- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Cisco WS-C2960CX-8PC-L wired dot1x problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2018 05:26 AM - edited 03-08-2019 03:37 PM
Hi.
We purchased WS-C2960CX-8PC-L switches and begin to deploy them in our infrastructure.
In our enterprise network we using dot1x with mab.
We have following IOS on WS-C2960CX-8PC-L:
Cisco IOS Software, C2960CX Software (C2960CX-UNIVERSALK9-M), Version 15.2(6)E1, RELEASE SOFTWARE (fc4)
Our dot1x settings are the following:
aaa new-model ! ! aaa group server radius net-auth server name dl-dc01 ! aaa authentication dot1x default group radius aaa authorization network default group radius <...> mab request format attribute 2 7 ################ <...> dot1x system-auth-control dot1x logging verbose <...> service-template default_dot1x_vlan vlan 40 <...> policy-map type control subscriber dot1x_policy event session-started match-all 10 class always do-all 10 authenticate using dot1x priority 10 20 authenticate using mab priority 20 event authentication-failure match-all 10 class always do-all 10 activate service-template default_dot1x_vlan <...> interface GigabitEthernet0/1 switchport mode access switchport voice vlan 100 access-session host-mode single-host access-session port-control auto mab dot1x pae authenticator dot1x timeout tx-period 5 dot1x max-reauth-req 3 spanning-tree portfast edge spanning-tree bpdufilter enable service-policy type control subscriber dot1x_policy <...>
When we connect PC to interface Gi 0/1 we always get PC into vlan 40.
But we see dot1x mab request on our radius server and also we see that our radius server respond with access-accept message (we using MS NPS as Radius server).
But in "debug radius" we see the following:
Jul 9 12:24:19.573: RADIUS/ENCODE(00000000):Orig. component type = Invalid Jul 9 12:24:19.573: RADIUS(00000000): Config NAS IP: 10.10.30.83 Jul 9 12:24:19.573: RADIUS(00000000): Config NAS IPv6: :: Jul 9 12:24:19.573: RADIUS(00000000): sending Jul 9 12:24:19.573: RADIUS: Message Authenticator encoded Jul 9 12:24:19.573: RADIUS(00000000): Send Access-Request to 10.10.49.10:1645 onvrf(0) id 1645/7, len 264 Jul 9 12:24:19.573: RADIUS: authenticator 95 BB 73 3C 38 18 B6 19 - 08 89 FF 11 64 47 73 B3 Jul 9 12:24:19.577: RADIUS: User-Name [1] 14 "847beb27d595" Jul 9 12:24:19.577: RADIUS: User-Password [2] 18 * Jul 9 12:24:19.577: RADIUS: Service-Type [6] 6 Call Check [10] Jul 9 12:24:19.577: RADIUS: Vendor, Cisco [26] 31 Jul 9 12:24:19.577: RADIUS: Cisco AVpair [1] 25 "service-type=Call Check" Jul 9 12:24:19.577: RADIUS: Framed-MTU [12] 6 1500 Jul 9 12:24:19.577: RADIUS: Called-Station-Id [30] 19 "00-45-1D-E8-26-01" Jul 9 12:24:19.577: RADIUS: Calling-Station-Id [31] 19 "84-7B-EB-27-D5-95" Jul 9 12:24:19.577: RADIUS: Message-Authenticato[80] 18 Jul 9 12:24:19.577: RADIUS: 41 20 9B 4F FB AB B6 C0 4F 82 D8 8B 2A 5C A9 F5 [ A OO*\] Jul 9 12:24:19.577: RADIUS: EAP-Key-Name [102] 2 * Jul 9 12:24:19.577: RADIUS: Vendor, Cisco [26] 49 Jul 9 12:24:19.577: RADIUS: Cisco AVpair [1] 43 "audit-session-id=0A0A1E53000000130017995E" Jul 9 12:24:19.577: RADIUS: Vendor, Cisco [26] 18 Jul 9 12:24:19.577: RADIUS: Cisco AVpair [1] 12 "method=mab" Jul 9 12:24:19.577: RADIUS: Framed-IP-Address [8] 6 169.254.103.147 Jul 9 12:24:19.577: RADIUS: NAS-IP-Address [4] 6 10.10.30.83 Jul 9 12:24:19.577: RADIUS: NAS-Port-Id [87] 20 "GigabitEthernet0/1" Jul 9 12:24:19.577: RADIUS: NAS-Port-Type [61] 6 Ethernet [15] Jul 9 12:24:19.577: RADIUS: NAS-Port [5] 6 50101 Jul 9 12:24:19.577: RADIUS(00000000): Sending a IPv4 Radius Packet Jul 9 12:24:19.577: RADIUS(00000000): Started 5 sec timeout Jul 9 12:24:19.587: RADIUS: Received from id 1645/7 10.10.49.10:1645, Access-Accept, len 100 Jul 9 12:24:19.587: RADIUS: authenticator 46 9B DF 85 3C 16 8C 32 - 15 87 31 88 EC 7E 05 2B Jul 9 12:24:19.587: RADIUS: Vendor, Cisco [26] 6 Jul 9 12:24:19.587: RADIUS: Framed-Protocol [7] 6 PPP [1] Jul 9 12:24:19.587: RADIUS: Service-Type [6] 6 Framed [2] Jul 9 12:24:19.587: RADIUS: Tunnel-Medium-Type [65] 6 00:ALL_802 [6] Jul 9 12:24:19.587: RADIUS: Tunnel-Private-Group[81] 4 "15" Jul 9 12:24:19.587: RADIUS: Tunnel-Type [64] 6 00:VLAN [13] Jul 9 12:24:19.587: RADIUS: Class [25] 46 Jul 9 12:24:19.587: RADIUS: 97 16 09 F4 00 00 01 37 00 01 02 00 0A 0A 31 0A 00 00 00 00 15 D1 79 35 49 F2 51 B3 01 D3 F3 2E 41 C2 BD E3 00 00 00 00 00 04 89 71 [ 71y5IQ.Aq] Jul 9 12:24:19.587: RADIUS(00000000): Received from id 1645/7 Jul 9 12:24:19.587: RADIUS/DECODE: VSA external len != internal + VSA hdr Jul 9 12:24:19.587: RADIUS/DECODE: decoder; FAIL Jul 9 12:24:19.587: RADIUS/DECODE: attribute Vendor-Specific; FAIL Jul 9 12:24:19.587: RADIUS/DECODE: parse response op decode; FAIL
The same configuration of dot1x we successfully using on our 2960x, 3650.
How can we achieve normal vlan assignment by radius server?
Can somebody help with this situation?
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 12:26 AM
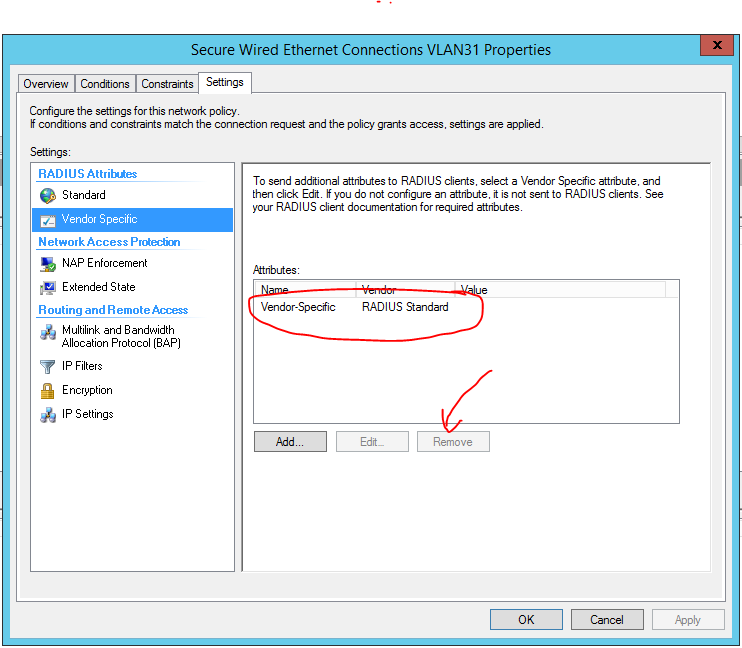
The problem was successfuly resolved.
We removed Vendor Specific attribute in NPS network policy settings on "Settings" Tab.
See screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 12:26 AM
The problem was successfuly resolved.
We removed Vendor Specific attribute in NPS network policy settings on "Settings" Tab.
See screenshot
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide