- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Catalyst 3750G using ACL?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 07:38 PM
Hello I was wondering if I am needing an ACL on my 3750G even though it is configured in vlan L2.
My issue is that from my Windows PC I can ping, from 192.168.1.6, the 10.0.1.1 Router, the 10.0.2.1 Router AND the NAS on 10.0.2.111 and get a reply but when I try to map the drive, it does not map and errors out as if it does not exist.
I can connect to the GUI for the 10.0.1.1 and the 10.0.2.1 Routers but again can not map the 10.0.2.111, and can ping it.
It is utilizing SMB2 which I believe uses Port 445 and SMB1 using Port 139, but I am only using 445.
What is weird is I can access other aspects of either network on their ports so I am at a loss. When I connect to a 10.0.2.0 or 10.0.1.0 network I can map the NAS in the same manor and it works just fine. I mention this because I do not believe it is any configuration on the NAS as it works on every other network.
I have verified that my PC is getting its routes to the 10.0.1.0 and the 10.0.2.0 through the 3750G and not the ASA-5508 that it is connected to.
Here is my running-config;
Current configuration : 4818 bytes
!
! Last configuration change at 03:46:47 UTC Tue Mar 2 1993
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
username Cisco privilege 15 password 0 Cisco123
no aaa new-model
switch 1 provision ws-c3750g-24ps
system mtu routing 1500
ip routing
!
!
!
!
crypto pki trustpoint TP-self-signed-29955072
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-29955072
revocation-check none
rsakeypair TP-self-signed-29955072
!
!
crypto pki certificate chain TP-self-signed-29955072
certificate self-signed 01
3082023A 308201A3 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
2F312D30 2B060355 04031324 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32393935 35303732 301E170D 39333033 30313030 30323334
5A170D32 30303130 31303030 3030305A 302F312D 302B0603 55040313 24494F53
2D53656C 662D5369 676E6564 2D436572 74696669 63617465 2D323939 35353037
3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 81008C88
CF06F23D 7A03F34C CD677D99 3CB4F6C4 32979254 6941E31B E0B8131D EDDD68A2
A5DEE51B CA5403B3 A11068F7 1C8475E2 AF8151C9 F7F68564 1DE41DFD 8D698C60
8937E5E8 9369F3E5 4BCEC188 91BB8B17 47B1A5B9 9807CDC2 535DB70A 953FDC26
CFDF8B35 9907E9AA 5E0ED6A0 56B27834 B29E836B 90413F72 3FF5F0FF 13B70203
010001A3 66306430 0F060355 1D130101 FF040530 030101FF 30110603 551D1104
0A300882 06537769 74636830 1F060355 1D230418 30168014 6AF085C3 A45F54E4
06E468C0 8062FA83 6D3DF995 301D0603 551D0E04 1604146A F085C3A4 5F54E406
E468C080 62FA836D 3DF99530 0D06092A 864886F7 0D010104 05000381 81004022
F5666C61 1EB181EB 6B8D24C8 70164803 28FC6FED 9D4CC778 4EBA567E 71B8ED32
9E28DE70 1FA3F6A6 C9506462 72C9D5EE 2787244C 5173980D 97C40D80 3793819C
A96AADAC C97764CA 709BAA37 B4513392 A09E21EF D59DA1CA D508C14A 1CA0B0EF
7CF7D5A4 D5AEC645 EBB905EA 3871D583 6697950F D24CEAC1 543D7116 4AF3
quit
!
!
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet1/0/1
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/2
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/3
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/4
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/5
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/6
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/7
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/8
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/9
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/10
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/11
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/12
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/13
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/14
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/15
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/16
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/17
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/18
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/19
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/20
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/21
description TPLink
switchport access vlan 12
switchport mode access
!
interface GigabitEthernet1/0/22
description VPN
switchport access vlan 13
switchport mode access
!
interface GigabitEthernet1/0/23
switchport mode access
!
interface GigabitEthernet1/0/24
switchport mode access
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface Vlan1
description ASA
ip address 192.168.1.5 255.255.255.0
!
interface Vlan10
description Home Lan
no ip address
!
interface Vlan11
description Home VPN
no ip address
!
interface Vlan12
description TPLink
ip address 10.0.1.161 255.255.255.0
!
interface Vlan13
description VPN
ip address 10.0.2.124 255.255.255.0
!
ip http server
ip http authentication local
ip http secure-server
!
!
logging esm config
no cdp run
!
!
line con 0
line vty 0 4
no login
line vty 5 15
no login
!
end
Solved! Go to Solution.
- Labels:
-
ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 11:24 AM
Also, correct me if I am wrong but is this the correct "router-on-a-stick" configuration using a Catalyst 3750G and an ASA-5508-X or is it backwards?
Router:
interface gigabitethernet 1/8
duplex full
no shutdown
interface gigbitethernet 1/8.1
description 10.0.1.0 vlan
encapsulation dot1q VLAN 10
ip address 10.0.1.105
interface gigabitethernet 1/8.2
description 10.0.2.0 vlan
encapsulation dot1q VLAN 20
ip address 10.0.2.105
Switch:
interface gigabitethernet 1/0/1
switchport mode trunk
switchport trunk encapsulation dot1q
vlan 10
name 10.0.1.0 vlan
vlan 20
name 10.0.2.0 vlan
interface gigabitethernet 1/0/2
switcphort mode access
switchport access vlan 10
interface gigabitether 1/0/3
switchport mode access
switchport access vlan 20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 12:06 PM
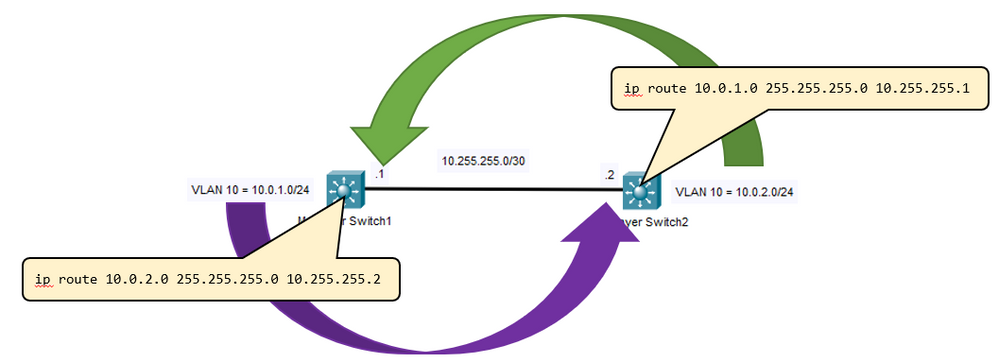
I'm not entirely clear on what you're asking so I'll say this. If there is another routing device (ASA, L3 Switch, or router) that has a network that is not directly attached to this other L3 switch, you will need to add a route to let the device know how to reach that network. For example (see graphic): If a device attached to VLAN 10 on SW1 (left) need to reach a network that is not also on 10.0.1.0/24, they will send their traffic to their default gateway which will be the VLAN 10 interface of SW1. SW1 will then look at the destination of the packet and check it's routing table. If it does not have a route then it will discard the packet. If we program SW1 with a route to say "to reach the 10.0.1.0/24 network, go to SW2", the switch will forward that traffic to SW2. SW2 then looks at the packet and realizes that it "owns" that network and forwards the traffic to the appropriate computer on that VLAN. Return traffic follows the same logic in the reverse order which means that SW2 also needs to know where to forward traffic destined for 10.0.2.0/24 so we have to add a static route there as well.
Does this answer your question?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 01:04 PM
Yes this diagram and description does indeed make sense as far as how the IP Routing works.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide