- Cisco Community
- Technology and Support
- Networking
- Switching
- Can't access the internet from a guest wireless VLAN on a SG300
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 01:08 AM - edited 03-08-2019 04:19 PM
I need a little assistance with this issue please.
I have a SG300-10. (10.7.0.32) I have 3 VLANS setup.
1 - LAN
20 - Guest WIFI
30 - Servers
On port 7 of the switch is a Ruckus WIFI AP. It has two SSID's one for private WIFI VLAN 1 and another for guest WIFI VLAN 20.
PORT 3 has a server attached and it is untagged on VLAN 30.
Port 10 has a Cyberoam switch with three static routes setup to forward back to the switch:
with the following VLANS: 1Untagged, 20 Tagged, 30 Tagged.
10.8.0.0 / 255.255.255.0 10.7.0.32
10.9.0.0 / 255.255.255.0 10.7.0.32
10.77.0.0 / 255.255.255.0 10.7.0.32
VLAN30 works well and all of the routing between VLANS is fine. The servers can get access to the internet without issue.
The private WIFI works well.
The Guest wifi allows access to the VLAN1 and 30 via the switch no problem. It will not forward packets to the router however. Despite the default route being in place. I have setup NAT for the Guest WIFI on the router but the packets never make it there from the switch so that is not the issue.
I'm pretty sure this is not an ACL issue as I've specified a permit any to any scenario and still the same issue.
If someone could please provide some assistance as to where to troubleshoot from here it would be really appreciated.
Switch config below:
config-file-header
switch5e8af7
v1.4.9.4 / R800_NIK_1_4_205_011
CLI v1.0
set system mode router
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
time-range Allways
time-range DaytimeWifi
absolute start 22:00 16 nov 2016
absolute end 04:58 17 nov 2069
periodic mon 04:58 to mon 22:30
periodic tue 04:58 to tue 22:30
periodic wed 04:58 to wed 22:30
periodic thu 04:58 to thu 22:30
periodic fri 04:58 to fri 22:30
periodic sat 04:58 to sat 22:30
periodic sun 04:58 to sun 22:30
exit
vlan database
vlan 10,20,30
exit
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
ip dhcp relay address 10.7.0.18
ip dhcp relay enable
ip dhcp information option
bonjour interface range vlan 1
ip access-list extended "Allow Guest out"
permit ip any any ace-priority 1
exit
ip access-list extended Firewall
permit ip any 10.9.0.0 255.255.255.0 ace-priority 1
exit
hostname switch5e8af7
username ** password encrypted *** privilege 15
ip ssh server
no ip http server
ip http secure-server
clock timezone *** +10
clock summer-time web recurring first sun dec 03:00 first sun jul 03:00
clock source sntp
sntp unicast client enable
sntp unicast client poll
sntp server 132.163.96.1 poll
ip name-server 8.8.8.8
!
interface vlan 1
ip address 10.7.0.32 255.255.255.0
no ip address dhcp
service-acl input Firewall default-action permit-any
!
interface vlan 10
name Test
ip address 10.8.0.32 255.255.255.0
!
interface vlan 20
name Test
ip address 10.9.0.32 255.255.255.0
ip dhcp relay enable
service-acl input "Allow Guest out" default-action permit-any
!
interface vlan 30
name Servers
ip address 10.77.0.32 255.255.255.0
!
interface gigabitethernet1
description Test
!
interface gigabitethernet2
description Unused
power inline never
!
interface gigabitethernet3
description "Test"
switchport trunk native vlan 30
!
interface gigabitethernet4
description Test
switchport trunk native vlan 30
!
interface gigabitethernet5
description Test
switchport trunk native vlan 30
!
interface gigabitethernet6
description Test
!
interface gigabitethernet7
description WIFI
switchport trunk allowed vlan add 20
!
interface gigabitethernet8
description "Test"
!
interface gigabitethernet9
description Test
!
interface gigabitethernet10
description "Router UplinkPort"
switchport trunk allowed vlan add 20,30
!
exit
ip default-gateway 10.7.0.1
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 02:43 AM
Ok got it sorted. I just disabled client isolation on the SSID and it started working. Go figure...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 01:29 AM
Hello,
post a schematic drawing of your topology so that we can tell what is connected to what...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 02:15 AM
--> On port 7 of the switch is a Ruckus WIFI AP. It has two SSID's one for private WIFI VLAN 1 and another for guest WIFI VLAN 20.
Is that port 7 of the SG switch ?
--> Port 10 has a Cyberoam switch with three static routes setup to forward back to the switch:
That is why I was asking for a drawing of your topology. The Cyberoam is connected to the SG switch on port 10 ? What are the static routes for if the VLANs are configured on the SG ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 03:41 AM
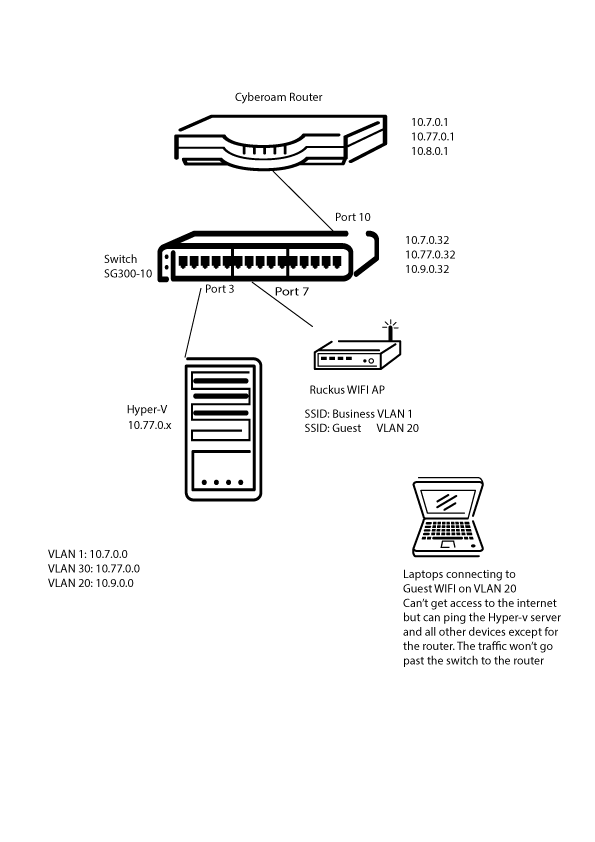
Thanks Georg, Yes of course here is the schematic:
Port tagging on the switch:
GE1 Trunk 1UP
GE2 Trunk 1UP
GE3 Trunk 30UP
GE4 Trunk 30UP
GE5 Trunk 30UP
GE6 Trunk 1UP
GE7 Trunk 1UP, 20T
GE8 Trunk 1UP
GE9 Trunk 1UP
GE10 Trunk 1UP, 20T, 30T
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 07:09 AM
Hello
on the switch looks like it running as a host switch so instead of using ip default- gateway enable io routing and specifiy a default route
ip routing
ip route 0.0.0.0 0.0.0.0. x.x.x.x
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 12:39 PM
I have tried "ip route" on the SG300 switch but it is not a recognised command.
I beleive the equivilent commands are these:
set system mode router
ip default-gateway 10.7.0.1
both have been entered.
Is there something else I have overlooked?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 01:38 PM
Hello
does the cyberroam rtr have a route back to vlan 20?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 01:46 PM
Yep it does!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 12:29 AM
Hello
okay then
Can a WiFi client ping-
-all the other vlans clients
- the cyberroam routers gateway
- is nat being performed from WiFi clients
- have you tested Without any acls applied
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 12:40 AM
Hi Paul,
Yes the WIFI client can ping other vlan clients on the same and other vlans. Yes NAT is being performed. Yes I have tried without ACLs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 01:26 AM
Hello,
try and configure port 7 on the SG300 as a Wireless Access Point Smartport. I am not sure if that makes a difference.
Try and configure port 10 as a layer 3 port with a DHCP assigned address. That will automatically create a default route from the SG300 to the Cyberoam...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 02:43 AM
Ok got it sorted. I just disabled client isolation on the SSID and it started working. Go figure...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 03:10 AM
Hello
glad you got it sorted -I am assuming this feature was to segregate the other vlans from your guest users? - would suggest now amend your acls to deny this communication as you dot want guest users being able to access your lan users
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 03:23 AM
Thanks for your suggestions Paul. It's appreciated. Yes I went ahead and setup the ACL's. It's actually working great now thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2018 04:55 AM
Just out of curiosity, where was the client isolation configured, on the Ruckus ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide