- Cisco Community
- Technology and Support
- Small Business Support Community
- Small Business Support Knowledge Base
- PPTP VPN configuration on RV340/345 routers
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-21-2017 04:33 AM - edited 03-21-2019 12:49 AM
Hello,
This article will describe how to configure PPTP VPN on the new RV340/345 routers from the Small Business series.
RV340/345 Configuration
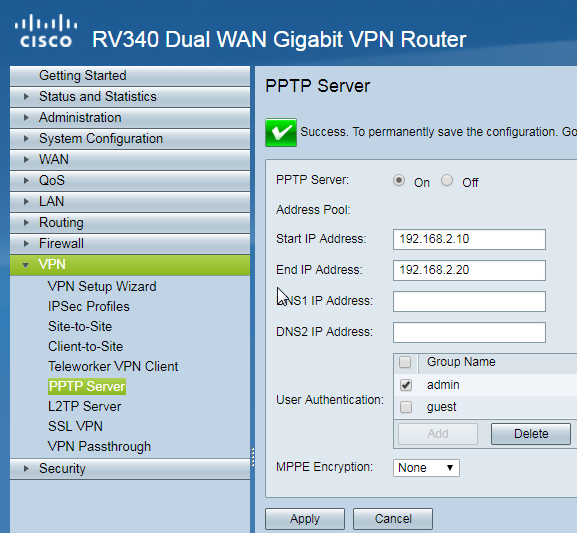
The first step is to enable the PPTP Server:
Go to VPN -> PPTP Server
Change PPTP Server: from Off to On
Select an appropriate pool of IPs for the PPTP clients. By default you cannot use subnets which are already in use by other VLANs on RV340/RV345. In the example below 192.168.1.10-20 is entered, which is part of the default VLAN1 (192.168.1.0/24) and you can see "Subnet range error".
For this example PPTP clients are configured to use the range of 192.168.2.10-192.168.2.20 which is not in use by another VLAN. Select the User Groups which will have access to PPTP VPN. In this case the default "admin" group is used, however, you can create a separate group specifically for VPN users if desired.
It is important to make sure that the selected User Group has been permitted access for PPTP VPN:
These are all the steps necessary to configure PPTP VPN on the RV340 routers. The next section will explain how to configure Windows 7 and Windows 10 for PPTP VPN:
Windows 10
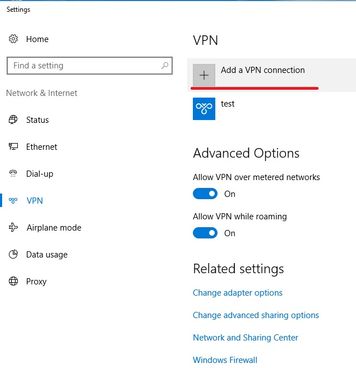
Go to Settings, VPN and click on Add a VPN connection.
Type a Connection name, enter the public WAN IP from your ISP under Server name or address, select the VPN type as PPTP and optionally enter the user name and password here. If you do not enter a username and password here you will be prompted to enter these later.

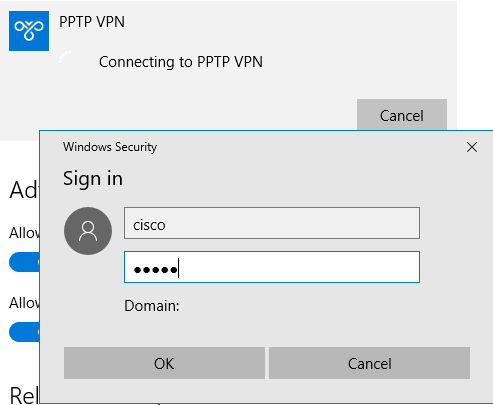
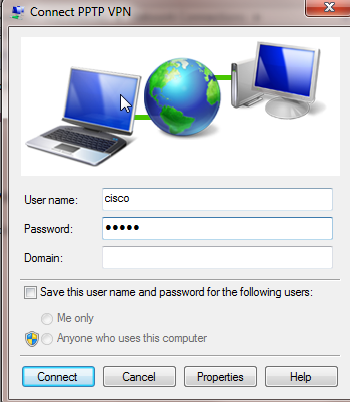
Click Connect on the newly created network adapter "PPTP VPN". You will be prompted for a username and password if you did not enter these on the previous menu.
You may receive the following message. This is due to the fact that by default Windows is using CHAP/MSCHAPv2 for authentication. Select PAP as the authentication method and continue.
Open the Network and Sharing Center.
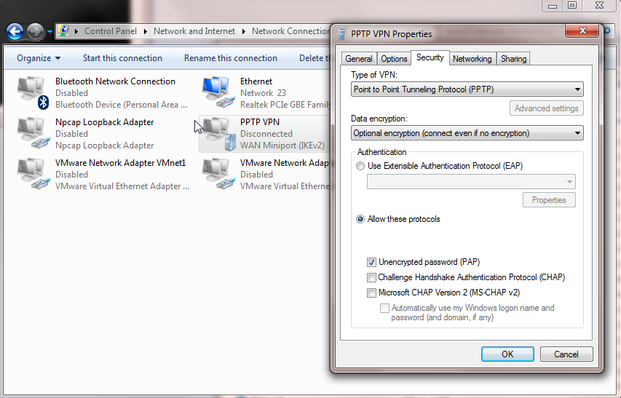
Right click the network adapter that you have created, go to Properties, select the Security tab and change the settings as below:
Type of VPN: Point to Point Tunneling Protocol (PPTP)
Data encryption: Optional encryption (connect even if no encryption)
Authentication: Allow these protocols - Unencrypted password (PAP)
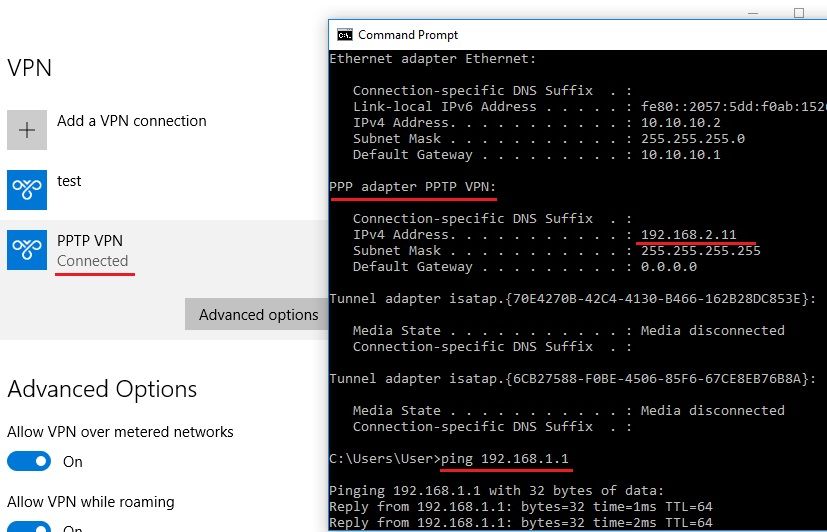
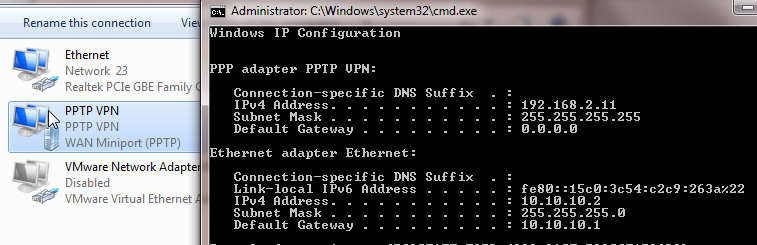
Connect again after making the changes above. You should be able to see status Connected and you should see an IP address from the PPTP pool defined in RV340/345 when you issue "ipconfig".
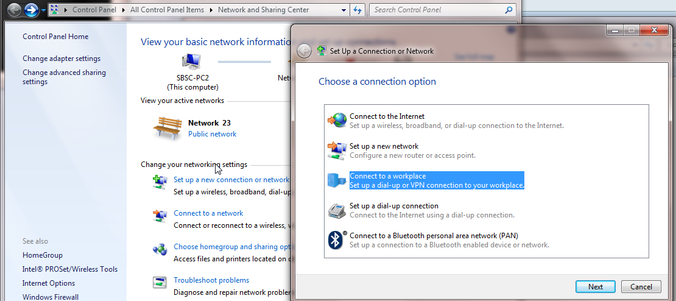
Windows 7
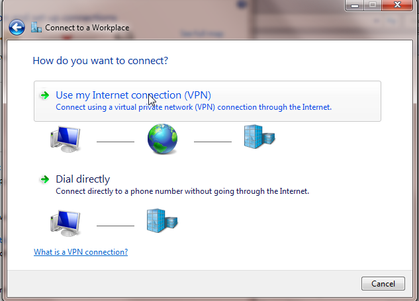
Open the Network and Sharing Center. Select Set up a new connection or network. Select Connect to a workplace and click Next.
Select Use my Internet connection (VPN).
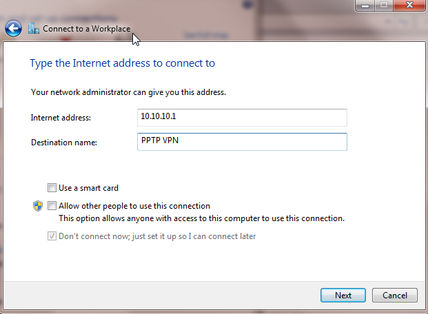
Enter the public WAN IP provided by your ISP under Internet address and provide a meaningful description under Destination Name. Click Next.
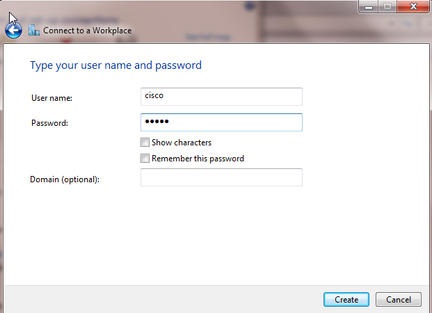
Enter the user name and password and click Create.
Right click the network adapter that you have created, go to Properties, select the Security tab and change the settings as below:
Type of VPN: Point to Point Tunneling Protocol (PPTP)
Data encryption: Optional encryption (connect even if no encryption)
Authentication: Allow these protocols - Unencrypted password (PAP)
Select OK, you will see the following pop up. Select Yes.
Click on the PPTP network adapter. You will be prompted for your user name and password. Click connect.
You should see a message pop up to indicate the connection is successful. If you issue a "ipconfig" command in command prompt you will see that you have received an IP address from the PPTP pool defined in the RV340/345:
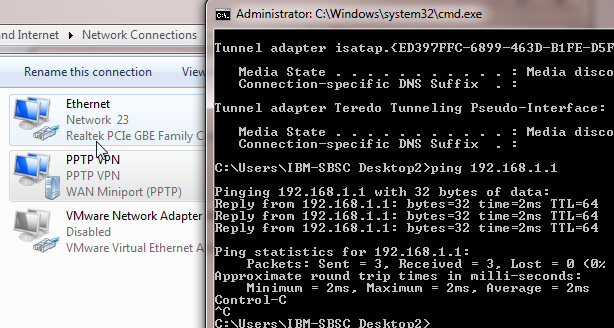
You should also be able to ping the interface of VLAN1 to test connectivity:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Following your instruction I am able to connect only with build-in admin account (cisco in my case). If I add new user to the local database even if it is set as member of the admin group connection is not possible.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the message. Please contact me on ktonev (at) cisco.com so I can open a service request and assist you further. There should be no problem for users different than the admin (cisco) to connect via PPTP VPN.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, it works for me. I have used cisco user and 2 new users too, all of them in admin group.
This is a workaround, but I need to know if this issue will be solved in the next firmware, 1.0.01.18 or newer.
I have bought this router a day ago, and I am thinking to return it. I feel lied with this solution, works better my old RV320
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
With the help from Cisco Support I was able to find out that my problem was in the password of the user in the router local user db. If this password contains some of the special symbols !@#$... user is not able to login via PPTP connection, with this message "The remote connection was denied because the user name and password combination you provided is not recognized, or the selected authentication protocol is not permitted on the remote access server. If the password is limited to letters, digits and punctuation symbols user in the router local User DB is able to connect via PPTP - this is the case with the current latest as of today firmware - v.1.0.01.17. This is not the case with the initial router admin - cisco - who is able to connect via PPTP even if password contains special chars.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
the rv320 has the same problem, (when we bought it, now I dont know), and the max char number for the password was 11.
even so, I still thinking this router is firmware is not finished yet or that they are laughing at us, nothing works as spected
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This RV340 is nothing but a headache. I'm done with Cisco!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have bought few Cisco rv345 router and looks like pptp and l2tp server is not working I have rv320 it's working beautiful but since we bought few of rv345 for our clients as well and all of them failed to make simple vpn connection. I also followed your instruction but still no luck!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
While I can get a Windows 7 PC to PPTP connect to the RV340 using the above instructions, with MPPE disabled as shown, but the connection is all in clear text as verified with wireshark and not encrypted. Calling it a VPN when its not encrypted seems to defeat the purpose. If I turn MPPE on, I cannot find any combination on the windows PPTP configuration that will connect to the RV340. This clearly seems like a bug. I had hoped to use the RV340 to replace an older RV042 that does encrypted PPTP.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Let me tell you and everyone what's happened and share my experience:
I logged tickets with Cisco about PPTP issue after some discussion finally I find out it's working if you are using Remote Authentication Service (RADIUS server) if you want to connect using local user you have to connect with no encryption! (PAP) looks like Cisco did that because they think they can sell RADIUS Server to SMB sector!!(upselling).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
On Thursday, March 7, 2019, I obtained attained, quite exactly, tonyatsp's level of success, and "failure." "Failure" to find any way to employ encryption in the PPTP connection, that is, while being "successful" insofar as to make connections (repeatedly to boot) at all. Clients were (employed separately, not simultaneously, though that probably would also work, as long as all authentication and data flow was in clear text with no PPTP encryption, at all) Windows XP client, or Windows 10 client. There were four client computers involved in such testing; two of each Windows OS type were local (connected to the RV340 @ LAN port) and two of each Windows OS type were remote (connected to RV340 @ WAN port, via internet, and geographically distal).
One thing John did, beyond tonyatsp (who actually was silent on this point) was to simultanously employ an IPSec (Layer 3) VPN, for the remote hook up; the PPTP connections were made and unmade, regardless of whether the IPSec VPN was enabled and up, enabled and down, or disabled. So that's encryption, and it's AES-256 bit encryption at that. But it's Layer 3 encryption, so there a problem because the Layer 3 datagram is a "packet" which is smaller than a Layer 2 datagram, which is a "frame" that envelopes every packet. So unencrypted Layer 2 PPTP frames have exposed headers and footers, it seems. So the impetus to encrypt, at Layer 2, remains.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just my $0.02
I followed this process and managed to connect to the RV340. Of course, I couldn't get any further because we're forced to connect to a different vlan from the vlan where the equipment reside that I want to connect to. I would have assumed that having the RV340 as the default gateway would have enabled resolution and routing of RV340 local addresses but that didn't appear to work.
What is *really* annoying/perplexing/motivating me to throw the RV340 away is that when I terminated the VPN connection, I no longer had access to my local router (which is not a Cisco P.O.S.) although everything else on my local lan was still visible. I was forced to power cycle my local router to restore internet connectivity. To be sure that this was the cause, I reconnect to and disconnected from the remote RV340 again and found exactly the same result - local router had been frozen.
The RV340 in question has been a pain since the day it was purchased. Cisco's insistence on doing things the hard way just makes a network administrator's life more difficult and Cisco's unique take on "clear terminology" is just as frustrating.
The only reason I was even looking at using the router for VPN access is because I was having difficulty with the VPN server that sits behind it. Now I'm wondering if the router isn't the *cause* of that difficulty.
Thank goodness it's the weekend tomorrow. When all the users are offline, I'll swap the RV340 for something that doesn't have a Cisco label on the front of it and see if that solves the problem.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Before attempting to address your particular issue, you should know that both the IP address ranges that you have selected for your vlans are "public" addresses and you shouldn't be using them unless you are Oracle Corporation. The C class address space for private use all start with 192.168 so you should maybe use 192.168.200.0/24 and 192.168.201.0/24 for your vlans.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, just in case someone faces the problem of being able to connect via PPTP but then not being able to ping resources on your local network, what you need to do is add a firewall access rule, from your VLAN subnet to your PPTP subnet. As shown below.
(The image is of the solution to my initial problem)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
RV345 have the same problem. I'm done with Cisco!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: