- Cisco Community
- Technology and Support
- Networking
- Routing
- Redundancy for IPSEC Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 05:05 AM - edited 03-05-2019 10:39 AM
Hi,
I have two Internet circuits from an ISP connecting to a Single router. The ISP is same but has provided us two different last mile providers for some redundancy. We have been given a /29 Public subnet by the ISP, and I have configured eBGP with these two last mile providers, and have preferred one link over another. Currently, there are two IPSEC tunnels going to two different locations.
Now, we are planning to upgrade the routers, and introduce another one for router level redundancy. The 2nd ISP link will connect on Router 2, and I would be configuring EBGP towards the ISP.
How can I make the tunnel work on backup router/Link if Router 1 (or ISP1) goes down?
Pic attached for reference.
Cheers
Mikey
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 02:34 AM
Hi there,
If you move the tunnel to Router1 make sure you source it from a globally reachable loopback interface and not the ISP connected interface. That way, if the ISP link fails IPSec traffic should be routed via Router2.
Regarding Router1 failing completely, you could create an EEM script on Router2 to look at the BGP entries in the routing table for routes belonging to the remote site on the end of IPSec tunnel1 (under normal conditions these would be received from Router1). When Router1 fails the routes would vanish, and your script could then no shut the Router2 loopback interface. The loopback would need to share the same global IP address because you would not be able change the IPSec tunnel config at the remote end.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 05:51 AM
Hi there,
Where is the IPSec tunnel sourced from? Is it Router1 or a device further into your network?
I would suggest establishing a iBGP peering between your routers. You should also configure Router1 with a higher local preference. If the ISP link on Router1 goes down traffic will be sent to Router2.
BTW your attachment wouldn't download, so the above suggestion may not be the best fit. :)
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 12:44 AM
Hi Seb,
The IPSEC Tunnel is currently sourced from a Firewall inside in my network. We plan to source it from Router going forward. So, If the ISP link1 fails, the traffic would be routed via iBGP to Router 2 and the tunnel would still work.
But, what if Router 1 fails? Do I have to setup a same tunnel config in Router 2 also for it to work as backup?
Cheers
Mikey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 02:34 AM
Hi there,
If you move the tunnel to Router1 make sure you source it from a globally reachable loopback interface and not the ISP connected interface. That way, if the ISP link fails IPSec traffic should be routed via Router2.
Regarding Router1 failing completely, you could create an EEM script on Router2 to look at the BGP entries in the routing table for routes belonging to the remote site on the end of IPSec tunnel1 (under normal conditions these would be received from Router1). When Router1 fails the routes would vanish, and your script could then no shut the Router2 loopback interface. The loopback would need to share the same global IP address because you would not be able change the IPSec tunnel config at the remote end.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 09:38 AM
Thanks Seb. I'll read more on the EEM scripts, and get back to you with the configs before I go ahead and implement them ;)
Cheers
Mikey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 12:04 PM
Hello again,
thinking about this a little more, is it possible to create a backup IPSec tunnel from Router2 to RemoteSite1?
On Router1 you could give the received prefixes from RemoteSite1 a higher local-preference. This means any traffic arriving on Router2 destined to RemoteSite1 would go via Router1.
In the event of Router1 failure, Router2 would already be receiving a prefix for RemoteSite1 via its own IPSec tunnel and would install it in its own routing table.
This is a preferable solution to hacking around with EEM scripts and having duplicate configuration running on different routers.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 07:37 AM
Hi Seb,
Apologies for the delay in reply. I had been travelling on an other project.
In regards to your query of setting up a backup tunnel with remote destination, I doubt this would be feasible. We prefer to run this without engaging the customer end IT folks due to various factors (limited technical knowledge, lack of coordination, support etc).
Cheers
Mikey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2018 11:03 PM
Can we source the tunnel from the HSRP IP, so that even if the link1 or router 1 fails, the router 2 would take the active role, and keep the tunnel up.
Few more queries
1) The customer is currently terminating the Tunnel on their firewall. So, if I move the tunnel termination to a router on my end, will that be a problem?
2) How do I source the tunnel from a loopback or HSRP IP? L2 over IPSEC won;t work, so I believe I have to make a VTI (Virtual tunnel interface) on my routers?
3) Customer end tunnel IP is on a public segment. what should the tunnel subnet be on?
Appreciate your inputs on this.
Cheers
Mikey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 12:33 PM
Hello again.
I don't believe it is possible to have an HSRP vIP as a tunnel endpoint. I've never seen it in production/ lab or in any documentation.
I still standby the idea that you need to run IPSec tunnels to both sites from both routers, and use BGP local-preference to 'draw' the traffic the Routers adjacent remote site.
ie, RouterA should advertise SiteA prefixes within your AS with a higher local_preference. This will ensure traffic arriving on Router2 will be routed to Router1 to reach SiteA.
Regarding your questions:
1) The IPSec tunnel can be terminated on any device which supports the required crypto algorithms.
2) Sourcing the tunnel from a loopback is as easy as tunnel source loopback0. but now we are moving from IPSec syntax to GRE. IPSec tunnels are placed with crypto map statements on interfaces. If you are planning on using VTIs, last time I checked they are not supported on firewalls so the remote site firewall will not know how to handle the tunnel.
3) The IP addresses used on the tunnel source interfaces must be reachable from either end for it to establish correctly. The subnet used within the tunnel should be in the RFC1918 range.
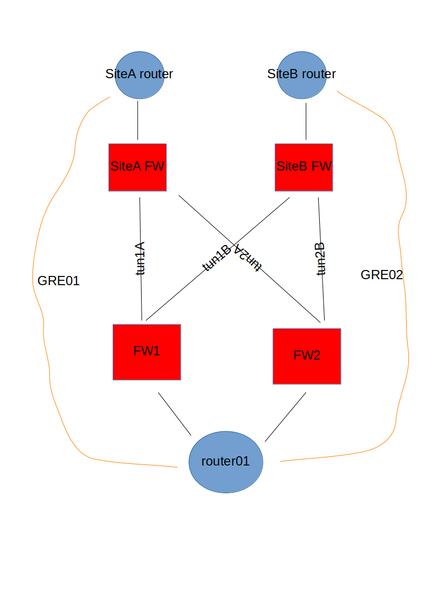
Behold this topology diagram I've just knocked up in libreoffice draw(!):
This is how I would put it together. IPsec tunnels running between the firewalls. Loopbacks on each router for GRE tunnels. Each site advertising the GRE tunnel endpoint IPs across the IPsec tunnel mesh. This would create a GRE overlay over the IPsec mesh. It would not matter which local router at the 'home' site was up, the GRE tunnel would be routed towards the remote sites A & B.
The GRE tunnels would be used to form IGP adjacencies between the sites, and permit the advertisement of internal networks to each other.
Take a look at this blog post I wrote about Tunnel VRFs:
https://configif.wordpress.com/2017/12/21/tunnel-vrf/
...if these are secure sites you are connecting to it may give you some good pointers.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2018 01:44 AM
Thanks for your reply. We have now finally agreed to only built one tunnel across Router1, and configure the other backup tunnel on Router 2 once the customer sets it up on their end.
But, I still have a problem though. While moving the tunnel to the router, I will have to move the same public IP (for tunnel termination), and I have to use VTI on the router. Just defining a crypto map on the physical WAN interface won't work since that is on a different IP segment.
Are you sure VTIs won;t work if my end is a Cisco router, and the other end is a Palo Alto firewall?
Cheers
Mikey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2018 04:42 AM
I'm not clear on your second paragraph, it would be good to see some running config and intended additional tunnel config.
When I mentioned VTIs and firewalls I was thinking of ASAs, but a Palo Alto is a different beast. A quick google show it should be possible:
cheers
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 06:20 AM
hi,
you can run iBGP between your internet edge routers so it's all dynamic.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide