- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: IP connectivity between Nexus and Palo Alto firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 07:25 AM
I'm struggling to understand connectivity problem between a switch and firewall. The Nexus is located between the Core switch and the edge firewall. It's purpose is to divert traffic via ITD for content filtering. My problem right now is that I'm not able to ping from the Nexus to the Palo Alto. Both interfaces have an IP in the same network.
When there is an IP on the Cisco side L3 interface the IP ARP looks like below. I'm trying to ping 164.104.10.1 connected to Ethernet 1/1. I can ping it if there is no IP configured on the Cisco interface, but when I put 164.104.10.2 on it, I can't ping and see the INCOMPLETE in the table.
IP ARP Table for context default
Total number of entries: 9
Address Age MAC Address Interface Flags
10.112.11.2 00:16:29 3cec.effa.dc98 Vlan3
10.112.11.3 00:16:29 3cec.ef62.a318 Vlan3
10.112.11.4 00:16:29 3cec.effa.dc1a Vlan3
10.112.11.5 00:16:29 3cec.effa.dc48 Vlan3
10.112.11.6 00:16:29 3cec.effa.dc88 Vlan3
10.112.11.7 00:16:29 3cec.effa.8eea Vlan3
10.112.11.8 00:16:29 3cec.effa.db5c Vlan3
164.104.10.130 00:03:10 8030.e0ba.a600 Vlan1
164.104.10.1 00:00:10 INCOMPLETE Ethernet1/1
Solved! Go to Solution.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:35 AM
Cisco_iBoss_switch# show ip interface brief
IP Interface Status for VRF "default"(1)
Interface IP Address Interface Status
Vlan1 164.104.10.129 protocol-up/link-up/admin-up
Vlan3 10.112.11.1 protocol-up/link-up/admin-up
Eth1/1 164.104.10.2 protocol-up/link-up/admin-up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:37 AM
there are two IP in same subnet hop you use different mask ? VLAN1 and Eth1/1
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:41 AM
Yes, those are both using a /25 mask.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:59 AM
NSK# show ip adjacency 164.104.10.1 detail | b default | grep –v ^$
share the output of above
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 10:26 AM
I'm not able to add the grep part of the command...
Cisco_iBoss_switch# show ip adjacency 164.104.10.1 detail | b default
IP Adjacency Table for VRF default
Total number of entries: 1
Address : 164.104.10.1
MacAddr : 0000.0000.0000
Preference : 255
Source : arp
Interface : Ethernet1/1
Physical Interface : Ethernet1/1
Packet Count : 0
Byte Count : 0
Best : No
Throttled : No
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 11:28 AM
Active/passive FW in cisco abd I think it same in Palo
Both FW interface use same subnet'
But the Sw that connect to is not use L3 port it use VLAN SVI
And here is your issue
Make two port connect to both FW in one VLAN' assign IP to this VLAN
That it
It design issue
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 12:20 PM
Okay, thank you. I understand why that would be a better design.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 12:25 PM
it not better or not
it work or not
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 01:42 PM - edited 04-29-2024 10:41 AM
Understood, and it would look like this, correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 02:29 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:24 PM
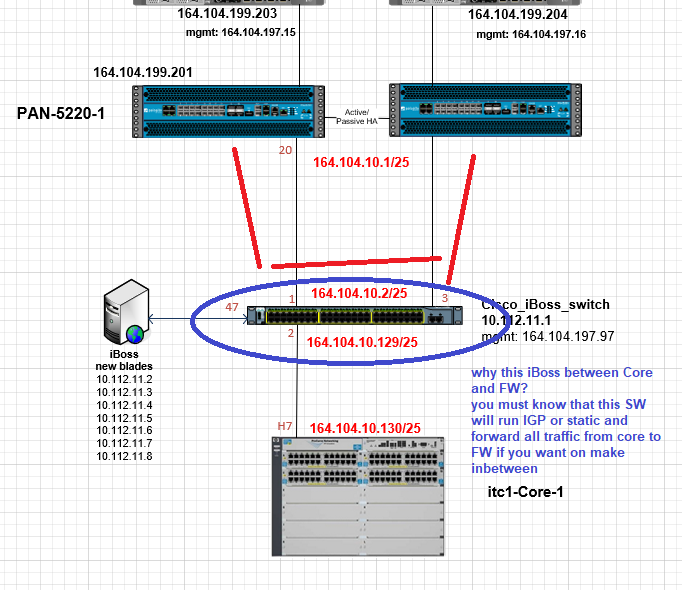
It's at that location in the topology because of ITD needed for iBoss content filtering, which we can't run on our core HPE switch. The default 0.0.0.0/0 route on the core switch points to 164.104.10.129 on the Cisco, then ITD redirects some traffic by means of ACLs in and out of the iBoss filter. Then the default route to the Internet on the Cisco points to 164.104.10.1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 07:28 PM
JFYI
I am unfamiliar with iBoss, but I know you can do all your content filtering on the PAs with the right license.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 08:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 09:31 AM
As of now the original "asymmetric" design is functioning by means of manual re-configuration of the 0.0.0.0/0 route on the Core switch, along with manual clearing of the ARP table on the Core and the Cisco. Re-design of this segment is planned to provide hands-off resiliency as suggested in this thread. Thanks for the help!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 09:57 AM
You are so welcome'
For my the only solution is re-design
MHM
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide