- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: PAT interfers with Web Server Access over L2 tunnel (thought that is was solved)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:32 PM - edited 03-05-2019 11:09 AM
I posted this already but my mistake, it is not solved.
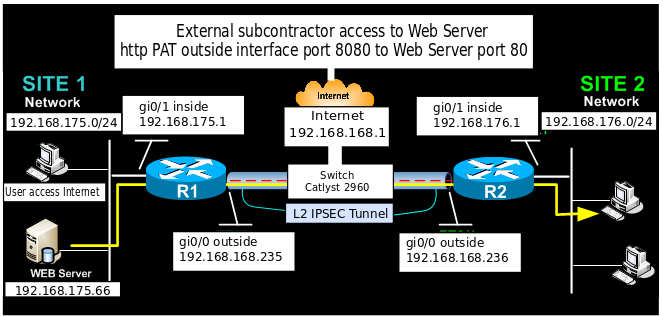
I'm working on a network to accomplish 3 things:
1) NAT overload to the internet
2) L2 tunnels to remote users
3) PAT subcontractors to the Web server on the outside interface with port mapping
PROBLEM STATEMENT
Everything is working except the PAT (ip nat inside source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080) stops the remote user (over the L2 tunnel) from accessing the web server. If I remove t he PAT, Web access for the remote user is good. See the tcpdump on the Web Server showing http coming in but not getting out (note length 0 shows that the hand-shake fails).
QUESTION
How can I change to PAT to allow normal access to the Web Server over L2.
This is the test configuration I'm using to simulate the WAN. Attached are the two configurations and the tcpdump.
Solved! Go to Solution.
- Labels:
-
vEdge Routers
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 01:32 PM - edited 01-07-2019 01:35 PM
I'll work on it a little more and then send all the configs.
At least I can ping the RTR gi0/0.175 now from the switch and a PC on vlan 175. whew!!!!!
I really appreciate you help. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2019 08:03 AM - edited 01-10-2019 09:16 AM
Hi Paul, I implemented you changes that you suggested and I'm happy with the results. Thank you :-)
Got the (((Not Domain_based))) nat working using sub-interfaces. But I have the same PAT issue. I can't browse to the Apache server from the distant end of the L2 tunnel - the PAT (8080 to 80) to Apache interferes with browsing to Apache (regular port 80). See the tcpdump at the end - note that the Apache netstat shows no ESTABLISHED connection to the remote browser. But the remote PC can reach http://192.168.168.235:8080 now because of the change to sub-interfaces
Here are the configurations and a template for adding another remote L2 client.
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!LOCALSW!!!!!!!!!!!!!!!!!!!!!!!!!!!!
interface FastEthernet0/13
description trunk_to_localrtr
switchport encapsulatoin dot1q
switchport trunk allowed vlan 1,175
switchport mode trunk
interface FastEthernet0/14
description local_VM_server
switchport access vlan 175
switchport mode access
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!LOCALRTR!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.236
crypto isakmp key firewallcx address 192.168.168.237
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto map CMAP 76 ipsec-isakmp
set peer 192.168.168.236
set transform-set TS
match address VPN_TRAFFIC_176
crypto map CMAP 77 ipsec-isakmp
set peer 192.168.168.237
set transform-set TS
match address VPN_TRAFFIC_177
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.235 255.255.255.0
ip nat enable
ip virtual-reassembly in
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip nat enable
ip virtual-reassembly in
!
interface GigabitEthernet0/1.175
description INSIDE_175
encapsulation dot1Q 175
ip address 192.168.175.1 255.255.255.0
ip nat enable
!
ip nat source list 175 interface GigabitEthernet0/0 overload
!
! Note this prevents L2 tunnels from browsing to http://192.168.175.66:80
! remote sites have to use http://192.168.168.235:8080
ip nat source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080
!
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 192.168.168.1
ip route 192.168.176.0 255.255.255.0 192.168.168.236
ip route 192.168.177.0 255.255.255.0 192.168.168.237
!
ip access-list extended VPN_TRAFFIC_176
permit tcp 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
ip access-list extended VPN_TRAFFIC_177
permit tcp 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
!
access-list 175 remark -=[Define NAT Service]=-
access-list 175 deny ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
access-list 175 deny ip 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
access-list 175 permit ip 192.168.175.0 0.0.0.255 any
!
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!REMOTESW!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
interface FastEthernet0/1
description trunk_to_remotertr
switchport trunk allowed vlan 1,176
switchport mode trunk
!
interface FastEthernet0/2
description remote_PC_192_168_176_3
switchport access vlan 176
switchport mode access
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!REMOTERTR1!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!
ip dhcp excluded-address 192.168.176.1 192.168.176.2
ip dhcp excluded-address 192.168.176.64 192.168.176.255
!
ip dhcp pool DHCPPOOL
network 192.168.176.0 255.255.255.0
dns-server 192.168.168.200 192.168.168.1
default-router 192.168.176.1
lease 0 2
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.235
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.168.235
set transform-set TS
match address VPN_TRAFFIC
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.236 255.255.255.0
ip virtual-reassembly in
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip virtual-reassembly in
!
interface GigabitEthernet0/1.176
description INSIDE_176
encapsulation dot1Q 176
ip address 192.168.176.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 192.168.168.1
ip route 192.168.175.0 255.255.255.0 192.168.168.235
!
ip access-list extended VPN_TRAFFIC
permit tcp 192.168.176.0 0.0.0.255 192.168.175.0 0.0.0.255
permit ip 192.168.176.0 0.0.0.255 192.168.175.0 0.0.0.255
!
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!REMOTESW2!!!!!!!!!!!!!!!!!!!!!!!!!!!!
interface FastEthernet0/1
description trunk_to_remotertr
switchport trunk allowed vlan 1,177
switchport mode trunk
!
interface FastEthernet0/2
description remote_PC_192_168_177
switchport access vlan 177
switchport mode access
CONFIG!!!!!!!!!!!!!!!!!!!!!!!!!REMOTERTR2!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!
ip dhcp excluded-address 192.168.177.1 192.168.177.2
ip dhcp excluded-address 192.168.177.64 192.168.177.255
!
ip dhcp pool DHCPPOOL
network 192.168.177.0 255.255.255.0
dns-server 192.168.168.200 192.168.168.1
default-router 192.168.177.1
lease 0 2
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.235
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.168.235
set transform-set TS
match address VPN_TRAFFIC
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.237 255.255.255.0
ip virtual-reassembly in
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip virtual-reassembly in
!
interface GigabitEthernet0/1.177
description INSIDE_177
encapsulation dot1Q 177
ip address 192.168.177.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 192.168.168.1
ip route 192.168.175.0 255.255.255.0 192.168.168.235
!
ip access-list extended VPN_TRAFFIC
permit tcp 192.168.177.0 0.0.0.255 192.168.175.0 0.0.0.255
permit ip 192.168.177.0 0.0.0.255 192.168.175.0 0.0.0.255
!
TEMPLATE--------------================REMOTERTR=================--------------------------------
no ip dhcp conflict logging
ip dhcp excluded-address 192.168.177.1 192.168.177.2
ip dhcp excluded-address 192.168.177.64 192.168.177.255
!
ip dhcp pool DHCPPOOL
network 192.168.177.0 255.255.255.0
dns-server 192.168.168.200 192.168.168.1
default-router 192.168.177.1
lease 0 2
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.235
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
ip access-list extended VPN_TRAFFIC
permit tcp 192.168.177.0 0.0.0.255 192.168.175.0 0.0.0.255
permit ip 192.168.177.0 0.0.0.255 192.168.175.0 0.0.0.255
!
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.168.235
set transform-set TS
match address VPN_TRAFFIC
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.237 255.255.255.0
ip virtual-reassembly in
duplex auto
speed auto
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip virtual-reassembly in
duplex auto
speed auto
!
interface GigabitEthernet0/1.177
description INSIDE_177
encapsulation dot1Q 177
ip address 192.168.177.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 192.168.168.1
ip route 192.168.175.0 255.255.255.0 192.168.168.235
!
TEMPLATE--------------==============LOCALRTR===================--------------------------------
!
crypto isakmp key firewallcx address 192.168.168.237
!
crypto map CMAP 77 ipsec-isakmp
set peer 192.168.168.237
set transform-set TS
match address VPN_TRAFFIC_177
!
ip route 192.168.177.0 255.255.255.0 192.168.168.237
ip access-list extended VPN_TRAFFIC_177
permit tcp 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
TEMPLATE--------------=================================--------------------------------
===TCPDUMP on Apache Server 192.168.175.66 - client PC_Browser on 192.168.176.3===
#
[root@apache myuser]# tcpdump -i -vv enp0s3 | grep 192.168.176.3
tcpdump: -vv: No such device exists
(SIOCGIFHWADDR: No such device)
[root@apache myuser]# tcpdump -vv -i enp0s3 | grep 192.168.176.3
tcpdump: listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144 bytes
192.168.176.3.49345 > apache.myco.com.http: Flags [S], cksum 0x3052 (correct), seq 1850609357, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49345: Flags [S.], cksum 0xe0bd (incorrect -> 0x9d84), seq 1779422871, ack 1850609358, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
192.168.176.3.49345 > apache.myco.com.http: Flags [R], cksum 0x13ff (correct), seq 1850609358, win 0, length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [S], cksum 0x7ae5 (correct), seq 391912235, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49346: Flags [S.], cksum 0xe0bd (incorrect -> 0xab44), seq 1029849112, ack 391912236, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [R], cksum 0xa926 (correct), seq 391912236, win 0, length 0
192.168.176.3.49345 > apache.myco.com.http: Flags [S], cksum 0x3052 (correct), seq 1850609357, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49345: Flags [S.], cksum 0xe0bd (incorrect -> 0xf28d), seq 1826455232, ack 1850609358, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
192.168.176.3.49345 > apache.myco.com.http: Flags [R], cksum 0x13ff (correct), seq 1850609358, win 0, length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [S], cksum 0x7ae5 (correct), seq 391912235, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49346: Flags [S.], cksum 0xe0bd (incorrect -> 0xf902), seq 1076883340, ack 391912236, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [R], cksum 0xa926 (correct), seq 391912236, win 0, length 0
192.168.176.3.49345 > apache.myco.com.http: Flags [S], cksum 0x445b (correct), seq 1850609357, win 8192, options [mss 1460,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49345: Flags [S.], cksum 0xe0b9 (incorrect -> 0x03fb), seq 1920302025, ack 1850609358, win 29200, options [mss 1460,nop,nop,sackOK], length 0
192.168.176.3.49345 > apache.myco.com.http: Flags [R], cksum 0x13ff (correct), seq 1850609358, win 0, length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [S], cksum 0x8eee (correct), seq 391912235, win 8192, options [mss 1460,nop,nop,sackOK], length 0
apache.myco.com.http > 192.168.176.3.49346: Flags [S.], cksum 0xe0b9 (incorrect -> 0x1dae), seq 1170725207, ack 391912236, win 29200, options [mss 1460,nop,nop,sackOK], length 0
192.168.176.3.49346 > apache.myco.com.http: Flags [R], cksum 0xa926 (correct), seq 391912236, win 0, length 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 09:23 AM
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide