- Cisco Community
- Technology and Support
- Networking
- Routing
- ZBF problem with remote VPN via virtuel interface on a 2911
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 09:57 AM - edited 08-13-2019 04:14 AM
Hi again and thanks in advance.
I had some good help from Georg Pauwen before and he found som issues and directed me in the right direction but I'm still stocked with this problem even after implementing his fixes
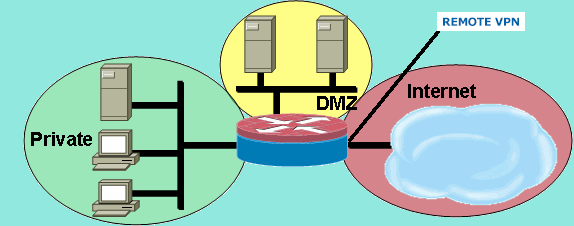
My Zone Based Firewall setup.
My problem is still that when I connect remotely via VPN.
- I connect with some log issues to my router and data flows through VPN
%CRYPTO-6-IKMP_MODE_FAILURE: Processing of Aggressive mode failed with peer at 77.241.128.136
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to down
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up
%FW-6-DROP_PKT: Dropping Unknown-l4 session 80.XX.XX.126:0 80.XX.XX.100:0 on zone-pair INTERNET-TO-DMZ class class-default due to DROP action found in policy-map with ip ident 0
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to down
%IP_VFR-7-FEATURE_DISABLE_IN: VFR(in) is manually disabled through CLI; VFR support for features that have internally enabled, will be made available only when VFR is enabled manually on interface Virtual-Access2- I have full access to the Internet (Outside) through Remote VPN
- But can't connect to my servers ( DMZ)
%FW-6-DROP_PKT: Dropping Unknown-l4 session 80.XX.XX.126:0 80.XX.XX.100:0 on zone-pair INTERNET-TO-DMZ class class-default due to DROP action found in policy-map with ip ident 0Indicates that my policy maps in zone-pair INTERNET-TO-DMZ are wrong or inadequate.- I can't even ping the servers the DMZ via the VPN connection. but the default-router 80.xx.xx.97 answer the ping request.
My Server (DMZ) and VPN are on the same IP range, not that I think matters.
I have read CISCO ZBF guide many times now, but I really can't figure out what seems to be the problem. I even deleted all ZBF setting and tried to start all over again but with no luck.
So I would be thankful for a pair of keen eyes to see if I have an obvious mis match somewhere in my config...
Key elements in my config
R2911
boot system flash c2900-universalk9-mz.SPA.154-3.M.bin
ip dhcp excluded-address 192.168.100.1 192.168.100.49
ip dhcp excluded-address 192.168.50.1 192.168.50.49
ip dhcp pool VLAN200
network 80.xx.xx.96 255.255.255.240
default-router 80.xx.xx.97
dns-server 8.8.8.8 4.4.4.4
ip dhcp pool VLAN100
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
dns-server 192.168.100.1
ip dhcp pool VLAN50
network 192.168.50.0 255.255.255.0
default-router 192.168.50.1
dns-server 192.168.50.1
class-map type inspect match-any CLASS_CRYPTO_IPSEC_PASS
match access-group name IPSEC_TRAFFICclass-map type inspect match-any CLASS-L4-IP
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any CLASS-APPLE-REMOTE-DESKTOP
match access-group name APPLE-REMOTE-DESKTOP
class-map type inspect match-any CLASS-APPLE-AFP
match access-group name APPLE-FILE-SHARING
class-map type inspect match-any CLASS-INTERNET-TRAFFIC
match protocol http
match protocol https
match protocol dns
match protocol icmp
class-map type inspect match-any CLASS-FTP
match protocol ftp
match protocol ftps
class-map type inspect match-any CLASS-SSH
match protocol ssh
class-map type inspect match-any CLASS-IMAP-SMTP
match protocol imap
match protocol smtp
class-map type inspect match-any CLASS-ALLOW_ALL_TRAFFIC_THROUGH
match access-group name ALLOW_ALL_TRAFFIC_THROUGH
policy-map type inspect POLICY-(PRIVATE-->DMZ)
class type inspect CLASS-FTP
inspect
class type inspect CLASS-SSH
inspect
class type inspect CLASS-APPLE-REMOTE-DESKTOP
inspect
class type inspect CLASS-APPLE-AFP
inspect
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-IMAP-SMTP
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(SELF-->INTERNET)
class type inspect CLASS_CRYPTO_IPSEC_PASS
pass
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(INTERNET-->SELF)
class type inspect CLASS_CRYPTO_IPSEC_PASS
pass
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(PRIVATE-->INTERNET)
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-FTP
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(INTERNET-->DMZ)
class type inspect CLASS-IMAP-SMTP
inspect
class type inspect CLASS-INTERNET-TRAFFIC
inspect
class type inspect CLASS-L4-IP
inspect
class class-default
drop log
policy-map type inspect POLICY-(DMZ-->INTERNET)
class type inspect CLASS-ALLOW_ALL_TRAFFIC_THROUGH
inspect
class class-default
drop log
zone security PRIVATE-ZONE
zone security INTERNET-ZONE
zone security DMZ-ZONE
The Green zone-pairs works fine
zone-pair security PRIVATE-TO-DMZ source PRIVATE-ZONE destination DMZ-ZONE
service-policy type inspect POLICY-(PRIVATE-->DMZ)
zone-pair security PRIVATE-TO-INTERNET source PRIVATE-ZONE destination INTERNET-ZONE
service-policy type inspect POLICY-(PRIVATE-->INTERNET)
zone-pair security INTERNET-TO-DMZ source INTERNET-ZONE destination DMZ-ZONE
service-policy type inspect POLICY-(INTERNET-->DMZ)
zone-pair security DMZ-TO-INTERNET source DMZ-ZONE destination INTERNET-ZONE
service-policy type inspect POLICY-(DMZ-->INTERNET)
zone-pair security SELF-TO-VPN-INTERNET source self destination INTERNET-ZONE
service-policy type inspect POLICY-(SELF-->INTERNET)
zone-pair security VPN-INTERNET-TO-SELF source INTERNET-ZONE destination self
service-policy type inspect POLICY-(INTERNET-->SELF)
crypto isakmp policy 150
encr aes 256
authentication pre-share
group 2
crypto isakmp client configuration group SAS-VPN
key XXXXXX
dns 208.67.222.222 208.67.220.220
pool REMOTE-VPN-CLIENTS
acl 101
crypto isakmp profile SAS-VPN-PROFILE
match identity group SAS-VPN
client authentication list userauthen
isakmp authorization list userauthen
client configuration address initiate
client configuration address respond
virtual-template 1
crypto ipsec transform-set SAS-VPN-1 esp-aes 256 esp-sha-hmac
crypto ipsec profile SAS-VPN-VTUNNEL-PROFILE
set security-association lifetime kilobytes disable
set security-association lifetime seconds 86400
set transform-set SAS-VPN-1
set isakmp-profile SAS-VPN-PROFILE
interface GigabitEthernet0/0
description ISP WAN (Wide Area Network)
ip address 87.XXX.XXX.190 255.255.255.252
ip nat outside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
duplex auto
speed auto
interface GigabitEthernet0/1
description LAN (Local Area Network)
ip address pool VLAN100
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
interface GigabitEthernet0/2
description LAN (Local Area Network)
ip address pool VLAN50
ip nat inside
ip virtual-reassembly in
zone-member security PRIVATE-ZONE
duplex auto
speed auto
interface Vlan200
description HWIC-4ESW_LAN - SERVER PARK
ip address 80.XXX.XXX.97 255.255.255.224
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
interface Virtual-Template1 type tunnel
description Virtuel VPN Forbindelse
ip unnumbered GigabitEthernet0/0
ip nat inside
ip virtual-reassembly in
zone-member security INTERNET-ZONE
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile SAS-VPN-VTUNNEL-PROFILE
router eigrp 100
network 80.0.0.0
network 87.0.0.0
network 192.168.0.0
router ospf 123
network 80.0.0.0 0.255.255.255 area 0
network 87.0.0.0 0.255.255.255 area 0
network 192.0.0.0 0.255.255.255 area 0
ip local pool REMOTE-VPN-CLIENTS 80.xx.xx.123 80.xx.xx.126
ip forward-protocol nd
ip nat inside source list 1 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 87.63.227.189
ip access-list extended ALLOW_ALL_TRAFFIC_TROUGH
permit ip any any
ip access-list extended APPLE-FILE-SHARING
permit tcp any any eq 427
permit tcp any any eq 548
ip access-list extended APPLE-REMOTE-DESKTOP
permit tcp any any eq 22
permit udp any any eq 3283
permit tcp any any eq 5900
permit udp any any eq 5900
permit tcp any any eq 3283
ip access-list extended EIMS-MAILSERVER
permit tcp any any eq 587
permit tcp any any eq smtp
permit tcp any any eq 143
ip access-list extended EIMS-MAILSERVER-ADMIN
permit tcp any any eq 4199
ip access-list extended IPSEC_TRAFFIC
permit ahp any any
permit esp any any
permit udp any any eq non500-isakmp
permit udp any any eq isakmp
access-list 1 permit 192.168.100.0 0.0.0.225
access-list 1 permit 192.168.50.0 0.0.0.255
access-list 123 permit esp any any
access-list 123 permit udp any any eq non500-isakmp
access-list 123 permit ahp any any
access-list 123 permit udp any any eq isakmp
Solved! Go to Solution.
- Labels:
-
Other Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2019 02:44 AM - edited 08-13-2019 04:10 AM
I finally found a solution to my problem ;-)
My (DMZ) and (Remote VPN) are on the same IP range, BUT in different ZONES
- AND that is a problem !! - when (Remote VPN) is in the INTERNET-ZONE.
So I had to move (Remote VPN) into the (DMZ-ZONE) and then everything works... And my Remote VPN users is trusted users ..
Or keep (Remote VPN) in the (INTERNET-ZONE) and then give it a IP range of it ovn (f.ex. 10.10.10.0 - 255.255.255.0) TESTED and works to
interface Virtual-Template1 type tunnel
description Virtuel VPN Forbindelse
ip unnumbered GigabitEthernet0/0
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile SAS-VPN-VTUNNEL-PROFILE
But anyways thanks to you all for taking your time to review my config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2019 02:44 AM - edited 08-13-2019 04:10 AM
I finally found a solution to my problem ;-)
My (DMZ) and (Remote VPN) are on the same IP range, BUT in different ZONES
- AND that is a problem !! - when (Remote VPN) is in the INTERNET-ZONE.
So I had to move (Remote VPN) into the (DMZ-ZONE) and then everything works... And my Remote VPN users is trusted users ..
Or keep (Remote VPN) in the (INTERNET-ZONE) and then give it a IP range of it ovn (f.ex. 10.10.10.0 - 255.255.255.0) TESTED and works to
interface Virtual-Template1 type tunnel
description Virtuel VPN Forbindelse
ip unnumbered GigabitEthernet0/0
ip nat inside
ip virtual-reassembly in
zone-member security DMZ-ZONE
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile SAS-VPN-VTUNNEL-PROFILE
But anyways thanks to you all for taking your time to review my config.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide