- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Downloadable URL-Redirect ACL with ISE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-27-2020
02:33 PM
- edited on
04-06-2023
01:54 PM
by
thomas
![]()
Contents
- Downloadable URL-Redirect ACL
- Create URL-Redirect ACL
- External ACL Name: URL-Redirect ACL as dACL to reveal the name
- External ACL name: Configuration Change Alarm
- Create CWA authorization profile
- Result
For additional advanced ISE related Tips, please visit Advanced ISE tips to make your deployment easier document
Downloadable URL-Redirect ACL
If you have ever configured CWA (Central Web Authentication) with ISE you understand that it requires one to configure ACL that dictates what traffic is to be redirected vs. let through without redirection. You also understand that this ACL needs to be configured locally on the switch or the wireless controller and referenced by name from ISE, thus the ACL content cannot be downloaded from ISE like dACL (downloadable ACL). URL-Redirect ACL is not limited to CWA only, and it is used throughout ISE advanced flows such as BYOD, posture, and MDM/EMM flows. Being able to download the URL-Redirect ACL provides great value as it allows administrators to centralize the ACL, and eliminates the need to touch every network device in the event that the ACL needs to be updated. The feature was introduced on IOS-XE, however currently missing on ISE to leverage it.
Here, I am going to provide experimental configuration that you can try for downloadable URL-Redirect ACL from ISE just like dACL. It requires few steps to grab the version number of the ACL but fairly simple once the external name of the ACL is found. This has been tested with:
- Catalyst 9800 v17.1.1s, but should also work with previous versions
- Catalyst 9300 v16.12.1, but should also work with v16.9.1 and above on other Catalyst 9k switch models
Create URL-Redirect ACL
1. Login to ISE
2. Go to Policy > Policy Elements > Results > Authorization > Downloadable ACLs
3. Click Add
4. Provide a name. I am using “Redirect-Test” in my example
5. Enter following in the DACL Content box and click Submit
permit tcp any any eq 80
Note: implicit deny will ensure other traffic is not redirected. You can also add line for ISE for exemption or permit statement for HTTPS if necessary
External ACL Name: URL-Redirect ACL as dACL to reveal the name
Method 1 using URL-Redirect ACL as dACL to reveal the name.
1. Go to Policy > Policy Elements > Results > Authorization > Authorization Profile
2. Click Add
3. Provide a name and create a simple authorization profile with the URL-Redirect ACL as dACL
4. Go to Policy > Policy Set
5. Assign it to any policy and get it matched to a real authentication with a test endpoint
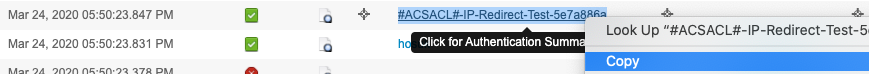
6. Go to LiveLog and grab the ACL name shown in the details of the log or just above the real user authentication event. In our example it is #ACSACL#-IP-Redirect-Test-5e7a886a
7. Once ACL name has been captured, you can delete this temporary authorization profile
External ACL name: Configuration Change Alarm
Method 2 using configuration change alarm.
1. Go to main ISE dashboard
2. Within ALARMS dashlet, click on “Configuration Changed” Alarm
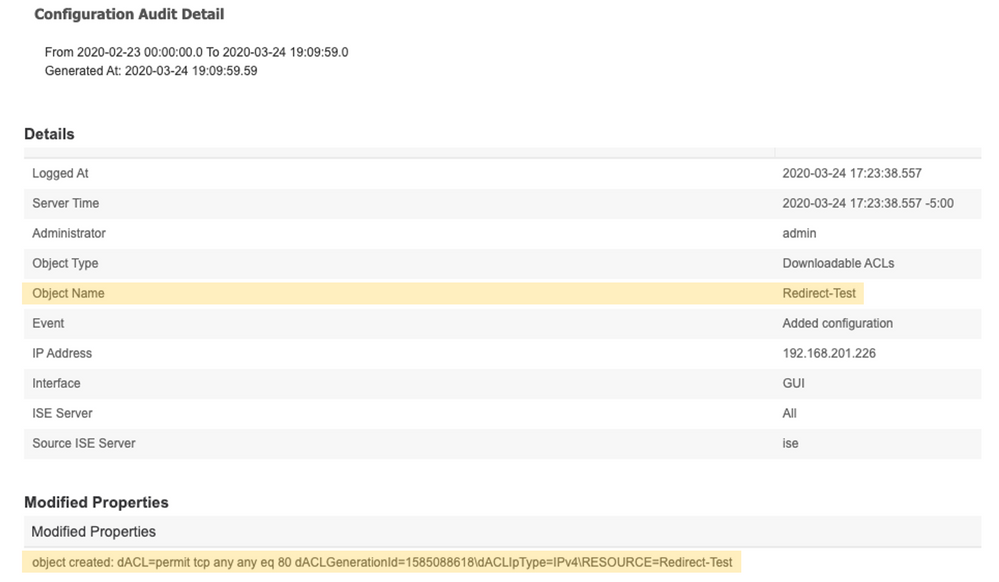
3. Find the line for creation of Downloadable ACL that reads something like “Configuration Added: Admin=admin; Object 4. Type=Downloadable ACLs; Object Name=Redirect-Test” and click Details. If it was modified it will read "Configuration Changed: Admin=admin; Object Type=Downloadable ACLs; Object Name=Redirect-Test". Make sure to pick the latest event
4. On the bottom there is a line that starts with “object created: …”
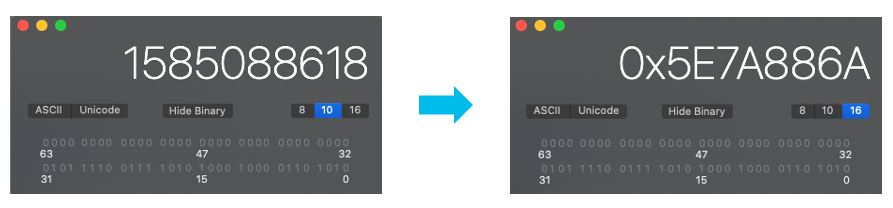
5. Copy the number that comes after “GenerationId=“ part. In my example it is 1585088618. This is the epoch when the ACL was created which is also used as version number.
6. Convert this number into hexadecimal format using any calculator to get the actual version number in use which is 5e7a886a
7. Now we are going to get the external ACL name which is concatenation of #ACSACL#-IP-, ACL Name, -, version number. In our example it will be
#ACSACL#-IP-Redirect-Test-5e7a886a
Note: The version number is case sensitive and should be in lower case
Create CWA authorization profile
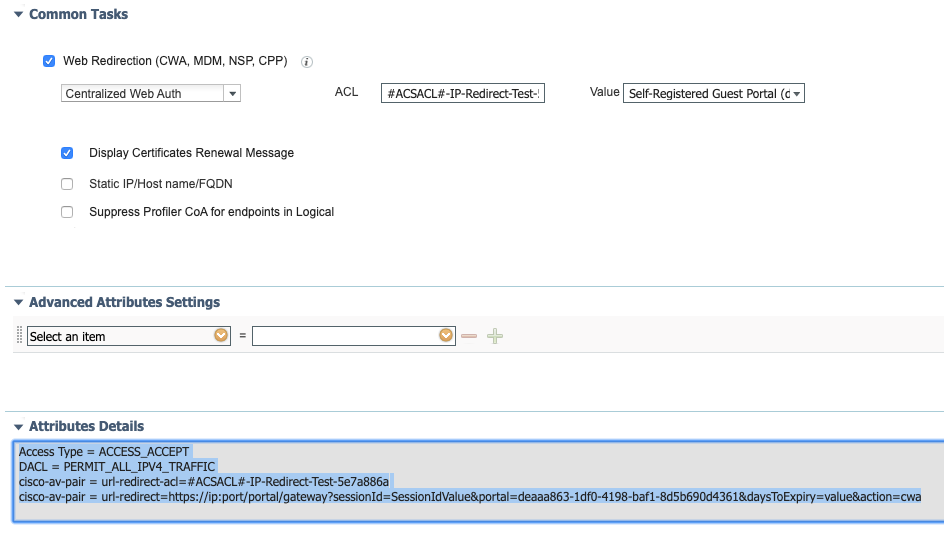
Create or modify existing CWA authorization profile and replace the redirect ACL with the name that we generated.
Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_IPV4_TRAFFIC
cisco-av-pair = url-redirect-acl=#ACSACL#-IP-Redirect-Test-5e7a886a
cisco-av-pair = url-redirect=https://ip:port/portal/gateway?sessionId=SessionIdValue&portal=deaaa863-1df0-4198-baf1-8d5b690d4361&daysToExpiry=value&action=cwa
Note: I am also using regular dACL "PERMIT_ALL_IPV4_TRAFFIC" along with downloadable URL-Redirect ACL in the example above
IMPORTANT: Every time you modify the redirect ACL on ISE, make sure to go through one of the 2 methods to find the updated ACL version number and apply new version number in the authorization profile.
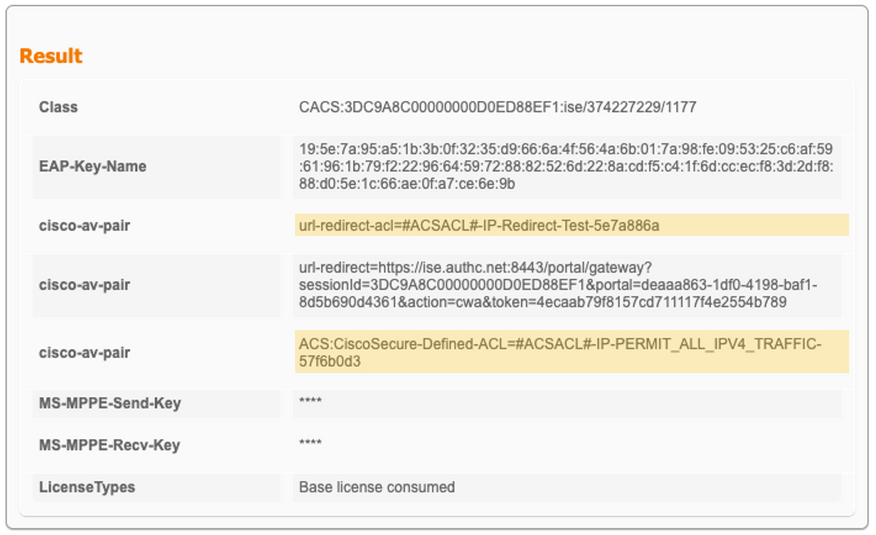
Result
Assuming both dACL and downloadable URL-Redirect ACL is applied, you will see authentication success followed by two ACL entries:
Also, the result section of the live log details will show the corresponding downloadable URL-Redirect ACL and dACL
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Interesting, never looked at this, as it seems the "version" part of the ACL was not really consistent. So it changes each time you modify the ACL and only at that point? Does it survive a reload of ISE (hard) or of its services?
Regards,
Cristian Matei.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, the ACL version will survive the reload.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is amazing!
But I'm still confused about the content of the dACL for the redirect to happen.
Can you please share an example dACL that will work with redirection:
Scenario:
Allow destination A
Redirect destination B
Many thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
rajo, in case of IOS, in the redirect ACL the permit statements are for traffic that is to be redirected while deny is not redirected. If you want to redirect port 80 to B and not redirect traffic to port 80 A then use something like this:
deny tcp any host A eq 80
permit tcp any host B eq 80
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hello everyone, during this redirect process. should switch have reachability to ise server over port 80.
as we are facing problem while downloading compliance module since the switch radius source ip is different than ise ip.
but when we get switch and ise on same vlan the module gets downloaded.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the guide! "sh access-session..." output seems to indicate it works. Now I just need to test it the next time I am onsite. I do have a few notes.
1) It seems, at least in ISE 3.1, that the configuration audit log no longer provides the generation ID.
2) However, it also seems the generation ID is just the epoch time in seconds of the "Server Time" or "Logged Time" in the Audit Details table, so I was able to figure out the generation ID with a time format converter and the calculator method you provided.
Thank you, again!
_Nathan
Update:
On the Linux box I have available to me, the following command outputs the properly formatted version number, which I then append to the properly formatted ACL name preceded by a hyphen.
printf "%x\n" `date --date='<Server Time field value>' +%s`i.e.
#$> printf "%x\n" `date --date='2023-05-19 16:21:23.462 -6:00' +%s`
6467f663
#$>
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: