- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: RV340 Inter-VLAN routing and access list
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 Inter-VLAN routing and access list
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 12:31 PM
I have a RV340 and am pretty green when it comes to CISCO router. Here is the details of our set up:
- 3 VLANs - VLAN2 = 172.16.99.1/24, VLAN3 = 172.16.66.1/24 and VLAN4 = 172.16.77.1/24
- WAN PORT = 192.168.77.254/24 (Static IP)
- Inter-Vlan Routing are enabled on all VLANs
I wish to do the following:
- Allow all traffic from VLAN2 to all VLANs and WAN (this is my main LAN)
- Disallow all traffic from VLAN3 and VLAN4 and VLAN1 (default) to VLAN2
I tried to use Firewall/Access List to control the traffic but it does not work or may be I do not know how.
Please advise...
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 12:48 PM
Can you post the screen shots to look..here is reference guide for reference (you may have seen it to configure)
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 12:57 PM
Hello Jonlp,
first of all, RV340 runs a different OS then IOS please refer to the following admin guide for your device:
https://www.cisco.com/c/dam/en/us/td/docs/routers/csbr/RV340/Administration/EN/b_RV340x_AG.pdf
Download it so that you can perform searches on the pdf file.
Look for Firewall Access Rules on pag 84 of the pdf file.
Use the Firewall >> Access Rule add to create a new rule
For example you can
Rule status Enable
However, what would be needed here is the capability to check for TCP established sessions.
This is possible in IOS with extended ACLs using protocol tcp and the keyword established.
If you deny traffic from Vlan3, Vlan4, Vlan1 IP subnets to Vlan2 IP subnet you are not able to have bidirectional communications started by users in Vlan2 that is what you would like to have.
Looking for established word in the pdf I have found 8 occurrences related to VPN status and so on but not to ACLs.
Verify if when you specify TCP protocol in IPv4 >> Services in the access rule there is a flag for established sessions.
This is what you would need in my opinion and experience.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 05:07 PM
Thank you for providing the info; however, I looked the the admin guide
but it does not help.
Just to make sure that we are on the same page as far as my network
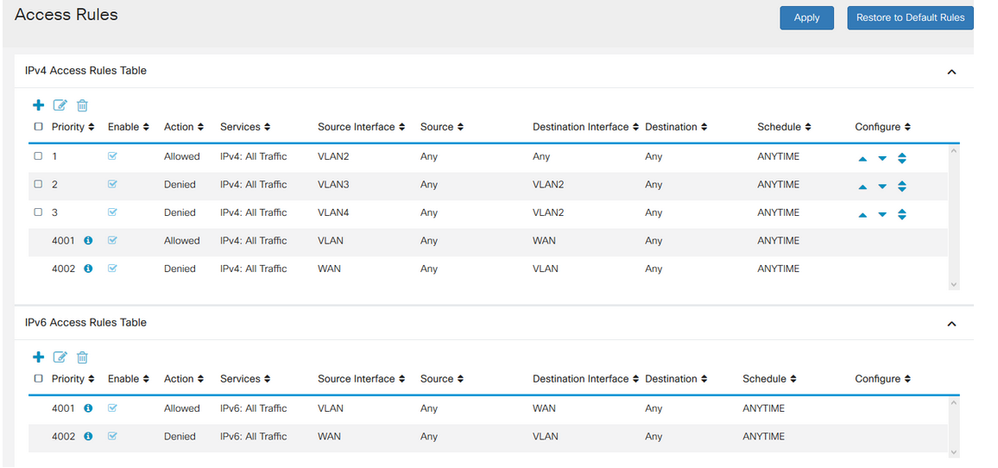
topology, below is the screenshots of my VLANs and Access Rules. As
previously indicated, here is what I wish to configure....Any devices
from VLAN2 can get to anywhere (WAN and all VLANs) and any devices that
are from WAN, VLAN1, VLAN3 or VLAN4 cannot get to devices in VLAN2
(which is my internal LAN).
Thank you.
*VLAN setting*
Here are my access rules
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 05:55 PM
Some how pictures were not enclosed in my reply. Here they are
VLAN SETTING
ACCESS RULES SETTING
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 05:55 PM
Some how pictures were not enclosed in my reply. Here they are
VLAN SETTING
ACCESS RULES SETTING
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 11:30 PM
Hello Jonlp,
are the users in Vlan2 able to connect to the internet and to start communications with other Vlan subnets?
If the firewall is stateful the return path should be provided for sessions permitted by access rule 1.
I apologize for the possible confusion, if the firewall is stateful it can work without the need for checking the TCP flags.
Can you describe the issues you are seeing with this configuration ?
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 03:57 AM
Giuseppe,
Here is our current situation.
1. Users from VLAN2, VLAN3, and VLAN4 can get to the Internet and have proper IP addresses assigned to them (DHCP is working).
2. Users from VLAN2 (172.16.99.100) can ping VLAN3 ip address (172.16.66.1) so routing appears to work but it cannot ping any users in VLAN3 (ie. 172.16.66.120) or VLAN4 (ie. 172.16.77.110)
3. The same is true for users in VLAN4, they can get to the Internet but cannot ping any users in VLAN2 or VLAN3.
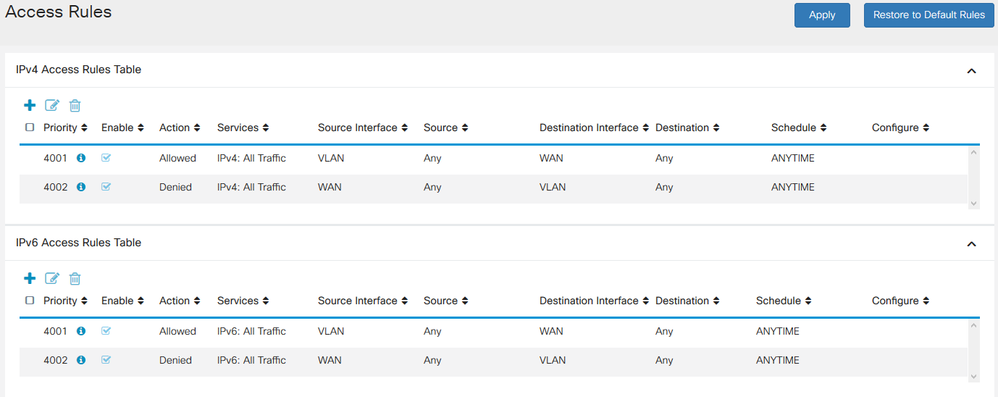
Let set aside what I wish to do for a moment; per my understanding, Inter-Vlan routing allows traffic between VLANs but that does not appears to work. Even when I reset firewall access rules to default (see below)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 07:27 AM
Hello Jonlp,
if you do the following under
Firewall >> Basic Setting
uncheck the Firewall enable check
and you apply the change is inter vlan routing working ?
This is just for a test for a short time to understand if the default access rules keep each vlan segregated as you are seeing in your device.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2019 09:10 AM
Giuseppe,
Good news...
With the firewall disabled, devices in all VLANs can get to each other (Inter-Vlan routing works...)
I then re-enabled the firewall and added access rules according to the desired traffic flow....now they are all working as designed. Not sure what happened but it appears that disable/re-enable firewall did clear what caused the issue.
Thank you very much for your assistance.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide