- Cisco Community
- Technology and Support
- Networking
- Routing
- WAN redundancy with HSRP and VPN IPsec, problem adding new tunnels
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WAN redundancy with HSRP and VPN IPsec, problem adding new tunnels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2011 11:07 AM - edited 03-04-2019 12:24 PM
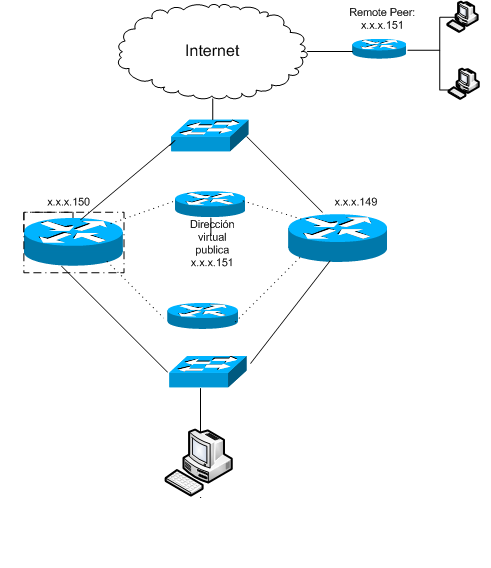
Hi, I have a topology with two Cisco routers 891 where I am doing other remote vendors to have as a peer the HSRP virtual address to set up the VPN. The problem is the client wants to add more sites via CCP (Cisco Configuration Professional) and due to the HSRP configuration is done through CLI, the crypto map assignation on WAN interface is overwritten and created tunnel goes down because it can´t establish virtual address connection.
The only solution i have found is to reconfigure through CLI the crypto map redundancy on WAN interface but this is a Customer problem who does not have the skills to set up this way, also wants to add and delete tunnels graphically respecting redundancy.
Is there any option or missing configuration to solve this problem?
This is the scenario:
Active router´s configuration:
!
version 15.0
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname GAIRET_1
!
boot-start-marker
boot-end-marker
!
logging buffered 52000
no logging console
!
no aaa new-model
!
!
ip cef
no ip domain lookup
ip domain name yourdomain.com
no ipv6 cef
!
!
multilink bundle-name authenticated
license udi pid CISCO891-K9 sn FTX151404HR
!
!
username gairet privilege 15 secret 5 $1$/FlP$ZJpvjKBYK07.czLV/94ob/
username ccpuser privilege 15 secret 5 $1$Y4Nq$2DOtuuo3tiLlH5jS7VmI8/
!
!
!
track 1 interface FastEthernet8 line-protocol
!
track 2 interface Vlan1 line-protocol
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key gairet address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
mode transport
crypto ipsec transform-set ESP-3DES-SHA1 esp-3des esp-sha-hmac
mode transport
crypto ipsec transform-set ESP-3DES-SHA2 esp-3des esp-sha-hmac
mode transport
!
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set ESP-3DES-SHA
match address 100
reverse-route
crypto dynamic-map SDM_DYNMAP_1 2
set transform-set ESP-3DES-SHA1
match address 101
reverse-route
crypto dynamic-map SDM_DYNMAP_1 3
set transform-set ESP-3DES-SHA2
match address 102
reverse-route
!
!
crypto map SDM_CMAP_1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
!
!
!
!
!
interface FastEthernet0
!
!
interface FastEthernet8
ip address 201.116.40.150 255.255.255.240
duplex auto
speed auto
standby 1 ip 201.116.40.151
standby 1 priority 150
standby 1 preempt
standby 1 name VPNHA
standby 1 track 2 decrement 100
crypto map SDM_CMAP_1 redundancy VPNHA /// This conf. is overwritten by "crypto map SDM_CMAP_1" after a new VPN is added on CCP
!
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
!
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-FE 1$
ip address 192.0.0.237 255.255.255.0
ip tcp adjust-mss 1452
standby 0 ip 192.0.0.236
standby 0 priority 150
standby 0 preempt
standby 0 track 1 decrement 100
!
!
interface Async1
no ip address
encapsulation slip
!
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
!
ip route 0.0.0.0 0.0.0.0 FastEthernet8 permanent
!
access-list 100 remark CCP_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 192.0.0.0 0.0.0.255 192.0.30.0 0.0.0.255
access-list 101 remark CCP_ACL Category=4
access-list 101 remark IPSec Rule
access-list 101 permit ip 192.0.0.0 0.0.0.255 192.0.28.0 0.0.0.255
access-list 102 remark CCP_ACL Category=4
access-list 102 remark IPSec Rule
access-list 102 permit ip 192.0.0.0 0.0.0.255 192.0.2.0 0.0.0.255
no cdp run
!
!
!
!
!
!
control-plane
!
Standby router´s configuration:
!
version 15.0
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname GAIRET_2
!
boot-start-marker
boot-end-marker
!
logging buffered 51200 warnings
!
no aaa new-model
!
!
no ip cef
no ip domain lookup
ip domain name yourdomain.com
no ipv6 cef
!
!
multilink bundle-name authenticated
license udi pid CISCO891-K9 sn FTX1513017R
!
!
username gairet privilege 15 secret 5 $1$ARWh$Tp9XeX5pWXThh99qQOmsm0
!
!
!
track 1 interface FastEthernet8 line-protocol
!
track 2 interface Vlan1 line-protocol
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key gairet address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
mode transport
crypto ipsec transform-set ESP-3DES-SHA1 esp-3des esp-sha-hmac
mode transport
crypto ipsec transform-set ESP-3DES-SHA2 esp-3des esp-sha-hmac
mode transport
!
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set ESP-3DES-SHA
match address 100
reverse-route
crypto dynamic-map SDM_DYNMAP_1 2
set transform-set ESP-3DES-SHA1
match address 101
reverse-route
crypto dynamic-map SDM_DYNMAP_1 3
set transform-set ESP-3DES-SHA2
match address 102
reverse-route
!
!
crypto map SDM_CMAP_1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
!
!
!
!
!
interface FastEthernet0
!
!
interface FastEthernet1
!
!
interface FastEthernet2
!
!
interface FastEthernet3
!
!
interface FastEthernet4
!
!
interface FastEthernet5
!
!
interface FastEthernet6
!
!
interface FastEthernet7
!
!
interface FastEthernet8
ip address 201.116.40.149 255.255.255.240
no ip route-cache
duplex auto
speed auto
standby 1 ip 201.116.40.151
standby 1 preempt
standby 1 name VPNHA
standby 1 track 2 decrement 10
crypto map SDM_CMAP_1 redundancy VPNHA
!
!
interface GigabitEthernet0
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-FE 1$
ip address 192.0.0.238 255.255.255.0
no ip route-cache
ip tcp adjust-mss 1452
standby 0 ip 192.0.0.236
standby 0 preempt
standby 0 track 1 decrement 10
!
!
interface Async1
no ip address
encapsulation slip
no ip route-cache
!
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
!
ip route 0.0.0.0 0.0.0.0 FastEthernet8 permanent
!
access-list 100 remark CCP_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 192.0.0.0 0.0.0.255 192.0.30.0 0.0.0.255
access-list 101 remark CCP_ACL Category=4
access-list 101 remark IPSec Rule
access-list 101 permit ip 192.0.0.0 0.0.0.255 192.0.28.0 0.0.0.255
access-list 102 remark CCP_ACL Category=4
access-list 102 remark IPSec Rule
access-list 102 permit ip 192.0.0.0 0.0.0.255 192.0.2.0 0.0.0.255
no cdp run
!
control-plane
!
Regards,
Alejandra Rodríguez
- Labels:
-
Routing Protocols
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide