- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: C9300 Routing issue?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
C9300 Routing issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 08:15 AM
This is a diagram of my simple network.
The firewall is a FortiGate. I have my LAN and VLAN interfaces under my LAN.
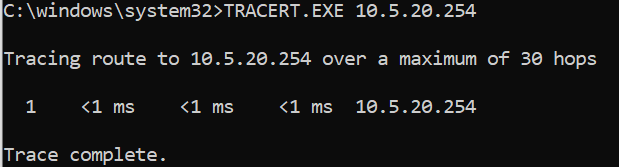
The issue is when I placed my PC on VLAN20, the internet bounces. Found out, I can ping my firewall gateway of 10.5.20.254, but I couldn't traceroute to it. When pinging 40 or 60% of packets failed. I have no static routes.
Routes...
- Labels:
-
Catalyst 9000
-
Other Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 08:26 AM - edited 12-18-2020 08:27 AM
What is the PC IP address in VLAN 20, what is the GW setup ?
where is your Layer 2 spanning Root for VLAN 10/20/3040 ( Hope that is Cat 9300 root bridge right ?)
By default some FW dont allow PING and Traceroute.
Couple of test : ( also post full configuration of Cat 9300 and Nexus to look)
1. is your ping from 10.5.20.249 to 10.5.20.254 ok ? both the sides ?
2. PC can ping 10.5.20.2 249 ? with out packet Loss ?
3. PC can ping 10.5.20.2 250 ? with out packet Loss ?
Do you have any static route on FW back to switch - and NAT for these VLAN 10 20 30 40 range IP address ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 10:59 AM
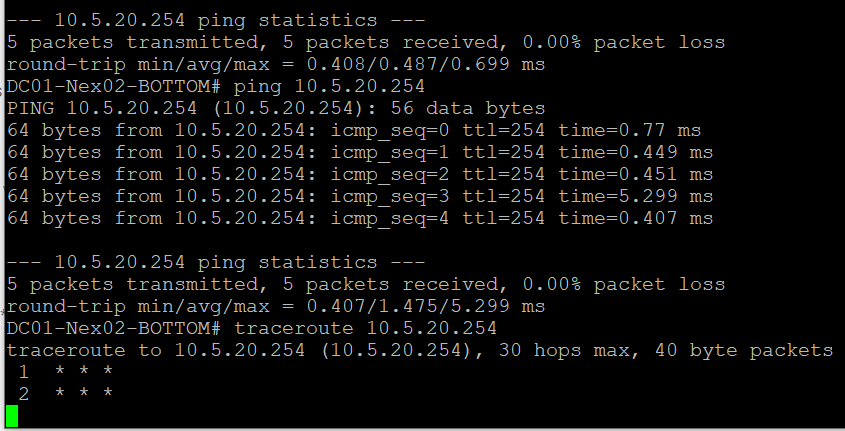
I resolved the internet bouncing issue. But I still cannot traceroute. No static routes exist on the firewall, I was thinking they are directly connected to the LAN? No need?
1. is your ping from 10.5.20.249 to 10.5.20.254 ok ? both sides ? YES both sides ping
2. PC can ping 10.5.20.2 249 ? without packet Loss? YES, using SSH into Nexus
3. PC can ping 10.5.20.2 250 ? without packet Loss ? YES, using SSH into Nexus
Traceroute from PC to 20.254 seemed to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 11:09 AM
if the VLAN Stretched all over until FW, sure it should work. (with that output i am guessing)
Still, the basic question remains the same - what is the PC IP address, post from PC ipconfig /all to view.
But I still cannot traceroute. - what traceroute not working post the example output to understand better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 11:16 AM
I also showed you can ping the 20.254.
Maybe doesn't matter, since the devices connected (Nutanix) are reporting DHCP addresses from the firewall.
IP of PC is 10.5.20.4, with a default gateway of 10.5.20.254 - And I have the PC plugged into the Nexus. So means it is transversing through the C9300 to fortigate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 12:45 PM
Ok only Traceroute not working, but the rest of the Service is ok?
If you leave the traceroute what happens until the 30th Hop. same traceroute if you do from Fortinet console what is the results.
The issue not really related to cisco product - this could be your provider not allowing or you need to look Fortinet point of view :
https://www.fortinetguru.com/2017/01/how-to-run-ping-and-traceroute/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2020 11:54 AM - edited 12-18-2020 01:43 PM
Hello,
you are trying to traceroute to the Fortigate ? As far as I recall, "the FortiGate is designed not to allow UDP packets in the local-in policy. UDP packets destined for the interface of the FortiGate are dropped when a standard UDP-based traceroute is performed."
Check the local policy for the Fortigate interface you are trying to traceroute to. Since ping is working, I have a feeling that this might be the problem...
Check the 'set allowaccess' settings for your Vlan interface, it should look like this:
set ip 10.5.20.254 255.255.255.0
set allowaccess ping https ssh snmp http telnet
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide