- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: OSPF leak to area 0
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
OSPF leak to area 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 05:47 PM - edited 03-05-2019 11:11 AM
Hi Guys
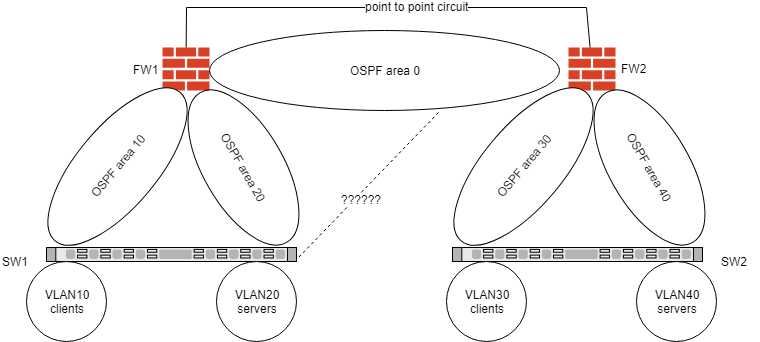
I'm bumping my head for couple of days already - I have the topology below. My VLANs are routed through my firewalls. I'm pushing the traffic towards the firewall via PBR with tracking towards the FW interfaces and that works fine. I have full access from VLAN to VLAN. If FW goes down the switch is performing inter-VLAN routing itself. My goal is to advertise both VLAN10 and VLAN20 to FW2 in case of failure at FW1. I tried setting up SVI on SW1 and adding it to backbone 0 area but in that case traffic from area 30 and 40 is routed directly through SW1. From what i'm reading changes in metrics for SVI in Cisco Nexus switch won't affect traffic.. again the requirement is SW1 to route and advertise its SVIs (10 and 20) to FW2 in case of failure at FW1. Any feedback is greatly appreciated!
Thanks!
Chris
- Labels:
-
LAN Switching
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 05:55 PM
Hi Chris,
Are the two switches (SW1 and SW2) connected to each other? How does SW1 connected to FW2? Please provide more information.
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 07:09 PM
Hi Meheretab
Thanks for your question!
SW1 and SW2 are at different physical locations and are directly connected via point to point line. They are providing the VLAN for the circuit between the FWs and there is one service VLAN for managing network devices.
In order to connect from SW1 to FW2 I must have SVI in SW1 and corresponding SVI in FW2. SW2 is just a medium providing the track.
I hope that doesn't sound too confusing ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 08:25 PM
Hello
@Chris_78 wrote:
I hope that doesn't sound too confusing ..
It does really as as you say , if either FW fails looking at your topology, how do the two site connect, you dont have any other physical connection between those sites or do you?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 07:12 AM - edited 01-17-2019 08:41 AM
Hi Paul
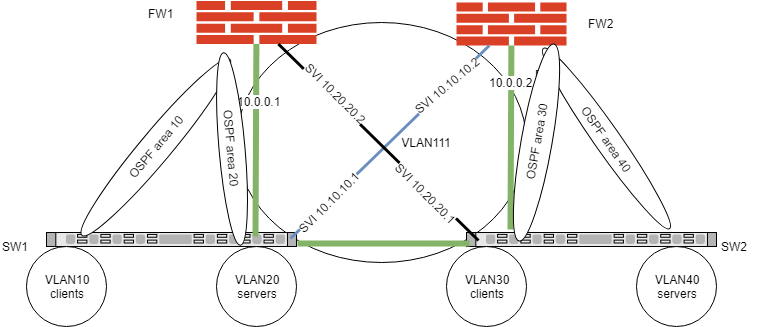
I'm sorry I know it sounds very complicated - below is topology with IPs. The green connection between FW1 and FW2 is currently in use as main circuit between both FWs. I have default route on both switches blue and black connections.
SW1 ip route 0.0.0.0/0 10.10.10.2
SW2 ip route 0.0.0.0/0 10.20.20.2
However these are not in use due to PBR on the switches with tracking pushing all the traffic towards the FWs in each site. If FW1 outage occurs then tracking fails and the SW is routing as usual - default route towards FW2 (blue connection) is in use and that works and Inter-VLAN routing is operational on the SW1. The issue is that I have to advertise VLAN10 and VLAN20 subnets to FW2.
Best
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 10:56 AM
Chris,
It would make it easier if you share configs (at least config of SW1 and SW2). Could you do that while hiding sensitive information?
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 12:32 PM
Hi Meheretab
Below is config from SW1, the same applies to SW2 just different IP scheme.
ip access-list SVI-FW
10 permit ip any any
track 1 ip sla 1 reachability
delay up 10 down 35
ip sla 1
icmp-echo 10.99.99.1 (FW1 interface for tracking)
frequency 100
ip sla schedule 1 life forever start-time now
route-map PBR-CLIENTS permit 10
match ip address SVI-FW
set ip next-hop verify-availability 10.99.99.1 track 1 (OSPF area 10 link)
route-map PBR-Servers permit 10
match ip address SVI-FW
set ip next-hop verify-availability 10.99.99.9 track 1 (OSPF area 20 link)
interface Vlan98
description UPLINK-CLIENTS-FW
no shutdown
no ip redirects
ip address 10.99.99.2/29
no ipv6 redirects
ip ospf network broadcast
ip ospf mtu-ignore
ip router ospf 1 area 10
interface Vlan99
description UPLINK-SERVERS-FW
no shutdown
no ip redirects
ip address 10.99.99.10/29
no ipv6 redirects
ip ospf network broadcast
ip ospf mtu-ignore
ip router ospf 1 area 20
interface Ethernet1/48
description CONNECTION-BETWEEN-SITES
switchport mode trunk
switchport trunk allowed vlan 1-1000
duplex full
speed 100
Interface VLAN111
Description SW1-FW2-BACKUP (this is the backup link from SW1->FW2 that should be used in case of FW1 outage)
no shutdown
ip address 10.10.10.1/29 (not sure if I should keep it in the same subnet or change it to something different and match on FW2) this is the port that I can use to tap into are 0.
interface Vlan10
no shutdown
no ip redirects
ip address 10.18.19.254/23
no ipv6 redirects
ip ospf passive-interface
ip router ospf 1 area 10
ip policy route-map PBR-CLIENTS
no shutdown
interface Vlan20
no shutdown
no ip redirects
ip address 192.168.1.254/24
no ipv6 redirects
ip ospf passive-interface
ip router ospf 1 area 20
ip policy route-map PBR-Servers
no shutdown
ip route 0.0.0.0/0 10.10.10.2
router ospf 1
rfc1583compatibility
area 10 range 10.18.18.0/23
area 20 range 192.168.1.0/24
Thanks!
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 01:43 PM
Can you move the OSPF Area 0 backbone down between the two switches, create another OSPF adjacency from switches to FWs to propagate routes and then redistribute routes via Area 0 backbone on switches? That way, each switch knows about the routes from each side and if the FW fails, move default route to other FW that already knows about the routes from the OSPF adjacent on SW2 and FW2. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2019 02:48 PM
That would work - however Inter-VLAN will happen on the switches which is something we are trying to avoid. We need each VLAN traffic to pass through the FWs so we can inspect the traffic.
The only occasion when we can allow Inter-VLAN routing performed on the switch is when there is FW outage.
Thanks!
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 07:31 AM
You can send to FW for inspection. Port on switch directly connected to FW, access vlan x and then default route to FW. We are doing something very similar on our end so I am familiar with what you are trying to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 10:07 AM - edited 01-18-2019 10:08 AM
Is your gateway for your Access/Clients on your FWs?
In our case access/client gateway is at the SW1 level. They are actually two pairs of NX OS switches at each side - (not showing on the topology) Pair of Nexus switches is providing the gateway redundancy for the clients and servers along with VPC towards the switches south and north for the FW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 09:45 AM
Chris,
What is the problem with configuring all switch-fw links in area 0 and ramping up their costs to something silly? In that case default path to other areas will be via area 0, in which the fw-fw link will be the cheapest and hence selected first. In case it fails, then more expensive link kicks in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 10:20 AM
Thanks Sergei @Sergey Lisitsin
This was my initial idea - The main problem was setting up the metrics, my FWs are Palo Alto and my switches are Nexus 3k - I had some issues getting the correct metrics, I wasn't sure how bandwidth is reacting on SVIs - since these are my main interfaces on the switches.
However I was able to mess up with it last night and pump the metrics/cost for the link between SW and FW and things are looking promising. I wasn't able to fully test anything we have scheduled maintenance tonight so fingers cross :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2019 01:36 PM
Hello
Use ospf costing on the least preferred links for resiliency
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2019 03:03 PM
I've tried that couple of times but the FW doesn't really gets it and keep forward all the traffic to the backup connections hitting the VLANs directly through the switch instead of sending the traffic to the opposite FW.
On the switches I tried bandwidth 10, 100 and 1000 and there was no difference on the FW end - traffic was forwarded through the backup route.
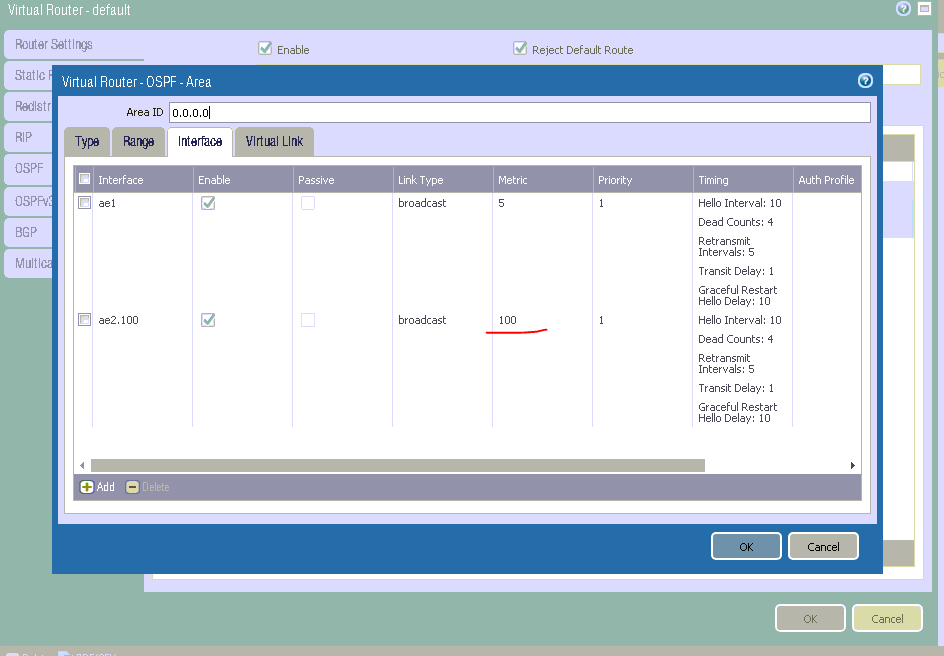
The only way I finally got it to work is by adjusting the cost at FWs to 100 on the backup links FW2-SW1 and FW1-SW2, however I had to have each backup connection in a separate subnet as shown on my topology. Here is also a screenshot from the FWs web interface. Just to wrap things -
Each FW ended with 2 interfaces to area 0: one interface directly connected to the opposite FW (priority route) and one interface to the opposite SW (used as backup) - cost had to be applied on the FW end as shown. For some reason we couldn't manipulate on the SW no matter what values we were applying. Not sure if that matters - but please note these were SVI.
Thanks to everyone for the input!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide