- Cisco Community
- Technology and Support
- Networking
- Routing
- ZBF issue with remote VPN via virtuel interface on a 2911
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 02:14 AM - edited 08-08-2019 04:50 AM
Hi again and thanks in advance
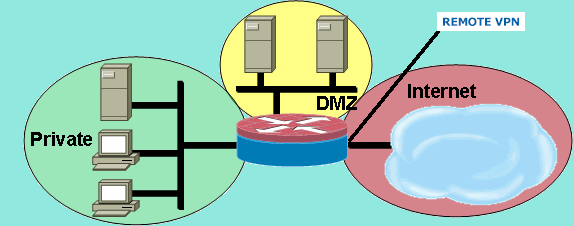
I just vent from static firewall to Zone Based Firewall as sugested in another discussion and so far so god and my setup nearly works perfect !! and here is the schematic
My issue is that when I connect remotely via VPN
- I have access to Internet (Outside)
- But can't connect to my servers ( DMZ)
My Server (DMZ) and VPN are on the same IP range, not that I think matters.
I'll try to give the VPN connections another IP range later.
Key elements in my config
ip dhcp excluded-address 192.168.100.1 192.168.100.49
ip dhcp excluded-address 192.168.50.1 192.168.50.49
ip dhcp pool VLAN200
network xx.xx.xx.96 255.255.255.240
default-router xx.xx.xx.97
dns-server 8.8.8.8 4.4.4.4
ip dhcp pool VLAN100
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
dns-server 192.168.100.1
ip dhcp pool VLAN50
network 192.168.50.0 255.255.255.0
default-router 192.168.50.1
dns-server 192.168.50.1
—————————————————————————————————————————————————————————————
I know the are the same !! / BUT easier to create an overview with fuld naming
class-map type inspect match-any CLASS-L4-IPSEC
match access-group name IPSEC_TRAFFIC
class-map type inspect match-all CLASS_CRYPTO_IPSEC_TRAFFIC_OUT_TO_SELF_PASS
match access-group name IPSEC_TRAFFIC
class-map type inspect match-any CLASS_CRYPTO_IPSEC_TRAFFIC_SELF_TO_OUT_PASS
match access-group name IPSEC_TRAFFIC
I know the are the same !! / BUT easier to create an overview with fuld naming
class-map type inspect match-any CLASS-L4-IP
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any CLASS_SELF_TO_OUT_INSPECT
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any CLASS_OUT_TO_SELF_INSPECT
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any CLASS-APPLE-REMOTE-DESKTOP
match access-group name APPLE-REMOTE-DESKTOP
class-map type inspect match-any CLASS-APPLE-AFP
match access-group name APPLE-FILE-SHARING
class-map type inspect match-any CLASS-INTERNET-TRAFFIC
match protocol http
match protocol https
match protocol dns
match protocol icmp
class-map type inspect match-any CLASS-FTP
match protocol ftp
match protocol ftps
class-map type inspect match-any CLASS-SSH
match protocol ssh
class-map type inspect match-any CLASS-IMAP-SMTP
match protocol imap
match protocol smtp
class-map type inspect match-any CLASS-ALLOW_ALL_TRAFFIC_THROUGH
match access-group name ALLOW_ALL_TRAFFIC_THROUGH
—————————————————————————————————————————————————————————————
policy-map type inspect POLICY-(PRIVATE-->DMZ)
class type inspect CLASS-FTP
inspect
class type inspect CLASS-SSH
inspect
class type inspect CLASS-APPLE-REMOTE-DESKTOP
inspect
class type inspect CLASS-APPLE-AFP
inspect
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-IMAP-SMTP
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(SELF-->INTERNET)
class type inspect CLASS_CRYPTO_IPSEC_TRAFFIC
pass
class type inspect CLASS_SELF_TO_OUT_INSPECT
inspect
class class-default
drop log
policy-map type inspect POLICY-(INTERNET-->SELF)
class type inspect CLASS_CRYPTO_IPSEC_TRAFFIC
pass
class type inspect CLASS_OUT_to_SELF_INSPECT
inspect
class class-default
drop log
policy-map type inspect POLICY-(PRIVATE-->INTERNET)
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-FTP
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(INTERNET-->DMZ)
class type inspect CLASS-IMAP-SMTP
inspect
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(DMZ-->INTERNET)
class type inspect CLASS-ALLOW_ALL_TRAFFIC_THROUGH
inspect
class class-default
drop log
—————————————————————————————————————————————————————————————
zone security PRIVATE-ZONE
zone security INTERNET-ZONE
zone security DMZ-ZONE
—————————————————————————————————————————————————————————————
zone-pair security PRIVATE-TO-DMZ source PRIVATE-ZONE destination DMZ-ZONE
service-policy type inspect POLICY-(PRIVATE-->DMZ)
zone-pair security PRIVATE-TO-INTERNET source PRIVATE-ZONE destination INTERNET-ZONE
service-policy type inspect POLICY-(PRIVATE-->INTERNET)
zone-pair security INTERNET-TO-DMZ source INTERNET-ZONE destination DMZ-ZONE
service-policy type inspect POLICY-(INTERNET-->DMZ)
zone-pair security DMZ-TO-INTERNET source DMZ-ZONE destination INTERNET-ZONE
service-policy type inspect POLICY-(DMZ-->INTERNET)
zone-pair security SELF-TO-VPN-INTERNET source self destination INTERNET-ZONE
service-policy type inspect POLICY-(SELF-->INTERNET)
zone-pair security VPN-INTERNET-TO-SELF source INTERNET-ZONE destination self
service-policy type inspect POLICY-(INTERNET-->SELF)
—————————————————————————————————————————————————————————————
crypto isakmp policy 150
encr aes 256
authentication pre-share
group 2
crypto isakmp client configuration group SAS-VPN
key XXXXXX
dns 208.67.222.222 208.67.220.220
pool REMOTE-VPN-CLIENTS
acl 101
crypto isakmp profile SAS-VPN-PROFILE
match identity group SAS-VPN
client authentication list userauthen
isakmp authorization list userauthen
client configuration address initiate
client configuration address respond
virtual-template 1
crypto ipsec transform-set SAS-VPN-1 esp-aes 256 esp-sha-hmac
crypto ipsec profile SAS-VPN-VTUNNEL-PROFILE
set security-association lifetime kilobytes disable
set security-association lifetime seconds 86400
set transform-set SAS-VPN-1
set isakmp-profile SAS-VPN-PROFILE
interface GigabitEthernet0/0
description ISP WAN (Wide Area Network)
ip address XXX.XXX.XXX.190 255.255.255.252
ip nat outside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
duplex auto
speed auto
interface GigabitEthernet0/1
description LAN (Local Area Network)
ip address pool VLAN100
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
interface GigabitEthernet0/2
description LAN (Local Area Network)
ip address pool VLAN50
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
interface Vlan200
description HWIC-4ESW_LAN - SERVER PARK
ip address XXX.XXX.XXX.97 255.255.255.224
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
interface Virtual-Template1 type tunnel
description Virtuel VPN Forbindelse
ip unnumbered GigabitEthernet0/0
ip nat inside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile SAS-VPN-VTUNNEL-PROFILE
—————————————————————————————————————————————————————————————
router eigrp 100
network 80.0.0.0
network 87.0.0.0
network 192.168.0.0
router ospf 123
network 80.0.0.0 0.255.255.255 area 0
network 87.0.0.0 0.255.255.255 area 0
network 192.0.0.0 0.255.255.255 area 0
ip local pool REMOTE-VPN-CLIENTS 80.xx.xx.123 80.xx.xx.126
ip forward-protocol nd
ip nat inside source list 1 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 87.63.227.189
ip access-list extended ALLOW_ALL_TRAFFIC_TROUGH
permit ip any any
ip access-list extended APPLE-FILE-SHARING
permit tcp any any eq 427
permit tcp any any eq 548
ip access-list extended APPLE-REMOTE-DESKTOP
permit tcp any any eq 22
permit udp any any eq 3283
permit tcp any any eq 5900
permit udp any any eq 5900
permit tcp any any eq 3283
ip access-list extended EIMS-MAILSERVER
permit tcp any any eq 587
permit tcp any any eq smtp
permit tcp any any eq 143
ip access-list extended EIMS-MAILSERVER-ADMIN
permit tcp any any eq 4199
ip access-list extended IPSEC_TRAFFIC
permit udp any eq isakmp any
permit udp any eq non500-isakmp any
permit ahp any any
permit esp any any
permit udp any any eq non500-isakmp
permit udp any any eq isakmp
—————————————————————————————————————————————————————————————
access-list 1 permit 192.168.100.0 0.0.0.225
access-list 1 permit 192.168.50.0 0.0.0.255
access-list 123 permit esp any any
access-list 123 permit udp any any eq non500-isakmp
access-list 123 permit ahp any any
access-list 123 permit udp any any eq isakmp
Solved! Go to Solution.
- Labels:
-
Other Routers
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 08:22 AM
Hello,
based on your configuration, I have come up with the below. Since I haven't been able to match all the classes and policies to what is already in your configuration, I have created new ones. Basically, you need two zone pairs. In the out to self policy, I am not sure if you have to inspect or pass the IPSEC traffic, so toggle these values.
ip access-list extended IPSEC_TRAFFIC
permit udp any eq isakmp any
permit ahp any any
permit esp any any
permit udp any eq non500-isakmp any
!
class-map type inspect match-any CLASS_OUT_TO_SELF
match access-group name IPSEC_TRAFFIC
!
policy-map type inspect POLICY_OUT_TO_SELF
class type inspect CLASS_OUT_TO_SELF
inspect or pass <-- toggle these values
class class-default
drop log
!
zone-pair security OUT_TO_SELF source INTERNET-ZONE destination self
service-policy type inspect POLICY_OUT_TO_SELF
class-map type inspect match-any CLASS_SELF_TO_OUT_PASS
match access-group name IPSEC_TRAFFIC
class-map type inspect match-any CLASS_SELF_TO_OUT_INSPECT
match protocol icmp
match protocol tcp
match protocol udp
!
policy-map type inspect POLICY_SELF_TO_OUT
class type inspect CLASS_SELF_TO_OUT_PASS
pass
class type inspect CLASS_SELF_TO_OUT_INSPECT
inspect
class class-default
drop log
!
zone-pair security SELF_TO_OUT source self destination INTERNET-ZONE
service-policy type inspect POLICY_SELF_TO_OUT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 03:21 AM
Hello,
post the full running configuration. I cannot see how your client pool is configured. Make sure that it contains an ACL that allows traffic from the DMZ to any. It should look like this (the lines in bold must match):
crypto isakmp client configuration group cisco
key cisco
dns 8.8.8.8
domain cisco.com
pool client_pool
acl 101
!
interface Vlan200
description HWIC-4ESW_LAN - SERVER PARK
ip address XXX.XXX.XXX.97 255.255.255.224
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
!
access-list 101 permit ip XXX.XXX.XXX.97 0.0.0.31 any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 04:06 AM
hostname R2911
!
boot-start-marker
boot system flash c2900-universalk9-mz.SPA.154-3.M.bin
boot-end-marker
!
!
! card type command needed for slot/vwic-slot 0/2
no logging console
enable secret 5 $1$8LqH$9JXseHd62tFJvW3cp9gxp.
!
aaa new-model
!
!
aaa authentication login userauthen local
aaa authorization network userauthen local
!
!
!
!
!
aaa session-id common
!
memory-size iomem 25
!
no ipv6 cef
no ip source-route
!
!
!
ip dhcp excluded-address 192.168.100.1 192.168.100.49
ip dhcp excluded-address 192.168.50.1 192.168.50.49
!
ip dhcp pool VLAN200
network XXX.XXX.XXX.96 255.255.255.240
default-router XXX.XXX.XXX.97
dns-server 8.8.8.8 4.4.4.4
!
ip dhcp pool VLAN100
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
dns-server 192.168.100.1
!
ip dhcp pool VLAN50
network 192.168.50.0 255.255.255.0
default-router 192.168.50.1
dns-server 192.168.50.1
!
!
ip domain name mediadesign.dk
ip name-server 208.67.222.222
ip name-server 208.67.220.220
ip name-server 62.243.0.166
ip name-server 194.192.207.166
ip cef
ip cef accounting non-recursive
!
multilink bundle-name authenticated
!
!
!
!
!
crypto pki token default removal timeout 0
!
crypto pki trustpoint TP-self-signed-2506629599
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2506629599
revocation-check none
rsakeypair TP-self-signed-2506629599
!
!
crypto pki certificate chain TP-self-signed-2506629599
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32353036 36323935 3939301E 170D3137 31313231 31383331
34355A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 35303636
32393539 3930819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100B864 001074AA 3ACB326E 0746CC7D 5A1A7E4B 92667702 844CEF49 166B0D95
DAF80B11 3A0C8AF0 A4A4C5D4 491FB34D 28F83027 8E882C56 16890795 80538DF4
754EA389 DBCD4C5F 24ED9E61 D4A5FD94 B2A6DBAA D2A624EB 23D4E3DB CD2B27EC
73277F09 5908425D 70D1212B 946D3A92 9C628C55 96FB2A75 376BF8A4 B2632D47
B3030203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 1421FD81 D44399EA FFD554A4 97C6A7DC C3C72BD8 FD301D06
03551D0E 04160414 21FD81D4 4399EAFF D554A497 C6A7DCC3 C72BD8FD 300D0609
2A864886 F70D0101 05050003 8181008E 5E8AFBFC 86243F4E AD1785BC 72C1FC2C
F2CB747E E70E5983 F1A1F60B 539C67F7 028712AD 1A9A3154 7459C967 A51AE7CD
1C8DB2A5 0BF089EB B9B1A24C 951C677B CBD18212 CC59A5A3 8F3AB203 9B839185
93798F89 141FCCBD F67CCDE2 1428963A 982720ED 59D95C02 DCC9CD7D B842BE47
C37855E0 7901AFD3 B71FA3A4 B48ADD
quit
voice-card 0
!
!
!
!
!
!
!
!
license feature snasw
license udi pid CISCO2911/K9 sn FTX1814ALDX
license accept end user agreement
license boot module c2900 technology-package securityk9
license boot module c2900 technology-package uck9
license boot module c2900 technology-package datak9
hw-module pvdm 0/0
!
hw-module pvdm 0/1
!
!
!
object-group network DMZ-FILEMAKER
description FILEMAKER server in DMZ
host XXX.XXX.XXX.99
!
object-group network DMZ-MAIL
description EMAIL servers in DMZ
host XXX.XXX.XXX.100
host XXX.XXX.XXX.115
!
object-group network DMZ-MEDIADESIGN
description MEDIADESIGN file-www-ftp server in DMZ
host XXX.XXX.XXX.101
host XXX.XXX.XXX.102
host XXX.XXX.XXX.103
host XXX.XXX.XXX.104
host XXX.XXX.XXX.105
host XXX.XXX.XXX.106
host XXX.XXX.XXX.107
host XXX.XXX.XXX.108
host XXX.XXX.XXX.109
host XXX.XXX.XXX.110
username XXX
username xxx
!
redundancy
!
!
!
!
!
ip ssh time-out 60
ip ssh version 2
!
class-map type inspect match-any L4-ip-class
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any INTERNET-TRAFFIC-CLASS
match protocol http
match protocol https
match protocol dns
match protocol icmp
class-map type inspect match-all FILEMAKER-SERVER-CLASS
match access-group name INTERNET-->DMZ-FILEMAKER
match access-group 105
class-map type inspect match-any NTP-CLASS
match protocol ntp
class-map type inspect match-all MEDIADESIGN-SERVER-CLASS
match access-group name INTERNET-->DMZ-MEDIADESIGN
match class-map NTP-CLASS
class-map type inspect match-any APPLE-REMOTE-DESKTOP
match access-group name APPLE-REMOTE-DESKTOP
class-map type inspect match-any FTP-CLASS
match protocol ftp
match protocol ftps
class-map type inspect match-any SSH-CLASS
match protocol ssh
class-map type inspect match-any APPLE-AFP
match access-group name APPLE-FILE-SHARING
class-map type inspect match-any IMAP-SMTP-CLASS
match protocol imap
match protocol imap3
match protocol imaps
match protocol smtp
match protocol pop3
match protocol pop3s
class-map type inspect match-all MAIL-SERVER-CLASS
match access-group name INTERNET-->DMZ-EMAIL
match class-map IMAP-SMTP-CLASS
match access-group name EIMS-MAILSERVER
class-map type inspect match-any L4-ipsec-class
match access-group name IPSECtraffic
!
!
policy-map type inspect PRIVATE-->DMZ-POLICY
class type inspect FILEMAKER-SERVER-CLASS
inspect
class type inspect FTP-CLASS
inspect
class type inspect SSH-CLASS
inspect
class type inspect APPLE-REMOTE-DESKTOP
inspect
class type inspect APPLE-AFP
inspect
class type inspect L4-ip-class
inspect
class type inspect MAIL-SERVER-CLASS
inspect
class class-default
drop log
policy-map type inspect ALLOW-ALL-ISAKMP
class type inspect L4-ipsec-class
pass
class class-default
drop
policy-map type inspect PRIVATE-->INTERNET-POLICY
class type inspect INTERNET-TRAFFIC-CLASS
inspect
class type inspect FTP-CLASS
inspect
class type inspect L4-ip-class
inspect
class class-default
drop log
policy-map type inspect INTERNET-->DMZ-POLICY
class type inspect INTERNET-TRAFFIC-CLASS
inspect
class type inspect MEDIADESIGN-SERVER-CLASS
inspect
class type inspect FILEMAKER-SERVER-CLASS
inspect
class type inspect MAIL-SERVER-CLASS
inspect
class type inspect L4-ip-class
inspect
class class-default
drop log
policy-map type inspect DMZ-->INTERNET
class type inspect MAIL-SERVER-CLASS
inspect
class type inspect L4-ip-class
inspect
class class-default
drop log
!
zone security PRIVATE-ZONE
zone security INTERNET-ZONE
zone security DMZ-ZONE
zone security VPN-ZONE
zone-pair security PRIVATE-TO-DMZ source PRIVATE-ZONE destination DMZ-ZONE
service-policy type inspect PRIVATE-->DMZ-POLICY
zone-pair security PRIVATE-TO-INTERNET source PRIVATE-ZONE destination INTERNET-ZONE
service-policy type inspect PRIVATE-->INTERNET-POLICY
zone-pair security INTERNET-TO-DMZ source INTERNET-ZONE destination DMZ-ZONE
service-policy type inspect INTERNET-->DMZ-POLICY
zone-pair security DMZ-TO-INTERNET source DMZ-ZONE destination INTERNET-ZONE
service-policy type inspect DMZ-->INTERNET
zone-pair security VPN-TO-SELFXX source INTERNET-ZONE destination self
service-policy type inspect ALLOW-ALL-ISAKMP
!
!
crypto isakmp policy 150
encr aes 256
authentication pre-share
group 2
!
crypto isakmp client configuration group SAS-VPN
key XXXXXX
dns 208.67.222.222 208.67.220.220
pool REMOTE-VPN-CLIENTS
crypto isakmp profile SAS-VPN-PROFILE
match identity group SAS-VPN
client authentication list userauthen
isakmp authorization list userauthen
client configuration address initiate
client configuration address respond
virtual-template 1
!
!
crypto ipsec transform-set SAS-VPN-1 esp-aes 256 esp-sha-hmac
!
crypto ipsec profile SAS-VPN-VTUNNEL-PROFILE
set security-association lifetime kilobytes disable
set security-association lifetime seconds 86400
set transform-set SAS-VPN-1
set isakmp-profile SAS-VPN-PROFILE
!
!
!
!
!
!
!
interface Loopback0
ip address 10.108.1.1 255.255.255.0
!
interface Embedded-Service-Engine0/0
no ip address
!
interface GigabitEthernet0/0
description ISP WAN (Wide Area Network)
ip address XXX.XXX.XXX.190 255.255.255.252
ip nat outside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
duplex auto
speed auto
!
interface GigabitEthernet0/1
description LAN (Local Area Network)
ip address pool VLAN100
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
!
interface GigabitEthernet0/2
description LAN (Local Area Network)
ip address pool VLAN50
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
!
interface Serial0/0/0
no ip address
!
interface FastEthernet0/1/0
switchport access vlan 200
no ip address
!
interface FastEthernet0/1/1
switchport access vlan 200
no ip address
!
interface FastEthernet0/1/2
switchport access vlan 200
no ip address
!
interface FastEthernet0/1/3
switchport access vlan 200
no ip address
!
interface Virtual-Template1 type tunnel
description Virtuel VPN Forbindelse
ip unnumbered GigabitEthernet0/0
ip nat inside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile SAS-VPN-VTUNNEL-PROFILE
!
interface Vlan1
no ip address
!
interface Vlan50
description GUEST NETWORK DHCP POOL
no ip address
ip nat inside
ip virtual-reassembly in
!
interface Vlan100
description INTERNAL NETWORK DHCP POOL
ip address dhcp
ip nat inside
ip virtual-reassembly in
!
interface Vlan200
description HWIC-4ESW_LAN - SERVER PARK
ip address XXX.XXX.XXX.97 255.255.255.224
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
!
!
!
router eigrp 100
network 80.0.0.0
network 87.0.0.0
network 192.168.0.0
!
router ospf 123
network 80.0.0.0 0.255.255.255 area 0
network 87.0.0.0 0.255.255.255 area 0
network 192.0.0.0 0.255.255.255 area 0
!
ip local pool REMOTE-VPN-CLIENTS XXX.XXX.XXX.123 XXX.XXX.XXX.126
ip forward-protocol nd
!
no ip http server
ip http authentication local
ip http secure-server
!
ip nat inside source list 1 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 XXX.XXX.XXX.189
!
ip access-list extended APPLE-FILE-SHARING
permit tcp any any eq 427
permit tcp any any eq 548
ip access-list extended APPLE-REMOTE-DESKTOP
permit tcp any any eq 22
permit udp any any eq 3283
permit tcp any any eq 5900
permit udp any any eq 5900
permit tcp any any eq 3283
ip access-list extended EIMS-MAILSERVER
permit tcp any any eq 587
ip access-list extended INTERNET-->DMZ-EMAIL
permit ip any object-group DMZ-MAIL
ip access-list extended INTERNET-->DMZ-FILEMAKER
permit ip any object-group DMZ-FILEMAKER
ip access-list extended INTERNET-->DMZ-MEDIADESIGN
permit ip any object-group DMZ-MEDIADESIGN
ip access-list extended IPSECtraffic
permit esp any any
permit udp any any eq isakmp
permit ahp any any
permit udp any any eq non500-isakmp
!
access-list 1 permit 192.168.100.0 0.0.0.225
access-list 1 permit 192.168.50.0 0.0.0.255
access-list 1 permit XXX.XXX.XXX.96 0.0.0.31
access-list 105 remark ## FILEMAKER SERVER ##
!
no cdp run
!
!
!
!
!
!
!
control-plane
!
!
!
!
mgcp profile default
!
!
!
!
!
gatekeeper
shutdown
!
!
telephony-service
max-ephones 10
max-conferences 8 gain -6
transfer-system full-consult
!
!
!
line con 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport input all
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
session-timeout 30
transport input ssh
line vty 5 15
session-timeout 30
transport input ssh
!
scheduler allocate 20000 1000
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 08:22 AM
Hello,
based on your configuration, I have come up with the below. Since I haven't been able to match all the classes and policies to what is already in your configuration, I have created new ones. Basically, you need two zone pairs. In the out to self policy, I am not sure if you have to inspect or pass the IPSEC traffic, so toggle these values.
ip access-list extended IPSEC_TRAFFIC
permit udp any eq isakmp any
permit ahp any any
permit esp any any
permit udp any eq non500-isakmp any
!
class-map type inspect match-any CLASS_OUT_TO_SELF
match access-group name IPSEC_TRAFFIC
!
policy-map type inspect POLICY_OUT_TO_SELF
class type inspect CLASS_OUT_TO_SELF
inspect or pass <-- toggle these values
class class-default
drop log
!
zone-pair security OUT_TO_SELF source INTERNET-ZONE destination self
service-policy type inspect POLICY_OUT_TO_SELF
class-map type inspect match-any CLASS_SELF_TO_OUT_PASS
match access-group name IPSEC_TRAFFIC
class-map type inspect match-any CLASS_SELF_TO_OUT_INSPECT
match protocol icmp
match protocol tcp
match protocol udp
!
policy-map type inspect POLICY_SELF_TO_OUT
class type inspect CLASS_SELF_TO_OUT_PASS
pass
class type inspect CLASS_SELF_TO_OUT_INSPECT
inspect
class class-default
drop log
!
zone-pair security SELF_TO_OUT source self destination INTERNET-ZONE
service-policy type inspect POLICY_SELF_TO_OUT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2019 03:01 AM
Your solution didn’t solve the issue -
But it boosted the general response time and flov speed tremendously
So could have been and still was some of the problem.
So nice spottet
I think I have to analyse my Classes and Policies and Zone-pairs a little deeper
Before implementing ZBF again
Somebody on the list pointet at that I needed 2 ZONE-PAIR’s one for both ways
INTERNET to SELF
SELF TO INTERNET
That fixed my problem
But then I found out that ZONE-PAIR "INTERNET to DMZ" wasn’t running smooth
I could ping through but UDP keeps dropping in the log and I have no connection in or out for Application services.
I have to dig a little deeper into the manuals to see what’s wrong ;-)
Thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2019 05:11 AM
Hello,
can you, for future reference, post your final, working (if it is working) configuration ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 05:18 AM - edited 08-01-2019 05:19 AM
Hello
@lars.arler wrote:
My issue is that when I connect remotely via VPN
- I have access to Internet (Outside)
- But can't connect to my servers ( DMZ)
My Server (DMZ) and VPN are on the same IP range, not that I think matters.
I'll try to give the VPN connections another IP range later.
I'm puzzled by the zone-pair to SELF set up !!
zone-pair security VPN-TO-SELFXX source INTERNET-ZONE destination SELF
service-policy type inspect ALLOW-ALL-ISAKMPShouldn't the SELF not have free access to all networks by default ??
How should I approach this problem solving ??
No
My understanding the self zone is for control plane traffic , to/from router only (non transit traffic) By default traffic from the other zones are allowed to access the router so amending this self zone allows you control the access to the router from the other zones.
I see you have a pass action applied to the vpn-self zone pair now when using this action you need to make allowances for the return traffic meaning you need an additional zone-pair in the other direction with the pass action.
Can you confirm what exactly isnt working, connection from the internet to you router or connection to/from internet and dmz zones?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 08:38 AM
Hi Paul and thanks for taking your time.
PRIVAT --> INTERNET = Works
PRIVAT --> DMZ = Works
DMZ --> INTERNET = Works
INTERNET --> DMZ = WORKS
It is when I try to connect via REMOTE VPN
That I can browse the Internet - but I can't browse my own web-server and mail-server
So it seems as that I can't connect to the DMZ-ZONE when on REMOTE VPN
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide