- Cisco Community
- Technology and Support
- Networking
- Switching
- rip 224.0.0.9 suppression not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
rip 224.0.0.9 suppression not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2018 05:27 PM - edited 03-08-2019 03:32 PM
hi all i am working on rip
i want to break rip updates by denying 224.0.0.9
which is not working
my configurion
access-list 1 deny 224.0.0.9 0.0.0.0a
access-list 1 permit any
int fa0/0
ip access-group 1 in
ip access-group 1 out
but still, have rip route and ip debug rip is showing packet send with multicast address.
why shouldn't it blocked?
thanks
regard
babar
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2018 11:34 PM
Hello,
you need to use an extended IP access list:
access-list 101 deny ip any host 224.0.0.9
access-list 101 permit ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 03:04 AM
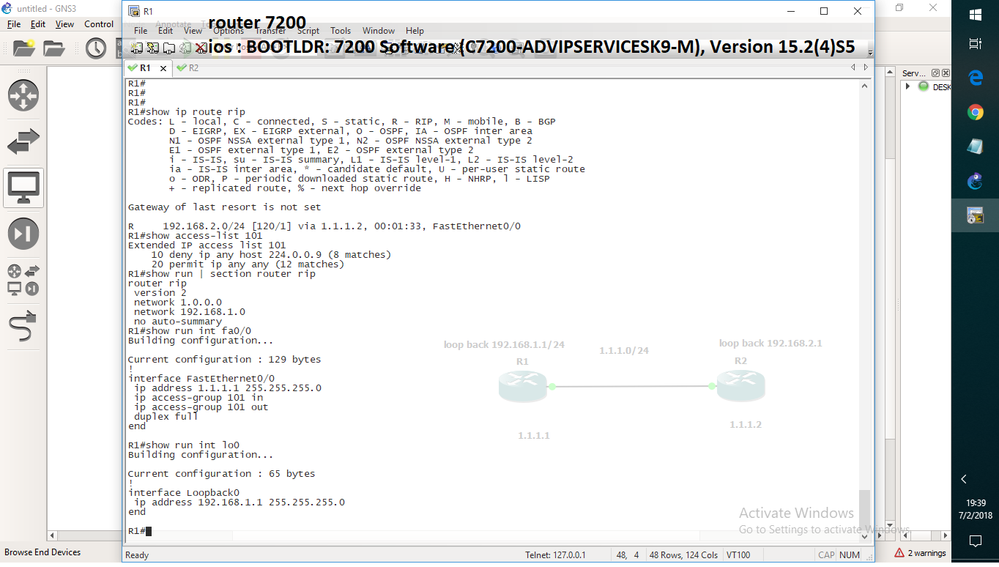
i tried it but still it is not working .
rip is still learning route from neighbor
i also did clear ip route *
show access-list 101
10 deny ip any host 224.0.0.9 (312 matches)
20 permit ip any any ( 12 matches)
inter fa0/0
ip access-group 101 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 03:16 AM
If you're interested there a functionality that achieve your purpose and it's used with the command passive-interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 03:26 AM
yeah i used standard access-list, but after guidance of first reply i tried for extended access list still it is not working.
i know about passive interface ,it stop sending routing updates i tried it is working perfactly...
But i want to block its multi-cast address using extended control list ...
it is not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 04:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 04:18 AM
Did you apply the access list outbound as well ?
access-list 101 deny ip any host 224.0.0.9
access-list 101 permit ip any any
!
inter fa0/0
ip access-group 101 in
ip access-group 101 out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 04:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 07:54 AM
Rip routes are still there
if it is not working could i block at udp layer 520....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 08:33 AM
Hello,
what does your topology look like ? Do you have back to back routers with only one connection ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 01:25 PM - edited 07-02-2018 01:39 PM
You can't use an ACL to block outgoing RIP messages originated locally. ACL simply doesn't filter locally originated traffic. Thats why there's a "passive-interface" command.
You can however block inbound traffic. Make sure you create the ACL before trying to apply it to the interface otherwise it won't work. So give it a try agagain and recreate it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide