- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- AnyConnect: Azure AD SAML SSO
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-26-2019 07:02 AM - edited 02-21-2020 10:03 PM
Preface: I had a hard time locating documentation for configuring AnyConnect with Azure AD as a SAML IdP - So I took some notes and thought I'd share. I hope it helps someone.
Azure Setup
Login to Azure Portal (https://portal.azure.com)
Click Azure Active Directory
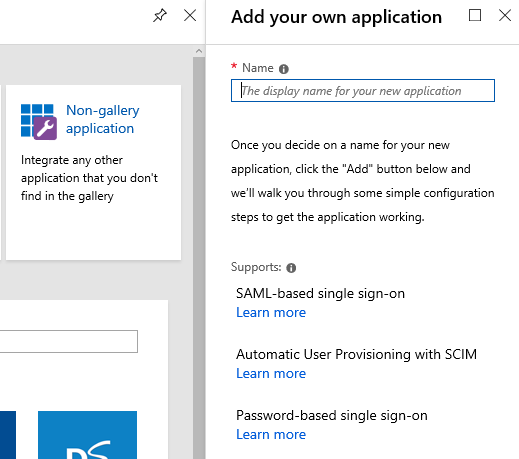
Click Enterprise Applications -> New Application -> Non-Gallery Application
Give it a Name (I'll use AnyConnect-SAML) and click Add at the bottom.
Click the Single sign-on menu Item.
Select SAML
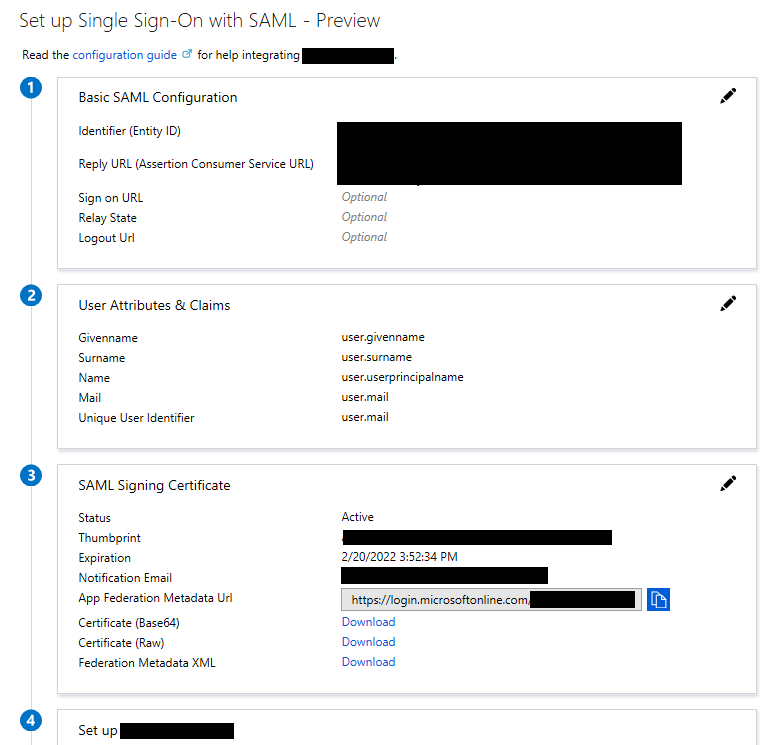
Download the Certificate Base64 from section 3 (We'll install this later)
Make note of the following from Section 4:
Azure AD Identifier - This will be the saml idp in our VPN configuration.
Login URL - This will be the url sign-in
Logout URL - This will be the url sign-out
At this point you have the Data Required to begin configuring the VPN Appliance.
We will need to come back here after configuring the VPN Tunnel-Group and grabbing the metadata.
VPN Configuration - CLI
Alright, we're going to do this on the CLI first, I might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, we're going to be using an ASA running 9.8 code train, and our VPN clients will be 4.6+
Please note there are SAML 2.0 minimum requirements (I believe they are ASA 9.7+ and AC 4.5+ otherwise SAML 2.0 isn't supported or you need to use external browser config… this is outside the scope of this walk-through)
First we'll create a Trustpoint and import our SAML cert.
config t
crypto ca trustpoint AzureAD-AC-SAML
revocation-check none
no id-usage
enrollment terminal
no ca-check
crypto ca authenticate AzureAD-AC-SAML
-----BEGIN CERTIFICATE-----
…
PEM Certificate Text from download goes here
…
-----END CERTIFICATE-----
quit
The following commands will provision your SAML IdP
webvpn
saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from SSO Section 4 of Azure App)
url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (Login URL: SSO Section 4 of Azure App)
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (Logout URL)
trustpoint idp AzureAD-AC-SAML
trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here)
no force re-authentication
no signature
base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
(Configuration of a VPN Tunnel Group or Group Policy is beyond the scope of this document)
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
*Note: There's a feature with the SAML IdP configuration - If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Finishing up with the Azure AD App
We're now ready to grab the meta-data for our tunnel config and finish the Azure application configuration.
You can use a URL similar to below to view the SP metadata.
my.asa.com = the address at which my ASA is reachable
AC-SAML is the tunnel group name configured for SAML auth.
SP Metadata:
https://my.asa.com/saml/sp/metadata/AC-SAML (Also your Entity ID - Azure App Section 1)
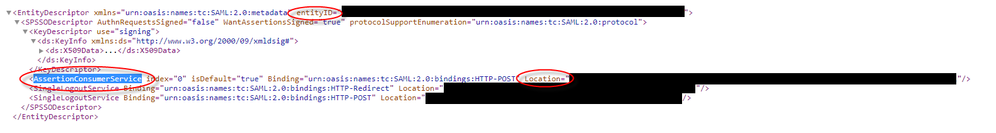
In the metadata XML look for AssertionCustomerService, the Location field in this tag is the Reply URL for the Azure App In SSO Section 1.
Edit the Basic Configuration Section by clicking on the pencil in the top right.
Add the Entity ID & Reply URL
Click Save in the SAML Basic Configuration.
You should now have the basic communication between the ASA and Azure AD wired up.
You may need to add user permissions to the app in Azure AD and conditional access policy for multi-factor, etc.
All beyond the scope of this walk-through, but highly recommended.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Sloanstar this is some of the best AnyConnect documentation I've seen.
I'm currently trying to switch our users from certificate based auth to use Azure AD Conditional Access. MFA works fine, but when I add a condition that the device must be compliant, Apple iOS devices cannot logon because the AnyConnect Embedded browser cannot see or pass the compliance state from the device. After successful MFA they get "You cannot access the resource from this browser on your device. You need to use Safari or Edge."
Do you, or anyone else reading this, know if it's possible to get AnyConnect to use the default web browser for authentication instead of the embedded browser? The same Conditional Access policy works fine on Windows PCs.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this post! Quick question, I followed this steps and I was able to get the connection between the ASA and AzureAD working.
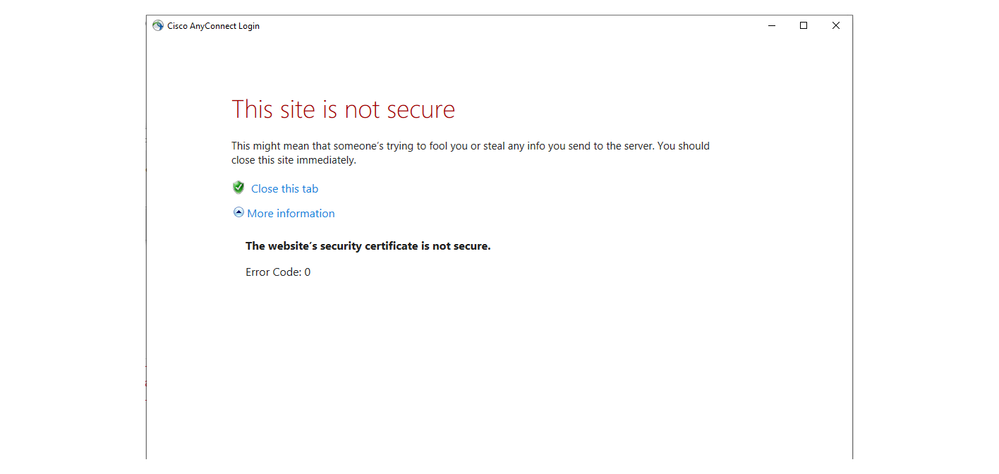
However, when I try to VPN using the tunnel group created to use this, the VPN client says that the site is not trusted. Any ideas on how to resolve this?
I have also installed the base64 cert from Azure to my ASA so I do not know what could possibly be wrong.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@jhidalgo There are a few things that could cause that. Incorrect time on the pc you're using is generally the first thing to check. Second try to go to login.microsoftonline.com through the web browser and see if get you get a similar response. We just had one yesterday that had this error after installing some updates and we had to roll back (from 20H2 to 1909). It shouldn't be something related to the vpn configuration as far as I know.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Went through all replies but not sure this was ever answered... Would this work with AnyConnect Essentials? If not, what license type would I need?
TIA
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
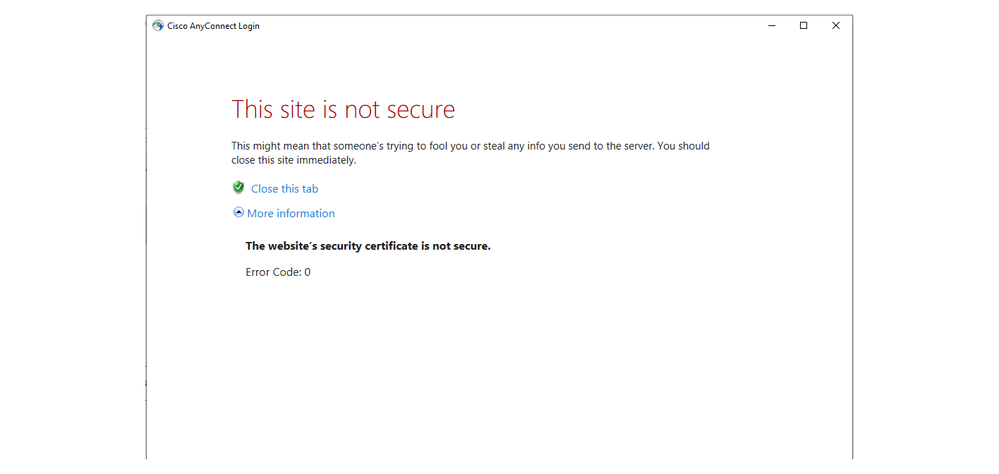
@PatWruk Thanks for responding back. This link, login.microsoftonline.com, works perfectly fine when using a regular browser (Chrome, Firefox, or Internet Explorer.) My issue only occurs when I try to VPN. I should be prompted to enter my credentials from the login site, but instead the Error Code: 0 appears. Also, the time on my pc is fine. I'll check the ASA's time just in case.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Anyone have any advice or tips for enabling the no force re-authentication that was mentioned in the first page of comments? I didn't come across that in my setup. Things are working fine but our users are going to get prompted for MFA every time they connect which for some will be daily. I don't know if my boss is going to want to leave it that way and tell them to deal with it, or if he's going to want to investigate how to change that, so I want to be prepared with an answer. Ideally I'd love to have the option to say have a check in place that if the IP from the user is the same and it was successfully authenticated in the last, say 14 days, then no need to re-auth. Or if the computer is domain joined, no need to prompt, etc. I don't see options to get that granular in the Azure Conditional Access policies. Any suggestions or is this not doable? What does no force re-auth actually do, when would re-auth occur? Assuming it would under some conditions.
Thanks.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Community, I have a question regarding the binding between Anyconnect SALM Server and Azure... Is it need to have a public DNS and valid Cert for the ASA/FTD side? in order to these technologies works happy? or is it possible to use IP Address and Selfsigned Certs for ASA/FTD?....
I appresiate your feedback, Thanks !!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
anyconnect app and Cisco ASA and the other one between Asa and the Clients.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello all,
For this url:
https :// <SUBDOMAIN>.YourCiscoServer.com/saml/sp/metadata/<Tunnel_Group_Name>
Can i use just the public IP of my ASA?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For reasons of the certificate validity, you should use the hostname.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for replying, i did not find any reference for details, should the domain be resolving the public IP of my ASA? and the subdomain is something i create during the Anyconnect Enterprise app installation?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes it should.
- « Previous
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: