- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- sd-wan- hub and spoke topology
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2023 08:38 AM
Hello,
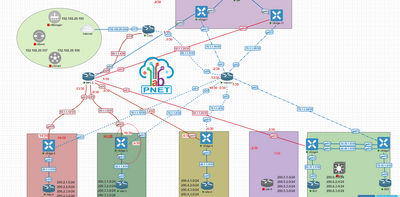
I don't have spoke to spoke communication between the two vedge devices. As per the topology, Vedge3 is HUB and the rest is spoke.
vEdge2# show ip routes omp
Codes Proto-sub-type:
IA -> ospf-intra-area, IE -> ospf-inter-area,
E1 -> ospf-external1, E2 -> ospf-external2,
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2,
e -> bgp-external, i -> bgp-internal
Codes Status flags:
F -> fib, S -> selected, I -> inactive,
B -> blackhole, R -> recursive, L -> import
PROTOCOL NEXTHOP NEXTHOP NEXTHOP
VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS
---------------------------------------------------------------------------------------------------------------------------------------------
100 30.1.1.0/30 omp - - - - 100.100.100.30 mpls ipsec F,S
100 30.1.1.0/30 omp - - - - 100.100.100.30 biz-internet ipsec F,S
100 200.0.0.0/8 omp - - - - 100.100.100.30 mpls ipsec F,S
100 200.0.0.0/8 omp - - - - 100.100.100.30 biz-internet ipsec F,S
100 200.3.1.0/24 omp - - - - 100.100.100.30 mpls ipsec F,S
100 200.3.1.0/24 omp - - - - 100.100.100.30 biz-internet ipsec F,S
100 200.3.2.0/24 omp - - - - 100.100.100.30 mpls ipsec F,S
100 200.3.2.0/24 omp - - - - 100.100.100.30 biz-internet ipsec F,S
100 200.3.3.0/24 omp - - - - 100.100.100.30 mpls ipsec F,S
100 200.3.3.0/24 omp - - - - 100.100.100.30 biz-internet ipsec F,S
100 200.3.4.0/24 omp - - - - 100.100.100.30 mpls ipsec F,S
100 200.3.4.0/24 omp - - - - 100.100.100.30 biz-internet ipsec F,S
vEdge3# show run
system
host-name vEdge3
system-ip 100.100.100.30
site-id 30
admin-tech-on-failure
no route-consistency-check
no vrrp-advt-with-phymac
sp-organization-name "viptela sdwan"
organization-name "viptela sdwan"
clock timezone Asia/Kolkata
vbond 192.168.29.107
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
user admin
password $6$siwKBQ==$wT2lUa9BSreDPI6gB8sl4E6PAJoVXgMbgv/whJ8F1C6sWdRazdxorYYTLrL6syiG6qnLABTnrE96HJiKF6QRq1
!
ciscotacro-user true
ciscotacrw-user true
!
logging
disk
enable
!
!
ntp
parent
no enable
stratum 5
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type sha1-hmac ah-sha1-hmac
!
!
banner
login "Only for authorized users"
motd "Welcome to SD-WAN"
!
vpn 0
name Transport-VPN0
interface ge0/0
description "CONNECT TO MPLS"
ip address 60.1.1.10/30
tunnel-interface
encapsulation ipsec
color mpls
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
no allow-service stun
allow-service https
!
no shutdown
!
interface ge0/1
description "CONNECTED TO INTERNET"
ip address 70.1.1.10/30
tunnel-interface
encapsulation ipsec
color biz-internet
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
no allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 60.1.1.9
ip route 0.0.0.0/0 70.1.1.9
!
vpn 100
name service-vpn
router
ospf
timers spf 200 1000 10000
redistribute omp
area 0
interface ge0/2
exit
exit
!
!
interface ge0/2
description vpn100-internal-LAN
ip address 30.1.1.1/30
no shutdown
!
omp
advertise aggregate 200.0.0.0/8
!
!
vpn 512
name Mgnt-VPN512
interface eth0
description Magnt-VPN512-Interface
ip dhcp-client
no shutdown
Codes Proto-sub-type: omp - - - IA -> ospf-intra-area, IE -> ospf-inter-area,psec F,S
E1 -> ospf-external1, E2 -> ospf-external2, - - - 100.100.100.60 mpls ipsec F,S
N1 -> ospf-nssa-external1, N2 -> ospf-nssa-external2, - - 100.100.100.60 mpls ipsec F,S
e -> bgp-external, i -> bgp-internal Codes Status flags: F -> fib, S -> selected, I -> inactive, B -> blackhole, R -> recursive, L -> import PROTOCOL NEXTHOP NEXTHOP NEXTHOP VPN PREFIX PROTOCOL SUB TYPE IF NAME ADDR VPN TLOC IP COLOR ENCAP STATUS --------------------------------------------------------------------------------------------------------------------------------------------- 100 10.1.1.0/24 omp - - - - 100.100.100.10 mpls ipsec F,S 100 10.1.1.0/24 omp - - - - 100.100.100.10 biz-internet ipsec F,S 100 10.1.1.0/24 omp - - - - 100.100.100.11 mpls ipsec F,S
100 10.1.1.0/24 omp - - - - 100.100.100.11 biz-internet ipsec F,S
100 20.1.1.0/30 omp - - - - 100.100.100.20 mpls ipsec F,S
100 20.1.1.0/30 omp - - - - 100.100.100.20 biz-internet ipsec F,S
100 40.1.1.0/24 omp - - - - 100.100.100.40 mpls ipsec F,S
100 60.10.1.0/30 omp - - - - 100.100.100.60 mpls ipsec F,S
100 70.10.1.0/30 omp - - - - 100.100.100.70 biz-internet ipsec F,S
100 200.1.1.0/24 omp - - - - 100.100.100.10 mpls ipsec F,S
100 200.1.1.0/24 omp - - - - 100.100.100.10 biz-internet ipsec F,S
100 200.1.1.0/24 omp - - - - 100.100.100.11 mpls ipsec F,S
100 200.1.1.0/24 omp - - - - 100.100.100.11 biz-internet ipsec F,S
100 200.1.2.0/24 omp - - - - 100.100.100.10 mpls ipsec F,S
100 200.1.2.0/24 omp - - - - 100.100.100.10 biz-internet ipsec F,S
100 200.1.2.0/24 omp - - - - 100.100.100.11 mpls ipsec F,S
100 200.1.2.0/24 omp - - - - 100.100.100.11 biz-internet ipsec F,S
100 200.1.3.0/24 omp - - - - 100.100.100.10 mpls ipsec F,S
100 200.1.3.0/24 omp - - - - 100.100.100.10 biz-internet ipsec F,S
100 200.1.3.0/24 omp - - - - 100.100.100.11 mpls ipsec F,S
100 200.1.3.0/24 omp - - - - 100.100.100.11 biz-internet ipsec F,S
100 200.1.4.0/24 omp - - - - 100.100.100.10 mpls ipsec F,S
100 200.1.4.0/24 omp - - - - 100.100.100.10 biz-internet ipsec F,S
100 200.1.4.0/24 omp - - - - 100.100.100.11 mpls ipsec F,S
100 200.1.4.0/24 omp - - - - 100.100.100.11 biz-internet ipsec F,S
100 200.2.1.0/24 omp - - - - 100.100.100.20 mpls ipsec F,S
100 200.2.1.0/24 omp - - - - 100.100.100.20 biz-internet ipsec F,S
100 200.2.2.0/24 omp - - - - 100.100.100.20 mpls ipsec F,S
100 200.2.2.0/24 omp - - - - 100.100.100.20 biz-internet ipsec F,S
100 200.2.3.0/24 omp - - - - 100.100.100.20 mpls ipsec F,S
100 200.2.3.0/24 omp - - - - 100.100.100.20 biz-internet ipsec F,S
100 200.2.4.0/24 omp - - - - 100.100.100.20 mpls ipsec F,S
100 200.2.4.0/24 omp - - - - 100.100.100.20 biz-internet ipsec F,S
100 200.6.1.1/32 omp - - - - 100.100.100.60 mpls ipsec F,S
100 200.6.2.1/32 omp - - - - 100.100.100.60 mpls ipsec F,S
100 200.6.3.1/32 omp - - - - 100.100.100.60 mpls ipsec F,S
100 200.6.4.1/32 omp - - - - 100.100.100.60 mpls ipsec F,S
100 200.7.1.1/32 omp - - - - 100.100.100.70 biz-internet ipsec F,S
100 200.7.2.1/32 omp - - - - 100.100.100.70 biz-internet ipsec F,S
100 200.7.3.1/32 omp - - - - 100.100.100.70 biz-internet ipsec F,S
100 200.7.4.1/32 omp - - - - 100.100.100.70 biz-internet ipsec F,S
vSmart1# show running-config policy
policy
lists
vpn-list VPN-100
vpn 100
!
site-list HUB
site-id 30
!
site-list SPOKE
site-id 10
site-id 11
site-id 20
site-id 40
site-id 60
site-id 70
!
!
control-policy control_792992085
sequence 10
match route
site-list HUB
vpn-list VPN-100
!
action accept
!
!
sequence 20
match tloc
site-list HUB
!
action accept
!
!
default-action reject
!
!
vSmart1#
Solved! Go to Solution.
- Labels:
-
SD-WAN Infrastructure
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 06:31 AM
The default is full-mesh and requires a control policy to change the topology. First thing is to reject TLOCS between all the spokes which is sequence 1 below. Sequence 11 says that all routes from a spoke need to be sent to the hub. Default action is to accept so if there are multiple hubs or other "non spoke" sites they will build a full mesh. The policy is applied only to the spoke routers in the outbound direction. Outbound is using vSmart as the reference point.
The control policy sequences and where the control policy applied are equally important.
control-policy spoke-hub-spoke
sequence 1
match tloc
site-list spokes
!
action reject
!
!
sequence 11
match route
prefix-list _AnyIpv4PrefixList
site-list spokes
!
action accept
set
tloc-list hubsEast
!
!
!
default-action accept
apply-policy
!
site-list spokes
control-policy spoke-hub-spoke out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 06:31 AM
The default is full-mesh and requires a control policy to change the topology. First thing is to reject TLOCS between all the spokes which is sequence 1 below. Sequence 11 says that all routes from a spoke need to be sent to the hub. Default action is to accept so if there are multiple hubs or other "non spoke" sites they will build a full mesh. The policy is applied only to the spoke routers in the outbound direction. Outbound is using vSmart as the reference point.
The control policy sequences and where the control policy applied are equally important.
control-policy spoke-hub-spoke
sequence 1
match tloc
site-list spokes
!
action reject
!
!
sequence 11
match route
prefix-list _AnyIpv4PrefixList
site-list spokes
!
action accept
set
tloc-list hubsEast
!
!
!
default-action accept
apply-policy
!
site-list spokes
control-policy spoke-hub-spoke out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 09:02 AM
Okay, I have done another way to HUB and spoke topology as mentioned below policy and It's working fine.
viptela-policy:policy
control-policy control_-1798040302
sequence 10
match route
site-list HUB
vpn-list VPN-100
!
action accept
!
!
sequence 20
match route
site-list SPOKE
vpn-list VPN-100
!
action accept
set
tloc-list hub-tloc
!
!
!
sequence 30
match tloc
site-list HUB
!
action accept
!
!
default-action reject
!
lists
site-list HUB
site-id 30
!
site-list SPOKE
site-id 20
site-id 40
site-id 60
site-id 70
site-id 10
site-id 11
!
tloc-list hub-tloc
tloc 100.100.100.30 color biz-internet encap ipsec
tloc 100.100.100.30 color mpls encap ipsec
!
vpn-list VPN-100
vpn 100
!
!
!
apply-policy
site-list SPOKE
control-policy control_-1798040302 out
!
!- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 09:39 AM
Provides flexibility and easy to come up with config., instead of coming up with CLI config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 09:41 AM
Screenshot from 20.12.1
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide