- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- AnyConnect: Azure AD SAML SSO
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-26-2019 07:02 AM - edited 02-21-2020 10:03 PM
Preface: I had a hard time locating documentation for configuring AnyConnect with Azure AD as a SAML IdP - So I took some notes and thought I'd share. I hope it helps someone.
Azure Setup
Login to Azure Portal (https://portal.azure.com)
Click Azure Active Directory
Click Enterprise Applications -> New Application -> Non-Gallery Application
Give it a Name (I'll use AnyConnect-SAML) and click Add at the bottom.
Click the Single sign-on menu Item.
Select SAML
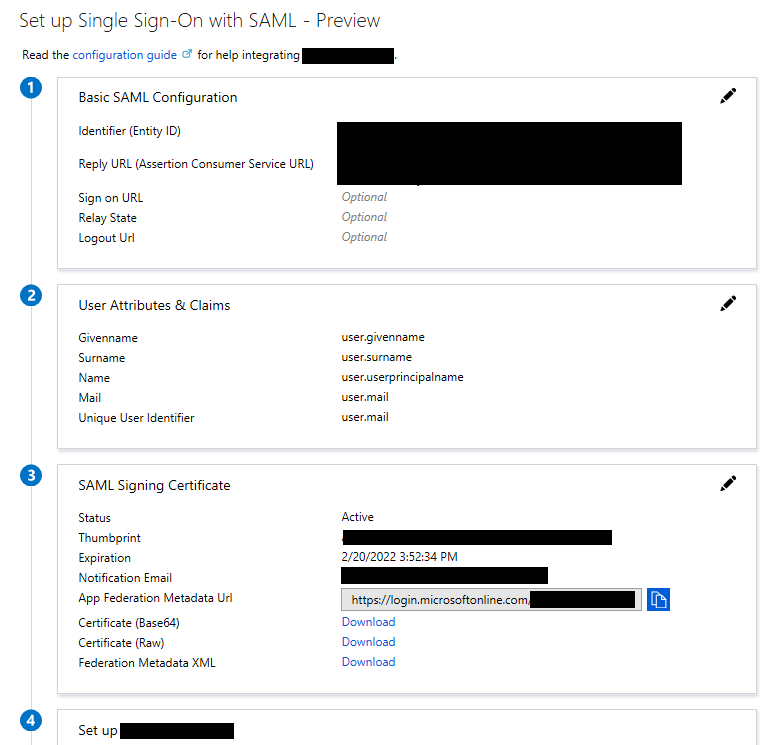
Download the Certificate Base64 from section 3 (We'll install this later)
Make note of the following from Section 4:
Azure AD Identifier - This will be the saml idp in our VPN configuration.
Login URL - This will be the url sign-in
Logout URL - This will be the url sign-out
At this point you have the Data Required to begin configuring the VPN Appliance.
We will need to come back here after configuring the VPN Tunnel-Group and grabbing the metadata.
VPN Configuration - CLI
Alright, we're going to do this on the CLI first, I might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, we're going to be using an ASA running 9.8 code train, and our VPN clients will be 4.6+
Please note there are SAML 2.0 minimum requirements (I believe they are ASA 9.7+ and AC 4.5+ otherwise SAML 2.0 isn't supported or you need to use external browser config… this is outside the scope of this walk-through)
First we'll create a Trustpoint and import our SAML cert.
config t
crypto ca trustpoint AzureAD-AC-SAML
revocation-check none
no id-usage
enrollment terminal
no ca-check
crypto ca authenticate AzureAD-AC-SAML
-----BEGIN CERTIFICATE-----
…
PEM Certificate Text from download goes here
…
-----END CERTIFICATE-----
quit
The following commands will provision your SAML IdP
webvpn
saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from SSO Section 4 of Azure App)
url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (Login URL: SSO Section 4 of Azure App)
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (Logout URL)
trustpoint idp AzureAD-AC-SAML
trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here)
no force re-authentication
no signature
base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
(Configuration of a VPN Tunnel Group or Group Policy is beyond the scope of this document)
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
*Note: There's a feature with the SAML IdP configuration - If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Finishing up with the Azure AD App
We're now ready to grab the meta-data for our tunnel config and finish the Azure application configuration.
You can use a URL similar to below to view the SP metadata.
my.asa.com = the address at which my ASA is reachable
AC-SAML is the tunnel group name configured for SAML auth.
SP Metadata:
https://my.asa.com/saml/sp/metadata/AC-SAML (Also your Entity ID - Azure App Section 1)
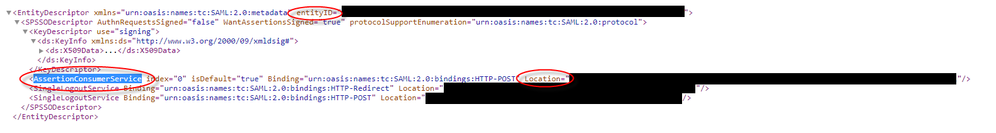
In the metadata XML look for AssertionCustomerService, the Location field in this tag is the Reply URL for the Azure App In SSO Section 1.
Edit the Basic Configuration Section by clicking on the pencil in the top right.
Add the Entity ID & Reply URL
Click Save in the SAML Basic Configuration.
You should now have the basic communication between the ASA and Azure AD wired up.
You may need to add user permissions to the app in Azure AD and conditional access policy for multi-factor, etc.
All beyond the scope of this walk-through, but highly recommended.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@danielkuhl I'm having the same problem in my test setup. Did you find a solution to this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@danielkuhl @danielkuhl , make sure that you are using the Cisco AnyConnect Client , NOT the Cisco AnyConnect App in Windows 10.
I had the same issue, when the IT department installed the App and not the Client on new Windows 10 laptops.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@danielkuhl I think i fixed mine. Try and update the firewall to the newest firmware version. I'm running 9.12(3) on my 5512 and it works great.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am running into an issue where it is working fine in our lab for a single ASA entity. However, we are running into issues with the prod environment with LB between 4 ASA, the common url is giving a " no valid certificate for authentication" - /mfa "microsoft" but it works fine with /VIP "another vendor TFA authentication"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
1+1 questions:
1) Does this work with Anyconnect Essentials licenses?
1+1) Need to test for example by using https://vpn.mycompany.com/test - Should I use that as a base URL?
TIA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Sloanstar
Great post! Yesterday I was making a lab with my customer, in order to implement Azure MFA integrated with AnyConnect VPN in our ASA 5545-X. Followed all the instructions here and in the official Azure guide and it was successful. We had initially the certificate issue too, but that was because we had no DNS name mapped to our ASA public IP so we assigned a DNS registry to these IP and now it works well. Tested several users we had available and they connected to VPN with no issues.
However there was something we didn't like. When disconnecting from the VPN configured with MFA, and trying to reconnect to another VPN, Cisco AnyConnect client redirects us to the last VPN profile used; in this case, the MFA one, but instead of asking the credentials and the MFA verification again in the embedded browser, it simply lets the user to continue to the VPN, authenticating him/her automatically. That's an issue for us, and we need to know if it's fixable from the ASA (through an AnyConnect configuration profile) or from our Azure portal.
We're running ASA 9.12(4) with AnyConnect 4.7.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I managed to configure this, including group locking (with the help of an LDAP authorization server and attribute-map).
But what I haven't figured out yet, can I also do this for the DefaultWebVPNGroup (Default) group profile? Because I'd like to have the users to simply connect to vpn.mydomain.tld instead of something like vpn.mydomain.tld/somegroupurl.
I haven't tested this yet, because it's a live system under quite some home-office load.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks so much for this great article.
We connect to Anyconnect using several URLs, for eg
usaconnect.company.com
partnerconnect.company.com
clientdownload.company.com
etc
The configuration works well for a single URL, for eg usaconnect.company.com.
However things get tricky when I try to add an additional URL to the config.
Some articles indicate that I have to add a second Enterprise Application in the azure portal for the second URL which is what I have tried.
The details from Section 4 of the second Azure App (Azure AD identifier, Login URL, Logout URL) are exactly the same as the ones defined in the first Azure App. Up until this point, it still makes sense, however the sticky point is the base-url which seems to be linked to the URL used to connect to Anyconnect.
Thus in theory I would either need to define a single SAML IdP on my ASA with multiple "base-url" or define several SAML IdP each with their own "base-url". The first option is not supported by design, and the second option doesn't work either as I am not able to configure two SAML IdP with the same Azure AD identifier.
Has anyone been able to configure multiple URLs either via a single Azure App or multiple Azure Apps or any other way ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Have you figure it out? I have a similar setup and will have to configure it.
Anyone had success in deploy the MFA for 4 different regions? I have one URL company.vpn.com that load balance to the nearest DC from the user.
Company.vpn.com can redirect to apac.vpn.company, eu.vpn.company.com and etc.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Leonterry , how many tunnel groups there are in each location?
We have implemented this by using multiple Enterprise Applications (no load balancing to the nearest DC).
One Enterprise Application per tunnel group.
You can configure the Enterprise Application with multiple Identifier (Entity ID) & Reply URL (Assertion Consumer Service URL) but this will not play nice if you try to configure "eu.vpn.company.com" & "apac.vpn.company.com" in the same Enterprise Application.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just one tunnel per location, 4 locations they have their own URL but the loadbalance one is vpn.company.com.
Have you had to configure 4 different anyconnect app's on azure to get it working? My doubt is the saml will work properly when a user has to call vpn.company.com and we will have 4 different Identifier (one or 4 azure apps).
Thank You.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Since you have one tunnel group but 4 locations, I suppose you have to create 4 x Ent Apps .Because you need 4 uniquer pairs of
Identifier (Entity ID) and Reply URL (Assertion Consumer Service URL). The mutual authentication between Cisco ASA and Azure AD is happening on the VPN endpoint level. Not between the Global Load Balancing mechanism - I assume you are using Azure Traffic Manager or Route 53 - for "vpn.company.com" and AAD.
Identifier (Entity ID)
https://us.company.com/saml/sp/metadata/<TunneGroupName>
https://eu.company.com/saml/sp/metadata/<TunneGroupName>
https://apac.company.com/saml/sp/metadata/<TunneGroupName>
https://location4.company.com/saml/sp/metadata/<TunneGroupName>
Note: I would use the same Certificate in Ent Apps and Cisco ASA firewalls.
Otherwise you will have to manage 4 different ones.
Try that, and let us know.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@aantonis Sorry about the Delay - Yes we are using Azure traffic manager, I will have it configured in few weeks and will give my feedback and findings that could help someone out there as well.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The caveats and shortcomings of SAML auth when using multiple site locations and further load-balancing at those locations is ultimately why we did not pursue a wide scale deployment of this authentication method for the enterprise and was limited only to a lab environment. The defined application list grows unwieldy quickly and we chose to stick with other traditional methods that require less overhead to administer.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, realy nice post. Ive been testing this and I am getting it to pop up the MS auth, i choose an account and then it just displays the entityID xml file. Nothing else happens and it fails. I have checked that the EntityID is the same as the Azure Portal etc.
Anyone else having this similar issue ? Thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: