- Cisco Community
- Technology and Support
- Networking
- Switching
- how to use ACL to redirect the traffic ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2012 02:28 AM - edited 03-07-2019 08:13 AM
hi guys :
i have following scenario
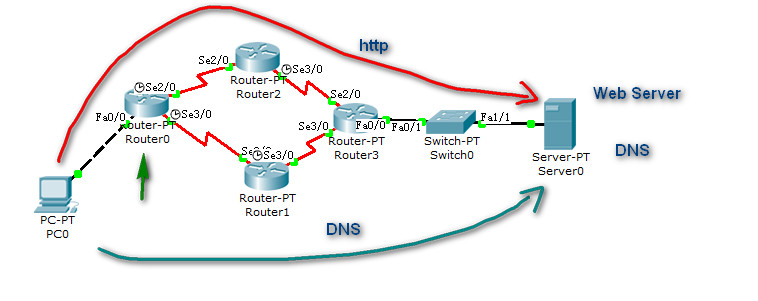
very simple, 4 routers runing ospf , i want to allow PC0 visit web server through the top route and other traffic (i.e. DNS) from bottom route.
OSPF at R0 by default is running load balance betweeb R1 and R2, so the packet from pc0 would be sent to R1 abd R2 respectively.
i know it can be done by using route map but i am just wondering if it can use simple access-lists to achieve the same goal?
have a nice day.
any help is appreciated.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2012 03:17 AM
You can't do that with only ACLs because you only drop the traffic, but you don't send it the other way. The most common solution to this is policy-based routing (PBR) where you also use an ACL to specify which traffic to send which way.
You could also look at Performance-routing. But that's much more complicated to implement:
http://www.cisco.com/en/US/partner/products/ps8787/products_ios_protocol_option_home.html
--
Don't stop after you've improved your network! Improve the world by lending money to the working poor:
http://www.kiva.org/invitedby/karsteni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2012 03:50 AM
Like Karsten stated, you can't do this with an acl. You'd need to use pbr to make any routing decisions based on protocol. You could create an acl that matches only dns, and then one to match http:
access-list 101 permit tcp any any eq 80
access-list 102 permit udp any any eq 53
route-map RouteDifferent permit 10
match ip address 101
set ip next-hop
route-map RouteDifferent permit 20
match ip address 102
set ip next-hop
int
ip policy route-map RouteDifferent
Whatever is denied by the routing policy (there's an implicit deny at the end like an acl) will get routed via the normal routing table. (policy routing comes before regular routing from inside -> outside).
HTH,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2012 03:17 AM
You can't do that with only ACLs because you only drop the traffic, but you don't send it the other way. The most common solution to this is policy-based routing (PBR) where you also use an ACL to specify which traffic to send which way.
You could also look at Performance-routing. But that's much more complicated to implement:
http://www.cisco.com/en/US/partner/products/ps8787/products_ios_protocol_option_home.html
--
Don't stop after you've improved your network! Improve the world by lending money to the working poor:
http://www.kiva.org/invitedby/karsteni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2012 08:11 PM
thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2012 08:11 PM
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2012 03:50 AM
Like Karsten stated, you can't do this with an acl. You'd need to use pbr to make any routing decisions based on protocol. You could create an acl that matches only dns, and then one to match http:
access-list 101 permit tcp any any eq 80
access-list 102 permit udp any any eq 53
route-map RouteDifferent permit 10
match ip address 101
set ip next-hop
route-map RouteDifferent permit 20
match ip address 102
set ip next-hop
int
ip policy route-map RouteDifferent
Whatever is denied by the routing policy (there's an implicit deny at the end like an acl) will get routed via the normal routing table. (policy routing comes before regular routing from inside -> outside).
HTH,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2012 08:10 PM
thanks, J!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

