- Cisco Community
- Technology and Support
- Networking
- Switching
- Isolated Vlan Can Ping Primary VLAN on VTP Primary but not VTP Client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Isolated Vlan Can Ping Primary VLAN on VTP Primary but not VTP Client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2022 01:53 PM - edited 05-12-2022 02:23 PM
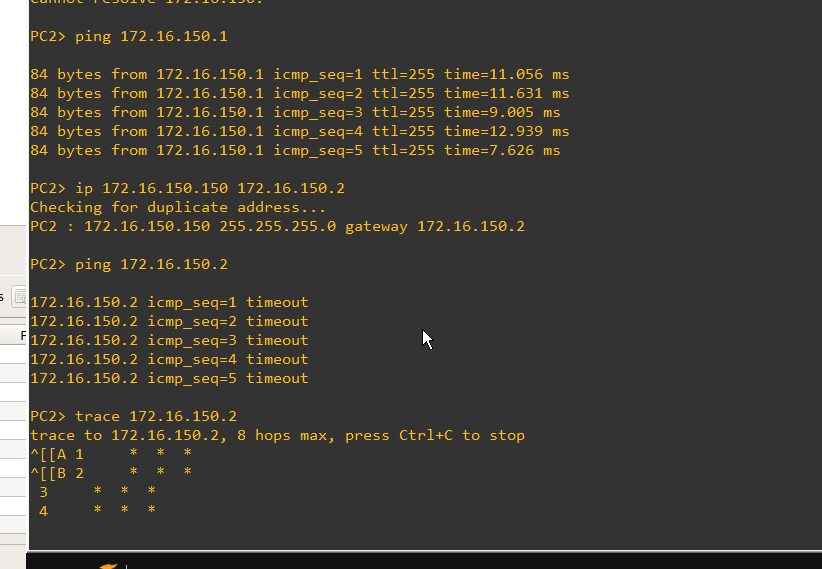
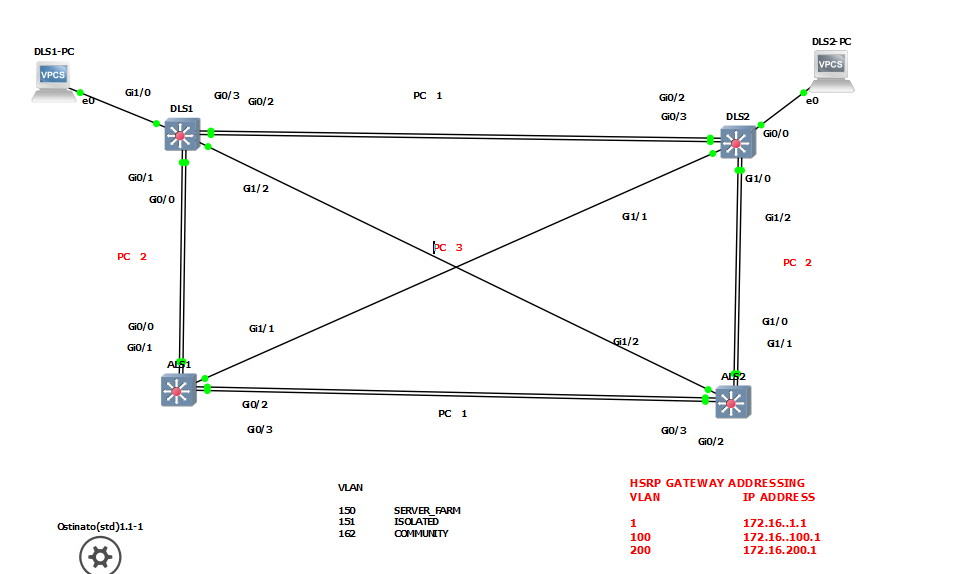
I have a host PC, DLS2-PC top right side of topology below. It belongs to secondary isolated VLAN 151, for the main vlan 150.
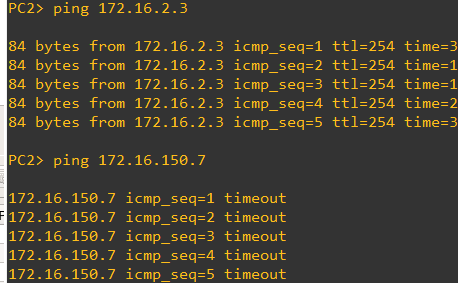
Switch DLS1 in the VTP primary whereas switch DLS2 is VTP server version 3. From host PC DLS2-PC2 can ping interface vlan 150 172.16.150.1 on DLS1 but not interface vlan 150 172.16.150.2 on DLS2. From this host PC I can also ping VLAN 1 on most of my switches given how my protocol is set up (I still cannot ping VLAN 1 on DLS2, I'm trying to work this out, but not a concern - I can ping VLAn 1 on DLS1). My concern is why can I ping VLAN 150 on VTP primary DLS1 switch (151, 152 are private VLANs which 150 is the main vlan) and not ping VLAN 150 on DLS2 switch?
I changed gateway on my host pc to 172.16.150.2 (int VLAN 150 on DLS2), and can still only ping VTP primary switch and not DLS2 switch see below where I change gateway to 172.16.150.2, and it timesout
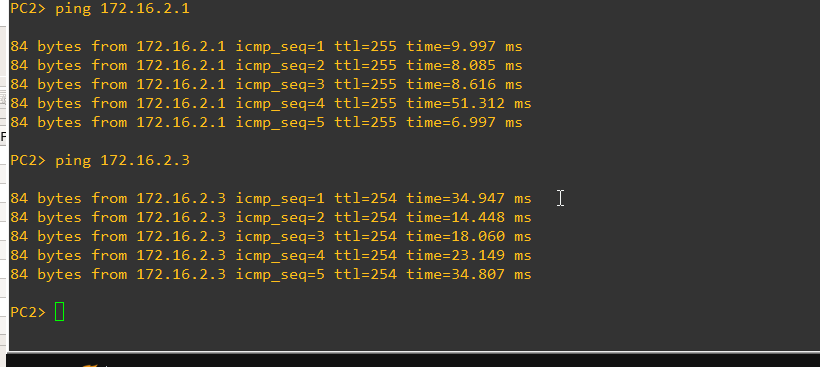
Isolated hosts can not communicate with other hosts. However they can communicate with the main vlan the isolated vlan belongs to according to documentation. According to pings it can also ping VLAN 1 on different switches (below DLS2-PC2 is pinging Vlan 1 on ALS1 and DLS1). Note 172.16.2.3 is on ALS1
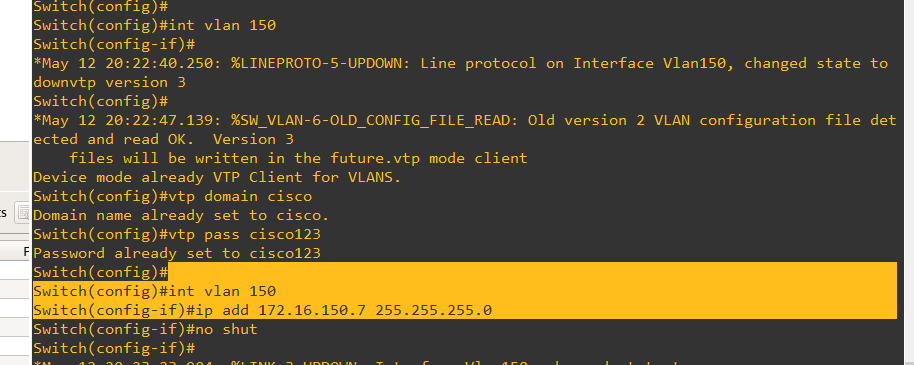
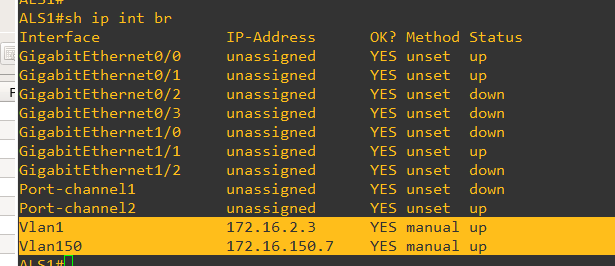
No on ALS1 I make it into a vtp vclient and add a VLAn 150 interface after updating DLS1 to propegate ALS1 vlan database
Here's ALS2 commands for VTP
And now DLS2-PC2 can ping vlan 1 on ALS1 but not VLAN 150, even though according to documentation vlan 150 is responsible for communication between private vlans and rest of network
"The PVLAN traffic flows are unidirectional from the host ports to the promiscuous ports. Traffic received
on primary VLAN enforces no separation and forwarding is done as in a normal VLAN.......
To allow host ports in secondary VLANs to communicate outside the private VLAN, you associate secondary
VLANs to the primary VLAN. If the association is not operational, the host ports (community and isolated
ports) in the secondary VLAN are brought down."
page 4
So according to what I have above I'm assuming that because it is not VTP primary the VLAN 150 on other switches cannot manage isolated vlan 151. I set DLS2 switch to a different VTp domain and still could not communicate with VLAN 150 on DLS2. So far it seems the isolated secondary VLAN can only communicate with VTP primary main VLAN 150, and not with vlan 150 on the other switches, and it seems like it was done like this by design.
Or am I missing something?
Any thoughts?
Below is topology and configs.
DLS2 SWITCH
May 12 20:43:24.570: %SYS-5-CONFIG_I: Configured from console by consolerunning-config
Building configuration...
Current configuration : 3862 bytes
!
! Last configuration change at 20:43:24 UTC Thu May 12 2022
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface Port-channel2
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/0
switchport private-vlan host-association 150 151
switchport mode private-vlan host
media-type rj45
negotiation auto
!
interface GigabitEthernet0/1
switchport private-vlan host-association 150 152
switchport mode private-vlan host
media-type rj45
negotiation auto
!
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 1 mode on
!
interface GigabitEthernet0/3
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 1 mode on
!
interface GigabitEthernet1/0
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 2 mode on
!
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
!
interface GigabitEthernet1/2
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 2 mode on
!
interface Vlan1
ip address 172.16.2.2 255.255.255.0
!
interface Vlan150
ip address 172.16.150.2 255.255.255.0
private-vlan mapping 152
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 172.16.2.1 255.255.255.255 172.16.2.1
!
!
!
!
!
control-plane
!
DLS1 Switch
urrent configuration : 4026 bytes
!
! Last configuration change at 20:45:12 UTC Thu May 12 2022
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname DLS1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
spanning-tree vlan 150-152 priority 24576
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface Port-channel2
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/0
switchport trunk encapsulation dot1q
switchport private-vlan host-association 150 152
switchport mode trunk
media-type rj45
negotiation auto
channel-group 2 mode on
!
interface GigabitEthernet0/1
switchport trunk encapsulation dot1q
switchport private-vlan host-association 150 152
switchport mode private-vlan host
media-type rj45
negotiation auto
channel-group 2 mode on
!
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 1 mode on
!
interface GigabitEthernet0/3
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
channel-group 1 mode on
!
interface GigabitEthernet1/0
switchport access vlan 152
switchport private-vlan host-association 150 152
switchport mode private-vlan host
media-type rj45
negotiation auto
!
interface GigabitEthernet1/1
media-type rj45
negotiation auto
!
interface GigabitEthernet1/2
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation auto
!
interface Vlan1
ip address 172.16.2.1 255.255.255.0
!
interface Vlan77
no ip address
shutdown
!
interface Vlan150
ip address 172.16.150.1 255.255.255.0
private-vlan mapping 151-152
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 172.16.2.3 255.255.255.255 172.16.2.3
!
!
!
!
!
control-plane
!
banner exec ^C
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2022 02:33 PM
Please note according to the lab I am taking this from DLS1-PC1 (top left of topology) can in dact ping vlan 150 on other switches, ehich is the case in my topology
DLS2-PC2 should not be able to ping vlan 150 on DLS2 according to the lab, which is my situation as well.
VTP version 3 propegation should work with Private VLANS according to the lab which is what i did. I defined the VLANS on DLS1 and not on otther switches. They were however propegated as private VLANS
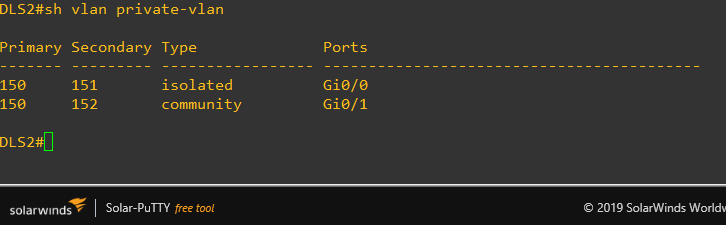
below is DLS2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2022 02:48 PM
Hi
Not sure which switch is this, the IOS I saw that is 15. But, where did you define that vlan 150 is the primary?
The syntax change a lot among devices but I expected to see something like:
switch(config)# vlan 150
switc(config-vlan)# private-vlan primary
switc(config-vlan)# end
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide