- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE and Catalyst 9800 Series Integration Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-27-2018 01:13 PM - edited 04-07-2021 11:24 PM
Content
- Introduction
- Setup
- Components used:
- Notes:
- Catalyst 9800 Configuration
- Steps 1 - 3: Define AAA
- Step 4: Create Webauth Parameter Map (Required for BYOD)
- Step 5: Create VLANs
- Step 6: Create WLANs
- Step 7: Create Policy Profiles
- Step 8: Create Policy Tag
- Step 9: Assign Policy Tag to AP
- Step 10a: Create Redirect ACL for Guest flow
- Step 10b: Create Redirect ACL for BYOD flow
- Step 11a: Create URL Filter for BYOD flow
- Step 11b: Create URL Filter for Social Network Guest access - Facebook
- ISE Configuration
- Authorization Profile with URL Filter
- Catalyst 9800 Configuration for FlexConnect Local switching
- Modify Policy Profile
- Create Flex Profile
- Create Site Tag
- Assign Site Tag to AP
- Modify Redirect ACL
- Troubleshooting
You may then Print or Print to PDF or copy and paste to Word or any other document format you like.
Introduction
Cisco Catalyst 9800 (C9800) series wireless controller configuration is different from AireOS and this document shows how to configure C9800 to work with ISE. For more information on Cisco Catalyst 9800 series, please go to: https://www.cisco.com/c/en/us/products/wireless/catalyst-9800-series-wireless-controllers/index.html
Setup
Components used:
WLC: Catalyst 9800-CL running 16.10.1
AP: Cisco 1815i
ISE: 2.4p3 (Previous versions of ISE should work with C9800 as well)
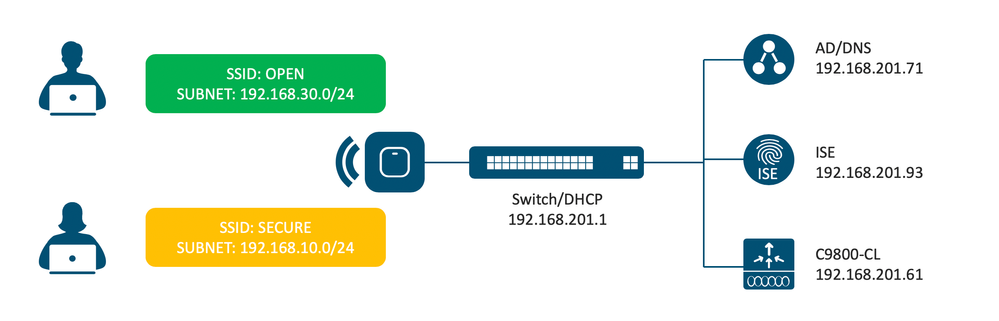
The document does not cover details on how to bootstrap the ISE, C9800, and AP. The document assumes the C9800 is accessible from the management PC and AP is associated to the C9800. The document also assumes underlying network elements are already configured, which includes, VLANs, SVIs, Subnets, DHCP, routing, and DNS. The following diagram and table shows settings for the components.
| C9800 IP | 192.168.201.61 |
| ISE IP | 192.168.201.93 |
| DNS IP | 192.168.201.71 |
| OPEN SSID | OPEN |
| SECURE SSID | SECURE |
| Guest VLAN | 30 |
| Guest Subnet | 192.168.30.0/24 |
| User VLAN | 10 |
| User Subnet | 192.168.10.0/24 |
Notes:
- If static ACL needs to be applied to a session, use AireSpace-ACL-Name (6) attribute to send down a ACL name. The ACL needs to be pre-created on C9800
- If dVLAN needs to be applied to a session, use AireSpace-VLAN-Name (5) attribute to send down a VLAN name/ID. The VLAN needs to be pre-created on C9800. Alternatively standard RADIUS 3 tuple attributes can be used for VLAN assignment using VLAN name/ID
- Redirect ACL follows Catalyst IOS syntax instead of AireOS syntax. So permit statement means the matching traffic is redirected, while deny means it will be allowed without redirect
- With local mode, unlike AireOS, DNS ACL entries are not tied to the redirect ACL. URL entries needs to be defined in the URL Filters and called upon via separate RADIUS attribute during the authentication. More information on this at the end of the document on ISE section.
- With FlexConnect mode, URL filter is tied to the redirect ACL within the flex profile, so URL filter does not need to be called upon via separate RADIUS attribute
- URL redirect feature requires that the http (optionally https) server service on the 9800 be enabled. It is enabled by default but to enable it run 'ip http server' (For HTTP redirect) and 'ip http secure-server' (For HTTPS redirect)
Catalyst 9800 Configuration
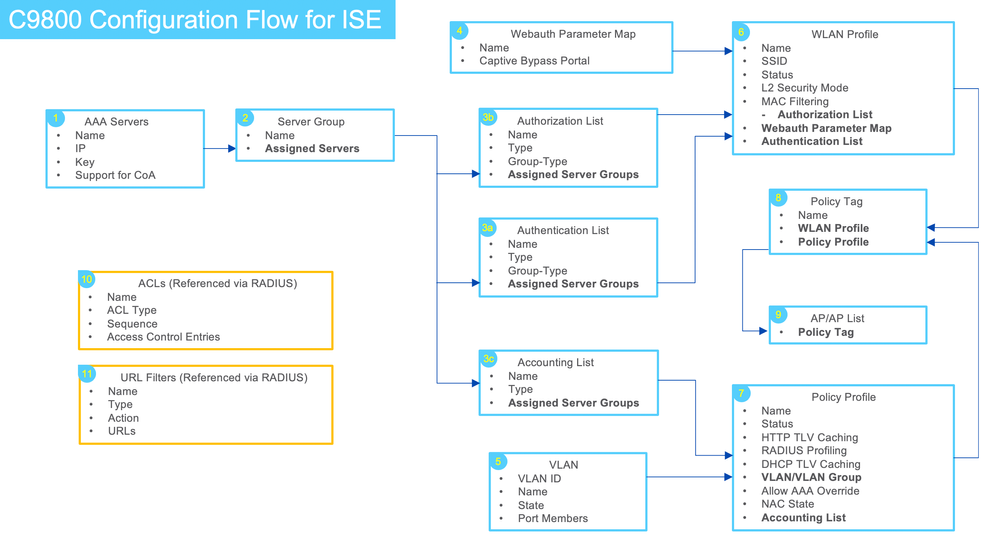
Following diagram shows the C9800 configuration at a high level. Each box represents individual configuration profile with relevant options shown and how each profile feeds into other profiles to make a working configuration. The bullet points within the profile that are in bold represents sub profile being fed into the profile. It also includes the suggested order to create the profiles that maps to the main section of the document.
Steps 1 - 3: Define AAA
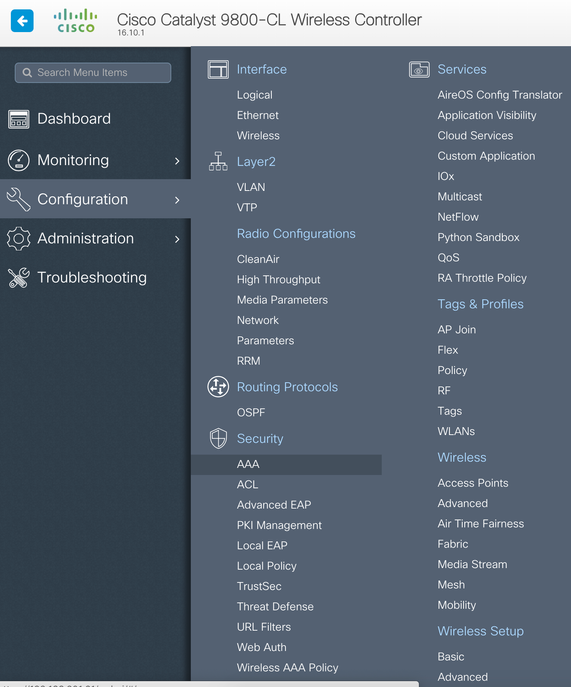
- Go to Configuration > Security > AAA > Servers / Groups > Servers, Click Add
Enter following information (Any configuration not defined in the table assumes default settings):
Name
ISE01 IP 192.168.201.93 Key ***** (Match with ISE) Support for CoA Checked - Click Server Groups, Click Add
Enter following information:
Name
ISE Available Servers ISE01 - Go to Configuration > Security > AAA > AAA Method List > Authentication, Click Add
Create Authentication list using following information that will be used for both OPEN SSID and SECURE SSID:
Name
default Type dot1x Group-Type Group Available Server Groups ISE Note: If clients are failing to associate and authentication request does not show up on ISE Live Log, try setting the authentication list name to 'default' as shown above.
-
Go to Configuration > Security > AAA > AAA Method List > Authorization, Click Add
- Enter following information for AAA Authorization list that will be shared for both SSIDs:
Note: The Authorization name 'default' is significant here since there is no Authorization list that can be defined within the 802.1X WLAN. By using 'default' as name, C9800 can use the ISE to get additional authorization. If default authorization list cannot be used or desired, then named authorization can be created and can be referenced via RADIUS server as a Cisco VSA. The Cisco VSA to use is 'Method-List={authorization-method-list}', which can be configured in ISE advanced Attribute Settings. Please see examples at the end of the document.Name
default Type Network Group-Type Group Available Server Groups ISE - Go to Configuration > Security > AAA > AAA Method List > Accounting, Click Add
- Enter following information for AAA Authorization list that will be shared for both SSIDs:
Name
default Type Identity Available Server Groups ISE
Step 4: Create Webauth Parameter Map (Required for BYOD)
This will only be used in the SECURE SSID to suppress Apple CNA (AKA mini browser) from popping up upon association to the WLAN. This is required as the Apple CNA is unable to fulfill the BYOD onboarding flow.
- Go to Configuration > Security > Webauth > Webauth Parameter Map, Click Add
- Enter Name ‘Captive-Bypass-Portal, Click Apply to Device
- Click ‘Captive-Bypass-Portal’ parameter map from the list
- Check Captive Bypass Portal, Click Update & Apply
Step 5: Create VLANs
- Go to Configuration > Layer 2 > VLAN > VLAN, Click Add
- Add two VLANs using following table for User VLAN and Guest VLAN. These VLANs will be mapped to SECURE SSID and OPEN SSID respectively using policy profiles and tags:
VLAN ID 10 30 Name User Guest State Activated Activated Port Members Gi2 Gi2
- Click Save & Apply to Device
Step 6: Create WLANs
- Go to Configuration > Tags & Profiles > WLANs, Click Add
- Add WLANs using following table for OPEN WLAN and SECURE WLAN. These WLANs will be mapped to the AP using tags (Any configuration not defined in the table assumes default settings):
Note: There is no reference to Authorization List for 'SECURE' SSID. This is not an issue for AAA override operation that applies authorization directly from RADIUS ACCESS-ACCEPT response. However, this is an issue for applying authorization as it requires additional RADIUS communication which requires authorization list. To address this issue, either use special name 'default' as authorization list as configured above or configure ISE to send Cisco VSA 'Method-List={authorization-method-list}' with ACCESS-ACCEPT. See ISE section below for more information.General Profile Name OPEN SECURE SSID OPEN SECURE Status Enabled Enabled Security > Layer 2 Layer 2 Security Mode None WPA + WPA2 MAC Filtering Enabled Authorization List default Security > Layer 3 Webauth Parameter Map Captive-Bypass-Portal Security > AAA Authentication List default default - Click Save & Apply to Device
Step 7: Create Policy Profiles
- Go to Configuration > Tags & Profiles > Policy, Click Add
- Add Policy Profiles for both WLANs using following table. Policy profile covers device sensor, default VLAN, CoA, and RADIUS Accounting. Since VLANs are different, two profiles are created one for each WLAN. These profiles will be mapped to the WLANs using tags (Any configuration not defined in the table assumes default settings):
Note: For device sensor based ISE profiling to work make sure to enable RADIUS profiling, HTTP TLV Caching, DHCP TLV Caching, and Accounting List in the policy profileGeneral Name Guest User Status Enabled Enabled Access Policies HTTP TLV Caching Checked Checked RADIUS Profiling Checked Checked DHCP TLV Caching Checked Checked VLAN/VLAN Group Guest User Advanced Allow AAA Override Checked Checked NAC State Checked Checked Accounting List default default - Click Save & Apply to Device
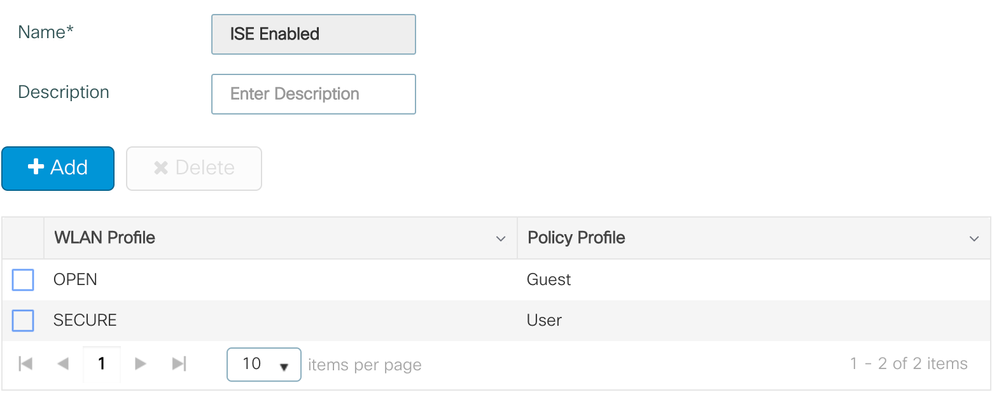
Step 8: Create Policy Tag
- Go to Configuration > Tags & Profiles > Tags, under Policy Click Add
- Enter Name: ISE Enabled
- Within the 'ISE Enabled' Tag window, click Add to map following WLANs to matching policy profiles. This ties the WLAN to the respective Policy Profile.
WLAN Profile Policy Profile OPEN Guest SECURE User - Click Save & Apply to Device
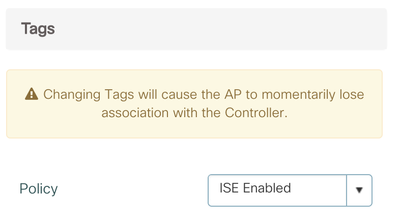
Step 9: Assign Policy Tag to AP
Finally, apply the tag to the AP. This section shows instructions on tying it to a single AP. Using Advanced Wireless Setup Wizard on C9800, same tag can be applied to multiple APs at the same time.
- Go to Configuration > Wireless > Access Points
- Click on the AP Name or MAC address
- Under General > Tags, Select 'ISE Enabled'
- Click Update & Apply to Device
Step 10a: Create Redirect ACL for Guest flow
- Go to Configuration > Security > ACL, Click Add
- Use ACL Name: ACL_WEBAUTH_REDIRECT
- For ACL Type, select IPv4 Extended
- Enter following rules in the ACL for Guest only access redirect ACL
Sequence Action Source IP Destination IP Protocol Source Port Destination Port 10 deny any 192.168.201.93 tcp eq 8443 20 deny any 192.168.201.71 udp eq domain (53) 30 permit any any tcp eq www (80) - Click Save & Apply to Device
Step 10b: Create Redirect ACL for BYOD flow
- Enter following rules in the ACL for Guest and BYOD (Sequence 20 is needed for any endpoints using Network Setup Assistant for BYOD)
Sequence Action Source IP Destination IP Protocol Source Port Destination Port 10 deny any 192.168.201.93 tcp eq 8443 20 deny any 192.168.201.93 tcp eq 8905 30 deny any 192.168.201.71 udp eq domain (53) 40 permit any any tcp eq www (80) - Click Save & Apply to Device
Step 11a: Create URL Filter for BYOD flow
Unlike AireOS which allows DNS entries to be part of redirect ACL, separate URL filter have to be created and be called upon via RADIUS attribute from ISE to permit access to Internet hosts using FQDNs.
- Go to Configuration > Security > URL Filters, Click Add
- Add URL Filter using following table (Example here is to allow access to Google Play store for BYOD):
Note: The PRE-AUTH URL filter always works as if the 'Action' is Permit regardless of whether it is setup as Permit or Deny.Name BYOD-URL-Filter Type PRE-AUTH Action Permit URLs *.google.com
accounts.youtube.com
gstatic.com
*.googleapis.com
*.appspot.com
ggpht.com
gvt1.com
market.android.com
android.pool.ntp.org
*.googleusercontent.com
*.google-analytics.com - Click Save & Apply to Device
Step 11b: Create URL Filter for Social Network Guest access - Facebook
- Go to Configuration > Security > URL Filters, Click Add
- Add URL Filter using following table (Example here is to allow access to Facebook OAUTH2 login for Guest access):
Name Guest-URL-Filter Type PRE-AUTH Action Permit URLs *.facebook.com
*.akamai.com
*.fbcdn.net
*.akamaihd.net - Click Save & Apply to Device
ISE Configuration
Authorization Profile with URL Filter
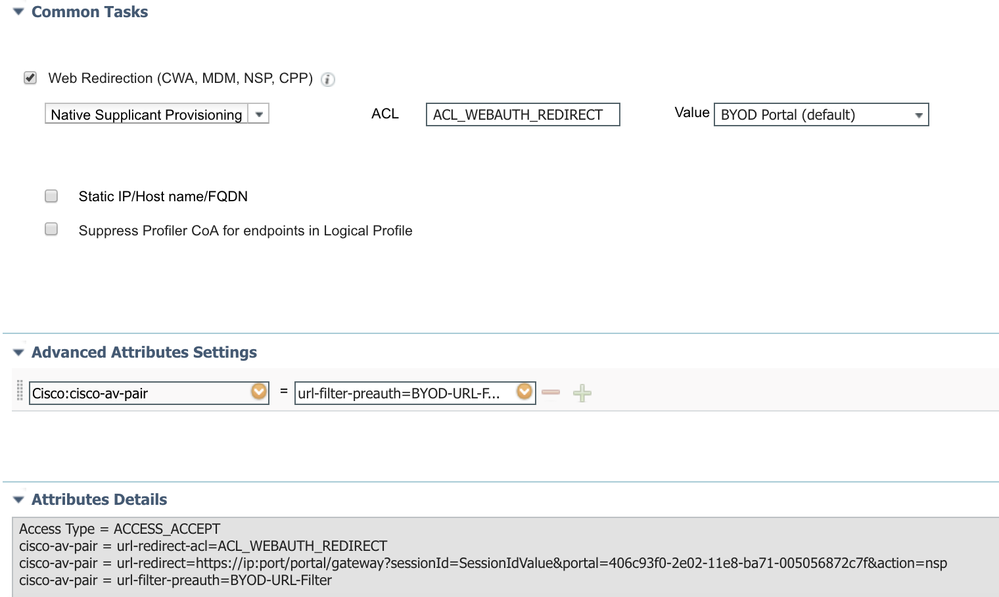
Catalyst 9800 Configuration for FlexConnect Local switching
This section describes additional configuration needed to configure the WLAN as FlexConnect Local switching and integrate it with ISE. This section will utilize existing configurations made above.
Modify Policy Profile
- Go to Configuration > Tags & Profiles > Policy, Click profile name that maps to the WLAN to change to local switching
- Under WLAN Switching Policy section, uncheck Central Switching
- Click Update & Apply to Device
- Repeat above steps for other policy profiles that maps to the WLANs to be converted to local switching
Create Flex Profile
- Go to Configuration > Tags & Profiles > Flex, Click Add
- Add Flex Profile using following table
Note: When 'Central WebAuth' is checked, the C9800 automatically creates a Flex ACL that is in reverse of selected redirect ACL. The permit statements are changed to deny and deny statements are changed to permit. This is due to differences between the two redirect ACL types and slight modification is needed on the ACL to make it work with FlexConnect mode. This option should only be checked for ACL that is going to be used for redirect purpose and for post-authentication ACL, this option should not be checked. See ACL section below for more information.General Name Flex Policy ACL ACL Name ACL_WEBAUTH_REDIRECT Central WebAuth Checked Pre Auth URL Filter (If this is for BYOD, select BYOD-URL-Filter, else blank) VLAN VLAN Name User Guest VLAN Id 10 30 - Click Save & Apply to Device
Create Site Tag
- Go to Configuration > Tags & Profiles > Tags, Click Site, Click Add
- Add Site Tag using following table
Note: Unchecking 'Enable Local Site' will reveal Flex Profile optionName Branch Flex Profile Flex Enable Local Site Unchecked - Click Save & Apply to Device
Assign Site Tag to AP
- Go to Configuration > Wireless > Access Points
- Click on the AP Name or MAC address
- Under General > Tags > Site, Select 'Branch'
- Click Update & Apply to Device
Note: The AP will disconnect for few minutes and when reconnected to the controller, it will be in FlexConnect mode
Modify Redirect ACL
When ACL is translated to the FlexConnect ACL, it requires return traffic to be allowed for it to work. If deny is missing for return traffic the endpoint in Central_WebAuth state will not be able to finish the redirect flow. Following changes to the existing ACL will make ACL wotk for both local mode and FlexConnect mode.
- Go to Configuration > Security > ACL, Click ACL name ACL_WEBAUTH_REDIRECT
- For any deny statement ensure that deny ACE entry is added for return traffic. See sequence 11 & 12 for example:
Sequence Action Source IP Destination IP Protocol Source Port Destination Port 10 deny any 192.168.201.93 tcp eq 8443 11 deny 192.168.201.93 any tcp eq 8443 20 deny any 192.168.201.71 udp eq domain (53) 21 deny 192.168.201.71 any udp eq domain (53) 30 permit any any tcp eq www (80) - Click Update & Apply to Device
Troubleshooting
For more information on the C9800/ISE integration and troubleshooting, please go to: https://www.cisco.com/c/en/us/support/wireless/catalyst-9800-series-wireless-controllers/products-configuration-examples-list.html
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, this is a very good and helpful write-up.
Something also to note is that the http server must be enabled on the controller to process the redirects. It may be on by default, but I had a customer disable it and we spent some time troubleshooting why the redirects were not happening.
ip http server
ip http active-session-modules none
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@jj27 Yes, it is enabled by default. And much of the configuration is done via GUI which assumes it is enabled. But, I've added it in the notes section.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So Helpful, Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is excellent as usual @howon!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Howon
in the article u dont mention how u apply ACL_WEBAUTH_REDIRECT in case of centrally switched WLAN. So it's difficult to conclude how it works finally. There is though n article written by one of wifininjas (https://wifininjas.net/2019/08/13/wn-blog-009-c9800-wlc-guest-mab-cwa-ise/ ) where he describes case where he applies his redirect ACL on global level. It's not possible to comment n article though (to ask the Q :0). Could u pls kindly explain it?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Andrii Oliinyk , when using centrally switched WLAN there is no need to configure the ACL on the Policy Profile, we just need to configure the ACL on the 9800 WLC, and ISE will send the ACL name as an attribute. When locally switched we need to specify the ACL on the flex profile, so the 9800 WLC pushes this ACL to the AP, but will be the same, ISE needs to send the ACL name in the flow for the usage of it. Hope this can help you to better understand.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I haven't seen much regarding RADIUS configuration on the 9800 and "aaa accounting update". In AireOS it's a best practice to configure accounting interim update with a timer value of 0, but that's not accepted on the 9800. The lowest value that is accepted is 1, which is definitely not what I'm after. I found a suggestion for "aaa accounting update newinfo periodic 2880" recommended elsewhere (Not specific to 9800). That seems pretty much the same as interim update with a value of 0 with the benefit that it also updates every 2 days if the device stayed connected for longer than that. Would you suggest that command for 9800 as well?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very helpful.
Note that dACL is NOT supported on Cat 9800 WLC, no matter where you read that it is.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@jasond Can you somehow prove your statement?
It is very important note.
Where is it mentioned (NOT supported) ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@stayd DACL is not official supported until IOS-XE 17.10.1. See What's New in Cisco IOS XE Dublin 17.10.1
|
Downloadable ACL (Central Switching Only) |
The Downloadable ACL (dACL) feature defines and updates ACLs in one place (Cisco ISE) and allows ACL download to all the applicable controllers. For more information, see the Chapter Downloadable ACL (dACL). |
It has worked previously in some small-scale lab, such as our demo lab in Cisco dCloud.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: