- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- Re: Cisco SD-WAN Global Forum : Quick Guide to Design, Deploy, Operate, and Maintain - AMA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco SD-WAN Global Forum : Quick Guide to Design, Deploy, Operate, and Maintain - AMA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021
10:57 PM
- last edited on
03-10-2021
03:50 PM
by
Jimena Saez
![]()
| Español | Português | Français | Русский | 日本語 | 简体中文 |
All the knowledge of these four experts at your disposal!
Cisco Software-Defined Wide Area Network (SD-WAN) provides a highly scalable, resilient, and secure network infrastructure. With advanced security features built into the solution, automation, centralized management, and monitoring, Cisco SD-WAN enables you to control your network through a single dashboard, reduce operating costs, and ensure the best possible experience for your users in local applications or on the cloud.
In this event, the experts will help you understand how Cisco SD-WAN is designed and its main benefits.
They will explore everything from the basic solution design, which license to choose, or which router to select, to overall design and deployment best practices. vManage allows you to configure devices, templates, security / control policies and much more... What if, for some reason, vManage fails? We will help you master an understanding of the policy framework and common troubleshooting tools and learn from programmatic methods to create backups in the SD-WAN environment.
This event is for Cisco SD-WAN beginners and advanced professionals.
To participate in this event, please use the 
Ask questions from Monday, March 8 to Friday, March 19, 2021
 Guilherme Lyra is a Solutions Architect focused on the Enterprise Networking area. With more than 14 years of experience in networking and security technologies, he has designed and led the implementation of projects with national and global extension for companies in segments such as retail, manufacturing, utilities, and government agencies. Guilherme has also conducted training on Software-Defined Networks and WAN optimization. He holds Cisco CCNP, Cisco CCDP, Juniper JNCIA, and Meraki CMNA certifications.
Guilherme Lyra is a Solutions Architect focused on the Enterprise Networking area. With more than 14 years of experience in networking and security technologies, he has designed and led the implementation of projects with national and global extension for companies in segments such as retail, manufacturing, utilities, and government agencies. Guilherme has also conducted training on Software-Defined Networks and WAN optimization. He holds Cisco CCNP, Cisco CCDP, Juniper JNCIA, and Meraki CMNA certifications. Danny Blais joined Cisco in 2000 in the role of Lab Administrator. In 2004, he moved to RTP, North Carolina for one year to be part of an incubator program leading him to a Systems Architect role. He is currently based out of Montréal and supports a major enterprise account in the Québec province. Danny has a college degree in computer science with a networking specialty. He has specialized in many Cisco technologies over the years, from Unified Communications to Data Center and now for the last couple of years Cisco SD-WAN. He holds multiple Cisco certifications: CCNA, CCDA, CCNP, CCDP, and CMNA.
Danny Blais joined Cisco in 2000 in the role of Lab Administrator. In 2004, he moved to RTP, North Carolina for one year to be part of an incubator program leading him to a Systems Architect role. He is currently based out of Montréal and supports a major enterprise account in the Québec province. Danny has a college degree in computer science with a networking specialty. He has specialized in many Cisco technologies over the years, from Unified Communications to Data Center and now for the last couple of years Cisco SD-WAN. He holds multiple Cisco certifications: CCNA, CCDA, CCNP, CCDP, and CMNA. Osvaldo Salazar Tovar is currently in the role of Solutions Architect for Cisco SD-WAN technology for Latin America. He works with the partner ecosystem to deliver new approaches to simplify and optimize their WAN environments to end customers from different verticals, using the Cisco portfolio as a digital transformation platform. Osvaldo graduated from ITESM, and has several certifications such as CCNP R&S, DevNet Associate, and SD-WAN Specialist.
Osvaldo Salazar Tovar is currently in the role of Solutions Architect for Cisco SD-WAN technology for Latin America. He works with the partner ecosystem to deliver new approaches to simplify and optimize their WAN environments to end customers from different verticals, using the Cisco portfolio as a digital transformation platform. Osvaldo graduated from ITESM, and has several certifications such as CCNP R&S, DevNet Associate, and SD-WAN Specialist.
Please be sure to rate the Answers to Questions
- answer
- ask me anything
- backup
- best practices
- ccda
- ccdp
- ccna
- ccnp
- Cisco SD-WAN
- cmna
- Danny Blais
- dashboard
- deployment
- design
- event
- Global event
- Guilherme Lyra
- JNCIA
- license
- maintenance
- operation
- Osvaldo Salazar Tovar
- programmatic
- q&a
- question
- reduce costs
- SD-WAN
- SD-WAN Configuration
- SD-WAN controllers
- SD-WAN Design
- sdn
- SDWAN
- solution
- Thomas Matzeu
- troubleshooting
- vBond
- Viptela
- vmanage
- vSmart
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 04:30 AM
I would like to know the differences between (pros and cons) the virtual images for SDWAN: vEdgeCloud, CSR1000V and Cat8000v.
What are the best practices for these types of deployments, performances, and avavilability in Cloud Services Providers (AWS, AZR, GCP).
Many Thanks
Andres Castagna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 11:44 AM
Hello Andres,
The vEdge Cloud is based on Viptela OS, while the CSR1000v and Catalyst 8000v are running IOS-XE.
Actually, the Catalyst 8000v is an evolution of the CSR1000v and starting from release 17.4, only the Catalyst 8000v will be available.
How to choose between them? If your current architecture is built on vEdge devices, the vEdge Cloud is probably the best option.
In case of green field deployment, the Catalyst 8000v could offer more services.
The Catalyst 8000v is available on AWS, Azure and Google Cloud Platform.
The vEdge Cloud can be found in Azure and AWS marketplace.
Below the link to the Catalyst 8000v Configuration Guides where you can see some deployment examples:
https://www.cisco.com/c/en/us/support/routers/catalyst-8000v-edge-software/products-installation-and-configuration-guides-list.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 10:57 AM
Hi,
I understand that the Controller UI can be used immediately. What would be the next steps for a more detailed configuration?
Jackson
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 02:02 PM
Hello Jackson, how are you?
First, keep in mind what are the business goals with this solution, what are the reasons you are deploying it, what you are trying to accomplish.
Second, take your time Planning before diving into configuration. Plan ahead your System IPs, create a structured Site ID scheme, define what TLOC Colors you're going to use, design your security policy regarding VPN Segmentation and Topologies and so on. This way, you will bring up most of the details involved in the configuration and it will save you quite some time later when you're creating your Configuration Templates.
Once you're done planning, then it's time to set up the control plane. At this point you will configure basic connectivity and deploy certificates on the vManage, vBond and vSmart controllers. Once your control plane is up and running, with control connections established, you're ready to start creating your Configuration Templates and provisioning your WAN Edges.
Hope this helps and, please, hit us up if you have any further questions.
Regards.
G.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 11:35 AM
Hi Team, Thanks for the event.
I have a question, how is a security plan determined?
Att,
Note: This question is the translation of a post originally created in Portuguese by Adolfo Suarez. It was translated by the Cisco Community to share the query and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 07:41 AM
Hello Adolfo,
First, the control plane uses digital certificates with 2048-bit RSA keys to authenticate the edge routers in the network.
The Control Plane is encrypted either by DTLS or TLS. Which means that all the edge devices will establish secure connections with the orchestration components.
We keep the control plane integrity by using the combination of two security elements: AES-GCM message digests, and public and private keys.
As our control plane is now secure and trusted, we are building IPsec tunnels for data traffic (data plane).
This is a simplified answer but let me point you out to the following documentation, you will find here all the details about the security inside the SD-WAN Fabric:
https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/security/vedge-20-x/security-book/security-overview.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 12:23 AM - edited 03-09-2021 12:25 AM
Hi, Team,
Sorry to say I am not quite familiar with SD-WAN, so my questions may be very basic ones. Thanks for your expertise.
1. Can Viptela and Cisco's ISR and ASR series coexist in an SD-WAN network?
2. Viptela equipment seems outdated nowadays. What are the advantages of upgrading ISR, ASR and other equipment to SD-WAN mirroring, compared to Viptela?
3. vManage, vBond, vSmart, vEdge, what are their main roles in the SD-WAN network, and how many of them can exist in the SD-WAN network at least & at most?
4. vEdge has both cloud and hardware products, while vManage / vBond / vSmart only have cloud products, am I right? Do they need to be installed in a virtual environment?
5. Could vEdge go online without manual intervention? It can be zero contact? What is the detailed process of launching vEdge ?
6. What is the strategic framework of SD-WAN?
7. What troubleshooting tools are commonly used in SD-WAN networks? Which ones are more commonly used.
8. What kind of backup does SD-WAN backup refer to, and how should we operate the backup involved in the topic?
Note: This question is the translation of a post originally created in Chinese by 1540488497lcj It was translated by the Cisco Community to share the query and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 05:28 PM
Hello, thank you so much for participating in the forum, all questions are welcome.
- Can Viptela and Cisco's ISR and ASR series coexist in an SD-WAN network? Absolutely, XE and Viptela OS can completely interoperate in one single SD-WAN Fabric.
- Viptela equipment seems outdated nowadays. What are the advantages of upgrading ISR, ASR and other equipment to SD-WAN mirroring, compared to Viptela? From 17.x versions in XE we have a universal image that allows you run in Autonomous mode (traditional XE) or Controller mode (SDWAN), only thing required is a single command. XE offers a more rich set of functionalities compared to Viptela OS, while having embedded SD-WAN capabilities that Viptela OS brought to Cisco SD-WAN. Just to mention some features XE can offer and Viptela OS cannot, is URL-F and IPS, which are functions hosted on containers inside XE architecture. Remember Cisco has launched new routers, Catalyst 8000 Edges which can help as well. Check more details on https://www.cisco.com/c/es_mx/solutions/enterprise-networks/sd-wan/index.html#~case-studies
- vManage, vBond, vSmart, vEdge, what are their main roles in the SD-WAN network, and how many of them can exist in the SD-WAN network at least & at most?
vManage is the single pane of glass from where you can operate, configure, troubleshoot, monitor your SD-WAN network. vBond acts as an orchestrator and leverages trustworthy systems from Cisco as well as acts as STUN server to deal with private/public addressing for fabric elements. vSmart is the brain of the operation and deals with encryption keys and all intelligence -meaning routing information- propagation to data plane -routers-. Last but not less important, WAN Edges execute what controllers dictate, while maintaining their intelligence and horse powers to develop tasks like QoS, ACLs, etc.
Numbers can vary for Edges on an overlay, it depends on customer, but that number will directly matter in terms of how many vManage, vBond and vSmart instances we will have in the overlay. Common deployments have 1 vManage, 2 vBonds and 2 vSmarts. But you can have up to 6 vBonds, 20 vSmarts and 6 vManages. In order to design according to best practices make sure you check https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/sdwan-xe-gs-book/hardware-and-software-installation.html , Cisco Team is always happy to help you design with best practices according to your customer requirements.
4. vEdge has both cloud and hardware products, while vManage / vBond / vSmart only have cloud products, am I right? Do they need to be installed in a virtual environment? Correct, vEdge has physical appliances and VNF or virtual instance (vEdge cloud). Same happens with cEdge (XE OS), there are CSR1000V and C8KV available in public cloud providers marketplaces when IaaS is required. In case on premise deployment is required they can be instantiated according to the following links:
To see more specific information please one of the previous questions where this has been addressed.
5. Could vEdge go online without manual intervention? It can be zero contact? What is the detailed process of launching vEdge ? Absolutely, Cisco SD-WAN offers true Zero Touch Provisioning (ZTP), you can get details here:
Basically, PnP Service from Cisco maps devices you have licensed for your organization, once you connect your device and it gets an IP via DHCP as well as DNS, there is call home (to retrieve validation from PnP) and authentication from vBond, to be on boarded to SD-WAN fabric, configuration template is lately downloaded, this is one pre requisite, have one configuration template assigned to your device Serial number.
[..]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2021 10:18 AM
- Could vEdge go online without manual intervention? It can be zero contact? What is the detailed process of launching vEdge ? Absolutely, Cisco SD-WAN offers true Zero Touch Provisioning (ZTP), you can get details here:
6. What is the strategic framework of SD-WAN? Cisco SD-WAN offers you the most granular and customizable routing framework achieved with its different policies, this is the more strategic part of the solution, you can see detailed information here: https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/policies/ios-xe-17/policies-book-xe/policy-framework.html
7. What troubleshooting tools are commonly used in SD-WAN networks? Under Network > Troubleshooting for each device you can check Device Bringup stage, Control Connections, use Ping or TraceRoute with specific, these two are commonly used by all network engineers. While you need to see how an application is behaving you can use App Route visualization or simulate flows. Packet Capture is also a good tool to know the truth.
8. What kind of backup does SD-WAN backup refer to, and how should we operate the backup involved in the topic? In terms of how to back up and/or restore your device templates, feature templates, policies or lists, you can use programmatic ways as this is native part from Cisco SD-WAN, recommended to see https://github.com/CiscoDevNet/sastre and take a look at https://developer.cisco.com .
Hope these answers help, regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 12:26 AM - edited 03-09-2021 12:27 AM
What requirements must a server meet to implement SD-WAN?
Note: This question is the translation of a post originally created in Chinese by zero.xia. It was translated by the Cisco Community to share the query and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 09:26 AM - edited 03-09-2021 11:33 AM
Hi Yanli,
Cisco SD-WAN includes all the management components (vManage, vBond and vSmart) in the cloud and supports the following platforms at the edge:
- Cisco ASR 1000 Series Aggregation Services Routers
- Cisco 1000 Series ISRs
- Cisco 4000 Series ISRs
- Catalyst 8000
- Cisco 5400 ENCS with the ISRv
- Cisco UCS with the ISRv
- CSR 1000v
Having said that, if you are using the cloud deployment model and you are using Catalyst 8000, ASRs or ISRs as an edge device, there are no specific server requirements since no servers are used.
In the event where you would like to have all the management components on-premise. The ESX/KVM servers recommendations for the Cisco vBond Orchestrator server, Cisco vManage server, and Cisco vSmart Controller server are available at the following link: https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/sdwan-xe-gs-book/hardware-and-software-installation.html
The resources required to run each components Cisco vBond Orchestrator, Cisco vSmart Controller, and Cisco vManage server on the VMware vSphere ESXi or the Kernel-based Virtual Machine (KVM) server will vary depending on the number of devices you deploy in the overlay network. Also pay attention that all the OS volume must be on a solid-state drive (SSD).
If your edge device is not a Catalyst 8000, ASRs or ISRs routers but rather an ISRv running on Cisco UCS servers and/or Cisco ENCS platforms:
The server must support at least the following:
- Intel ® Atom ® or Xeon ® CPU at 1.5 GHz or above
- AMD ® Embedded R-Series
- Gigabit Ethernet interfaces
The ISRv requires the following from the virtualized server hardware:
- CPU: 1 to 4 virtual CPUs (depending on the throughput and feature set)
- Memory: 4 GB to 16 GB (depending on the throughput and feature set)
- Disk space: 8 GB
- Network interfaces: Two or more vNICs, up to maximum allowed by hypervisor (26)
In regards to the CSR 1000v, the requirements are available here for:
Regards,
Danny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 12:44 AM - edited 03-09-2021 12:45 AM
Could you share an example of DIA deployment?
Note: This question is the translation of a post originally created in Chinese by 陈少卿. It was translated by the Cisco Community to share the query and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 11:28 AM - edited 03-09-2021 11:32 AM
Hi Yanil,
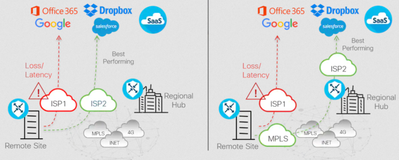
DIA improves the user experience by allowing branch users to access Internet resources and SaaS applications directly from the branch. Traditionally, branches have accessed SaaS applications through centralized data centers which results in increased application latency and unpredictable user experience. As SD-WAN has evolved, additional network paths to access SaaS applications are possible, including Direct Internet Access (DIA) and access through regional gateways or colocation sites. However, network administrators may have limited or no visibility into the performance of the SaaS applications from remote sites, so, choosing what network path to access the SaaS applications in order to optimize the end-user experience can be problematic. In addition, when changes to the network or impairment occurs, there may not be an easy way to move affected applications to an alternate path.
With Cisco SD-WAN this function is called Cloud onRamp. It allows you to easily configure access to SaaS applications, either direct from the Internet or through gateway locations. It continuously probes, measures, and monitors the performance of each path to each SaaS application and it chooses the best-performing path based on loss and delay. If impairment occurs, SaaS traffic is dynamically and intelligently moved to the updated optimal path.
Example of application that can leverage this functionality are:
- Office 365
- Salesforce
- Google App
- Box
- Dropbox
- Concur
- Intuit
- AWS
- GoToMeeting
- Oracle
- SugarCRM
- Zendesk
- Zoho CRM
Cloud onRamp for SaaS – best performing path is chosen
A second example is DIA for IaaS. IaaS delivers network, compute, and storage resources to end users on-demand, available in a public cloud (such as AWS, Azure or Google Cloud) over the Internet. Traditionally, for a branch to reach IaaS resources, there was no direct access to public cloud data centers, as they typically require access through a data center or colocation site. In addition, there was a dependency on MPLS to reach IaaS resources at private cloud data centers with no consistent segmentation or QoS policies from the branch to the public cloud.
Cisco Cloud onRamp for IaaS is a feature that automates connectivity to workloads in the public cloud from the data center or branch. It automatically deploys WAN Edge router instances in the public cloud that become part of the SD-WAN overlay and establish data plane connectivity to the routers located in the data center or branch. It extends full SD-WAN capabilities into the cloud and extends a common policy framework across the SD-WAN fabric and cloud. Cisco Cloud onRamp for IaaS eliminates traffic from SD-WAN sites needing to traverse the data center, improving the performance of the applications hosted in the public cloud. It also provides high availability and path redundancy to applications hosted in the cloud, which is also very cost effective.
Regards,
Danny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2021 09:49 PM - edited 03-09-2021 10:12 PM
Regarding the certification for SD-WAN, what new materials have been published or are there tutorials that can support us for the exam?
Note: This question is the translation of a post originally created in Japanese by SaTo663696. It was translated by the Cisco Community to share the query and its solution in different languages.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide