- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Route device with public IP via Cisco ASA.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2020 08:18 AM
Hi All,
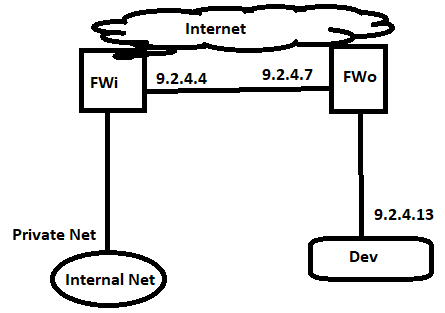
I have IP range from our provider 9.2.4.0/24
GW is configured on ISP router (ISPr) 9.2.4.1/28
I have two FWs, one of them is used for Internal (FWi) network and second one is used for Ousourcing (FWo).
FWi has IP: 9.2.4.4
FWo has IP: 9.2.4.7
Aditionally I have device (Dev) which must have public IP 9.2.4.13
Dev should be behind FWo, I have setted up default route on Dev to reach any go via FWi and on ISPr to reach Dev, go via FWi. - for Internet this works.
Problem is with comunication from internal network (behind FWi) to Dev, because traffic goes directly to Dev and not through FWo, same issue is for different direction from Dev to internal network behind FWi.
FWo is cisco ASA 5508, what I can do to solve this issue and put Dev behind cisco ASA ?
Thank you
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2020 12:47 AM
Hi,
About loosing one public IP, you can't just win, there is no solution, generally speaking which has no drawbacks or loses, it's just a matter of you being able to visualise and assess what you loose, what you win and take a decision. So, finally, solutions:
1. Clustering or active/active, both with multiple-context, where you'll be having one context as transparent; if the HW model is 5508, than no clustering, just active/active with routed and transparent contexts
2. Keep things as are, just pick the 9.2.4.12/30 subnet and attach it behind your routed FWo
If you weigh better the pros and cons, the first options requires much more changes, technical expertise and complexity, and without knowing the full architecture and overall network requirements it may actually break or influence other things. The second option, has only the drawback of "loosing" one public IP. You have a /24 PA public IP space. I don't really see loosing one IP as a loss, given your options.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2020 12:42 PM
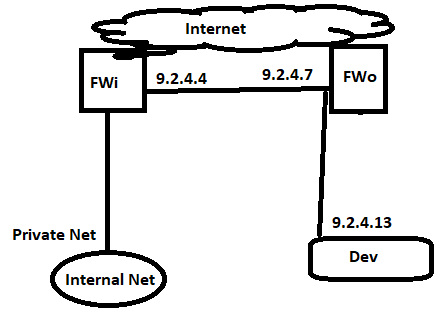
There are several things in your description that I do not understand. Let us start with what appears to be on FWo an address on interface outside that appears to be in the same subnet as an address on interface inside. Can you clarify the relationship of these interfaces on this firewall?
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2020 10:45 PM
Hi Richard,
Thank you for reply, with picture above, I wanted to show you, that I need Dev to be behind firewall, but Dev is on same interface as outside interface, I changed picture, please see below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 01:08 AM
Hi,
Configure FWi in routed mode and FWo in transparent mode.This way any traffic going to Private net needs to go/pass through FWi rules, traffic going to Dev needs to go/pass through FWo rules.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 03:53 AM
Hi Cristian,
problem is, that behind FWo, I have private networks, which are used for outsourcing, so it is not possible to change it by that way, somwhere I read to do multicontext FW on FWo, one of them will be in routed mode and second one will be in transparent mode.
I do not know, how dificult is to do it, and if you see it as an option. Is there maybe some different option to do it ?
FWo are two firewalls which are in cluster, but it is in production, so I have to be sure it is right solution, and there is not anything less risky.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 07:40 AM
Hi,
I see some mismatched on your presented data. You're saying that the FWo is actually an ASA cluster of ASA 5508, were the ASA 5508 does not support clustering. In case there is clustering and that is actually a different HW model, you could configure clustering and multi-context, but this clearly requires a maintenance window.
What you could do, since you have a /24 public PA, you could leave the FWo as it is in routed mode, subnet the /24 public PA and allocate the 9.2.4.12/30 to the interconnect between the FWo ASA and the dev endpoint. You have the endpoint as 9.2.4.13/30 with a default gateway of 9.2.4.14/30 (the FWo ASA), and so all traffic for your dev endpoint dest inspected by FWo, and the impact is minimum. Your FWi would need a static route, in order not to ARP, for the 9.2.4.12/30 towards FWo.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 12:57 PM
Hi Cristian,
Yes you are right, I can make only failover, but fortunately I can make 2 multicontext with security plus license, which I have on 5508, so it is possible to do it, if there is not possible clustering?
Regarding second option, now is gw on ISP, with 9.2.4.1/28, so if I have this range, could I use 9.2.4.12/30 as separate interface on F5 and keep ISP interface as it is? In that case I will lost one public IP.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2020 12:47 AM
Hi,
About loosing one public IP, you can't just win, there is no solution, generally speaking which has no drawbacks or loses, it's just a matter of you being able to visualise and assess what you loose, what you win and take a decision. So, finally, solutions:
1. Clustering or active/active, both with multiple-context, where you'll be having one context as transparent; if the HW model is 5508, than no clustering, just active/active with routed and transparent contexts
2. Keep things as are, just pick the 9.2.4.12/30 subnet and attach it behind your routed FWo
If you weigh better the pros and cons, the first options requires much more changes, technical expertise and complexity, and without knowing the full architecture and overall network requirements it may actually break or influence other things. The second option, has only the drawback of "loosing" one public IP. You have a /24 PA public IP space. I don't really see loosing one IP as a loss, given your options.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 04:21 AM
Hello
Do those FW's reside locally to each other, Is it applicable to introduce an addtional interconnect between them?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 04:38 AM
Hi Paul,
thank you for your reply, FWi is used for internal network, and also for global purposes, lot of VPNs.., FWo have to be used only for outsourcing purposes. Yes FWi and FWo are in same DCs, but if it is not necessary I do not want to make interconnection between them.
Existing interconnect between them is because of Internet access from same provider.
Thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide