- Cisco Community
- Technology and Support
- Networking
- Switching
- Catalyst 3750G using ACL?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 07:38 PM
Hello I was wondering if I am needing an ACL on my 3750G even though it is configured in vlan L2.
My issue is that from my Windows PC I can ping, from 192.168.1.6, the 10.0.1.1 Router, the 10.0.2.1 Router AND the NAS on 10.0.2.111 and get a reply but when I try to map the drive, it does not map and errors out as if it does not exist.
I can connect to the GUI for the 10.0.1.1 and the 10.0.2.1 Routers but again can not map the 10.0.2.111, and can ping it.
It is utilizing SMB2 which I believe uses Port 445 and SMB1 using Port 139, but I am only using 445.
What is weird is I can access other aspects of either network on their ports so I am at a loss. When I connect to a 10.0.2.0 or 10.0.1.0 network I can map the NAS in the same manor and it works just fine. I mention this because I do not believe it is any configuration on the NAS as it works on every other network.
I have verified that my PC is getting its routes to the 10.0.1.0 and the 10.0.2.0 through the 3750G and not the ASA-5508 that it is connected to.
Here is my running-config;
Current configuration : 4818 bytes
!
! Last configuration change at 03:46:47 UTC Tue Mar 2 1993
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
username Cisco privilege 15 password 0 Cisco123
no aaa new-model
switch 1 provision ws-c3750g-24ps
system mtu routing 1500
ip routing
!
!
!
!
crypto pki trustpoint TP-self-signed-29955072
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-29955072
revocation-check none
rsakeypair TP-self-signed-29955072
!
!
crypto pki certificate chain TP-self-signed-29955072
certificate self-signed 01
3082023A 308201A3 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
2F312D30 2B060355 04031324 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32393935 35303732 301E170D 39333033 30313030 30323334
5A170D32 30303130 31303030 3030305A 302F312D 302B0603 55040313 24494F53
2D53656C 662D5369 676E6564 2D436572 74696669 63617465 2D323939 35353037
3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 81008C88
CF06F23D 7A03F34C CD677D99 3CB4F6C4 32979254 6941E31B E0B8131D EDDD68A2
A5DEE51B CA5403B3 A11068F7 1C8475E2 AF8151C9 F7F68564 1DE41DFD 8D698C60
8937E5E8 9369F3E5 4BCEC188 91BB8B17 47B1A5B9 9807CDC2 535DB70A 953FDC26
CFDF8B35 9907E9AA 5E0ED6A0 56B27834 B29E836B 90413F72 3FF5F0FF 13B70203
010001A3 66306430 0F060355 1D130101 FF040530 030101FF 30110603 551D1104
0A300882 06537769 74636830 1F060355 1D230418 30168014 6AF085C3 A45F54E4
06E468C0 8062FA83 6D3DF995 301D0603 551D0E04 1604146A F085C3A4 5F54E406
E468C080 62FA836D 3DF99530 0D06092A 864886F7 0D010104 05000381 81004022
F5666C61 1EB181EB 6B8D24C8 70164803 28FC6FED 9D4CC778 4EBA567E 71B8ED32
9E28DE70 1FA3F6A6 C9506462 72C9D5EE 2787244C 5173980D 97C40D80 3793819C
A96AADAC C97764CA 709BAA37 B4513392 A09E21EF D59DA1CA D508C14A 1CA0B0EF
7CF7D5A4 D5AEC645 EBB905EA 3871D583 6697950F D24CEAC1 543D7116 4AF3
quit
!
!
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet1/0/1
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/2
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/3
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/4
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/5
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/6
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/7
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/8
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/9
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/10
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/11
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/12
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/13
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/14
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/15
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/16
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/17
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/18
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/19
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/20
switchport access vlan 11
switchport mode access
!
interface GigabitEthernet1/0/21
description TPLink
switchport access vlan 12
switchport mode access
!
interface GigabitEthernet1/0/22
description VPN
switchport access vlan 13
switchport mode access
!
interface GigabitEthernet1/0/23
switchport mode access
!
interface GigabitEthernet1/0/24
switchport mode access
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface Vlan1
description ASA
ip address 192.168.1.5 255.255.255.0
!
interface Vlan10
description Home Lan
no ip address
!
interface Vlan11
description Home VPN
no ip address
!
interface Vlan12
description TPLink
ip address 10.0.1.161 255.255.255.0
!
interface Vlan13
description VPN
ip address 10.0.2.124 255.255.255.0
!
ip http server
ip http authentication local
ip http secure-server
!
!
logging esm config
no cdp run
!
!
line con 0
line vty 0 4
no login
line vty 5 15
no login
!
end
Solved! Go to Solution.
- Labels:
-
ACI
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 12:06 PM
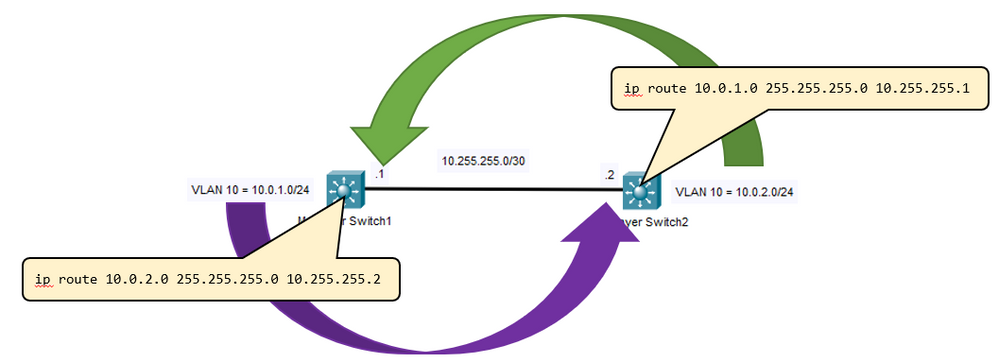
I'm not entirely clear on what you're asking so I'll say this. If there is another routing device (ASA, L3 Switch, or router) that has a network that is not directly attached to this other L3 switch, you will need to add a route to let the device know how to reach that network. For example (see graphic): If a device attached to VLAN 10 on SW1 (left) need to reach a network that is not also on 10.0.1.0/24, they will send their traffic to their default gateway which will be the VLAN 10 interface of SW1. SW1 will then look at the destination of the packet and check it's routing table. If it does not have a route then it will discard the packet. If we program SW1 with a route to say "to reach the 10.0.1.0/24 network, go to SW2", the switch will forward that traffic to SW2. SW2 then looks at the packet and realizes that it "owns" that network and forwards the traffic to the appropriate computer on that VLAN. Return traffic follows the same logic in the reverse order which means that SW2 also needs to know where to forward traffic destined for 10.0.2.0/24 so we have to add a static route there as well.
Does this answer your question?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 09:12 PM
What is the configured default gateway for the 192.168.1.6 computer?
What is the configured default gateway for the NAS? I'm assuming it is 10.0.2.124
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 08:13 AM
When I get home will verify all that and let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 02:11 AM
Hello
If your switch is suppose to be running as a host switch why does it have mutlple SVI appended to it, those SVI interfaces should reside on the L3 device servcing your LAN?
Remove ths SVIs off that switch, append them to the L3 device, Make sure you dont have any software Fw on the PC negating file-sharing, check you nic settings, and if you trying to map a drive via FQDN then make sure you have dns has A records for that particualr host
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 08:15 AM
Honestly at this point I really do not have any answer,. I was trying to many things in order to get vlan 10 and vlan 11 to talk that I created 12 and 13 with vlan IP's to communicate but I am learning now that with IP ROUTING and a valid ip route that would be accomplished regardless. I will revert my switch back to 1-10 being vlan10 L2 and 11-20 being vlan11 L2 and append correct routes and hopefully they will communicate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 09:59 AM
Also when you say "Remove the SVIs off that switch, append them to the L3 device" you mean simply leave the Catalyst in L2 configuration and leave the routers that host the 10.0.1.0, 10.0.2.0 and 192.168.1.0 do the L3 Routing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 10:08 AM - edited 02-01-2021 10:08 AM
Hello
yes i do mean that - that switch should only be running as a host deviice with a trunk interconnect to another upstream switch or L3 device
The only svi required on that switch would be for remote mgt of the switch itself a default-gateway and that’s iit with ip routing disabled
It will require the vlans included into its vtp database of what you want adding to the access ports
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 10:56 AM
Whew this is getting deeper. I do understand the trunk and it's configuration but I am confused as to why i would need a trunk in this scenario. 192.168.1.0 is coming from the ASA to the Switch vlan1. 10.0.1.0 is coming to the switch vlan10 and 10.0.2.0 is coming vlan11.
The only reason I even need the ASA/192.168.1.0 is so that from outside on my VPN I can access the 10.0.1.0/10.0.2.0.
Just not sure what I would be trunking..2.0 is 1 vlan in itself and 1.0 is one vlan on their own devices.
Or is that not how this works.
no ip routing
switchport mode access
switcport mode vlan <#>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 11:26 AM
I just assumed that you wanted to route on the switch which is why I saw the "ip routing" command in your running config along with all the SVI's with configured IP addresses. If you want to turn this Layer 3 switch into a Layer 2 switch, you could route between the VLANs using a "router-on-a-stick" topology. This requires the VLANs to be extended to the ASA in the form of a trunk. When a computer on a VLAN communicates with a computer on another VLAN, it will send traffic to it's default gateway (the ASA's sub-interface for that VLAN) to which the ASA will route the packet to the correct VLAN and send it out the same interface but this time with a VLAN tag appropriate for the destination VLAN that the other computer resides in. Return traffic will follow the same logic & path.
If you keep the topology the way that it was yesterday, devices will use the Layer 3 switch's SVI IP address as their default gateway and the only time that the Layer 3 switch will send traffic to the ASA is if you are either communicating with the ASA directly or you have a default gateway destined for the ASA to allow for Internet-bound traffic.
This confusion as to where the routing is occurring is likely the source cause of all your headaches on this project. The next steps really come down to if you want to route at the Layer 3 switch or the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 11:39 AM
Ah so this would essentially be 3 interfaces in use... 10.0.1.0 going to its router. 10.0.2.0 going to its router and then 1 going back to the ASA as a trunk line combining both subnets on the Switch for routing.
I will just have to eliminate the 192.168.1.0 and use it as the trunk port to the ASA instead of an access interface independently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 06:30 PM
I will be configuring the setup for the ASA to be doing the routing but is there a right/wrong in choosing the ASA over the L3 Switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:07 AM
There are advantages and disadvantages to both. Below is a non-exhaustive list:
---Using the ASA for Routing---
Advantage: If you are doing any kind of traffic inspection/filtering on the ASA, it will be able to inspect/filter traffic on all VLANs
Disadvantage: 1) Because the traffic has to hairpin through a single interface, it can quickly become a bottleneck if there is significant inter-VLAN routing occurring on the network. 2) Does not scale well as the organization grows because all VLANs have to be routed at the ASA
---Using the Layer 3 switch for Routing---
Advantage: Faster speeds of routing since it is not hendered by the issue listed above in the "router-on-a-stick" topology
Disadvantage: The ASA will only inspect traffic that is Internet-bound. Inter-VLAN traffic will not be inspected.
It's really up to you on how you want to build your network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:50 AM
Those are all very valid and helpful examples. Based on what you mentioned I feel the L3 Configuration would be best. Mainly because there is no Internet Access between vlans but simply access from one network to another internally so I do not think that I would need any sort of inspection. I assume the internet based on the vlan (as my vlan 12 and vlan 13 are set up) can not get Internet from each other vlan but their own network they initially connect to, or I hope. Another reason would be that 10.0.1.0 network would be streaming 60gig 4k video files so less amount of bottleneck the better.
Regardless of how I am keeping my Catalyst I do have 2 spare routers and 2 spare switches for mock networking and will configure using the Router-on-a-stick approach for the experience.
With that said it turns out that my initial problem of being able to ping but not access the NAS turned out to be that one Windows 10 PC. After hours of researching my Windows 10 had automatically disabled SMB2 access so I had to reactivate it and all worked as it should with my initial posting configuration.
Along with that, and I blame the idea of modifying a configuration opposed to starting fresh, I was NOT successful in implementing the router-on-a-stick configuration on the Catalyst and more specifically the ASA-5508-X as a lot of the commands were not the same as the examples I had looked up. So I reverted back to my configuration, which works, for now.
My question inquiry is this.
As we can see in my running-config I have GE 1-10 as a L2 vlan10 for 10.0.1.0 and GE 11 - 20 as a L2 vlan11 for 10.0.2.0. This are simply extra capacity access points for more physical devices on each subnet, nothing to do with each other.
I have GE21 as vlan12 configured with an IP address and GE22 as vlan13 configured with an IP address and both are independent from the vlan 10&11 as these are being used for the "communication". With this I still found myself unable to cross communicate even with 'ip routing' enabled. I have set no static routes. So what I did was create GE22 using default vlan1 with 192.168.1.5 which comes from the DHCP Server on the [inside] ASA-5508-X and on the ASA I made an ip route;
inside 10.0.1.0 255.255.255.0 192.168.1.5
inside 10.0.2.0 255.255.255.0 192.168.1.5
And now it all works.. With this in mind I also have static routes on the 10.0.1.0 and 10.0.2.0 Routers.
My question is should I be able to intercommunicate the vlans ON the Catalyst and not have the 2 ip routes on the ASA? And also what is the difference between the vlan 12 and vlan 13 with IP Addresses and GE 21/GE22 switcport mode access/switchport access vlan <#> versus NO vlan 12 and vlan 13 and just making the GE21/22 'no switchport' and configuring it with the same IP address as the vlans were?
I always wondered the difference between using a vlan with an ip vs just configuring the interface with an ip. I assume it is so that the 'vlan" configuration will be part of the other same vlans whereas the Interface IP is just an interface with an IP.
A lot of this is thinking out loud but also hoping to find answers as I also read through my books.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 11:15 AM
"With this I still found myself unable to cross communicate even with 'ip routing' enabled."
I'm not sure if you mean that you could not communicate between VLAN 12 & 13 or you could not communicate between VLAN 12 and VLAN 11.
If you were to move all the routing to the switch, you would need:
1. Assign an IP address for every VLAN on the switch and that IP address should be the default gateway for all devices on that VLAN.
2. A default static route destined for the ASA so that you could reach the Internet
3. Static routes for all your internal networks on the ASA destined for the switch.
The difference between using an SVI vs a routed port: https://loopedback.com/2018/02/13/multi-layer-switching-svi-and-l3-routed-ports-fundamentals-configuration-and-verification-labbed/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 11:35 AM
In reference to your:
1. Assign an IP address for every VLAN on the switch and that IP address should be the default gateway for all devices on that VLAN.
Do you mean if on the Switch the vlan is 10.0.1.115 and a vlan 10.0.2.115 that on the 10.0.1.0 switch I would have a route like 10.0.2.0 255.255.255.0 10.0.1.115 ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide