- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Failover Site-to-Site IPSec VTI Tunnels Between two ASA 9.7(1) using CLI
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 05-02-2018 04:49 AM
Introduction
This document describes how to configure a site-to-site (LAN-to-LAN) IPSec IKE Version 1 (IKEv1) tunnels using Virtual Tunnel Interface (VTI) between two Cisco ASA. ASA VPN module was enhanced with this logical interface in version 9.7(1) and is used to create a VPN tunnel to a peer, supports route based VPN using profiles attached to VTI interfaces. More details can be found on Release Notes for ASA software 9.7(1).
Objective
Traffic between HQ and DR should pass across primary IPSec tunnel and in the case that primary link fail should failover to the backup tunnel.
Components Used
- Cisco ASA version 9.7(1);
- Cisco 1941 Series Integrated Services Router (ISR) that runs Cisco IOS Version 15.4(3)M2, used to simulate ISP A and B.
Configuration
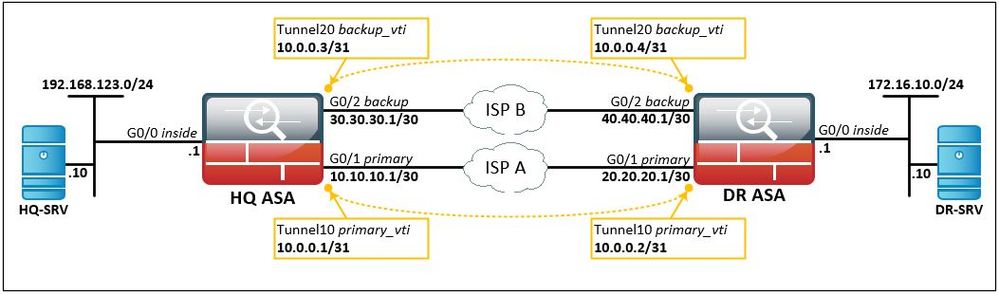
Network Diagram
The information in this document uses network setup as bellow:
Configuration Steps
HQ ASA Configuration
First, we are adding IPSec Phase 1 and 2 configuration:
crypto ikev1 enable primary
crypto ikev1 enable backup
!
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
crypto ipsec ikev1 transform-set SET1 esp-aes esp-sha-hmac
!
crypto ipsec profile PROFILE1
set ikev1 transform-set SET1
set pfs group2
!
tunnel-group 20.20.20.1 type ipsec-l2l
tunnel-group 20.20.20.1 ipsec-attributes
ikev1 pre-shared-key cisco123
!
tunnel-group 40.40.40.1 type ipsec-l2l
tunnel-group 40.40.40.1 ipsec-attributes
ikev1 pre-shared-key cisco123
for VTI interfaces configuration we are using a new feature introduced in version 9.7(1), 31-bit Subnet Mask (“For routed interfaces, you can configure an IP address on a 31-bit subnet for point-to-point connections.”, more information on Release Notes):
interface Tunnel10
description PRIMARY_VTI
nameif primary_vti
ip address 10.0.0.1 255.255.255.254
tunnel source interface primary
tunnel destination 20.20.20.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile PROFILE1
!
interface Tunnel20
description BACKUP_VTI
nameif backup_vti
ip address 10.0.0.3 255.255.255.254
tunnel source interface backup
tunnel destination 40.40.40.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile PROFILE1
to check connectivity to primary interface of our peer we use IP SLA and a track object:
sla monitor 1
type echo protocol ipIcmpEcho 20.20.20.1 interface primary
sla monitor schedule 1 life forever start-time now
!
track 1 rtr 1 reachability
then, add routes to destination networks/addresses:
route primary_vti 172.16.10.0 255.255.255.0 10.0.0.2 1 track 1
route backup_vti 172.16.10.0 255.255.255.0 10.0.0.4 5
route primary 20.20.20.1 255.255.255.255 10.10.10.2 1
route backup 40.40.40.1 255.255.255.255 30.30.30.2 1
DR ASA Configuration
For DR ASA configuration is similar to HQ ASA, only ip addresses are changed:
crypto ikev1 enable primary
crypto ikev1 enable backup
!
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
crypto ipsec ikev1 transform-set SET1 esp-aes esp-sha-hmac
!
crypto ipsec profile PROFILE1
set ikev1 transform-set SET1
set pfs group2
!
tunnel-group 10.10.10.1 type ipsec-l2l
tunnel-group 10.10.10.1 ipsec-attributes
ikev1 pre-shared-key cisco123
isakmp keepalive threshold 10 retry 10
!
tunnel-group 30.30.30.1 type ipsec-l2l
tunnel-group 30.30.30.1 ipsec-attributes
ikev1 pre-shared-key cisco123
isakmp keepalive threshold 10 retry 10
!
interface Tunnel10
description PRIMARY_VTI
nameif primary_vti
ip address 10.0.0.2 255.255.255.254
tunnel source interface primary
tunnel destination 10.10.10.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile PROFILE1
!
interface Tunnel20
description BACKUP_VTI
nameif backup_vti
ip address 10.0.0.4 255.255.255.254
tunnel source interface backup
tunnel destination 30.30.30.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile PROFILE1
!
sla monitor 1
type echo protocol ipIcmpEcho 10.10.10.1 interface primary
sla monitor schedule 1 life forever start-time now
!
track 1 rtr 1 reachability
!
route primary_vti 192.168.123.0 255.255.255.0 10.0.0.1 1 track 1
route backup_vti 192.168.123.0 255.255.255.0 10.0.0.3 5
route primary 10.10.10.1 255.255.255.255 20.20.20.2 1
route backup 30.30.30.1 255.255.255.255 40.40.40.2 1
Verifying the results
State of IKEv1 Phase 1 and Phase 2 can be checked with following commands:
HQ-ASA# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 2
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 2
1 IKE Peer: 40.40.40.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
2 IKE Peer: 20.20.20.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIV
HQ-ASA# show crypto ipsec sa
interface: primary_vti
Crypto map tag: __vti-crypto-map-5-0-10, seq num: 65280, local addr: 10.10.10.1
access-list __vti-def-acl-0 extended permit ip any any
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 20.20.20.1
#pkts encaps: 246, #pkts encrypt: 246, #pkts digest: 246
#pkts decaps: 246, #pkts decrypt: 247, #pkts verify: 247
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 246, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.10.1/0, remote crypto endpt.: 20.20.20.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: E93C8DB9
current inbound spi : 00AC6E39
inbound esp sas:
spi: 0x00AC6E39 (11300409)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, VTI, }
slot: 0, conn_id: 86016, crypto-map: __vti-crypto-map-5-0-10
sa timing: remaining key lifetime (kB/sec): (3914979/28492)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xE93C8DB9 (3913059769)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, VTI, }
slot: 0, conn_id: 86016, crypto-map: __vti-crypto-map-5-0-10
sa timing: remaining key lifetime (kB/sec): (3914979/28491)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
interface: backup_vti
Crypto map tag: __vti-crypto-map-6-0-20, seq num: 65280, local addr: 30.30.30.1
access-list __vti-def-acl-0 extended permit ip any any
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 40.40.40.1
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 30.30.30.1/0, remote crypto endpt.: 40.40.40.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 446005A9
current inbound spi : 8BB0984A
inbound esp sas:
spi: 0x8BB0984A (2343606346)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, VTI, }
slot: 0, conn_id: 77824, crypto-map: __vti-crypto-map-6-0-20
sa timing: remaining key lifetime (kB/sec): (3915000/27623)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x446005A9 (1147143593)
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 2, IKEv1, VTI, }
slot: 0, conn_id: 77824, crypto-map: __vti-crypto-map-6-0-20
sa timing: remaining key lifetime (kB/sec): (3915000/27623)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
HQ-ASA# show crypto ipsec stats
IPsec Global Statistics
-----------------------
Active tunnels: 2
Previous tunnels: 8
Inbound
Bytes: 410004
Decompressed bytes: 410004
Packets: 4881
Dropped packets: 0
Replay failures: 0
Authentications: 4881
Authentication failures: 0
Decryptions: 4881
Decryption failures: 0
TFC Packets: 0
Decapsulated fragments needing reassembly: 0
Valid ICMP Errors rcvd: 0
Invalid ICMP Errors rcvd: 0
Outbound
Bytes: 411012
Uncompressed bytes: 411012
Packets: 4893
Dropped packets: 0
Authentications: 4893
Authentication failures: 0
Encryptions: 4894
Encryption failures: 0
TFC Packets: 0
Fragmentation successes: 0
Pre-fragmentation successses: 0
Post-fragmentation successes: 0
Fragmentation failures: 0
Pre-fragmentation failures: 0
Post-fragmentation failures: 0
Fragments created: 0
PMTUs sent: 0
PMTUs rcvd: 0
Protocol failures: 0
Missing SA failures: 0
System capacity failures: 0
Inbound SA delete requests: 17
Outbound SA delete requests: 0
Inbound SA destroy calls: 17
Outbound SA destroy calls: 6
and interfaces status:
HQ-ASA# show interface Tunnel 10
Interface Tunnel10 "primary_vti", is up, line protocol is up
Hardware is Virtual Tunnel Description: PRIMARY_VTI
MAC address N/A, MTU 1500
IP address 10.0.0.1, subnet mask 255.255.255.254
Traffic Statistics for "primary_vti":
0 packets input, 0 bytes
1 packets output, 28 bytes
0 packets dropped
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 0 bytes/sec
5 minute output rate 0 pkts/sec, 0 bytes/sec
5 minute drop rate, 0 pkts/sec
Tunnel Interface Information:
Source interface: primary IP address: 10.10.10.1
Destination IP address: 20.20.20.1
Mode: ipsec ipv4 IPsec profile: PROFILE1
HQ-ASA# show interface ip brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 192.168.123.1 YES CONFIG up up
GigabitEthernet0/1 10.10.10.1 YES CONFIG up up
GigabitEthernet0/2 30.30.30.1 YES CONFIG up up
GigabitEthernet0/3 unassigned YES unset administratively down up
GigabitEthernet0/4 unassigned YES unset administratively down up
GigabitEthernet0/5 unassigned YES unset administratively down up
GigabitEthernet0/6 unassigned YES unset administratively down up
Management0/0 unassigned YES unset administratively down up
Tunnel10 10.0.0.1 YES CONFIG up up
Tunnel20 10.0.0.3 YES CONFIG up up
You might also see:
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.7
I hope to be helpful.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I was going to post something just like this as I was building what I believe would be the necessary configuration. Each site would have 2 public IPs and would try to use primary-primary, backup-primary, primary-backup, backup-backup in that order. I have 2 more VTI interfaces and more track objects for this. It does seem that using crypto map with 2 peer IP addresses is less involved than this, but that doesn't support IKEv2.
crypto ikev2 policy 10
encryption aes-256
integrity sha256
group 2
prf sha256
lifetime seconds 28800
crypto ikev2 enable OUTSIDE
crypto ipsec ikev2 ipsec-proposal S2S_PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-256
!
crypto ipsec profile S2S_PROFILE
set ikev2 ipsec-proposal S2S_PROPOSAL
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key key123
ikev2 local-authentication pre-shared-key key123
tunnel-group 2.2.2.2 type ipsec-l2l
tunnel-group 2.2.2.2 ipsec-attributes
ikev2 remote-authentication pre-shared-key key123
ikev2 local-authentication pre-shared-key key123
!
interface tunnel 1
nameif A_TO_B_VPN_1
description "PRIMARY LINK TO SITE B MAIN IP"
ip address 192.168.168.1 255.255.255.252
tunnel source interface OUTSIDE
tunnel destination 1.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile S2S_PROFILE
!
interface tunnel 2
nameif A_TO_B_VPN_2
description "SECONDARY LINK TO SITE B MAIN IP"
ip address 192.168.168.5 255.255.255.252
tunnel source interface BACKUP
tunnel destination 1.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile S2S_PROFILE
!
interface tunnel 3
nameif A_TO_B_VPN_3
description "PRIMARY LINK TO SITE B ALTERNATE IP"
ip address 192.168.168.1 255.255.255.252
tunnel source interface OUTSIDE
tunnel destination 2.2.2.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile S2S_PROFILE
!
interface tunnel 4
nameif A_TO_B_VPN_4
description "SECONDARY LINK TO SITE B ALTERNATE IP"
ip address 192.168.168.5 255.255.255.252
tunnel source interface BACKUP
tunnel destination 2.2.2.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile S2S_PROFILE
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key key123
ikev2 local-authentication pre-shared-key key123
tunnel-group 2.2.2.2 type ipsec-l2l
tunnel-group 2.2.2.2 ipsec-attributes
ikev2 remote-authentication pre-shared-key key123
ikev2 local-authentication pre-shared-key key123
!
route A_TO_B_VPN_1 10.0.0.0 255.255.255.0 1.1.1.1 1 track 1
route A_TO_B_VPN_2 10.0.0.0 255.255.255.0 1.1.1.1 10 track 2
route A_TO_B_VPN_3 10.0.0.0 255.255.255.0 2.2.2.2 20 track 3
route A_TO_B_VPN_4 10.0.0.0 255.255.255.0 2.2.2.2 30
sla monitor 1
type echo protocol ipIcmpEcho 1.1.1.1 interface OUTSIDE
num-packets 3
frequency 10
sla monitor schedule 1 life forever start-time now
track 1 rtr 1 reachability
!
sla monitor 2
type echo protocol ipIcmpEcho 1.1.1.1 interface BACKUP
num-packets 3
frequency 10
sla monitor schedule 2 life forever start-time now
track 2 rtr 2 reachability
!
sla monitor 3
type echo protocol ipIcmpEcho 2.2.2.2 interface OUTSIDE
num-packets 3
frequency 10
sla monitor schedule 3 life forever start-time now
track 3 rtr 3 reachability
!
!Don't forget your NAT exemptions
nat (INSIDE,OUTSIDE) source static LOCAL_LAN LOCAL_LAN destination static REMOTE_LAN REMOTE_LAN no-proxy-arp route-lookup
nat (INSIDE,BACKUP) source static LOCAL_LAN LOCAL_LAN destination static REMOTE_LAN REMOTE_LAN no-proxy-arp route-lookup
!You also need to allow ICMP between the sites
icmp permit <REMOTE_PRIMARY_IP> OUTSIDE
icmp permit <REMOTE_SECONDARY_IP> BACKUP
When you run a "show track" you will see your primary->secondary shows as "down" if the far end is not failing. This is due to the far end using its primary WAN as its default route.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi there!
Can you run OSPF over the VTI (tunnle10 & tunnel20)?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there a similar document for those who want to use BGP for routing instead of static routing?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: