- Cisco Community
- Technology and Support
- Networking
- Switching
- Firewall to 2 core switches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 12:35 PM - edited 03-08-2019 02:28 PM
Hi Folks! Seems like my firs post here. So sorry if the question is quite stupid - I don't know much about firewall yet.
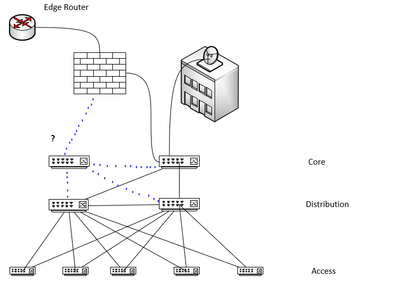
Could you point me to the right direction, please. Look at this picture and tell me, is it possible to add another core switch and have them wired to firewall so, that it could improve availability (fault tolerance) to the design? I know how it should be connected to another core switch and distributions switches, but do I connect to the firewall? Do I achieve load balancing in this case? Is firewall able to do this? If I cannot get load balancing, can I still have it as a spare one, which starts working as soon as the main core switch failed? Do I actually need this design at all? Thank you.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 12:48 PM
Hi,
This is not a stupid question at all, it's rather a good design question.
Yes, if you add a second core switch, you would need to add a second firewall for redundancy. You can configure the firewalls as active/standby, so when one firewall fails all traffic uses the other firewall. With most vendors' firewall, you can cluster them together and one firewall will be primary and the other on standby to take over traffic forwarding as soon as something happens to the primary.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 12:48 PM
Hi,
This is not a stupid question at all, it's rather a good design question.
Yes, if you add a second core switch, you would need to add a second firewall for redundancy. You can configure the firewalls as active/standby, so when one firewall fails all traffic uses the other firewall. With most vendors' firewall, you can cluster them together and one firewall will be primary and the other on standby to take over traffic forwarding as soon as something happens to the primary.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:03 PM
As I understand, the second firewall should be connected to another port on the Edge router. But that would be a different network (subnet)? Unless it is possible to port aggregation (ether channel) on the Edge router. I know we can do this on switches, but routers...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:22 PM
So, that depends on what vendor's firewall and edge router you are using. If the edge router is, for example, Cisco ASR or ISR series, they do support Etherchannel. Also, if the firewalls are Cisco, you should not have any issue with Portchannel between them and the router. Most other vendors support port aggregation with LACP, but it is a little more challenging to configure Cisco and non-Cisco devices together.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:25 PM - edited 04-01-2018 01:30 PM
Thank you Reza, this is exactly what I wanted to know. And yes, ASR will be used as Edge router and Cisco firewall too. Great.
P.S: I don't know, maybe there is no need in Core switches at all. Maybe I need to connect Cisco Catalyst 3850-24XS (distribution switches) directly to firewalls then. The building on the picture is a hotel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:31 PM
Sure. Great, good to know it is Cisco with Cisco. Also, here is a link showing firewall connectivity to a set of switches. It should work the same way if the firewalls will be configured in active/standby mode as they should logically look as one device.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:35 PM
If the core switches have enough ports to accommodate connectivity from all access switches, there is really no need for distro switches at all. That would make the design simpler and easier to manage with fewer devices. On the other hand, if the distro switches are more up to date or more powerful, you can keep them and eliminate the core altogether and connect the disto switches directly to the firewalls.
Wha type of devices are the core and distro switches?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 01:44 PM - edited 04-01-2018 01:47 PM
The distribution switches are Cisco Catalyst 3850-24XS and the Core switches are Cisco Catalyst 6503-E. There will be loads of traffic, but the network is not going to expand.
There will be only three access switches, which are Cisco Catalyst 3850-24XS as well (because of the nice features regarding wireless access points)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 02:17 PM
In this case, you can eliminate one set of switches. If the 6503 switches come with Sup-2 and redundant power supplies, you can then eliminate the 3850-24XS (distro) altogether and connect the access switches to 6503s.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 02:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2018 02:25 PM
Glad to help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2018 03:33 PM
Hi Reza. I need to ask one more question. Will 6503 make Layer 2/Layer 3 forwarding decisions too?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2018 04:10 PM
Hi,
Yes, the 6503 is capable of both layer-2 and layer-3.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 09:34 PM
Hi,
I am also planning to implement something like this.
Before actually configuring the entire setup at my office, i have simulated the topology in PacketTracer. I have designed a collapsed core enterprise architecture in one of my new office buildings. I am using MLS Catalyst switches in Core and Layer 2 switches at Access Layer.
I want to connect two to connect two routers/MLS above the Core layer such that they serve as active/standby. I want to connect all three ISP into both these WAN routers/MLS and perform NAT in them individually.
Access-Core block has STP, HSRP, VLAN and Trunks mainly. Both Core switches have a Layer 2 etherchannel between them and a Layer 3 connectivity as well.
All connections from Core and above are purely Layer 3.
I have successfully configured the Collapsed Core. I can configure both WAN Edge routers for NAT etc as well.
The only problem im facing is connecting the Core to WAN routers redundantly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2024 07:58 AM
I have a question regarding this configuration. Would you do each core /30 vlan to the firewall or would you do a /29 vlan with hsrp or glbp between the two switches and the firewall? I'm asking because I recently deployed two firewalls and two cores and I configured the two switches with /30 vlan to the FW and HA. on the cores, I have core 1 as the main always and the number 2 is only in case 1 is not available, for the FW I just static route to Core 1 and put core 2 as secondary. Everything is working fine, execpt for a IBM Mainframe outside the FW and the MPS Software running on a virtual Windows Server on Nutanix. they seems to keep losing connectivity everyday, server team said it used to happen once a month or so, but now it's every day. everything else in the network seems to be ok, but this is really triggering.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide