- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Do we need to set up ACL rules to deny for devices inside the comp
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Do we need to set up ACL rules to deny for devices inside the company?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 07:06 AM - edited 09-21-2023 07:16 AM
We have NetApp NAS storage inside the company, believe it is already protected by company's firewall which should already restrict all accesses attempted from outside.
Do I still need to create ACL rules to deny incoming packets from Internet, in addition to from within the company?
I am not a networking guy, if you can please explain to me in details.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 07:20 AM
I am not clear from your question exactly what you want the policy to be. It certainly seems that you want to prevent any access to the NAS from any external address. If you trust your firewall to prevent Internet access to the NAS then it is not a requirement to have an ACL to prevent Internet access. But you might want to have an ACL, as a backup to the firewall in case something does get through. And I am not clear what you want about access to NAS from inside resources. Are all inside devices to be allowed access to NAS? If so no ACL is required. But if some devices should not have access then an ACL would be needed.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 07:37 AM - edited 09-21-2023 07:49 AM
Yes, you kind of answered my questions. Thanks!
As for those accesses from inside resources, not all of them should be allowed to NAS. Now how to create ACL rules and to restrict the access from inside is the hard part. It is already on production and not protected well. Meanwhile, we don't want to restrict any legitimate accesses.
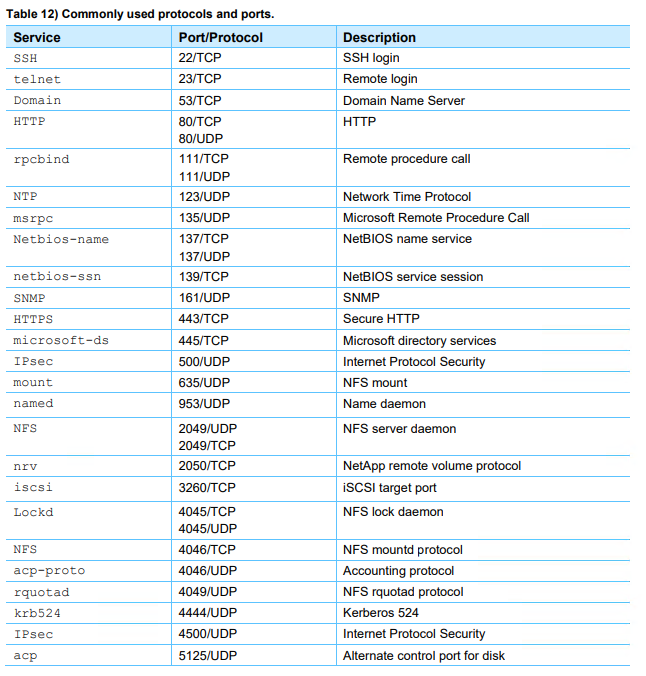
In general practice, should we just allow accesses based on the list of "commonly used protocol and ports" below, and also based on what are those networks/hosts our inside customer are located, and then at the bottom, deny everything else? Is this an good approach to start with? The list below (a portion of it) is provided by the NAS vendor.
Further, should we ask the networking team to provide us the list of all accesses (protocols, sources and destinations) from logs, and create ACL based on that? Is this a good approach also?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 07:55 AM
Configuring ACL to filter by protocol port is certainly an option. But it makes the configuration more complex and I wonder if it is needed. It seems to me that it would be sufficient to filter by IP address. Either you specify the device addresses/subnets etc that are permitted access and deny everything else. Or you specify device addresses/subnets etc that are to be denied and permit everything else. Your network team may have suggestions about which approach would be better.
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide