- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 08:09 AM - edited 03-08-2019 09:00 AM
Hello all good people,
Just preparing to my CCNA, an decided to prepare some easy network at my home. I was able to configure everything as i wish to have. I face one issue (seems to be easy to solve) but not for me somehow. Take a look on the network i did. Issue is i can't ping ISP router from S2 switch and of course then from all my regular hosts, do i need some additional configuration? P.S R1 and S1 can do a ping.
One of possibility i had was maybe some route has to be done on R1 but from my point of view there shouldn't be as on R1 192.168.59.254 is one of his interface and 192.168.0.254 is on second interface so R1 should now how to trace packet to ISP.
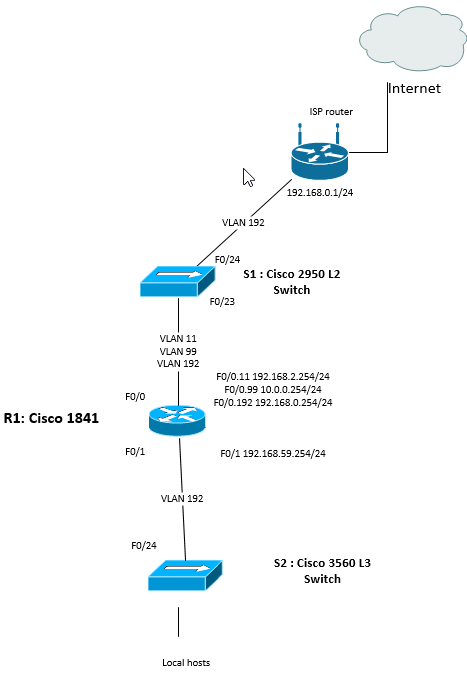
My configuration:
ISP router (from provider):
IP: 192.168.0.1 /24
R1: (1841)
Robert#show running-config
Building configuration...
Current configuration : 929 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Robert
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip cef
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.11
encapsulation dot1Q 11
ip address 192.168.2.254 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0/0.99
encapsulation dot1Q 99 native
ip address 10.0.0.254 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0/0.192
encapsulation dot1Q 192
ip address 192.168.0.254 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0/1
ip address 192.168.59.254 255.255.255.0
duplex auto
speed auto
!
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
scheduler allocate 20000 1000
end
Robert#
S1: (2950):
2950#show running-config
Building configuration...
Current configuration : 1431 bytes
!
version 12.1
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname 2950
!
!
ip subnet-zero
!
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
!
!
!
interface FastEthernet0/1
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
switchport trunk native vlan 99
switchport mode trunk
!
interface FastEthernet0/24
switchport access vlan 192
switchport mode access
!
interface FastEthernet0/25
!
interface FastEthernet0/26
!
interface Vlan1
no ip address
no ip route-cache
shutdown
!
interface Vlan99
ip address 10.0.0.253 255.255.255.0
no ip route-cache
!
interface Vlan192
no ip address
no ip route-cache
shutdown
!
ip default-gateway 10.0.0.254
ip http server
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
!
end
2950#
S2: (3560)
Switch#show running-config
Building configuration...
Current configuration : 3167 bytes
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
system mtu routing 1500
ip subnet-zero
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface FastEthernet0/1
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
!
interface FastEthernet0/24
switchport access vlan 192
switchport mode access
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
no ip address
shutdown
!
interface Vlan100
ip address 192.168.22.11 255.255.255.0
ip directed-broadcast
!
interface Vlan192
ip address 192.168.59.253 255.255.255.0
!
ip default-gateway 192.168.59.254
ip classless
ip http server
ip http secure-server
!
!
!
control-plane
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
Switch#
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 11:04 AM
Hi
I maybe missunderstand your concern.
On the ISP, the IP 192.168.0.1/24 is your inside interface right? Why are you saying it's given by ISP?
Normally you should have another interface facing your ISP with another IP (public IP, but in lab it could be whatever).
From R1 vlan 192, are you able to ping 192.168.0.1?
On you Switch L3 (S2), you need to configure a default route:
ip route 0.0.0.0 0.0.0.0 192.168.59.254
You're using vlan 192 for 2 different subnets. In your environment it doesn't matter that there is a Layer 3 interface breaking the dot1q vlan span but I should recommend to change it in case you want to expand your lab and don't want to face issues...
On your R1, you're also missing a default route pointing to your ISP router for all unknown subnets on Internet.
The route should be:
ip route 0.0.0.0 0.0.0.0 192.168.0.1
When you've corrected that routes, from Local hosts, you should be able to ping your inside ISP router IP (192.168.0.1). To go outside to Internet, the ISP router will handle that task by having a default route and natting your internal IP.
Let me know if this is ok and if I understand good your concerns.
Thanks
PS: Please don't forget to rate and mark as correct answer if this answered your question.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 11:04 AM
Hi
I maybe missunderstand your concern.
On the ISP, the IP 192.168.0.1/24 is your inside interface right? Why are you saying it's given by ISP?
Normally you should have another interface facing your ISP with another IP (public IP, but in lab it could be whatever).
From R1 vlan 192, are you able to ping 192.168.0.1?
On you Switch L3 (S2), you need to configure a default route:
ip route 0.0.0.0 0.0.0.0 192.168.59.254
You're using vlan 192 for 2 different subnets. In your environment it doesn't matter that there is a Layer 3 interface breaking the dot1q vlan span but I should recommend to change it in case you want to expand your lab and don't want to face issues...
On your R1, you're also missing a default route pointing to your ISP router for all unknown subnets on Internet.
The route should be:
ip route 0.0.0.0 0.0.0.0 192.168.0.1
When you've corrected that routes, from Local hosts, you should be able to ping your inside ISP router IP (192.168.0.1). To go outside to Internet, the ISP router will handle that task by having a default route and natting your internal IP.
Let me know if this is ok and if I understand good your concerns.
Thanks
PS: Please don't forget to rate and mark as correct answer if this answered your question.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 11:19 AM
I will do that ASAP but here's questions:
ISP - sorry its internal right - mistake :)
R1 can ping ISP so trunk working correctly
1) Why should i make any additional routes (default routes). For instance for R1 - subnet 192.168.59.254 is on one of it's interface as well as all 3 subnets so from my understanding if S2 sending something to R1 on 192.168.59.254 R1 should find 192.168.0.254 without any additional route. If that's not correct explain why not.
2) Even if i implement those default routes will it work also that ISP router would ping for instance S2 or do i need also additional routes in that way towards S2 on R1? If yes that;s also concenrs me as R1 knows all it's interfaces so should redirect to correct subnet when ISP router sends packet to R1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 12:29 PM
You'll need default route on R1 to send traffic over ISP routers for all unknown subnets (like 8.8.8.8 or other public IP). Without that default route, R1 will be able to ping all local 3 subnets and that's it.
Same thing for S2.
For ISP router, you'll need to add a route for all internal traffic. Let's assume that all subnets within your LAN are included into a global 192.168.0.0/16, then you'll need a route like:
ip route 192.168.0.0 255.255.0.0 192.168.0.254
Does that make sense for you? Is it understandable?
Thanks
PS: Please don't forget to rate and mark as correct answer if this answered your question.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 03:00 PM
Hi, to be honest not :(
Maybe let me make one change as you mentioned and as i understood to have only one subnet in one particurall vlan am i right? Correct me if i am wrong.
Instead on switch S2 to have vlan 192 on F0/24 i did make a change to make VLAN 1 there. But now i cant even ping R1 f0/1 (192.168.59.254). What to do know to correct that? Or how would you configure that another vlan or? I am planning connect user to that S2 switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 03:04 PM
Ok Let me clarify.
On S2 (Switch), it is setup as L3 and I assume that you have activated IP routing?
If IP routing is activated then you need IP ROUTE command. If not activated, then IP default-gateway is OK.
Then the command ip route is needed to reach out subnets that aren't locally configured.
Now for R1. Sur the subnet to reach ISP inside interface is configured. However if you initiate a communication to Google DNS (8.8.8.8), the router needs to know where to forward that packet and for that purpose it will looks into its RIB (routing table). If you have setup a default route to ISP router (as I told you before) then the packet will be forwarded and you will have access to internet otherwise it won't work.
Now on ISP router. If a packet arrives and need to reach 192.168.59.0/24 subnet, it needs to know that the packet has to be forwarded to R1 that knows this network otherwise it won't work.
Hope this more clear.
Thanks
PS: Please don't forget to rate and mark as correct answer if this answered your question
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 05:03 AM
Let me create new topci to not be this too long. I will make some changes and ask again. Thanks !
Hi supportlan,
Thanks for all your contribution here. I mark all you answers and rate. If you could support me bit more.
1) From what you said is it's good approach to have only one subnet belong to specific vlan is that right?
2) I would like to change my network a bit according to 1) -if answer is yes and deleted vlan 192 between R1 and S2 - what can you suggest to be there? Just VLAN 1 or new vlan?
Please let me know i will change and we can talk further according to that change.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 07:04 AM
Hi
You can keep the same vlan, it's just a matter of best practices.
You can use whatever vlan you want.
Don't use vlan 1.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 12:45 AM
Hello,
'supportlan' is absolutely correct. You need to add routing on your ISP router. To see the results, try:
ISP(config)#ip route 192.168.59.0 255.255.255.0 FastEthernet 0/0
Once you have added this route, you can ping the switch, and the switch can ping the ISP router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2017 03:03 PM
Hello,
I think your problem is related to a wrong IP addressing scheme:
Switch
interface Vlan192
ip address 192.168.59.253 255.255.255.0
Router
interface FastEthernet0/0.192
encapsulation dot1Q 192
ip address 192.168.0.254 255.255.255.0
no snmp trap link-status
The IP addresses belong to different address spaces, but you have configured them for the same Vlan...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

