- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ARP Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 03:38 PM
Hi Everyone,
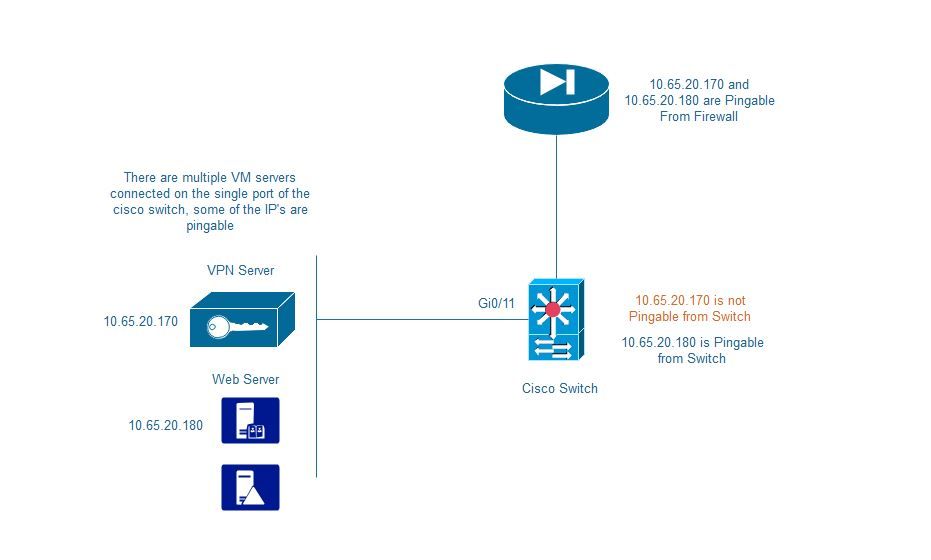
I have a problem with our VPN server connected to our switch. The 10.65.20.170 is not replying to arp/ping from the switch but it is reachable from our Firewall.
There are other VM's running on the same Gig0/11 port and the switch can ping to it without any issue. Only the VPN server as stated below is having an issue.
I already checked the server's subnet mask and it is correct. Any advice?
Thank you
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 07:34 PM
Hi
Can you give more details about L3 interfaces on the switch and firewall from which you're sourcing your pings?
What is the model of your firewall server?
Is there any firewall and/or acl filtering traffic?
Can you run any capture on this vpn server?
Thanks
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 07:49 PM
Hi Francesco,
Thanks for getting back to me on this. The L3 interfaces belong to VLAN1, there is not much anything to see to it.
Firewall is Juniper SSG and I'm not sure if I can pull any logs to the VPN yet.
Is it possible that there's some configuration problem in the VPN server? Since it is a VM that runs on Linux, the other servers looks fine.
Only the connection between the VPN server and the Switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 09:16 PM
check if there Server have FW that drop ping.
try ping from server itself to GW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2021 08:09 PM
Are your servers and the FW attached to same port-group on ESXi? Is the load sharing set the same?
When the fw is replying, can you share the show mac add command output and show ip arp as well please? Then when it's not working, take again both outputs and share them please.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 06:50 PM - edited 01-31-2021 07:59 PM
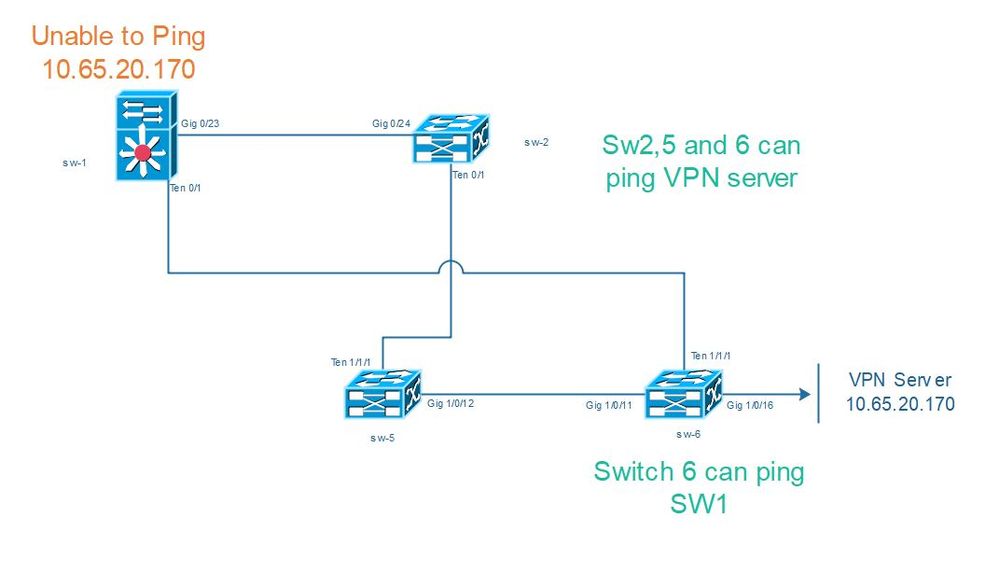
Hi Everyone, thanks for your inputs. We have tried to move the server to another physical port however looks like it's the same.
I have attached the Sw1 and Sw6 configuration and still cannot figure out what may cause the issue. There are other servers on the port of Sw6 and Sw1 can ping it aside from 10.65.20.170.
Switch 2, 5, and 6 where the server is located can ping the server just fine. The spanning-tree does not block any port from Sw1 or Switch 6.
sw-1#show arp | i 10.65.20.170
Internet 10.65.20.170 19 da03.2e49.839a ARPA Vlan1
sw-1#show cdp nei
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone
Device ID Local Intrfce Holdtme Capability Platform Port ID
sw-2.net
Gig 0/23 164 R S I WS-C3560E Gig 0/24
gw-2.net
Gig 0/24 179 R S I 2801 Fas 0/3/3
sw-6.net
Ten 0/1 173 R S I WS-C3750X Ten 1/1/1
sw-1#sw-6#show cdp nei
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
sw-7.net
Gig 1/0/24 150 R S I WS-C3750- Fas 1/0/48
sw-1.net
Ten 1/1/1 136 R S I WS-C3560E Ten 0/1
sw-5.net
Gig 1/0/11 165 R S I WS-C3750X Gig 1/0/12
Update: As per our Sys Admin, he can ping from the Physical Server to Sw1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2021 06:36 PM
Can you make sure sw1 is the root for spanning-tree?
Also if you follow the destination mac address from sw1, what is the path to reach it?
And if you do the invert, from sw6 to reach back mac address of source on sw1, what is the path?
So if I understand you, everything works fine except when you want to reach the VPN server? Have you done a SPAN on sw6 to see if packets are arring to VPN server and also coming back?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2021 06:52 PM
I will explain you the L2,
first here the Server is not config with any VLAN so it will take VLAN native VLAN1.
NOW VLAN 1 in SW-1 have correct subnet 10.65.20.1 that OK
so the frame is take L2 from SW-6 to SW-1,
NOW the issue in SW-1 with static route for 10.65.20.0 !!!
this SW is L3SW and have SVI for VLAN 1 so why it need this static route ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2021 08:07 PM
You have a static route on your sw1 for your vpn server that is sitting on the same vlan?
Is there any svi vlan 1 on other switches? What is the default gateway of this server?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide