- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: VRF and ACL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VRF and ACL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 02:23 AM
Hello team,
for my next network segmentation, I would use VRF and route them to a firewall for filter the different networks.
4 VRF are planned :
- VRF "front"
- VRF "front management"
- VRF "back"
- VRF "back management"
In each VRF, we'll have many vlans and we want to filter them from the firewall.
Example :
In the VFR "front", we have 10 vlans. Vlan number 1 must not speak with vlan number 2 but only if it's authorized by the firewall.
Then, is it possible, with a default gateway for each VRF to the firewall, to filter each vlan in the same VRF ? Or by default, all vlans in a same VRF could "speak" together ?
Thank you for your support :)
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 04:05 AM
Hi there,
In this topology all VLANs in the same VRF would be able to communicate, as they are the same security level/ classification in your model. If you wanted to restrict communication between them you would additional ACLs on the VLAN SVIs.
This would be stateless so perhaps not as secure as you require.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 04:32 AM
Hello,
thank you for your quick response.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 07:08 AM
Each vlan would need it's own L3 interface which is either on the firewall or somewhere else but if you want to filter between vlans within a VRF why put them in the same VRF ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 11:03 PM
I wanted use VRF to manage routes easily but in my case, effectively, it's not the good solution because I want to isolate each vlans by ACL.
Thank you for your support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2018 01:10 AM
In which case you will want to route every VLAN on the firewall and use the core switch as a Layer2 device only.
Depending on the firewall model this will involve SVIs and a trunk link to the core switch, or multiple routed sub interfaces on a Port-channel.
Since you are routing all VLANs on the firewall, ensure that you bundle enough member links into the Po to satisfy the both the east-west and outbound traffic.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 07:34 AM
Hello,
effectively, I want to route every VLAN to a main Firewall (Fortinet 3000D) to filter which vlan can talk with another.
Network 1 must be filtered by the FW to talk with Network 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 07:44 AM
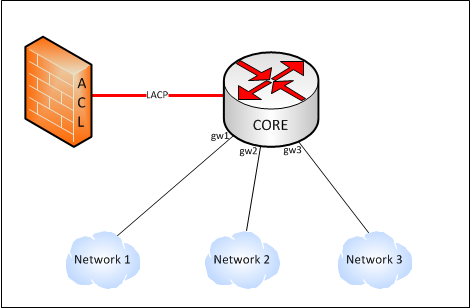
Then you will need the following config:
! CORE ! vlan 10 vlan 20 vlan 30 ! int gi0/1 switchport mode access switchport access vlan 10 spanning-tree portfast ! int gi0/2 switchport mode access switchport access vlan 20 spanning-tree portfast ! int gi0/3 switchport mode access switchport access vlan 30 spanning-tree portfast ! ! int range gi0/9-10 channel-group 1 mode active ! int po1 switchport mode trunk switchport trunk allowed vlan 10,20,30 !
Note, that VLANs 10,20,30 are not routed on the CORE switch, just trunked via Po1 to the firewall. I'm guessing you will need to configure the LCAP on the Fortigate with routed sub-interfaces for each VLAN. I've never confgured one so that' a guess.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 09:41 AM
Hello
Why dont you enable inter-vlan routing on the core switch and segregate vlan traffic from there and then push each vlan off site traffic up to the FW, it will save resource on the FW and you would have various options on the switch to perfrom this segregation.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide