- Cisco Community
- Technology and Support
- Networking
- Switching
- No internet access to some VLANs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
No internet access to some VLANs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 08:51 AM
Hi,
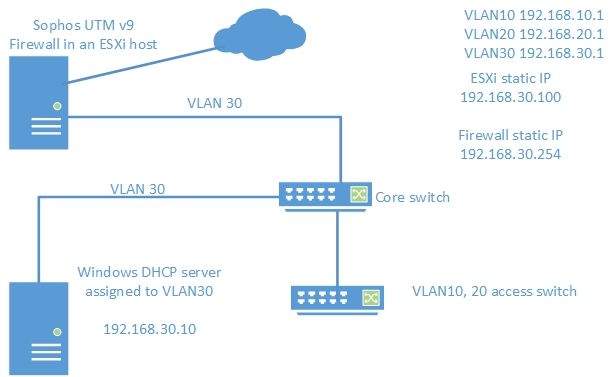
I have configured the setup mentioned in following drawing with Cisco 3650 core switch and two Cisco 2960 access switches. After configuring ip route 0.0.0.0 0.0.0.0 192.168.30.254 on core switch, vlan 30 is able to access internet while other vlans couldn't. Could someone please say what seems to be the issue preventing vlan 10,20 from accessing internet?
DHCP server and inter-vlan routing is working.
P.S - Sorry for my poor English
Regards,
M
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 09:07 AM
Hi.
Where is the default gateway configured for all the VLANs? I presume the DG in Core switch right? If this is the case, please use a different VLAN and subnet between the core switch and the FW. So all the traffic from VLANs 10,20,30 will hit the core switch (L2) and then from there will be routed to the firewall (L3)
Regards
Suresh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 09:50 PM
Hi Suresh,
Default gateways for VLANs are configured in core switch.
Could you please post the configuration for this?
Regards,
M
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 01:29 AM
- Create a new P2P /30 between the core switch and FW. for example, 192.168.40.0/30
- Create VLAN40 on the core switch and make the physical port connecting to the FW as an access-port vlan 40.
conf ter
inter gi1/10
switchport access vlan 40
- Create SVI for vlan40 on the switch and assign the IP of 192.168.40.2/30
conf ter
inter vlan 40
ip add 192.168.40.2/30
- Add a default route to the FW
conf ter
ip route 0.0.0.0 0.0.0.0 192.168.40.1
- Configure the IP of 192.168.40.1/30 in the physical port connecting to the core switch. The VLAN ID is NOT required.
- Add a static route for VLAN10,20,30 with the next-hop of 192.168.40.2
- Add NAT entries for VLAN10,20,30
Please rate all helpful responses
Regards
Suresh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 09:10 AM
between trunks to the core: all vlans are allowed?
in your firewall: Is there route back to your internal networks (vlan 10,20,30)?
in your firewall: Is there a nat configuration allowing others network (vlan 10,20,30)?
Maybe the problem is this.
*** Rate All Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 04:10 PM
Hello
The FW will be perfroming the NAT, so make sure that FW is aware of vlan 10,20 and as the routes back towards the core switch also it has the corect NAT rules for those other two subnets.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide