- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- L2TP over IPsec on Cisco IOS Router Using RADIUS authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 12-13-2014 04:54 PM
Introduction:
This document describes the process of configuring L2TP over IPSEC between Cisco IOS router and windows 7 and user authentication is using RADIUS.
Prerequesites:
This document requires a basic understanding of IPSec protocol. To learn more about IPSec, please refer to An Introduction to IP Security (IPSec) Encryption.
Components Used:
Cisco IOS® Software Release 12.4
Cisco 2961 router
Windows 7 machine (Client)
Windows 2008 server (Running RADIUS protocol)
Configuring AAA parameters:
We are talking about user authentication here. This authentication is done within L2TP framework, not IPSec. Depending on a LAC/LNS combination, and user database we are using, there are several choices here:
- PAP
- CHAP
- MS-CHAPv1
- MS-CHAPv2
- EAP
I would like to point out that all of these methods, except for some EAP types, are not considered secure and there are tools and ways of breaking these methods.
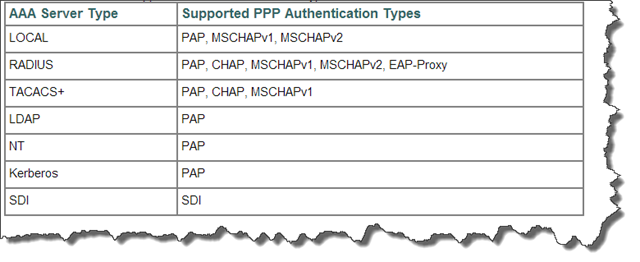
Diagram:
Configuration on Cisco IOS router:
aaa new-model
!
!
aaa authentication ppp l2tp group radius local
!
!
vpdn enable
!
vpdn-group L2TP
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
hash sha
lifetime 86400
!
!
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
!
ip local pool l2tp-pool 192.168.1.1 192.168.1.100
!
!
crypto ipsec transform-set L2TP-Set esp-3des esp-sha-hmac
mode transport
!
crypto dynamic-map dyn-map 10
set transform-set L2TP-Set
!
!
crypto map outside_map 65535 ipsec-isakmp dynamic dyn-map
!
!
interface Loopback1
ip address 192.168.1.10 255.255.255.0
!
interface FastEthernet0/0
ip address 192.168.2.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 47.47.47.100 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map outside_map
!
interface Virtual-Template1
ip unnumbered Loopback1
peer default ip address pool l2tp-pool
ppp authentication ms-chap-v2 l2tp
!
ip route 0.0.0.0 0.0.0.0 47.47.47.47
!
!
ip nat inside source list nat interface FastEthernet0/1 overload
!
ip access-list extended nat
deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.2.0 0.0.0.255 any
!
!
radius-server host 192.168.2.100
radius-server key cisco123
!
!
end
Configuration on Windows Machine:
1. Click on Start and select Control Panel:
2. Select Network and Sharing center :
3. Select "Set up a new connection or network":
4. Select "Connect to a workplace:
5. Select Use my Internet Connection (VPN):
6. Add the public IP address of the ASA (IP on the outside interface of the ASA). Destination name is optional and you can choose anything of your choice and then click on NEXT:
7. Add the username and the password and select "Remember Password" and click on create:
8. In the network and sharing center you will see the connection tab, right click on and click on Properties.
9. In the general TAB make sure the IP address is correct.
10. In the security TAB make sure that type of connection is set to L2TP/IPsec.
11. Go to Advanced settings and add the pre-shared key
12. In the Security, under allow these protocols select MS-CHAP v2 and then click on OK.
13. Double click on L2TP icon and you will get the connection window. Make sure username and passwords are correct. Then click on Connect. And if everything else in place it will get connected :)
14. Once connected right click on the L2tP icon and click on status to see connection details:
Debugs are attached. you can also refer the following links for the L2tP configuration.
Configure L2TP on Cisco IOS using Local Authentication:
https://supportforums.cisco.com/document/9878401/l2tp-over-ipsec-cisco-ios-router-using-windows-8
Configure L2TP over IPsec on Cisco ASA 8.4 using Local Authentication:
https://supportforums.cisco.com/document/12375996/configure-l2tp-over-ipsec-using-cisco-asa-84-and-local-authentication
Configure L2TP over IPsec on Cisco ASA 8.4 using LDAP Authentication:
https://supportforums.cisco.com/document/12376016/configure-l2tp-over-ipsec-using-cisco-asa-84-and-ldap-authentication
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Cisco 2951 router
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
coryalbert i didn't understand your question.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You should add the command bellow to make this thing working.
aaa authorization network default if-authenticated
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Please provide a configuration example for the 4321 router IOS 15.5 (release 3.16.04B.S) to act as VPDN server L2TP protocol for windows 10 L2TP clients
Thank you,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

