- Cisco Community
- Technology and Support
- Networking
- Switching
- access-class 10 out - not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 12:00 PM
At first I thought that blocking outbound traffic from the VTY line was to block outbound sessions from a particular router. However, I recalled that traffic generated from a device is not filtered by the ACLs on that device.
I have read that this configuration:
R5#show access-lists
Standard IP access list 10
10 deny any
R5#show running-config | section line vty
line vty 0 4
access-class 10 out
password telnet
login
transport input telnet
line vty 5 15
access-class 10 out
password telnet
login
transport input telnet
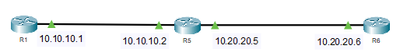
is supposed to block situations like this, R6 does telnet to R5 (this is where the outbound traffic from the VTY line is blocked) and from R5 we do telnet to R1, this shouldn't work, whereas I don't understand why, but it does.
R6#telnet 10.20.20.5
Trying 10.20.20.5 ...Open
User Access Verification
Password:
R5>telnet 10.10.10.1
Trying10.10.10.1 ...Open
User Access Verification
Password:
R1>
Do you have any ideas why this works? Thanks for every attempt to help!
In this video, everything works correctly. I think I did everything the way he did it.
https://www.youtube.com/watch?v=kn1efVxmq-0
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:21 PM
I see what you mean now and I could only speculate that it's a limitation of the packet tracer.
If you work with real routers, then telneting from R6 to R5, which has the access-class 10 out configured on the vty lines, you will not be able to telnet to R1. The message that you receive is:
R5#telnet 10.10.10.1
Trying 10.10.10.1 ...
% Connections to that host not permitted from this terminal
R5#
*** Please Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 12:38 PM
Hello @krzysztofmaciejewskiit ,
To restrict access via telnet or ssh to your router R5, the access-class 10 should be configured in not out.
*** Please Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 12:45 PM - edited 04-21-2024 12:46 PM
I am aware of this, however this is not what I want to achieve. I set up this post to understand the operation of "access-class X out".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:14 PM
this work if you access into R5 and from there you access to R6
here the ACL VTY OUT will work
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:20 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 12:50 PM
Your access-class 10 out will work only if you are connected to R5 via telnet or ssh, that is you are using a vty line. Only then the access-class out command will restrict your telnet to R1.
If you are connected via console, like I imagine you are, the access-class out will not work as you seen already.
*** Please Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:21 PM
I see what you mean now and I could only speculate that it's a limitation of the packet tracer.
If you work with real routers, then telneting from R6 to R5, which has the access-class 10 out configured on the vty lines, you will not be able to telnet to R1. The message that you receive is:
R5#telnet 10.10.10.1
Trying 10.10.10.1 ...
% Connections to that host not permitted from this terminal
R5#
*** Please Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:24 PM
Thanks for the answer!
Will try to test this on physical hardware or in GNS3, maybe it will be better mapped there.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide