- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- AnyConnect: Azure AD SAML SSO
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-26-2019 07:02 AM - edited 02-21-2020 10:03 PM
Preface: I had a hard time locating documentation for configuring AnyConnect with Azure AD as a SAML IdP - So I took some notes and thought I'd share. I hope it helps someone.
Azure Setup
Login to Azure Portal (https://portal.azure.com)
Click Azure Active Directory
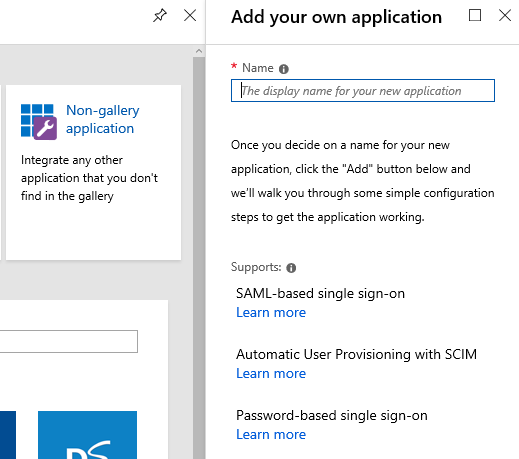
Click Enterprise Applications -> New Application -> Non-Gallery Application
Give it a Name (I'll use AnyConnect-SAML) and click Add at the bottom.
Click the Single sign-on menu Item.
Select SAML
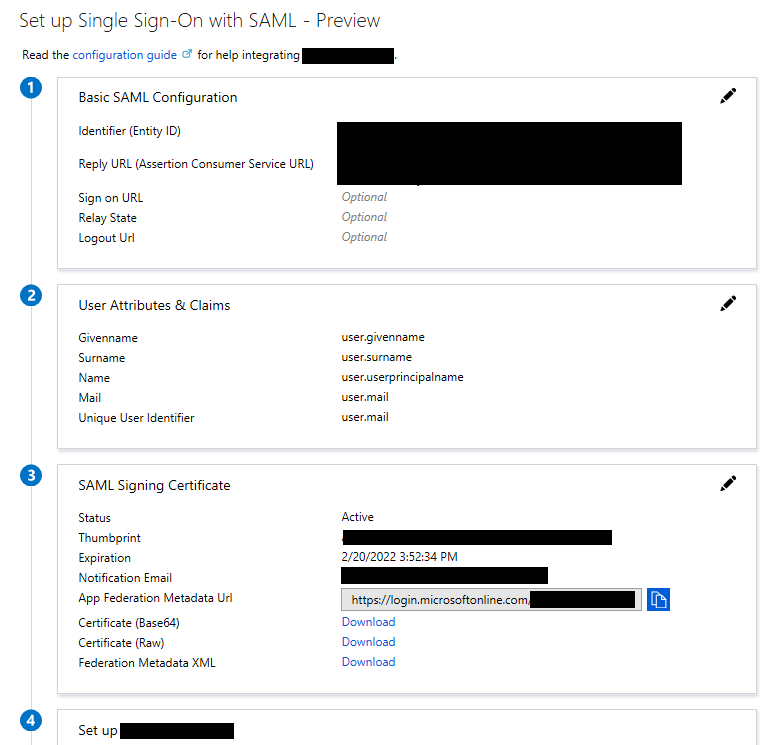
Download the Certificate Base64 from section 3 (We'll install this later)
Make note of the following from Section 4:
Azure AD Identifier - This will be the saml idp in our VPN configuration.
Login URL - This will be the url sign-in
Logout URL - This will be the url sign-out
At this point you have the Data Required to begin configuring the VPN Appliance.
We will need to come back here after configuring the VPN Tunnel-Group and grabbing the metadata.
VPN Configuration - CLI
Alright, we're going to do this on the CLI first, I might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, we're going to be using an ASA running 9.8 code train, and our VPN clients will be 4.6+
Please note there are SAML 2.0 minimum requirements (I believe they are ASA 9.7+ and AC 4.5+ otherwise SAML 2.0 isn't supported or you need to use external browser config… this is outside the scope of this walk-through)
First we'll create a Trustpoint and import our SAML cert.
config t
crypto ca trustpoint AzureAD-AC-SAML
revocation-check none
no id-usage
enrollment terminal
no ca-check
crypto ca authenticate AzureAD-AC-SAML
-----BEGIN CERTIFICATE-----
…
PEM Certificate Text from download goes here
…
-----END CERTIFICATE-----
quit
The following commands will provision your SAML IdP
webvpn
saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from SSO Section 4 of Azure App)
url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (Login URL: SSO Section 4 of Azure App)
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (Logout URL)
trustpoint idp AzureAD-AC-SAML
trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here)
no force re-authentication
no signature
base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
(Configuration of a VPN Tunnel Group or Group Policy is beyond the scope of this document)
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
*Note: There's a feature with the SAML IdP configuration - If you make changes to the IdP config you need to remove the saml identity-provider config from your Tunnel Group and re-apply it for the changes to become effective.
Finishing up with the Azure AD App
We're now ready to grab the meta-data for our tunnel config and finish the Azure application configuration.
You can use a URL similar to below to view the SP metadata.
my.asa.com = the address at which my ASA is reachable
AC-SAML is the tunnel group name configured for SAML auth.
SP Metadata:
https://my.asa.com/saml/sp/metadata/AC-SAML (Also your Entity ID - Azure App Section 1)
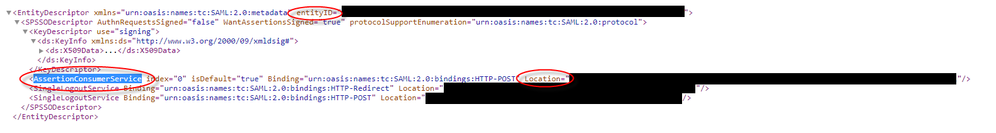
In the metadata XML look for AssertionCustomerService, the Location field in this tag is the Reply URL for the Azure App In SSO Section 1.
Edit the Basic Configuration Section by clicking on the pencil in the top right.
Add the Entity ID & Reply URL
Click Save in the SAML Basic Configuration.
You should now have the basic communication between the ASA and Azure AD wired up.
You may need to add user permissions to the app in Azure AD and conditional access policy for multi-factor, etc.
All beyond the scope of this walk-through, but highly recommended.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Netmetix007 Sounds like you might be having an issue with your reply URL.
Make sure you get it from the SAML SP Metadata and copy it into the Azure App exactly.
It's the AssertionConsumerService Location field.
There's a bit of back and forth between the ASA config and the Azure App while building out the configuration.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
When I try and run this part of the command and try and create a tunnel-group xxxxx webvpn-attributes it doesn't allow me to do so. I just get the following error message ERROR: % Invalid input detected at '^' marker.
I am not sure If I am doing something really silly.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I think you have to specify the type of VPN you are creating before configuring webvpn.
tunnel-group xxxxx type remote-access
tunnel-group xxxxx general-attributes
tunnel-group xxxxx webvpn-attributes
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have a Needed to have multiple enterprise apps, as I am configuring multiple conditional access policies.
How did you manage to have multiple apps? Because if I create multiple app's the Azure AD Identifier will be the same for all, and it is not possible to have the same Azure AD identifier on the ASA config.
Have you added the same certificate for all Enterprise Anyconnect app's? I guess is the only way to have multiple Tunnel Groups?
Thanks.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm not 100% sure if my solution would work for you. But I used an LDAP server on the ASA for the group attribute assignment, that way I only had to use one enterprise app. This guide here:
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/91831-mappingsvctovpn.html
So authentication via SAML, (tunnel) group assignment via LDAP.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Leonterry , you only need one Azure AD identifier on the ASA config. The same "saml identity-provider" will be configured in every tunnel group that requires SAML authentication.
This is regarding the App certificates:
"If you would like to on board multiple TGTs of the server then you need to add multiple instance of the Cisco AnyConnect application from the gallery. Also you can choose to upload your own certificate in Azure AD for all these application instances. That way you can have same certificate for the applications but you can configure different Identifier and Reply URL for every application."
Reference: https://docs.microsoft.com/en-us/azure/active-directory/saas-apps/cisco-anyconnect
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
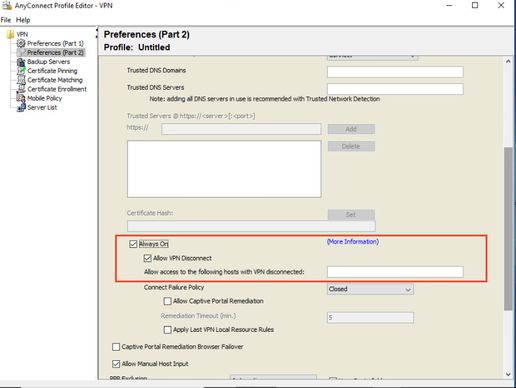
I have found the solution for the always on enabled redirectect problem.
Anyconnect VPN profile editor for the windows application ( 4.9 and 4.10 versiyon has an update.)
You can add allow hosts address to that to the profile (loginmicrosoftonline.com vb... )
I could not see that area on the ASDM, (Maybe it can be seen after ASDM update on the ASA device )
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@aantonis This may be a dumb question, I've been racking my brain on this for a week or so now. What kind of cert does it need to have uploaded to use multiple instances of Azure AnyConnect Application? We have 3 VPNs and therefore 3 Apps in Azure that we are trying to bring into the same ASA.
All of the information I can find on this seems to point to that same doc
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@PatWruk You can use a wildcard cert *.mycompany.com or a cert with multiple alternative names and then add them to the 3 apps and the ASA also needs use the same cert.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Leonterry Awesome, just to make sure I'm understanding this right, we have 3 vpns:
webvpn.mycompany.com
webvpn.mycompany.com/secure
webvpn.mycompany.com/admin
We already have a cert for webvpn.mycompany.com on the ASA, I can then take that cert and upload to Azure and link them to the iDP?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
different tunnel groups and not multiple fqdn’s.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
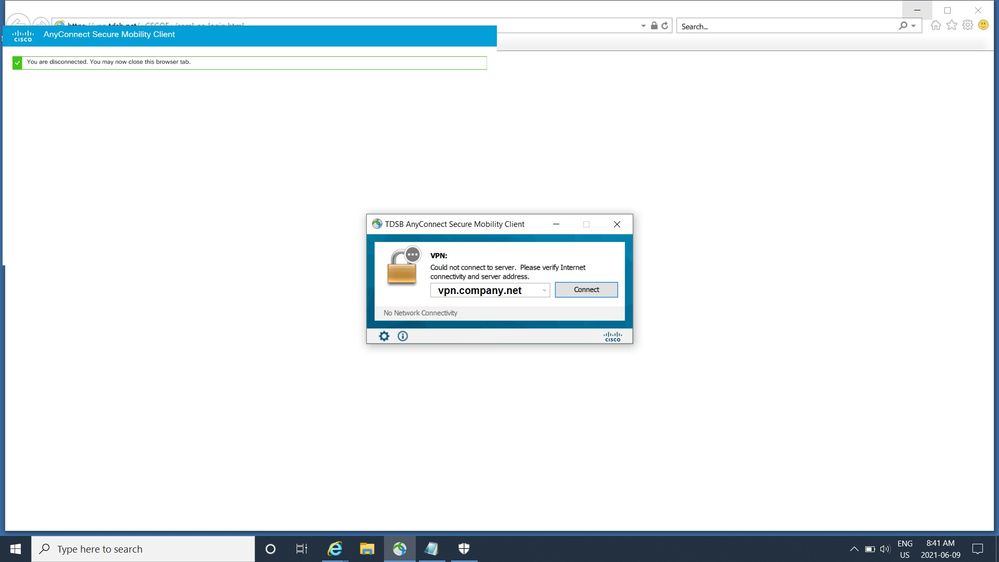
I had the same issue someone else mentioned before (see screenshot below) so I want to be specific about the solution: the ASA needs a later version (I was using 9.7 and that's why I was getting an external/additional browser instead of the one embedded into the new ASA/anyconnect version so I upgraded it both to 9.12.3). Older ASA versions do not support SHA-256 cert presented by Azure (trustpoint idp XXXX - Azure cert in the ASA configuration) and that is another reason because it failed.
In addition to that, you do not need to unchecked the "always on" or add an URL in the anyconnect profile as mentioned before even though looks like it was a workaround.
After upgrading the appliance/client on my laptop, the problem was basically Azure configuration not properly synchronized the metadata information from ASA (ASA Certificate used for outside interface, location,Reply URL,etc). As another option to the URL indicated at the beginning of this post, go to CLI and run the following command:
ASA# sh saml metadata TUNNEL-GROUP-NAME (SP CERTIFICATE INFORMATION, LOCATION, REPLY URL, ETC)
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<EntityDescriptor entityID="https://VPN.COMPANY.NET/saml/sp/metadata/TUNNEL-GROUP-NAME" xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>KTAYt1+iBuU2XRx5H/MmKiTtt8X074+56vCaiUXJsYMYnaGI (***SOME OUTPUT ABOUT THE ASA CERTIFICATE WAS OMITTED)
ua9UBYGbO5HjvCuQClPK6ncgFXDb6IS4
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<AssertionConsumerService index="0" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://VPN.COMPANY.NET/+CSCOE+/saml/sp/acs?tgname=TUNNEL-GROUP-NAME" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://VPN.COMPANY.NET/+CSCOE+/saml/sp/logout"/><SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://VPN.COMPANY.NET/+CSCOE+/saml/sp/logout"/></SPSSODescriptor>
</EntityDescriptor>
ASA#
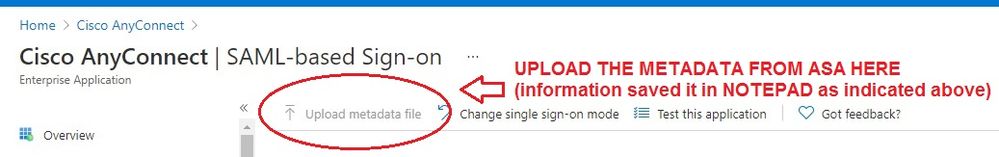
Copy and save the "bold" information above up to the </EntityDescriptor> into notepad, go to Azure site --- > Anyconnect SAML Profile and upload the notepad information (another screenshot below). That would allow to have both sides properly sync'ed.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Another comment, there are some security concerns about using wildcard certs. 2 articles next:
If you use wildcard certificates, we strongly recommend that you partition your domain space for greater security. For example, instead of *.example.com, you can partition it as *.amer.example.com. If you do not partition your domain, it can lead to serious security issues.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Leonterry @aantonis Thank you guys for your help understanding this. We were able to get this setup on all 3 VPNs that we needed it for.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: