- Cisco Community
- Technology and Support
- Networking
- Routing
- Rogue DHCP problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 10:48 AM - edited 03-05-2019 07:41 AM
Hi everyone!
I have a problem regarding one of our customers.
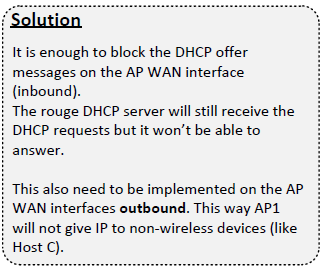
As you can see, there's two APs, where AP1 functions as a DHCP server assigning IPs to laptops using wireless. Non-wireless client PCs, however, lease an IP from the rogue DHCP server (customer-managed). The customer wants to keep this behaviour.
The problem is that the DHCP server is more faster than AP1 regarding IP assigning via DHCP. Therefore, all clients (incl. wireless ones) get an IP from the DHCP server, which is undesirable for the customer, as mentioned above.
As a possible solution, I think about DHCP snooping on the switch. What's your opinion about that?
Do you have any other better solutions for this problem?
Deactivating the DHCP function on the server is not possible as non-wireless client don't get an IP then.

Thanks in advance!
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:17 PM
Hello
You could try applying a mac ACL relating to the rouge DHCP server to the vlan(s) you don't want it to work on
mac address-table static xxxx.xxxx.xxxx vlan 10 drop
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:42 PM
Hello,
in addition to Paul's suggestion, you could also specify an access list that denies udp ports 67 and 68 inbound on the Vlan interface where the wireless clients are connected to...
ip access-list extended DROP_DHCP
deny udp host x.x.x.x any eq bootpc
deny udp host x.x.x.x any eq bootps
permit ip any any
interface Vlan1
ip access-group DROP_DHCP in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:17 PM
Hello
You could try applying a mac ACL relating to the rouge DHCP server to the vlan(s) you don't want it to work on
mac address-table static xxxx.xxxx.xxxx vlan 10 drop
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:40 PM
Hi Paul,
if I understand it correctly, this command's effect would be to drop frames with the specified MAC (the server's MAC) in the specified VLAN right?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:42 PM
Hello,
in addition to Paul's suggestion, you could also specify an access list that denies udp ports 67 and 68 inbound on the Vlan interface where the wireless clients are connected to...
ip access-list extended DROP_DHCP
deny udp host x.x.x.x any eq bootpc
deny udp host x.x.x.x any eq bootps
permit ip any any
interface Vlan1
ip access-group DROP_DHCP in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 12:54 PM
Hi,
yeah I did some more research and found the same alternative solution with MAC ACLs :)
Thank you! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 01:36 AM
Hello
Sis this assist you if so please rate and close - It can provide feedback for others.
res
paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 04:16 AM
Hello again,
meanwhile I discussed this case with my colleagues and we're planning to implement something like the following changes:
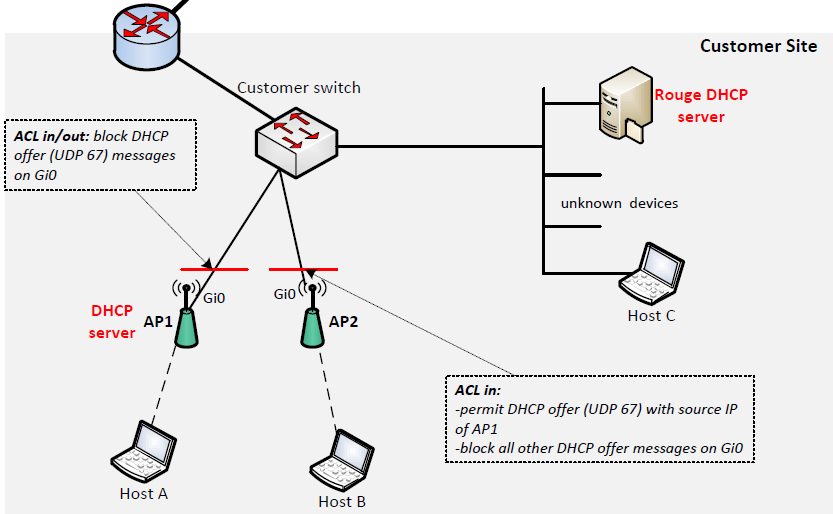
AP1
!
ip access-list extended DROP_DHCP
deny udp host [server-IP] eq bootps any eq bootpc
permit udp host [AP1-IP] eq bootps any eq bootpc
!
int x
ip access-group DROP_DHCP in
ip access-group DROP_DHCP out
!
AP2
!
ip access-list extended DROP_DHCP
deny udp host [server-IP] eq bootps any eq bootpc
permit udp host [AP1-IP] eq bootps any eq bootpc
!
int Gi0
ip access-group DROP_DHCP in
!
The only problem with this config is that on AP1, with the following line we cannot distinguish between wireless (which should get an IP from AP1) and non-wireless devices (which should get an IP from the server):
permit udp host [AP1-IP] eq bootps any eq bootpc
We couldn't find any solutions for that so far.
Do you have any ideas?
Thank you in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 04:59 AM
Hello,
I am thinking about configuring option 82 on the AP. The idea is that the DHCP server only gives out IP addresses to requests that contain option 82 parameters, which you can configure on the AP.
http://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/113302-dhcp-option82-00.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 05:09 AM
Hello
Maybe I am confused now - so to confirm you Wish for the Ap to receive address from the rogue dhcp server but not wifi clients assoicated with the AP
Res
paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 05:58 AM
Hi Paul,
just to be clear:
1. AP1 serves as DHCP server and it should only assign IPs to wireless devices (laptops).
2. The rogue DHCP server should only assign IPs to non-wireless devices (PCs).
@gpauwen: thanks for the tip, I will look after this option :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 05:58 AM
So you wrote:
"The idea is that the DHCP server only gives out IP addresses to requests that contain option 82 parameters, which you can configure on the AP."
I only have CLI access to the APs but this guide focuses on using WLCs with GUI. That helps me not so much.
Additonally, there isn't a relay agent configured on AP1 as it's in the same subnet as the clients - no off-subnet DHCP servers present.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2016 10:15 AM
Hi guys,
in the meantime it seems we will solve the issue by asking the customer to configure the switch.
We offered two options:
1. Configure an additional VLAN on the segment
2. Deny all DHCP traffic on both APs inbound and configure each of them as DHCP server by dividing the assignable DHCP pool by 2.
Anyway, thank you very much for your support! :)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide