- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- Service Chaining Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 09:30 AM - edited 02-09-2023 09:33 AM
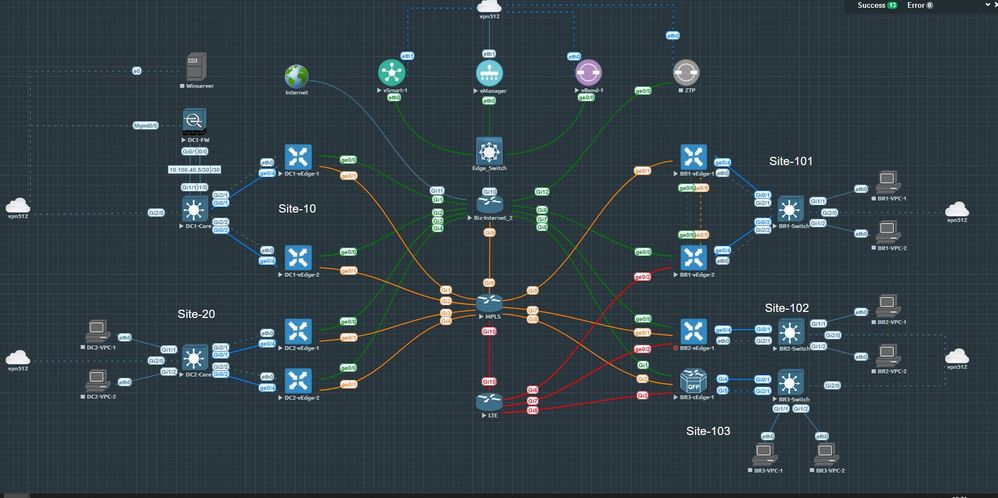
I have setup service chaining from site 20 vpn 10 to site 101 vpn 20 using vpn 40 at site 10 and vice versa (tested working), but what if there are resources at site 10 that also need to access vpn 20 from vpn 10 via the local firewall. How would I accomplish the required configuration?
viptela-policy:policy
control-policy vpn20-inter-vpn10-40
sequence 1
match route
vpn-list VPN_20
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list Corp_FW
!
!
default-action accept
!
control-policy site20-fw-site101
sequence 1
match route
site-list Site_101
prefix-list _AnyIpv4PrefixList
!
action accept
set
service netsvc1 vpn 40
!
!
!
default-action accept
!
control-policy vpn10-inter-vpn20-40
sequence 1
match route
vpn-list VPN_10
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list PoS_FW
!
!
sequence 11
match route
vpn-list VPN_40_FW
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list VPN_10
!
!
default-action accept
!
control-policy site101-fw-site20
sequence 1
match route
site-list Site_20
prefix-list _AnyIpv4PrefixList
!
action accept
set
service netsvc2 vpn 40
!
!
!
default-action accept
!
lists
site-list Site_10
site-id 10
!
site-list Site_101
site-id 101
!
site-list Site_20
site-id 20
!
vpn-list Corp_FW
vpn 10
vpn 40
!
vpn-list PoS_FW
vpn 20
vpn 40
!
vpn-list VPN_10
vpn 10
!
vpn-list VPN_20
vpn 20
!
vpn-list VPN_40_FW
vpn 40
!
prefix-list _AnyIpv4PrefixList
ip-prefix 0.0.0.0/0 le 32
!
!
!
apply-policy
site-list Site_10
control-policy vpn10-inter-vpn20-40 in
!
site-list Site_101
control-policy site101-fw-site20 out
control-policy vpn20-inter-vpn10-40 in
!
site-list Site_20
control-policy site20-fw-site101 out
control-policy vpn10-inter-vpn20-40 in
!
!
Solved! Go to Solution.
- Labels:
-
SD-WAN Infrastructure
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 09:06 AM
I managed to figure it out, I was using a dual edge site design and had add an extra interface for the 2nd edge and apply the acl to that interface as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 11:11 AM
DC2-Core#traceroute vrf 10 10.20.101.1
Type escape sequence to abort.
Tracing the route to 10.20.101.1
VRF info: (vrf in name/id, vrf out name/id)
1 10.10.20.2 21 msec
10.10.20.3 12 msec
10.10.20.2 18 msec
2 10.100.40.2 50 msec 50 msec 59 msec
3 10.100.40.1 65 msec 88 msec 81 msec
4 10.100.40.6 76 msec 79 msec 98 msec
5 10.20.101.2 93 msec 126 msec 136 msec
6 10.20.101.1 135 msec * 168 msec
DC2-Core#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 11:11 AM
BR1-Switch#traceroute vrf 20 10.10.20.1
Type escape sequence to abort.
Tracing the route to 10.10.20.1
VRF info: (vrf in name/id, vrf out name/id)
1 10.20.101.2 12 msec
10.20.101.3 11 msec
10.20.101.2 27 msec
2 10.100.40.6 81 msec 70 msec 68 msec
3 10.100.40.5 75 msec 121 msec 110 msec
4 10.100.40.2 95 msec 117 msec 117 msec
5 10.10.20.3 103 msec 135 msec 116 msec
6 10.10.20.1 141 msec * 170 msec
BR1-Switch#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 11:30 PM
You should used policy based routing with localized policies on site 10 routers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 12:52 AM
Thanks for pointing me in the right direction, so in a nutshell I should setup a localized routing policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2023 01:54 AM
This is not working, I can't find any documentation on this. Anyone?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 01:11 AM
Yes, in localized policy you can match a prefix and modify the next hop for local firewall. Also, you will need use route leaking in VPN template depending on the traffic bidirectional flows
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 05:15 AM
I have created a Local Routing Policy and attaced it to Site 10 but traffic swill go directly through to VPN 20
viptela-policy:policy
data-policy _VPN_10_site_10_vpn_10_to_vpn_20
vpn-list VPN_10
sequence 1
match
destination-ip 10.20.101.0/24
!
action accept
set
next-hop 10.100.40.1
!
!
!
default-action accept
!
control-policy vpn20-inter-vpn10-40
sequence 1
match route
vpn-list VPN_20
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list Corp_FW
!
!
default-action accept
!
control-policy site20-fw-site101
sequence 1
match route
site-list Site_101
prefix-list _AnyIpv4PrefixList
!
action accept
set
service netsvc1 vpn 40
!
!
!
default-action accept
!
control-policy vpn10-inter-vpn20-40
sequence 1
match route
vpn-list VPN_10
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list PoS_FW
!
!
sequence 11
match route
vpn-list VPN_40_FW
prefix-list _AnyIpv4PrefixList
!
action accept
export-to vpn-list vpn_10_20
!
!
default-action accept
!
control-policy site101-fw-site20
sequence 1
match route
site-list Site_20
prefix-list _AnyIpv4PrefixList
!
action accept
set
service netsvc2 vpn 40
!
!
!
default-action accept
!
lists
site-list Site_10
site-id 10
!
site-list Site_101
site-id 101
!
site-list Site_20
site-id 20
!
vpn-list Corp_FW
vpn 10
vpn 40
!
vpn-list PoS_FW
vpn 20
vpn 40
!
vpn-list VPN_10
vpn 10
!
vpn-list VPN_20
vpn 20
!
vpn-list VPN_40_FW
vpn 40
!
vpn-list vpn_10_20
vpn 10
vpn 20
!
prefix-list _AnyIpv4PrefixList
ip-prefix 0.0.0.0/0 le 32
!
!
!
apply-policy
site-list Site_10
data-policy _VPN_10_site_10_vpn_10_to_vpn_20 from-tunnel
control-policy vpn10-inter-vpn20-40 in
!
site-list Site_101
control-policy site101-fw-site20 out
control-policy vpn20-inter-vpn10-40 in
!
site-list Site_20
control-policy site20-fw-site101 out
control-policy vpn10-inter-vpn20-40 in
!
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 05:17 AM
DC1-Core#traceroute vrf 10 10.20.101.1
Type escape sequence to abort.
Tracing the route to 10.20.101.1
VRF info: (vrf in name/id, vrf out name/id)
1 10.10.10.2 15 msec
10.10.10.3 33 msec
10.10.10.2 21 msec
2 10.20.101.2 48 msec 61 msec 47 msec
3 10.20.101.1 98 msec * 99 msec
DC1-Core#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 09:06 AM
I managed to figure it out, I was using a dual edge site design and had add an extra interface for the 2nd edge and apply the acl to that interface as well.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

