- Cisco Community
- Technology and Support
- Networking
- Switching
- If you want to ping your
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5585-X Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 05:47 AM - edited 03-07-2019 10:07 PM
Hello,
I have configured different network on two different interfaces of firewall. Both interfaces are connected with different Cisco switches and hosts on them.
.....configured static route, access policy like "any-any", services like ip, icmp etc., both are configured on same security level.
But not able to ping from one LAN to another LAN, even different interfaces of firewall.
Firewall is in "Router" mode.
Please help what to do next.....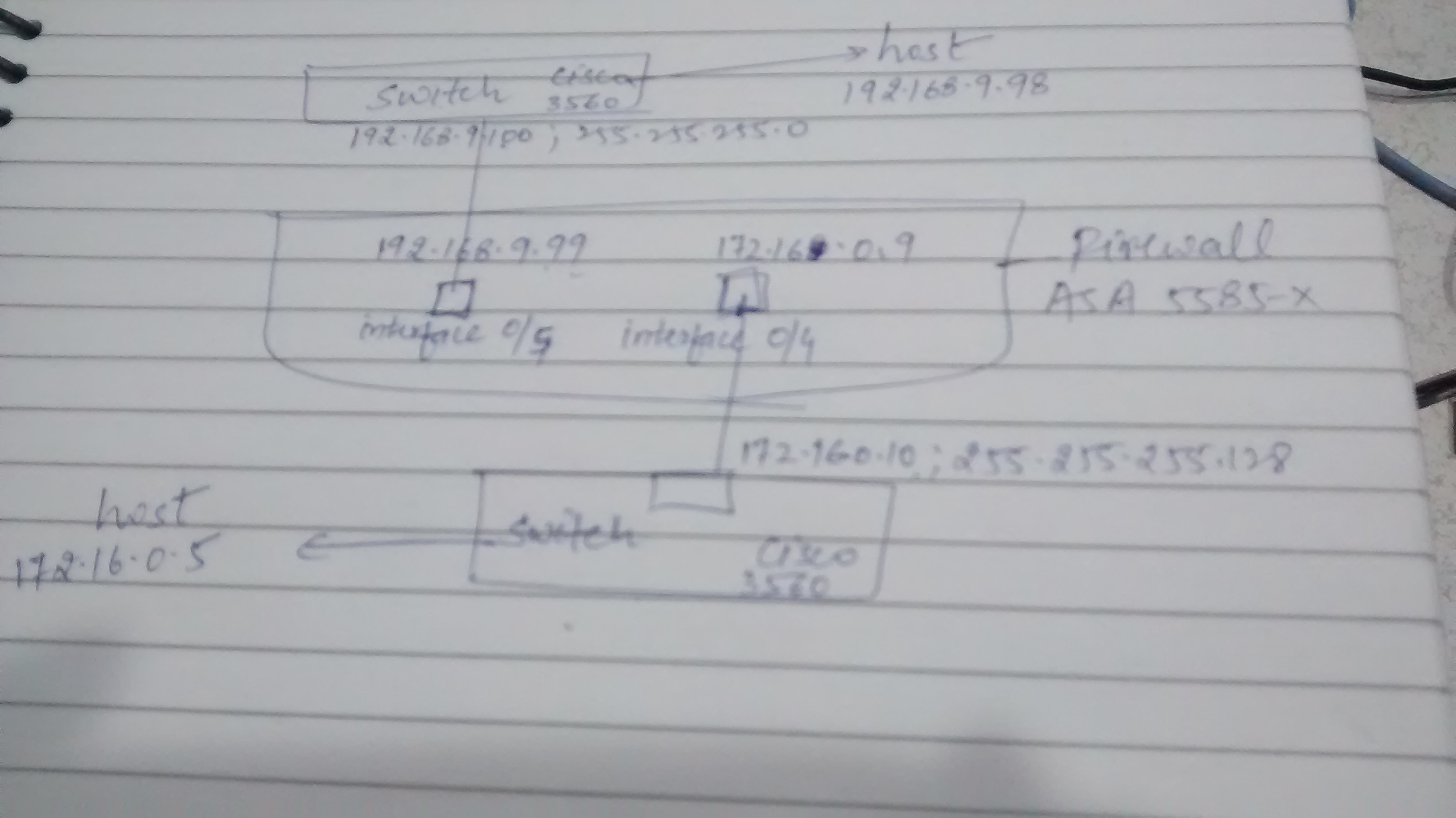
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 12:17 PM
Do you have same-security-traffic permit inter-interface configured? Do you have ICMP permited? Do your ACL's permit ICMP? Are you pinging with ICMP or TCP? What do the logs say? Post a config and we can help further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 10:01 PM
Please find configuration......
Result of the command: "show configuration"
: Saved
: Written by enable_15 at 11:28:07.936 IST Thu Jan 8 2015
!
ASA Version 9.1(2)
!
hostname lcsfirewall
enable password dmFvnBmCe7ncEvAA encrypted
names
!
interface GigabitEthernet0/0
shutdown
no nameif
security-level 0
no ip address
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
nameif cccswitch1
security-level 100
ip address 192.168.9.99 255.255.255.0
!
interface GigabitEthernet0/5
nameif cccswitch2
security-level 100
ip address 172.16.0.9 255.255.255.128
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.15 255.255.255.0
!
interface Management0/1
management-only
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet0/6
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet0/7
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet0/8
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet0/9
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet1/0
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet1/1
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet1/2
shutdown
no nameif
no security-level
no ip address
!
interface TenGigabitEthernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/8
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/9
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/10
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/11
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/12
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/13
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/14
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/15
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/16
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/17
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/18
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet2/19
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone IST 5 30
same-security-traffic permit inter-interface
object network InternalLAN
range 172.16.0.1 172.16.0.127
object network OuterLAN
range 192.168.9.1 192.168.9.254
object-group protocol DM_INLINE_PROTOCOL_5
protocol-object ip
protocol-object icmp
object-group service DM_INLINE_SERVICE_1
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_3
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_4
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
access-list global_mpc extended permit object-group DM_INLINE_PROTOCOL_5 any any
access-list cccswitch1_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list cccswitch2_access_out extended permit object-group DM_INLINE_SERVICE_4 any any
access-list cccswitch2_access_in extended permit object-group DM_INLINE_SERVICE_3 any any
access-list cccswitch1_access_out extended permit object-group DM_INLINE_SERVICE_2 any any
access-list test standard permit 192.168.9.0 255.255.255.0
access-list test standard permit 172.16.0.0 255.255.255.128
pager lines 24
logging enable
logging asdm informational
mtu cccswitch1 1500
mtu cccswitch2 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (any,any) source static any any no-proxy-arp
access-group cccswitch1_access_in in interface cccswitch1
access-group cccswitch1_access_out out interface cccswitch1
access-group cccswitch2_access_in in interface cccswitch2
access-group cccswitch2_access_out out interface cccswitch2
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http authentication-certificate management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt noproxyarp cccswitch1
sysopt noproxyarp cccswitch2
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
!
tls-proxy maximum-session 1000
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
anyconnect-essentials
!
class-map inspection_default
match access-list global_mpc
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:582e6852915fe4d94e0bab6f50fe2595
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 07:25 AM
Can we do a little clean up first? Can you remove the following-
no access-group cccswitch1_access_out out interface cccswitch1
no access-group cccswitch2_access_out out interface cccswitch2
no nat (any,any) source static any any no-proxy-arp
logging buffered 7
Can you then test connectivity and post the results of 'show log'?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 07:57 AM
.....executed all aforesaid commands, still no response.
Result of the command: "show log"
Syslog logging: enabled
Facility: 20
Timestamp logging: disabled
Standby logging: disabled
Debug-trace logging: disabled
Console logging: disabled
Monitor logging: disabled
Buffer logging: level debugging, 644 messages logged
Trap logging: disabled
Permit-hostdown logging: disabled
History logging: disabled
Device ID: disabled
Mail logging: disabled
ASDM logging: level informational, 8674 messages logged
ient management:192.168.1.14/1197
%ASA-6-605005: Login permitted from 192.168.1.14/1197 to management:192.168.1.15/https for user "enable_15"
%ASA-6-110003: Routing failed to locate next hop for icmp from NP Identity Ifc:192.168.9.99/0 to cccswitch1:172.16.0.9/0
%ASA-5-111008: User 'enable_15' executed the 'ping cccswitch1 172.16.0.9' command.
%ASA-5-111010: User 'enable_15', running 'CLI' from IP 0.0.0.0, executed 'ping cccswitch1 172.16.0.9'
%ASA-6-725007: SSL session with client management:192.168.1.14/1197 terminated.
%ASA-6-302014: Teardown TCP connection 2067 for management:192.168.1.14/1197 to identity:192.168.1.15/443 duration 0:00:10 bytes 938 TCP Reset-O
%ASA-6-106015: Deny TCP (no connection) from 192.168.1.14/1197 to 192.168.1.15/443 flags FIN ACK on interface management
%ASA-7-710005: TCP request discarded from 192.168.1.14/1197 to management:192.168.1.15/443
%ASA-6-302013: Built inbound TCP connection 2069 for management:192.168.1.14/1201 (192.168.1.14/1201) to identity:192.168.1.15/443 (192.168.1.15/443)
%ASA-6-725001: Starting SSL handshake with client management:192.168.1.14/1201 for TLSv1 session.
%ASA-7-725010: Device supports the following 6 cipher(s).
%ASA-7-725011: Cipher[1] : RC4-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-RSA-AES256-SHA
%ASA-7-725011: Cipher[4] : AES128-SHA
%ASA-7-725011: Cipher[5] : AES256-SHA
%ASA-7-725011: Cipher[6] : DES-CBC3-SHA
%ASA-7-725008: SSL client management:192.168.1.14/1201 proposes the following 8 cipher(s).
%ASA-7-725011: Cipher[1] : AES128-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-DSS-AES128-SHA
%ASA-7-725011: Cipher[4] : RC4-SHA
%ASA-7-725011: Cipher[5] : DES-CBC3-SHA
%ASA-7-725011: Cipher[6] : EDH-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[7] : EDH-DSS-DES-CBC3-SHA
%ASA-7-725011: Cipher[8] : RC4-MD5
%ASA-7-725012: Device chooses cipher : RC4-SHA for the SSL session with client management:192.168.1.14/1201
%ASA-6-725002: Device completed SSL handshake with client management:192.168.1.14/1201
%ASA-6-605005: Login permitted from 192.168.1.14/1201 to management:192.168.1.15/https for user "enable_15"
%ASA-5-111007: Begin configuration: 192.168.1.14 reading from http [POST]
%ASA-7-111009: User 'enable_15' executed cmd: show configuration
%ASA-6-725007: SSL session with client management:192.168.1.14/1201 terminated.
%ASA-6-302014: Teardown TCP connection 2069 for management:192.168.1.14/1201 to identity:192.168.1.15/443 duration 0:00:00 bytes 8103 TCP Reset-O
%ASA-6-106015: Deny TCP (no connection) from 192.168.1.14/1201 to 192.168.1.15/443 flags FIN ACK on interface management
%ASA-7-710005: TCP request discarded from 192.168.1.14/1201 to management:192.168.1.15/443
%ASA-6-302013: Built inbound TCP connection 2071 for management:192.168.1.14/1205 (192.168.1.14/1205) to identity:192.168.1.15/443 (192.168.1.15/443)
%ASA-6-725001: Starting SSL handshake with client management:192.168.1.14/1205 for TLSv1 session.
%ASA-7-725010: Device supports the following 6 cipher(s).
%ASA-7-725011: Cipher[1] : RC4-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-RSA-AES256-SHA
%ASA-7-725011: Cipher[4] : AES128-SHA
%ASA-7-725011: Cipher[5] : AES256-SHA
%ASA-7-725011: Cipher[6] : DES-CBC3-SHA
%ASA-7-725008: SSL client management:192.168.1.14/1205 proposes the following 8 cipher(s).
%ASA-7-725011: Cipher[1] : AES128-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-DSS-AES128-SHA
%ASA-7-725011: Cipher[4] : RC4-SHA
%ASA-7-725011: Cipher[5] : DES-CBC3-SHA
%ASA-7-725011: Cipher[6] : EDH-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[7] : EDH-DSS-DES-CBC3-SHA
%ASA-7-725011: Cipher[8] : RC4-MD5
%ASA-7-725012: Device chooses cipher : RC4-SHA for the SSL session with client management:192.168.1.14/1205
%ASA-6-725002: Device completed SSL handshake with client management:192.168.1.14/1205
%ASA-6-605005: Login permitted from 192.168.1.14/1205 to management:192.168.1.15/https for user "enable_15"
%ASA-5-111007: Begin configuration: 192.168.1.14 reading from http [POST]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 08:25 AM
If you want to ping your interfaces, you will need to allow that-
icmp permit any cccswitch1
icmp permit any cccswitch2
Please try and ping again and post the log.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 08:56 AM
.....getting similar response.
Result of the command: "show log"
Syslog logging: enabled
Facility: 20
Timestamp logging: disabled
Standby logging: disabled
Debug-trace logging: disabled
Console logging: disabled
Monitor logging: disabled
Buffer logging: level debugging, 1322 messages logged
Trap logging: disabled
Permit-hostdown logging: disabled
History logging: disabled
Device ID: disabled
Mail logging: disabled
ASDM logging: level informational, 8877 messages logged
management:192.168.1.14/1506
%ASA-6-605005: Login permitted from 192.168.1.14/1506 to management:192.168.1.15/https for user "enable_15"
%ASA-6-110003: Routing failed to locate next hop for icmp from NP Identity Ifc:172.16.0.9/0 to cccswitch2:192.168.9.99/0
%ASA-5-111008: User 'enable_15' executed the 'ping cccswitch2 192.168.9.99' command.
%ASA-5-111010: User 'enable_15', running 'CLI' from IP 0.0.0.0, executed 'ping cccswitch2 192.168.9.99'
%ASA-6-725007: SSL session with client management:192.168.1.14/1506 terminated.
%ASA-6-302014: Teardown TCP connection 2116 for management:192.168.1.14/1506 to identity:192.168.1.15/443 duration 0:00:10 bytes 940 TCP Reset-O
%ASA-6-106015: Deny TCP (no connection) from 192.168.1.14/1506 to 192.168.1.15/443 flags FIN ACK on interface management
%ASA-7-710005: TCP request discarded from 192.168.1.14/1506 to management:192.168.1.15/443
%ASA-6-302013: Built inbound TCP connection 2118 for management:192.168.1.14/1519 (192.168.1.14/1519) to identity:192.168.1.15/443 (192.168.1.15/443)
%ASA-6-725001: Starting SSL handshake with client management:192.168.1.14/1519 for TLSv1 session.
%ASA-7-725010: Device supports the following 6 cipher(s).
%ASA-7-725011: Cipher[1] : RC4-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-RSA-AES256-SHA
%ASA-7-725011: Cipher[4] : AES128-SHA
%ASA-7-725011: Cipher[5] : AES256-SHA
%ASA-7-725011: Cipher[6] : DES-CBC3-SHA
%ASA-7-725008: SSL client management:192.168.1.14/1519 proposes the following 8 cipher(s).
%ASA-7-725011: Cipher[1] : AES128-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-DSS-AES128-SHA
%ASA-7-725011: Cipher[4] : RC4-SHA
%ASA-7-725011: Cipher[5] : DES-CBC3-SHA
%ASA-7-725011: Cipher[6] : EDH-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[7] : EDH-DSS-DES-CBC3-SHA
%ASA-7-725011: Cipher[8] : RC4-MD5
%ASA-7-725012: Device chooses cipher : RC4-SHA for the SSL session with client management:192.168.1.14/1519
%ASA-6-725002: Device completed SSL handshake with client management:192.168.1.14/1519
%ASA-6-605005: Login permitted from 192.168.1.14/1519 to management:192.168.1.15/https for user "enable_15"
%ASA-5-111007: Begin configuration: 192.168.1.14 reading from http [POST]
%ASA-7-111009: User 'enable_15' executed cmd: show configuration
%ASA-6-725007: SSL session with client management:192.168.1.14/1519 terminated.
%ASA-6-302014: Teardown TCP connection 2118 for management:192.168.1.14/1519 to identity:192.168.1.15/443 duration 0:00:00 bytes 8157 TCP Reset-O
%ASA-6-106015: Deny TCP (no connection) from 192.168.1.14/1519 to 192.168.1.15/443 flags FIN ACK on interface management
%ASA-7-710005: TCP request discarded from 192.168.1.14/1519 to management:192.168.1.15/443
%ASA-6-302013: Built inbound TCP connection 2120 for management:192.168.1.14/1523 (192.168.1.14/1523) to identity:192.168.1.15/443 (192.168.1.15/443)
%ASA-6-725001: Starting SSL handshake with client management:192.168.1.14/1523 for TLSv1 session.
%ASA-7-725010: Device supports the following 6 cipher(s).
%ASA-7-725011: Cipher[1] : RC4-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-RSA-AES256-SHA
%ASA-7-725011: Cipher[4] : AES128-SHA
%ASA-7-725011: Cipher[5] : AES256-SHA
%ASA-7-725011: Cipher[6] : DES-CBC3-SHA
%ASA-7-725008: SSL client management:192.168.1.14/1523 proposes the following 8 cipher(s).
%ASA-7-725011: Cipher[1] : AES128-SHA
%ASA-7-725011: Cipher[2] : DHE-RSA-AES128-SHA
%ASA-7-725011: Cipher[3] : DHE-DSS-AES128-SHA
%ASA-7-725011: Cipher[4] : RC4-SHA
%ASA-7-725011: Cipher[5] : DES-CBC3-SHA
%ASA-7-725011: Cipher[6] : EDH-RSA-DES-CBC3-SHA
%ASA-7-725011: Cipher[7] : EDH-DSS-DES-CBC3-SHA
%ASA-7-725011: Cipher[8] : RC4-MD5
%ASA-7-725012: Device chooses cipher : RC4-SHA for the SSL session with client management:192.168.1.14/1523
%ASA-6-725002: Device completed SSL handshake with client management:192.168.1.14/1523
%ASA-6-605005: Login permitted from 192.168.1.14/1523 to management:192.168.1.15/https for user "enable_15"
%ASA-5-111007: Begin configuration: 192.168.1.14 reading from http [POST]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 09:30 AM
The interfaces are up right?
'show interface ip brief'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 09:34 AM
Yes, interfaces are up...
Result of the command: "show interface ip brief"
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 unassigned YES unset administratively down down
GigabitEthernet0/1 unassigned YES unset administratively down down
GigabitEthernet0/2 unassigned YES unset administratively down down
GigabitEthernet0/3 unassigned YES unset administratively down down
GigabitEthernet0/4 192.168.9.99 YES CONFIG up up
GigabitEthernet0/5 172.16.0.9 YES CONFIG up up
Internal-Data0/0 unassigned YES unset up up
Internal-Data0/1 unassigned YES unset up up
Internal-Data0/2 unassigned YES unset up up
Internal-Data0/3 unassigned YES unset up up
Internal-Data0/4 unassigned YES unset up up
Internal-Data0/5 unassigned YES unset up up
Internal-Data0/6 unassigned YES unset up up
Internal-Data0/7 unassigned YES unset up up
Internal-Data0/8 unassigned YES unset up up
Internal-Data0/9 unassigned YES unset up up
Internal-Data0/10 unassigned YES unset up up
Internal-Data0/11 unassigned YES unset up up
Internal-Data0/12 unassigned YES unset up up
Internal-Data0/13 unassigned YES unset up up
Management0/0 192.168.1.15 YES CONFIG up up
Management0/1 unassigned YES unset administratively down down
TenGigabitEthernet0/6 unassigned YES unset administratively down down
TenGigabitEthernet0/7 unassigned YES unset administratively down down
TenGigabitEthernet0/8 unassigned YES unset administratively down down
TenGigabitEthernet0/9 unassigned YES unset administratively down down
Internal-Data1/0 unassigned YES unset up up
Internal-Data1/1 unassigned YES unset up up
Internal-Data1/2 unassigned YES unset up up
TenGigabitEthernet1/0 unassigned YES unset administratively down down
TenGigabitEthernet1/1 unassigned YES unset administratively down down
TenGigabitEthernet1/2 unassigned YES unset administratively down down
TenGigabitEthernet1/3 unassigned YES unset administratively down down
GigabitEthernet2/0 unassigned YES unset administratively down down
GigabitEthernet2/1 unassigned YES unset administratively down down
GigabitEthernet2/2 unassigned YES unset administratively down down
GigabitEthernet2/3 unassigned YES unset administratively down down
GigabitEthernet2/4 unassigned YES unset administratively down down
GigabitEthernet2/5 unassigned YES unset administratively down down
GigabitEthernet2/6 unassigned YES unset administratively down down
GigabitEthernet2/7 unassigned YES unset administratively down down
GigabitEthernet2/8 unassigned YES unset administratively down down
GigabitEthernet2/9 unassigned YES unset administratively down down
GigabitEthernet2/10 unassigned YES unset administratively down down
GigabitEthernet2/11 unassigned YES unset administratively down down
GigabitEthernet2/12 unassigned YES unset administratively down down
GigabitEthernet2/13 unassigned YES unset administratively down down
GigabitEthernet2/14 unassigned YES unset administratively down down
GigabitEthernet2/15 unassigned YES unset administratively down down
GigabitEthernet2/16 unassigned YES unset administratively down down
GigabitEthernet2/17 unassigned YES unset administratively down down
GigabitEthernet2/18 unassigned YES unset administratively down down
GigabitEthernet2/19 unassigned YES unset administratively down down
Internal-Data2/0 unassigned YES unset up up
Internal-Data2/1 unassigned YES unset up up
Internal-Data2/2 unassigned YES unset up up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2015 09:43 AM
I see that you're running this command 'ping cccswitch2 192.168.9.99'. Can you try 'ping 192.168.9.99'?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
