- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Policy Based Routing for WLC that doesn't break connection to local APs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 11:10 AM
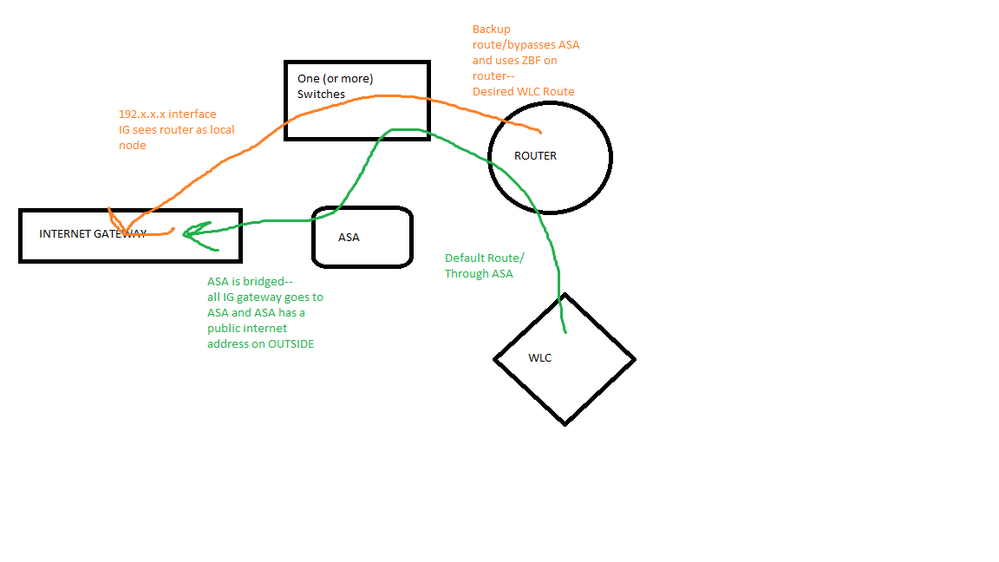
Alright guys, I've been scratching my head about this one for a few weeks and I'm hoping I'm just making a simple PBR mistake and someone can help me out.
As you can see (hopefully) all the traffic from my home network goes through my ASA. That's all well and good, but my wifi traffic SHOULD go through the Zone Based Firewall and straight out to the internet. I have some webcams and echos that do IoT things that the ASA does *NOT* like at all (I get enough trouble from my WLC for trying to run multicast packets). The ASA is breaking some of my appliances, and it should be easy enough to redirect all traffic from the ASA out of the ZBF and have it bypass the ASA entirely. Default route to 0 goes to the ASA with an AD of 5. There's a second static route out of the gateway with an AD of 6 for failover.
Some details that may matter:
the WLC is at 172.32.0.2, the IP on the router is 172.32.0.1 for the WLC subnet, APs throughout the house are dynamically assigned IP addresses in the 172.32.0.0/24 range. AP Clients (wireless devices like my phone and cameras) live on 172.32.32.0/24.
The PBR that I've tried so far, plus or mins a few variations:
I set an ACL to match 172.32/16.
I set a MATCH parameter and a next hop that anything coming from 172.32/16 has a next hop of the ISP gateway, completely avoiding the ASA.
ALL my APs go dead instantly.
I suspect that this is killing the connection between the WLC and the APs when I apply the route-map to 172.32.0.1 on the router. I suspect I need an ACL that I'm applying to my policy needs an exemption for traffic that's both to and from 172.32/16, or just to the 172.32/16 subnet but... I have no idea what that ACL or PBR would look like. I suspect it would look something like this:
ACL 1 - match all traffic to 172.32/16
ACL 2 - match all traffic from 172.32/16
Route-map 1
10 permit
match: ACL1
set: <Do nothing/follow normal route policy>
20 permit
match: ACL 2
set: Ip next-hop ISP Gateway
(I know that's not a perfect transcription but I'm not in my lab at this moment).
Does anyone have any experience splitting traffic to/from a subnet with a different default route? Setting up VRF seems excessive, and I'd rather still be able to access my WLC from other subnets for management. I feel like I just can't figure out the ACL/PBR logic (I've had zero luck figuring out how to get a match that then "does nothing") and if I could get the packets flowing correctly... well, that's what everyone's here for anyway, i guess. Currently my options are to run everything out the ZBF by changing the AD (so I might as well sell my ASA), or deal with broken wifi IoTs (so I might as well sell my WLC) and... neither of those should be true, i should just be able to figure out how to run the traffic.
Any help would be greatly appreciated and happily voted up. Thanks.
Solved! Go to Solution.
- Labels:
-
Other Routing
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 12:16 PM - edited 01-02-2020 12:30 PM
Hello
Try and have two stanza rules The first rule will deny policy routing for any traffic to-from wlc matching on an permitted acl, if this traffic flow isn't correct then append it to suit what traffic you DONT wish to be policy routed from that subnet
example:
access-list 100 permit ip host 172.32.0.2 172.32.0.0 0.0.0.255
access-list 100 permit ip 172.32.0.0 0.0.0.255 host 172.32.0.2
route-map wlc-wifi deny 10
match ip address 100
route-map wlc-wifi permit 99
set ip next-hop GATEWAY
int x/x
description WIFI lan
ip policy route-map wlc-wifi
Apologies for the format of the text but im on my phone and travelling on train
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 11:39 AM
Hello,
can you post the full running config of the ZBF router ? Is the wireless a separate zone ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 11:49 AM
I can post the full running config in a few hours. The wireless is not a separate zone, there are only 2 zones in the network, inside and outside. All inside traffic has the same trust level and is allowed to travel anywhere. All subnets are in the same zone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 12:16 PM - edited 01-02-2020 12:30 PM
Hello
Try and have two stanza rules The first rule will deny policy routing for any traffic to-from wlc matching on an permitted acl, if this traffic flow isn't correct then append it to suit what traffic you DONT wish to be policy routed from that subnet
example:
access-list 100 permit ip host 172.32.0.2 172.32.0.0 0.0.0.255
access-list 100 permit ip 172.32.0.0 0.0.0.255 host 172.32.0.2
route-map wlc-wifi deny 10
match ip address 100
route-map wlc-wifi permit 99
set ip next-hop GATEWAY
int x/x
description WIFI lan
ip policy route-map wlc-wifi
Apologies for the format of the text but im on my phone and travelling on train
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 05:10 PM
Paul,
I guess it had never actually occurred to me to use a "deny" statement in a PBR entry--I've literally never done it and even forgot it was an option. None of my googling lead me to believe a PBR deny would force regular route-logic. I guess I slept through that chapter.
I set all traffic to or from 173.32.0/24 (WLC and AP subnet) to a PBR "deny"
and all traffic to or from 172.32.32/24 (DHCP Scope for Wireless Clients) to a PBR "permit" with my backup gateway as the line out
I dropped the /16 statements just to clean it up a little
--Worked like a charm! This has seriously been plaguing me for weeks, not to mention just making me feel like an idiot for not being able to figure it out. Once the Route-map was showing positive matches I put an ACL on the interface out to the gateway and made sure my wireless connections dropped--all connections to the internet died, but connections to the local WLAN stayed up, exactly the behavior I wanted!
I guess when you run a WLAN (not a wireless guy so much), you don't want to interfere at all with the traffic on your WLC. My assumption was that the traffic flow went APs-->WLC-->Router-->Internet, and in reverse, but any attempt to enforce a policy based route on the management subnet causes instant catastrophic failure. I'm not sure how packet exchange works on the subnet (are the APs hitting the router before the WLC? Why would they???) but I've learned a valuable lesson about leaving the WLC/AP subnet alone--it's outside my expertise anyone.
I only explain on this, Paul, in case anyone one runs into a similar problem and finds my post. That information could have saved me a boatload of time and headaches. Thanks for typing this in the rain for me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 05:06 AM
Hello zachrhart@gmail.com
I am glad to hear you have now got it working as you wanted, and thank for your feedback to the community and the rating - Very much appreciated.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide