- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Hello guys,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Order Of Operations NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2012 02:20 AM - edited 03-07-2019 08:23 AM
Is someone able to confirm this is the correct order of operations for NAT.
Is there anything else that can be added to this network flow to make if more complete?
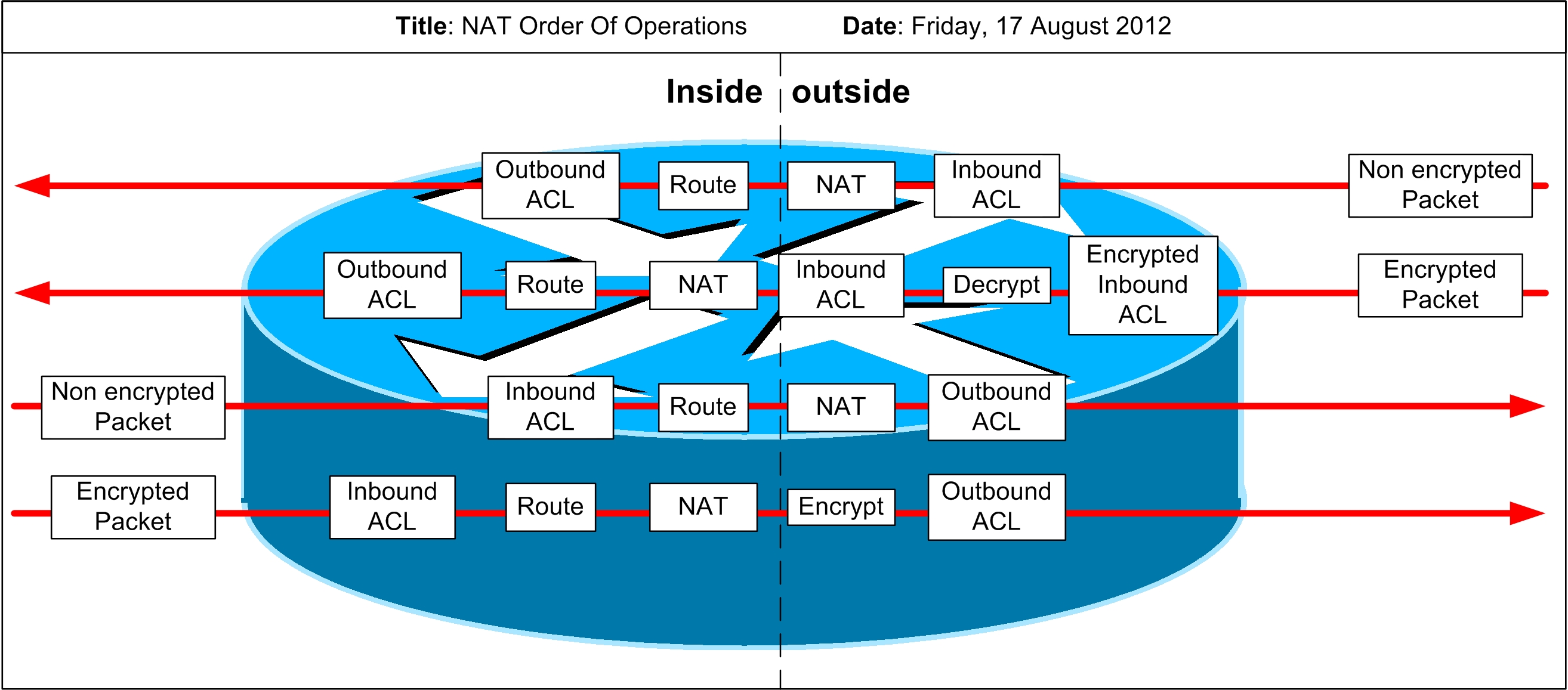
Any assistance is greatly appreciated.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2012 02:37 AM
Hello Tom,
I have always used the following document as a reference:
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080133ddd.shtml
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2012 03:40 AM
Cheers for the reply Peter,
That was the article I was working with.
I dont understand how the Decryption occurs in an Inside-To-Outside translation
or the encryption of an Outside-To-Inside translation?
Inside-to-Outside | Outside-to-Inside |
|
|
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2012 03:57 AM
Hello Thomas,
I would hypothesize that the decryption in the in-to-out and encryption in the out-to-in paths are related to IPsec VPNs in which the clients are considered "inside" and they are accessing the outside internet. Think of a teleworker using a IPsec-protected access to internet via his/her company infrastructure. After creating an IPsec tunnel terminated at an interface marked as "inside", the teleworker's IPsec-protected traffic arrives at the router, is decrypted and after routing out through an "outside" interface, it is being NATted. For the return traffic, it is NATted from "outside" to "inside", then sent to the teleworker IPsec-encrypted.
This is I how understand it.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2012 05:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 04:29 AM
http://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/6209-5.html
!
inside-to-outside
!
policy routing
routing
nat translation
!
outside-to-inside
nat translation
policy-routing
routing
!
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2016 05:43 AM
Hello guys,
I have the same problem and as I can see here, this is not answered yet.

I looked after this topic and I found the following:
Inside-to-Outside:
- policy routing
- routing
- NAT inside to outside (local to global translation)
Outside-to-Inside:
- NAT outside to inside (global to local translation)
- policy routing
- routing
I understand that by out-to-in direction NATing happens first and only then routing, this is logical, since the main point would be in to route only a private IP in the intern network instead of a public one.
But in case of in-to-out direction, I don't see the logic of making routing before NATing.
In order to properly route the packet with a public destination address, it first has to be NATted back from the private IP.
Did I understand something incorrectly?
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 07:59 AM
The reason it needs to check routing and policy routing first on in-to-out NAT translations is that there are likely several interfaces it could use to reach the next hop for routing and therefore the exit interface needs to be determined prior to invoking NAT because maybe you NAT it to different outside global address space depending on the interface which it leaves the router. On the out-to-in, you likely don't control the path in which it comes in because the most common (but not the ONLY) use case is traffic coming into the device from the internet and again the most common setup is a single, predictable and consistent interface on the router. So it's going to perform the UN-NAT first, and then use routing and policy routing to determine the inside interface it should go to in order to reach the final destination.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2020 05:42 AM
Old thread but came up in my searches and the question asked by @andnagy122 is what i had in mind as well . Cant really think of any reason why if the routing is correct the NAT cannot be performed before the routing. However for policy based routing that may look at source you would understand why policy-routing comes before NAT. The only reason that comes to mind is, Cisco or any vendor would want to combine the policy routing and routing together so to have all routing functions come first and not separate routing before and after NAT. So trying to avoid something like:
Policy Routing
NAT
Routing
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

