- Cisco Community
- Technology and Support
- Networking
- Routing
- Site2Site VPN hub and spoke with NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site2Site VPN hub and spoke with NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 06:19 AM - edited 03-05-2019 10:53 AM
Hello Everyone,
I would like to ask about help with configuration hub and spoke topology between three routers.
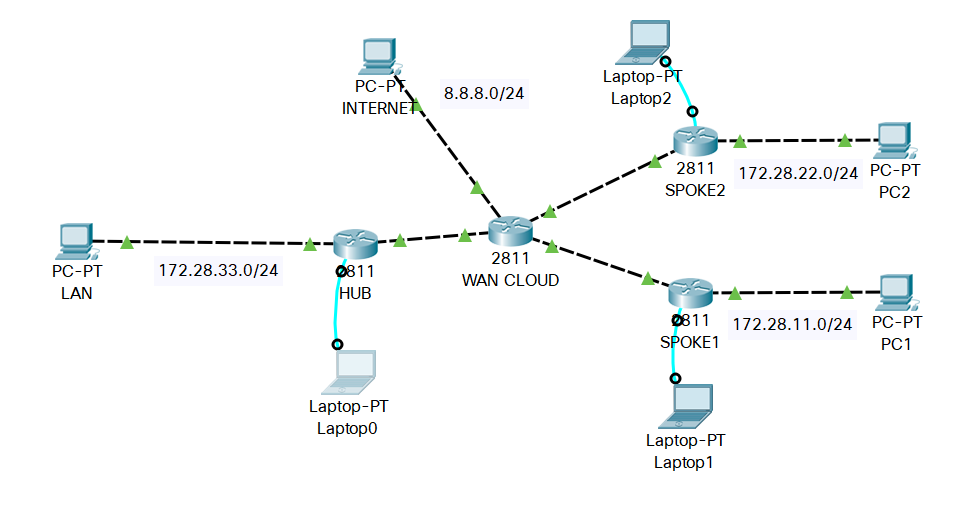
I have three LAN networks:
- HUB LAN network 172.28.33.0/24
- SPOKE1 LAN network 172.28.11.0/24
- SPOKE2 LAN network 172.28.22.0/24
There are two IPSec VPN tunnels:
HUB - SPOKE1 : basic tunnel without NAT between networks
HUB - SPOKE2 : tunnel with source NAT from HUB site
On HUB we have also Internet connection with NAT overload for local LAN users.
Topology diagram:
I have a problem with traffic between SPOKE1 and SPOKE2 over existing tunnels via HUB.
Traffic from SPOKE1 enters HUB and leave the HUB on the same interface but I can't see any NAT translations on the HUB. Tunnels between LAN HUB and SPOKE1 and SPOKE2 are working correctly.
Please advice what's missing / wrong in below config.
HUB:
hostname HUB ! ! crypto isakmp policy 10 encr aes 256 authentication pre-share group 5 lifetime 28800 ! crypto isakmp key 123 address 192.168.11.2 crypto isakmp key 123 address 192.168.13.2 ! crypto ipsec transform-set no1-set ah-sha-hmac esp-aes 256 ! crypto map no1-map 10 ipsec-isakmp set peer 192.168.11.2 set pfs group5 set security-association lifetime seconds 28800 set transform-set no1-set match address vpn-traffic-spoke1 ! crypto map no1-map 20 ipsec-isakmp set peer 192.168.13.2 set pfs group5 set security-association lifetime seconds 28800 set transform-set no1-set match address vpn2-traffic-spoke2 ! interface FastEthernet0/1 ip address 192.168.12.1 255.255.255.0 ip nat outside duplex auto speed auto crypto map no1-map ! interface Ethernet1/0 ip address 172.28.33.1 255.255.255.0 ip nat inside duplex auto speed auto ! ip nat pool peer2-pool 192.168.119.25 192.168.119.30 netmask 255.255.255.248 ip nat inside source list INTERNET-NAT interface FastEthernet0/1 overload ip nat inside source list VPN-NAT-SPOKE2 pool peer2-pool overload ip classless ip route 0.0.0.0 0.0.0.0 192.168.12.2 ! ip access-list extended vpn-traffic-spoke1 permit ip any 172.28.11.0 0.0.0.255 ip access-list extended INTERNET-NAT deny ip 172.28.33.0 0.0.0.255 172.28.22.0 0.0.0.255 deny ip 172.28.11.0 0.0.0.255 172.28.22.0 0.0.0.255 permit ip 172.28.33.0 0.0.0.255 any ip access-list extended vpn2-traffic-spoke2 permit ip 192.168.119.24 0.0.0.7 172.28.22.0 0.0.0.255 ip access-list extended VPN-NAT-SPOKE2 permit ip 172.28.33.0 0.0.0.255 172.28.22.0 0.0.0.255 permit ip 172.28.11.0 0.0.0.255 172.28.22.0 0.0.0.255 ! end
SPOKE1:
hostname SPOKE1 ! crypto isakmp policy 10 encr aes 256 authentication pre-share group 5 lifetime 28800 ! crypto isakmp key 123 address 192.168.12.1 ! ! ! crypto ipsec transform-set no1-set ah-sha-hmac esp-aes 256 ! crypto map no1-map 10 ipsec-isakmp set peer 192.168.12.1 set pfs group5 set security-association lifetime seconds 28800 set transform-set no1-set match address vpn-traffic ! interface FastEthernet0/0 ip address 192.168.11.2 255.255.255.0 duplex auto speed auto crypto map no1-map ! interface FastEthernet0/1 ip address 172.28.11.1 255.255.255.0 duplex auto speed auto ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.11.1 ! ip flow-export version 9 ! ip access-list extended vpn-traffic permit ip 172.28.11.0 0.0.0.255 any ! end
SPOKE2:
hostname SPOKE2 ! crypto isakmp policy 10 encr aes 256 authentication pre-share group 5 lifetime 28800 ! crypto isakmp key 123 address 192.168.12.1 ! ! ! crypto ipsec transform-set no1-set ah-sha-hmac esp-aes 256 ! crypto map no1-map 10 ipsec-isakmp set peer 192.168.12.1 set pfs group5 set security-association lifetime seconds 28800 set transform-set no1-set match address vpn-traffic ! interface FastEthernet0/0 ip address 192.168.13.2 255.255.255.0 duplex auto speed auto crypto map no1-map ! interface FastEthernet0/1 ip address 172.28.22.1 255.255.255.0 duplex auto speed auto ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.13.1 ! ip flow-export version 9 ! ! ip access-list extended vpn-traffic permit ip 172.28.22.0 0.0.0.255 192.168.119.24 0.0.0.7 !
- Labels:
-
LAN Switching
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:35 PM - edited 09-01-2018 02:35 PM
Haven't tested your config but noticed you have typo in second ip nat pointing to VPN-NAT but only acl to match is named VPN-NAT-SPOKE2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2018 12:37 PM - edited 09-02-2018 12:38 PM
Hi ahabcapitan,
Thank you for your answer. I missed this typo in the post where I was correcting ACL names for better understanding. In the lab I didn't do this mistake. I suppose that problem refers to NAT interface configuration.
Traffic from SPOKE1 to SPOKE2 comes in and out on the same HUB f0/1 interface. Interface f0/1 on the HUB is configured as ip nat outside, so traffic is not passing from ip nat inside interface to ip nat outside and NAT is not applied.
I have some solutions:
1. Perform NAT on a stick via loopback interface on HUB. Not tested yet.
2. Perform source NAT on SPOKE1 with expected source IP. Tested and it's working.
3. Change IPSec tunnel config to use VTI. On HUB set VTI pointing to SPOKE1 tunnel as ip nat inside. Not tested yet.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2018 02:23 PM
Hello,
when I change, on Spoke2, the access list:
ip access-list extended vpn-traffic
permit ip 172.28.22.0 0.0.0.255 192.168.119.24 0.0.0.7
to
ip access-list extended vpn-traffic
permit ip 172.28.22.0 0.0.0.255 any
and on the HUB:
ip access-list extended vpn2-traffic-spoke2
permit ip 192.168.119.24 0.0.0.7 172.28.22.0 0.0.0.255
to
ip access-list extended vpn2-traffic-spoke2
permit ip any 172.28.22.0 0.0.0.255
there is communication between SPOKE1 and SPOKE2. What are you trying to accomplish with the NAT pool ? None of the addresses in the pool seem to be configured anywhere...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide