reason for using two OSPF processes is the following: OSPF being link state does not support oubound route filtering out an interface, an OSPF router will send all known LSAs over a new link. This is called flooding and it is part of the link state nature of OSPF.
Finally if you are already using ip mtu 1400 you are safe about possible issues with MTU in OSPF over GRE .
As noted also by @Richard Burts you don't need to list all the subnets in OSPF network commands in each router this is not necessary the only needed network commands are those for the interfaces of the router that must participate to the OSPF process.
The objective of a routing protocol is to propagate routing information about prefixes that don't need to be known in advance on each node.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2020 01:02 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide