- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IP Phone SSL VPN to ASA using AnyConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-05-2010 08:06 AM - edited 08-28-2017 10:14 PM
- Purpose
- Functional Overview
- CUCM Places ASA Certificate Hash and VPN URL in Phone Config
- Phone Connects to ASA
- Software Versions
- Phone Models
- CUCM Configuration
- Phone Configuration
- ASA Configuration
- Additional Requirements:
- Troubleshooting Steps
- Common Issues
Purpose
Starting in CUCM 8.0.1 and IP Phone Firmware 9.X, IP Phones are now able to directly connect to an ASA using the AnyConnect VPN. This document will help address some common issues encountered during intial configuration. This guide will act as a supplement to the Official IP Phone VPN Documentation.
Functional Overview
Before we get into versions and model numbers let's look at how the feature works.
CUCM Places ASA Certificate Hash and VPN URL in Phone Config
Before the phone is ready for VPN, it must first be provisioned using the internal network. This requires direct access to the CUCM TFTP server.
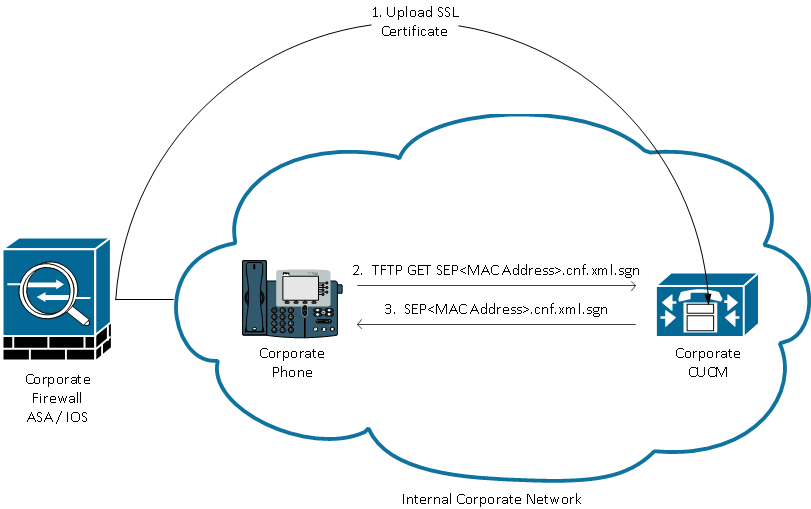
The first step after the ASA is fully configured is to take the ASA HTTPS Certificate and upload it to the CUCM server. This allows the CUCM server to build an IP phone config file that tells the phone how to get to the ASA. The CUCM requires some additional configuration to associate the uploaded certificate with a VPN Profile that can be assigned to the phone.
Here is an example of the IP Phone VPN section of a phone's config file after performing the required configuration:
jasburns@jasburns-gentoo /home/jasburns $ tftp 14.48.44.80 tftp> get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /home/jasburns $ cat SEP0011215A1AE3.cnf.xml.sgn .......... <vpnGroup> [Some Lines Omitted] <addresses> <url1>https://X.X.X.X/PhoneVPN</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>
Note that the URL is printed exactly as entered on the VPN Gateway Configuration page in CUCM. Make sure the IP Phone can resolve this address.
Even more interesting is the Cert Hash. The IP phone configuration does not contain the entire certificate, merely a SHA1 Base64 encoded hash of the certificate.
You can compare the certificate hash in the IP phone configuration file to the cert hash of the actual file on the ASA or CUCM if you copy it to a computer running OpenSSL (either Windows, Linux, or Mac)
$ cat r2800.cisco.com.pem
-----BEGIN CERTIFICATE-----
<Base64 value of the cert omitted>
-----END CERTIFICATE-----
openssl x509 -in r2800.cisco.com.pem -noout -fingerprint
SHA1 Fingerprint=D5:E0:FD:97:75:44:23:D0:C6:59:01:8A:94:D0:46:13:56:D1:85:48
This is the SHA1 Fingerprint in Hexadecimal form. In the configuration file this value is instead printed as the Base64 value. I used the following website to convert from Hex to Base64:
http://tomeko.net/online_tools/hex_to_base64.php
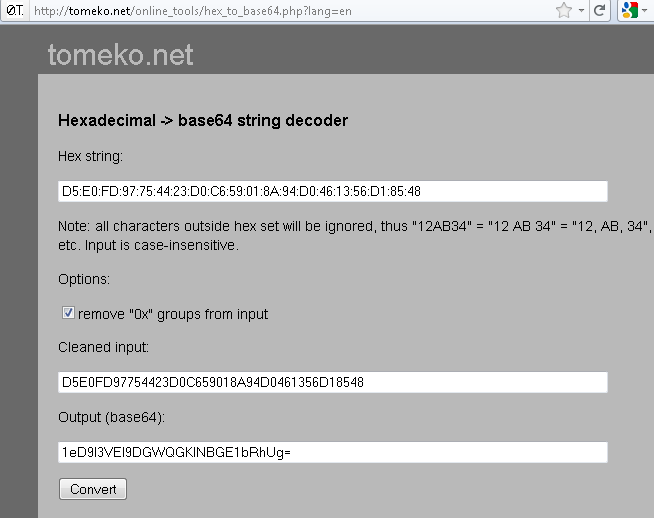
This method can be used to verify the certificate loaded onto and presented by the ASA matches the certificate hash loaded into the phone.
Phone Downloads Configuration
This part is extremely important. The phone must download the configuration (including the certificate hash in Base64) while it is inside the network and has direct access to the CUCM TFTP server.
The phone has to be provisioned inside the network before it can be moved outside the network and use the VPN feature.
Phone Connects to ASA
After internal provisioning has been completed, the phone can be moved to the external network for VPN access. Here the Corporate Phone has been moved to a Home location.
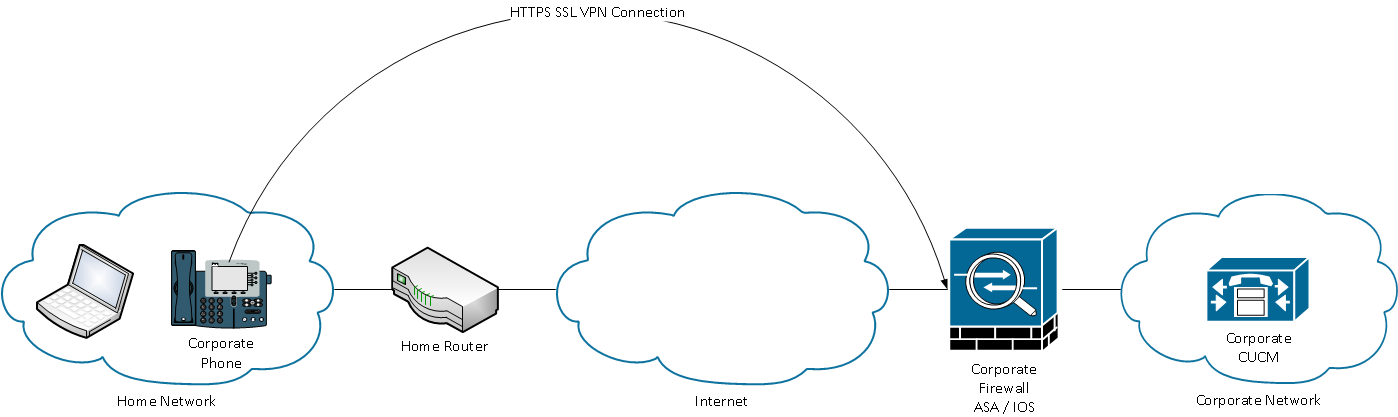
Depending on the phone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once manually initiated. If auto network detect is enabled, the phone will try to ping the TFTP server. If there is no response to this ping request the phone will automatically bring up the VPN process on the phone.
The phone connects on TCP port 443 over HTTPS to the ASA. The ASA responds back with the configured certificate, hopefully the same certificate uploaded to CUCM. In additional TCP 443 (Transport Layer Security, or TLS), the phone will also connect on UDP 443 for DTLS (Datagram Transport Layer Security).
Phone Verifies Presented Certificate
The phone console logs show us the hash of the certificate that the ASA presents in Hex form:
3943: INF 18:10:22.354209 VPNC: vpnc_save_to_file: wrote: </tmp/leaf.crt>, 479 bytes
3944: NOT 18:10:22.355351 VPNC: cert_vfy_cb: peer cert saved: /tmp/leaf.crt
3945: NOT 18:10:22.361892 SECD: Leaf cert hash = D5E0FD97754423D0C659018A94D0461356D18548
3946: NOT 18:10:22.362574 SECD: Hash was found in the trust list
3947: NOT 18:10:22.400294 VPNC: VPN cert chain trusted
These messages show us that the phone was able to validate the certificate that the ASA presented. The cert presented matched the hash in the configuration file.
At this point the phone will establish an SSL session with the ASA and continue setting up the VPN tunnel.
All communication will now flow between the phone and the ASA in an encrypted tunnel. Once the traffic reaches the ASA it will be decrypted and forwarded along to any location in the network that the phone would like to connect to.
The beauty of this solution is that the phone obtains an address on the Internal network that is typically not filtered. The phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Corporate Network. This allows advanced phone services and features to function that might not work through ASA Phone Proxy.
Software Versions
CUCM >= 8.0.1.100000-4
IP Phone >= 9.0(2)SR1S - SCCP
ASA >= 8.0.4
Anyconnect VPN Pkg >= 2.4.1012
Note: A "Premium" license and an "AnyConnect for Cisco VPN Phone" license is required. The part number for the "AnyConnect for Cisco VPN Phone" is L-ASA-AC-PH-55XX= where XX = 05,10,20,40,50,80.
Phone Models
7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete list of supported phones in your CUCM version go to:
https://<CUCM Server IP Address>:8443/cucreports/systemReports.do
Unified CM Phone Feature List
Generate a new report
Feature: Virtual Private Network
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full and correct address to reach the IP Phone VPN tunnel-group on the ASA.
Phone Configuration
- Use a supported phone model per the CUCM Supported Models / Features report.
- Register the phone to the CUCM server on the Internal network
- Configure the IP phone with a TFTP server manually.
- Move the phone to the external network.
ASA Configuration
Configure Anyconnect VPN access on ASA to provide network access.
See http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml for example configuration.
The lateset CUCM Security Guide also provides sample ASA configuration.
Additional Requirements:
- The ASA must have the AnyConnect for Cisco VPN Phone Licensed feature enabled. Licensing info can be found using show version command.
- Group-policy must not be configured with split tunnel or split exclude. Only tunnel all is the supported tunneling policy
- The tunnel-group used can not be the DefaultWEBVPNGroup. Create another tunnel-group and use "group-url https://x.x.x.x/phonevpn enable to map to the correct tunnel-group.
- DTLS must be enabled and negotiated for operation. This requires both tcp/443 and udp/443 to be open and allowed on all devices between the ASA and the phone.
Troubleshooting Steps
- Plug the phone into the internal network. This will test whether the phone's configuration works prior to adding VPN.
- Connect with AnyConnect on a PC from the outside to the ASA. This will confirm that the ASA is configured correctly for Anyconnect
- From the connected PC try to ping the TFTP server and CUCM server. This will test basic ip connectivity to the two servers.
- From the PC try to download the TFTP config file for the phone in question "tftp -i <TFTP Server> GET SEP<Mac Address>.cnf.xml" This will test that the tftp service is reachable and serving files.
- From the PC try to telnet to TCP Port 2000 on the CUCM server "telnet <CUCM IP> 2000". This should immediately come back with a new line and a blank cursor. This will test connectivity to the CUCM SCCP port, for SIP registrations use port 5060 instead.
Common Issues
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints.
- Auto Network Detect does not reliably work in IP Phone Firmware 9.0(2), but does work as expected in 9.2(1).
- Auto Network Detect allows the phone to detect whether it is inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly.
- The phone uses a series of pings to the TFTP server to determine whether it is outside the network. If pings to the TFTP server fail, the VPN GUI will be brought up on the phone and the phone will attempt to access the VPN URL.
- Username and Password authentication from the phone does NOT support the SPACE character in either the username or the password.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is the new ASA 5508 support vpn phone with the same licenses [PRE and phone any connect]
Or there is a change in the license naming as I see something called Plus Perpetual License
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The license enforcement model on the ASA will remain the same. The License for Anyconnect shifted to a enterprise model rather than a per-seat/per-box model. Purchasing a Anyconnect Plus or Apex subscription will all you to get a new activation-key for your ASA which will enable the necessary licenses on the ASA. Please see the Anyconnect Ordering Guide for more details.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
First off, Thanks Jason for the write up. I'm just getting into configuring this VPN setup and I have it working with Certificate based authentication and User and Password authentication, but I have a question regarding the "Password Only" option that shows in the Call Manager > VPN Profile config.
That question is, what is that? In all the research and docs that I've been through, it just merely states that its an option, but no where have I found a good description of where that Password is configured and stored for authentication.
I've seen entries in many docs that says you can configure "Password+Certificate" on the ASA where you configure a user that is the MAC address of the phone and a password. Is this what the Client Authentication option under the VPN Profile is pointing at for authentication when it connects?
Its a little confusing when Call Manager has the Option for "Password Only" but I can't seem to find the instructions anywhere for this configuration. As stated the closest thing I can find is the Password+Certificate config option for the ASA in some docs. Maybe they mention +Cert because no matter what you've got to exchange certs on the ASA and CUCM...
Anyway, any info to confirm my speculation is good or way off-base would be much appreciated!!
Thanks,
Dayne
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dayne,
On the ASA you can configure the tunnel group three ways (related to this configuration)
"authentication aaa" (Only Username+Password)
"authentication certificate" (Only Certificate)
"authentication certificate aaa" (Require both a User/Pass and Certificate)
There is no "Password only" kind of authentication. As a result I would assume that the "password only" option you see is referring to username/password type of authentication.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Jay,
Thanks for the Quick reply! I don't work on the ASA side of the house so your reply was very helpful.
Its weird the Call Manager and the ASA don't have like for like settings for this Config, or at least named the same way.
On the Call Manager side your options for Client Authentication are:
"User and Password" (We use MS user and PIN + RSA token combo)
"Certificate" (Call Manager CAPF uploaded to ASA and an LSC downloaded to the phone)
"Password Only" (This is the weird one. As you stated on the ASA side there really is no Password only config so not sure why its even an option in Call Manager...)
What would be nice is if I could have a user authenticate by passing them off to the CUCM TFTP server they are requesting and have them login based off their User Name and PIN that is set in Call Manager...
Anyway, probably be helpful if I knew the entire ASA config and how it works, but either way, with your info I now have a better understanding what's going on between the two systems.
Thanks again!
-Dayne
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi thanks for the write up.
We have had our VPN phones 7962 working for some time, with a CA cert, we are now required to use tlsv1.2 on the ASA (9.5) as we require PCI compliance, but everytime I change from tlsv1 to tlsv1.2, I receive authentication failed and all concentrators failed.
I have checked the hash of the cert presented by the ASA and from the phone and and its all as it should be?
I have added a custom SSL cipher to tlsv1.2 but we still can't connect, if I revert to tlsv1 it all works again, but we fail compliance.
any ideas?
Thanks,
Al
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Have you tested by Re-generating the Certs on the CUCM and ASA with tlsv1.2 active? I know it 'shouldn't' matter as changing TLS didn't change the Hash used to generate the original Certs, but... I've seen stranger things in my travels with CUCM's cert store.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the response Dayne, we are using ca certs so not generated on the ASA, you may have a point, about re-adding the certs, but i will leave that to a last resort.
However going through the phone logs, I may be a bit closer, it seems the phone is still trying to connect with tlsv1? (if i am reading them correctly) - am I missing a setting in CUCM to set the phone to use tlsv1.2?
From phone logs
1602: NOT 06:44:26.298727 VPNC: protocol_handler: got set ssl command
1603: NOT 06:44:26.299504 VPNC: protocol_handler: current ssl -> TLSv1 SSLv3
1604: NOT 06:44:26.300103 VPNC: protocol_handler: new ssl -> TLSv1 SSLv3
1605: NOT 06:44:26.302294 VPNC: create_ssl_ctx: use TLSv1 or SSLv3
and
1048: NOT 06:44:01.972804 VPNC: do_login: create_ssl_connection
1049: NOT 06:44:01.973858 VPNC: create_ssl_connection: have client cert/pkey
1050: NOT 06:44:01.974634 VPNC: create_ssl_connection: SSL_connect in non-block mode
1051: NOT 06:44:01.976288 VPNC: ssl_state_cb: TLSv1: SSL_connect: before/connect initialization
1052: NOT 06:44:01.978202 VPNC: ssl_state_cb: TLSv1: SSL_connect: unknown state
1053: ERR 06:44:02.170459 VPNC: create_ssl_connection: SSL_connect ret -1 error 5
1054: ERR 06:44:02.171105 VPNC: SSL: SSL_connect: SSL_ERROR_SYSCALL (error 5)
1055: ERR 06:44:02.171654 VPNC: SSL: SSL_connect: no additional error details
1056: ERR 06:44:02.172206 VPNC: create_ssl_connection: SSL setup failure
Al
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In that case my next stop would be the firmware on the phones and making sure what ever version you've got set as the device defaults in CUCM has support for tlsv1.2. If you're running an older firmware version it may not have support.
Also, you can check in the Enterprise parameters, under the Security heading to make sure the "TLS Ciphers" field is set to "All supported AES-256, AES-128 ciphers"...
That's about all I've got right now...
****Edit****
Al, since these security topics have always intrigued me, I did a little more digging and it looks like support for TLSv1.2 wasn't added until Communications Manager 10.5.2. Not sure what version of CUCM you're running as it wasn't in your original post. So, if you aren't on that version or higher of CUCM, that may be an issue.
Check here, release notes for CUCM 10.5.2, page 27 of 102.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Dayne,
Thank you for your help with this, you seem to be correct,I am currently on 8.6.2.
Ok, off I go to plan the upgrade.
Thanks again,
Al
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We have a VPN Phone issue with the 7942's set up as VPN and running CUCM running 9.1.2su4a.
A number of them go into an upgrading firmware mode, lose their VPN connection, and need to be brought into the office. The strange part is the VPN phones are already at the current firmware levels, so unsure what is forcing them to try and upgrade again. When they get stuck in this, the phones are unregistered, so the users can't get into settings etc...
Just curious if anyone else is seeing this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm curious if the VPN connection made by the phone can proxy to a PC connected to the phone's switch port. Are there configuration guidelines, if this is possible? I'd imagine that what the phone is allowed on the ASA connection may also be different that what the PC should be allowed, so I'm curious if this is possible. Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Jason, Still a great post even 10 years later. @Jason Burns
I know this is an old post but I wanted to clarify something.
The documentation for setting up Phone SSL VPN states that if using a 3rd Party CA to sign the ASA cert (Public CA like Entrust or Digicert for example) that its required to upload the signed ASA cert AND the full Public CA chain to the CUCM Phone-VPN Trust store.
You must copy the full certificate chain from the ASA to the CUCM and include all intermediate and root certificates. If the CUCM does not include the full chain, the phones do not have the necessary certificates to authenticate and will fail the SSL VPN handshake.
However; as Jason states in his article, the phone doesn't actually download any certs to itself, but only the Hash value of the cert(s) found in the CUCM Phone-VPN Trust store.
This would imply that the phone doesn't really validate the full chain of trust from Signed_ASA_Cert->IntermediatePublicCA->RootPublicCA, but only compares the Hash of the presented signed ASA cert with it's previously downloaded Hash value.
Can anyone confirm either or both of the two statements?
- The documentation is incorrect in stating it's required that the CA root cert(s) in addition to the ASA signed cert be uploaded to the Phone-VPN Trust
- My current customer running phone SSL VPN did not upload the full CA root chain and its been working fine for years.
- My understanding of the process was correct in that the phone does NOT actually download the full Phone-VPN Trust certs from CUCM, just the Hash value of the Cert in its config file.
Thanks
- « Previous
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



